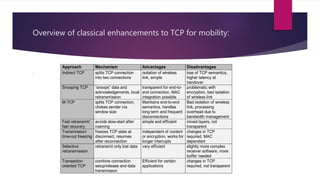
The document discusses several mechanisms used in TCP for mobile computing. It describes:
1) TCP congestion control mechanisms like slow-start and fast retransmit/fast recovery which are designed to address packet loss. However, these can be inappropriate for wireless networks where packet loss is often due to errors rather than congestion.
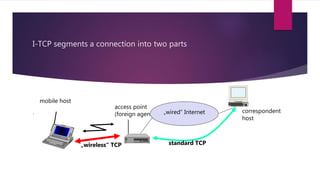
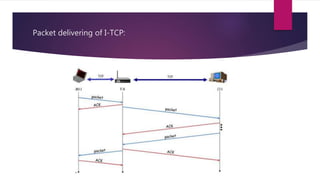
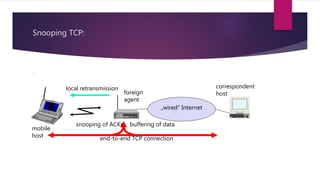
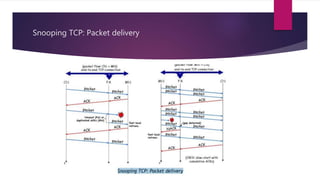
2) Approaches like Indirect TCP, Snooping TCP, and Mobile TCP which modify TCP for mobile networks by splitting connections or having a supervisory host monitor the connection to enable local retransmissions and avoid unnecessary window reductions when the mobile host disconnects.
3) Other TCP optimizations for mobile like forced fast retransmit after handovers and transmission timeout freezing to avoid slow-start