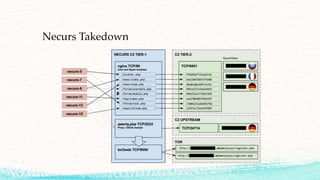
This document summarizes several cybersecurity news stories from March 2020. It discusses how scammers were exploiting fears around the coronavirus pandemic, hundreds of malicious Chrome extensions that stole user data, Microsoft releasing antivirus software for Linux, a vulnerability in WiFi encryption that could allow decrypting communications, a ransomware attack on a defense contractor that resulted in a $500,000 ransom payment, research into using ultrasonic waves to control audio devices for surveillance purposes, two new side-channel attacks affecting AMD processors, an unfixable flaw in Intel chips, and an operation that disabled the Necurs botnet through domain prediction.