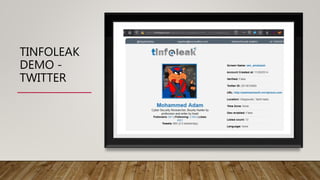
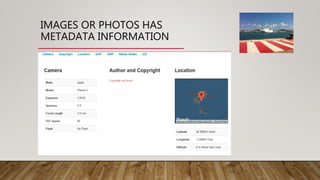
The document summarizes a webinar on ethical hacking and cybersecurity. It introduces the speaker, Mohammed Adam, and his background. It then outlines the 5 stages of ethical hacking that will be covered: reconnaissance, scanning and enumeration, exploitation, post-exploitation, and clearing tracks. It focuses on the reconnaissance stage, explaining the concepts of open-source intelligence (OSINT) and different types of intelligence like human, geospatial, signals, and open-source intelligence. It provides examples of how OSINT is used in ethical hacking and penetration testing as well as examples of traditional and modern OSINT methods and tools.