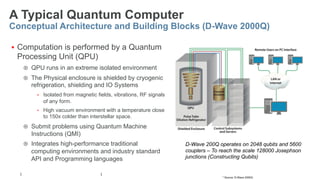
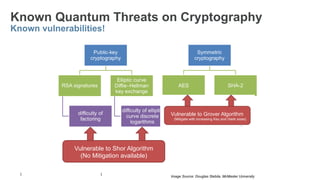
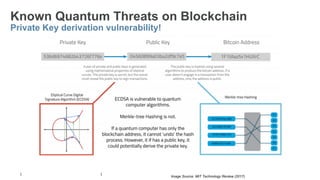
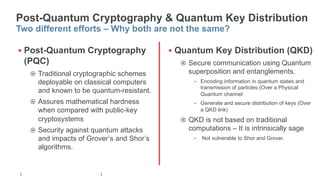
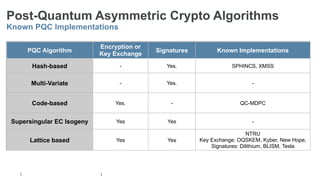
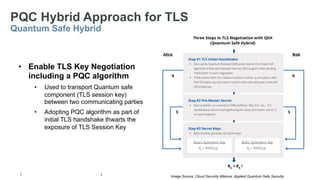
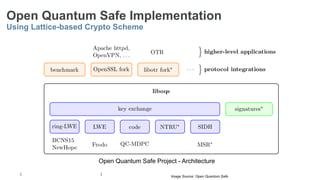
The document provides a comprehensive overview of post-quantum cryptography, comparing classical and quantum computing, and highlighting the vulnerabilities traditional encryption faces against quantum algorithms like Shor's and Grover's. It discusses the need for post-quantum cryptography (PQC) and quantum key distribution (QKD) as methods to secure communications against quantum attacks, detailing various quantum-resistant algorithms. Additionally, it reviews ongoing efforts for standardization in the realm of post-quantum cryptography through initiatives by NIST and ETSI.