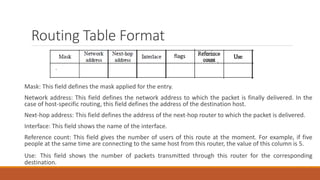
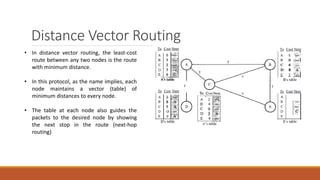
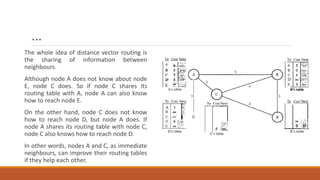
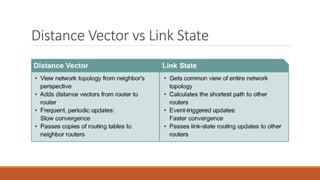
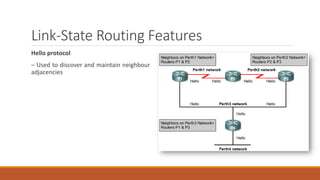
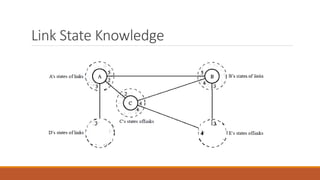
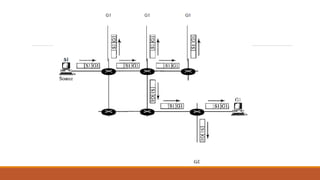
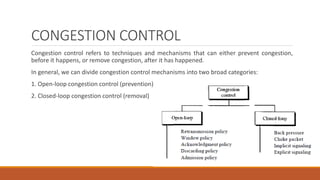
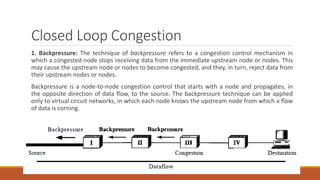
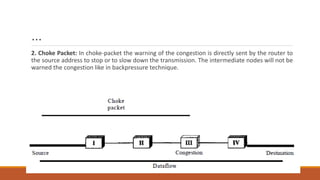
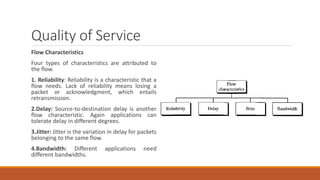
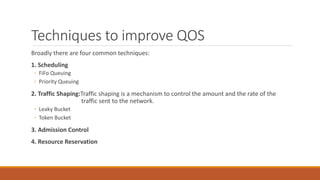
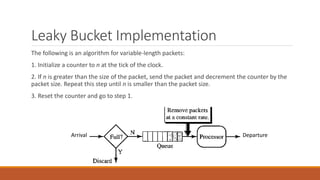
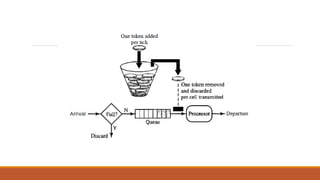
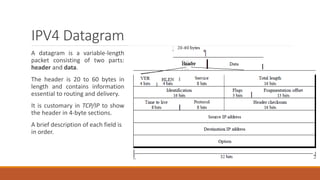
Static routing tables require manual configuration and cannot automatically update when network changes occur. Dynamic routing tables use protocols like RIP, OSPF, or BGP to periodically update routing tables across routers when links or routers fail. Routing tables contain information like the network address, next hop address, interface, and flags to determine the best path for packet delivery.