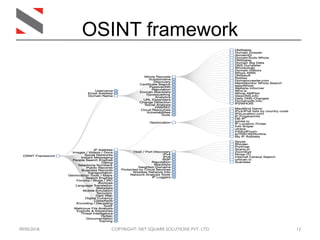
The document provides an overview of Open Source Intelligence (OSINT), its origins, and how it is utilized to gather information from public sources. It discusses various tools and techniques for OSINT activities, including Kali Linux, OSINT Framework, and tools like TheHarvester and Shodan. Key concepts include identifying targets, understanding digital footprints, and assessing security through intelligence gathering.