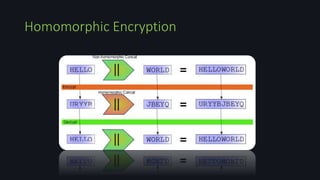
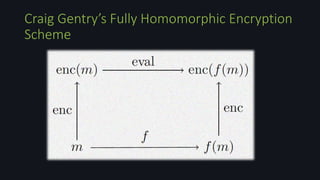
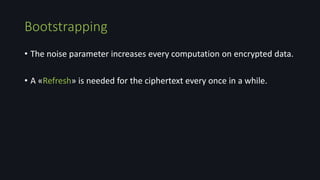
Homomorphic encryption allows computations to be performed on encrypted data without decrypting it first. This document discusses homomorphic encryption techniques including partially homomorphic encryptions that support either addition or multiplication operations, and fully homomorphic encryption introduced by Craig Gentry that supports both types of operations. It also covers the use of ideal lattices in lattice-based cryptosystems and the bootstrapping technique used to "refresh" ciphertexts and prevent noise from accumulating during homomorphic computations.











![Raw RSA MAGMA code
p:=NextPrime(Random([1..2^124]));
q:=NextPrime(Random([1..2^124]));
n:=p*q;
phi:=(p-1)*(q-1);
repeat
e:=Random([1..phi]);
until GCD(e,phi) eq 1;
g,x,y:=XGCD(e,phi);
d:=x mod phi;
//ENCRYPTION
m:=Random([0..n]);
c:=Modexp(m,e,n);
m;
//DECRYPTION
Modexp(c,d,n);](https://image.slidesharecdn.com/homomorphicencryptionseminar-150610122514-lva1-app6892/85/Homomorphic-Encryption-14-320.jpg)
![Partially Homomorphism of Raw RSA MAGMA code
p:=NextPrime(Random([1..2^124]));
q:=NextPrime(Random([1..2^124]));
n:=p*q;
phi:=(p-1)*(q-1);
repeat
e:=Random([1..phi]);
until GCD(e,phi) eq 1;
g,x,y:=XGCD(e,phi);
d:=x mod phi;
//ENCRYPTION
m1:=Random([0..n]);
m2:=10;
c:=Modexp(m1*m2,e,n);
(Modexp(m1,e,n)*Modexp(m2,e,n)) mod n;
c;
//DECRYPTION
Modexp(c,d,n);
(m1*m2) mod n;](https://image.slidesharecdn.com/homomorphicencryptionseminar-150610122514-lva1-app6892/85/Homomorphic-Encryption-15-320.jpg)













![Somewhat Homomorphic Scheme
• To add two ciphertexts;
𝑐 = 𝑐1 + 𝑐2 = 𝑏1 + 𝑏2 + 2 𝑥1 + 𝑥2 + 𝑘1 + 𝑘2 𝑝 = 𝑏1⨁ 𝑏2 + 2𝑥 + 𝑘𝑝
Decryption recovers the 𝑏1⨁ 𝑏2 as long as (𝑏1 + 2𝑥1) + (𝑏2 + 2𝑥2) ∈ [-N,N]
• To multiplicate two ciphertexts;
𝑐 = 𝑐1 ∗ 𝑐2 = 𝑏1 ∗ 𝑏2 + 2 𝑏1 𝑥2 + 𝑏2 𝑥1 + 2𝑥1 𝑥2 + 𝑘𝑝 = 𝑏1 ∗ 𝑏2 + 2x +𝑘𝑝
Decryption recovers the 𝑏1 ∗ 𝑏2 as long as (𝑏1 + 2𝑥1) * (𝑏2 + 2𝑥2) ∈ [-N,N]](https://image.slidesharecdn.com/homomorphicencryptionseminar-150610122514-lva1-app6892/85/Homomorphic-Encryption-30-320.jpg)


![• An ideal lattice, is simply an ideal in ℤ[x]/(f(x)).
• f(x) of degree n; each such ideal can be represented by a lattice
generated by the columns of a lattice basis 𝐵𝚤 , an n × n matrix.
Ideal Lattices](https://image.slidesharecdn.com/homomorphicencryptionseminar-150610122514-lva1-app6892/85/Homomorphic-Encryption-33-320.jpg)

















![//randomly select odd number of P bits with base 2
keygen := function()
p := Random([1,P-1]);
if (p mod 2) eq 0 then
p := p + Random([1,2]);
end if;
return p;
end function;
p := keygen();
Implementation of Somewhat Homomorphic
Encryption over Integers on MAGMA](https://image.slidesharecdn.com/homomorphicencryptionseminar-150610122514-lva1-app6892/85/Homomorphic-Encryption-52-320.jpg)
![//compute m' = m mod 2, c = m' + pq
encrypt := function(m)
mprime := Random([1,N-1]);
mprime := mprime - mprime mod 2 + m mod 2;
q := Random([1,Q-1]);
return mprime + p*q;
end function;
//compute m = (c mod p) mod 2
decrypt := function(c)
return (c mod p) mod 2;
end function;
Implementation of Somewhat Homomorphic
Encryption over Integers on MAGMA](https://image.slidesharecdn.com/homomorphicencryptionseminar-150610122514-lva1-app6892/85/Homomorphic-Encryption-53-320.jpg)
![//RSA
p1:=NextPrime(Random([1..2^124]));
q1:=NextPrime(Random([1..2^124]));
n1:=p1*q1;
phi:=(p1-1)*(q1-1);
repeat
e:=Random([1..phi]);
until GCD(e,phi) eq 1;
g,x,y:=XGCD(e,phi);
d:=x mod phi;
Implementation of Somewhat Homomorphic
Encryption over Integers on MAGMA](https://image.slidesharecdn.com/homomorphicencryptionseminar-150610122514-lva1-app6892/85/Homomorphic-Encryption-54-320.jpg)
![//RSA ENCRYPTION
m1:=Random([1..n1]);
c1:=Modexp(m1,e,n1);
printf "Plaintext: %on",m1;
printf "Ciphertext: %on",c1;
//value that we will add to ciphertext
op := 128;
//binary conversions
mbin := IntegerToSequence(m1,2);
opbin := IntegerToSequence(op,2);
cbin := IntegerToSequence(c1,2);
Implementation of Somewhat Homomorphic
Encryption over Integers on MAGMA](https://image.slidesharecdn.com/homomorphicencryptionseminar-150610122514-lva1-app6892/85/Homomorphic-Encryption-55-320.jpg)
![//noise parameter must be smaller than b
//HOMOMORPHIC ENCRYPTION
for i in [1..#opbin] do
cbin[i] := encrypt(cbin[i]) + encrypt(opbin[i]);
end for;
//HOMOMORPHIC DECRYPTION
for i in [1..#cbin] do
cbin[i] := decrypt(cbin[i]);
end for;
//decimal conversion
c2 := SequenceToInteger(cbin,2);
printf "Summed Ciphertext: %on",c2;
printf "Addend value to Ciphertext: %on",AbsoluteValue(c2 - c1);
printf "Noise: %o",c2 mod 2;
Implementation of Somewhat Homomorphic
Encryption over Integers on MAGMA](https://image.slidesharecdn.com/homomorphicencryptionseminar-150610122514-lva1-app6892/85/Homomorphic-Encryption-56-320.jpg)

