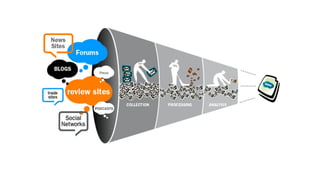
Open-source intelligence (OSINT) refers to information gathered from publicly available sources including social media sites, traditional media, maps, government reports, and academic papers. OSINT tools are used to gather intelligence from these sources through activities like searching metadata, websites, and databases. Common OSINT tools mentioned are Maltego for relationships, Google Hacking Database for search operators, Metagoofil for document metadata, Shodan for devices, Spiderfoot for automation, TheHarvester for online profiles, and FOCA for hidden information. While useful, OSINT has limitations like information overload and potential false positives.