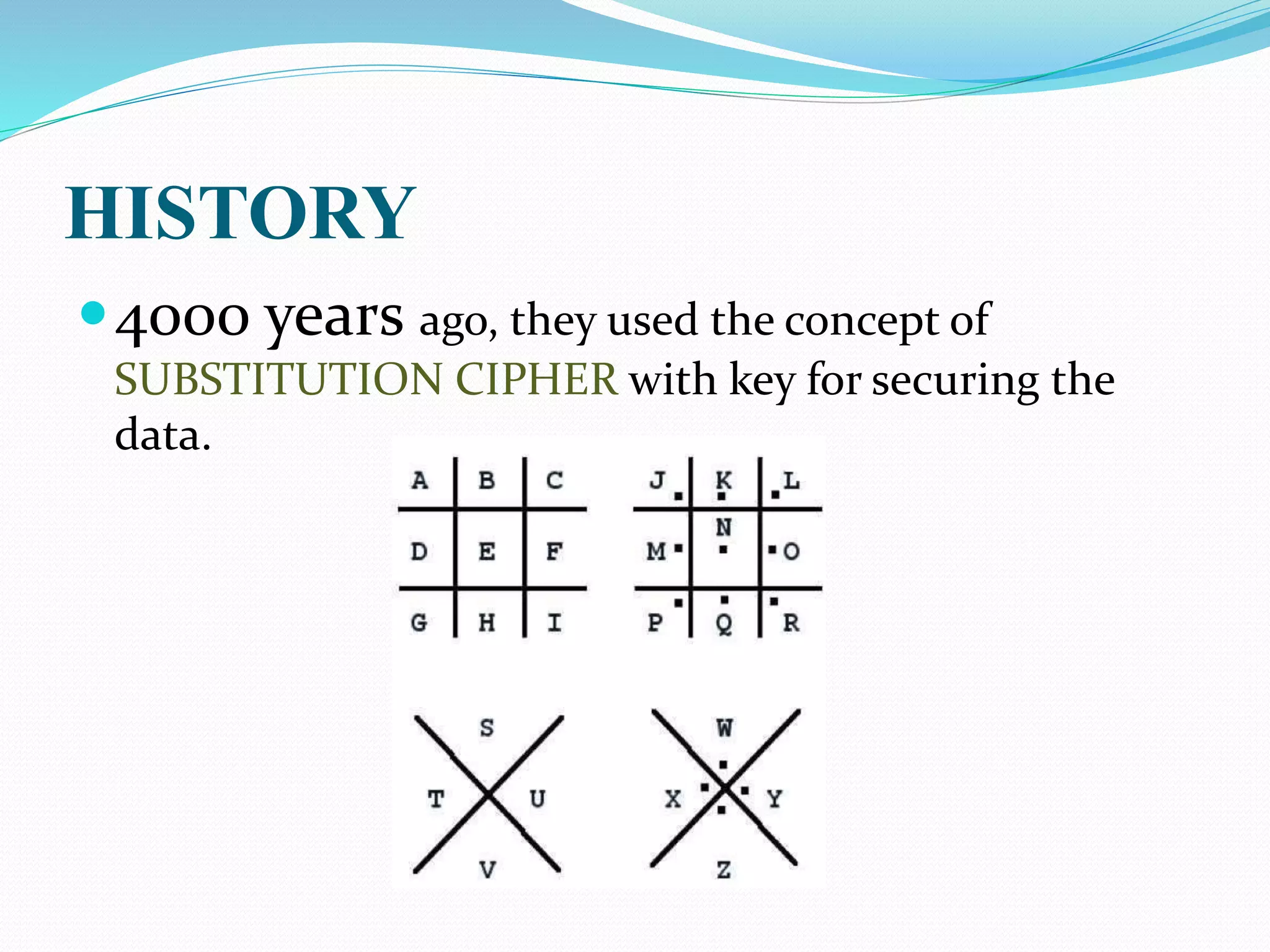
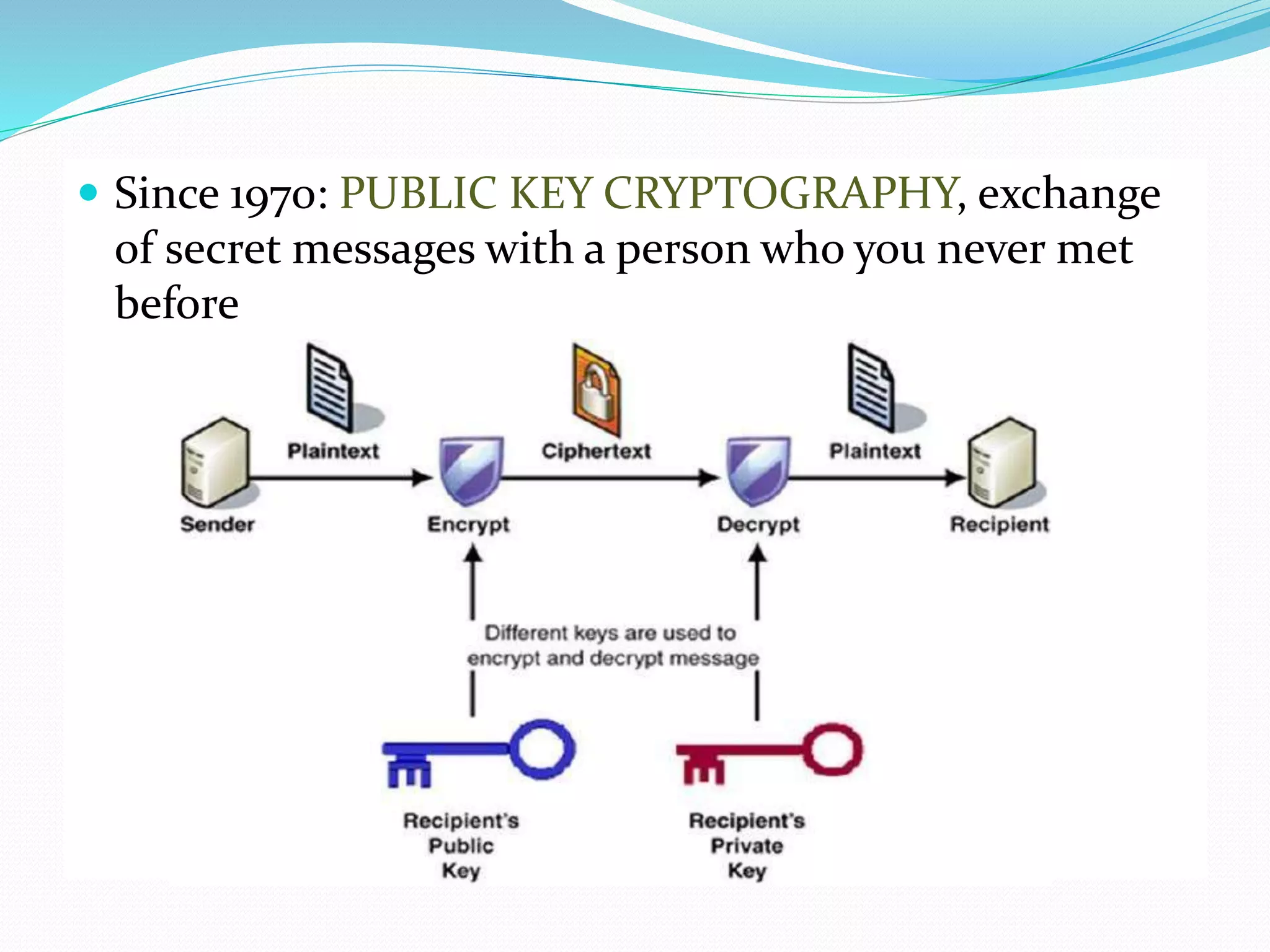
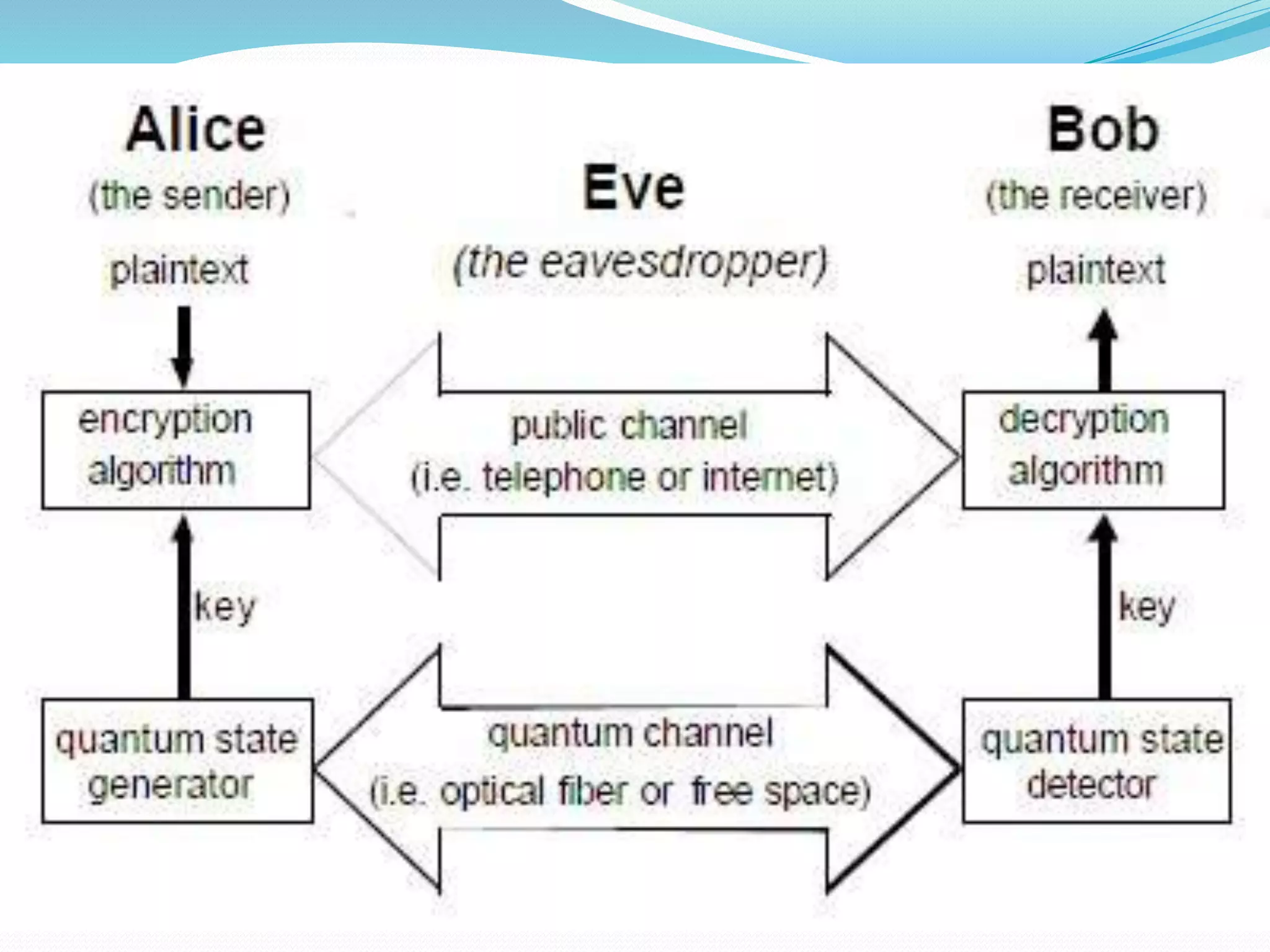
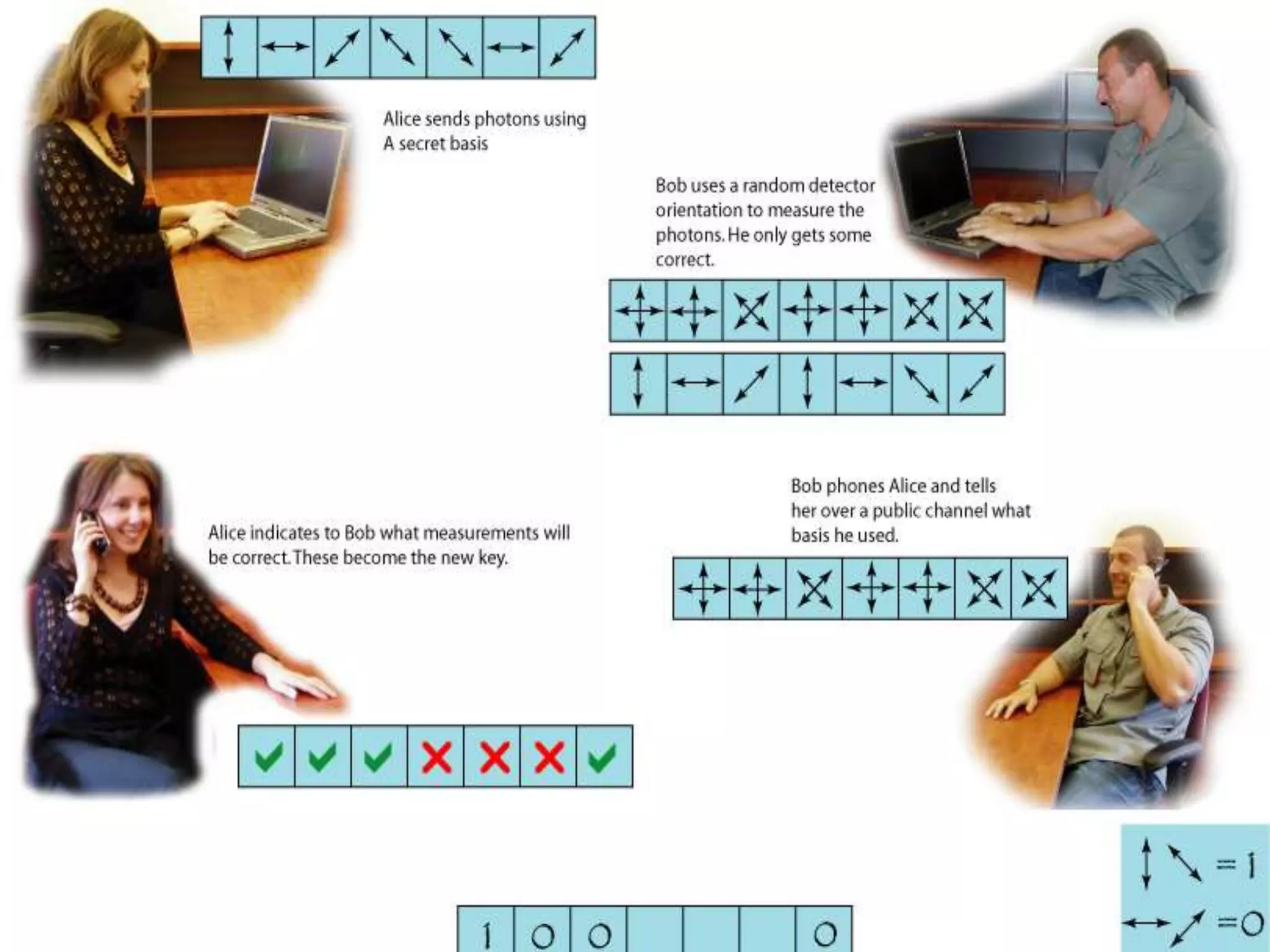
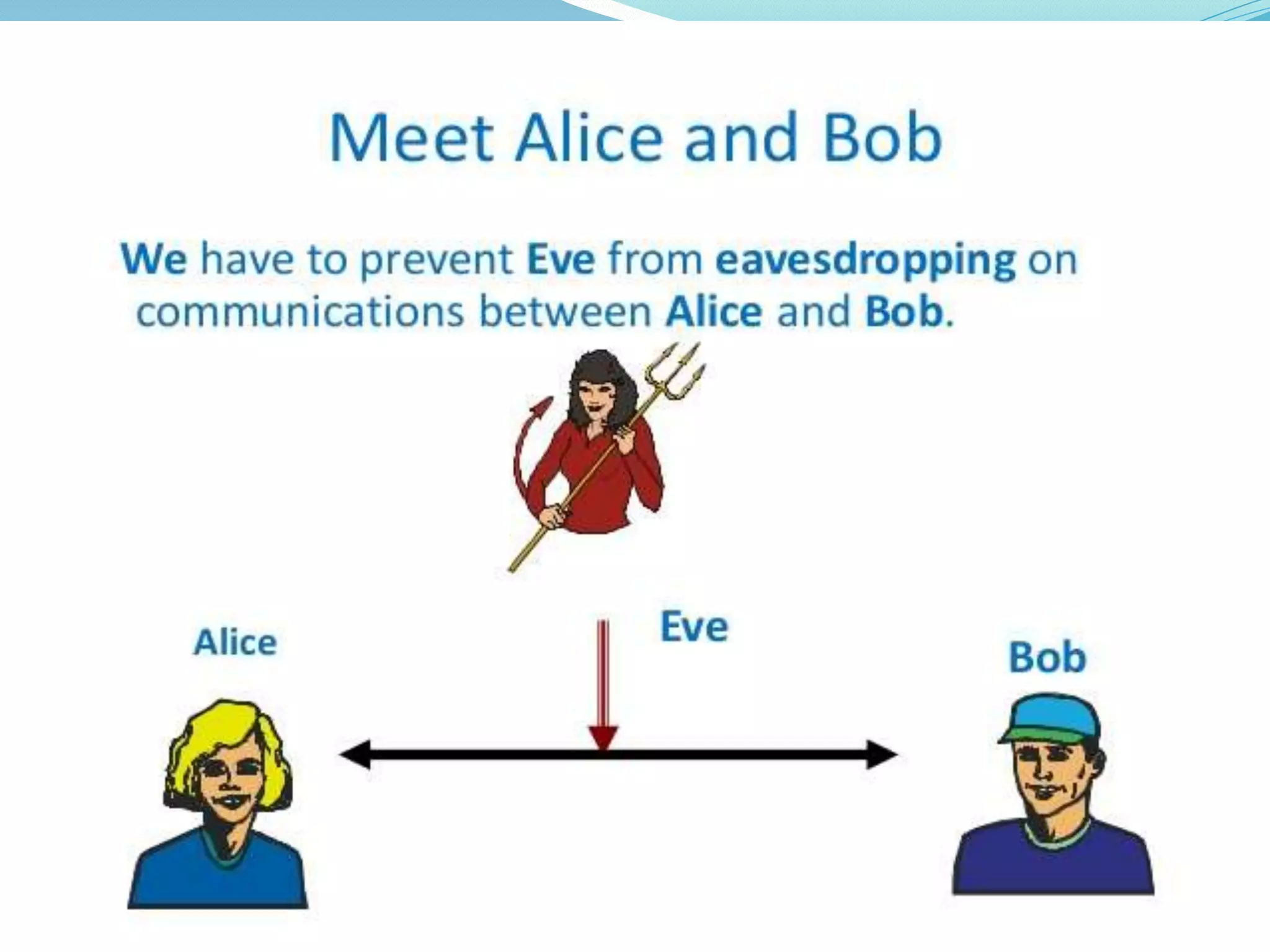
This document provides an introduction to quantum cryptography. It explains that quantum cryptography uses principles of quantum mechanics like quantum entanglement and the Heisenberg uncertainty principle to securely distribute encryption keys. It notes that quantum cryptography combines the concepts of one-time pads and quantum key distribution, using quantum mechanics to detect any attempts at eavesdropping. The document also briefly discusses the history of cryptography, how quantum key distribution works, advantages and disadvantages of quantum cryptography, and its future applications.