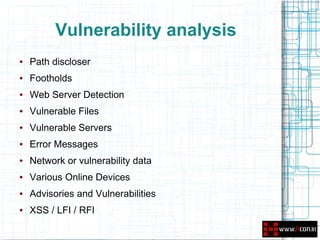
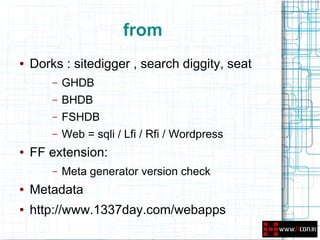
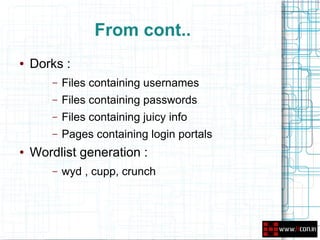
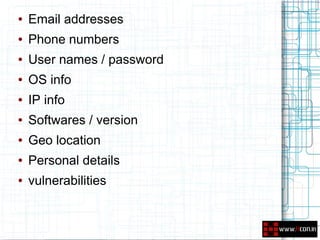
This document discusses leveraging open source intelligence (OSINT) for penetration testing. It defines OSINT as collecting publicly available information and analyzing it to produce actionable intelligence. The document outlines how OSINT can be used at different stages of a penetration test, including reconnaissance, vulnerability analysis, and social engineering. It provides examples of the types of information that can be obtained from OSINT, such as email addresses, passwords, and personal details. The document also lists specific tools and online resources that can be used to perform OSINT for purposes like passive reconnaissance, searching for vulnerabilities, and profiling individuals.