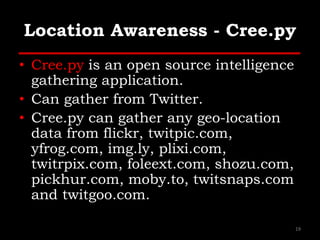
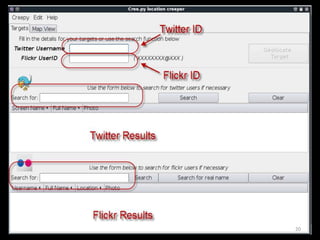
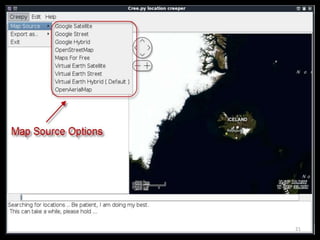
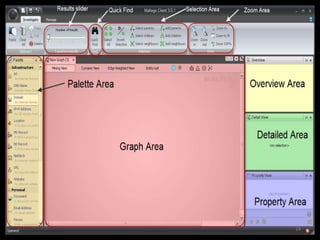
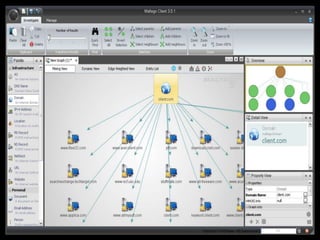
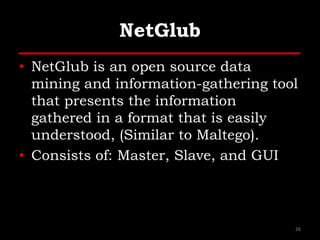
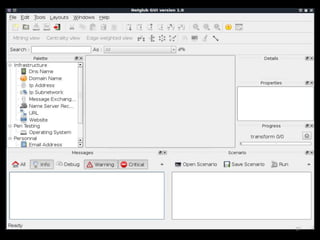
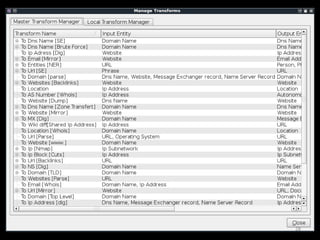
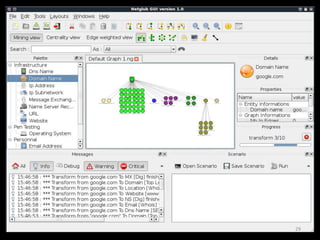
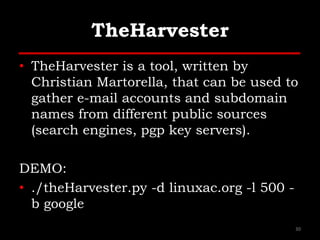
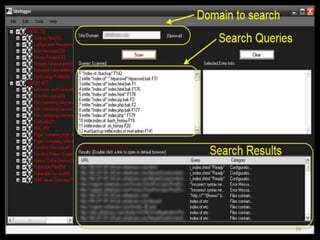
The document outlines various hacking techniques and methods for intrusion detection, focusing on the importance of reconnaissance and open-source intelligence (OSINT) in facilitating successful attacks. It details different forms of intelligence gathering, target selection, and tools such as cree.py, Maltego, and TheHarvester used for data mining and information extraction. Additionally, it discusses covert gathering techniques and the role of metadata leakage in cybersecurity operations.
![Hacking Techniques &
Intrusion Detection
Ali Al-Shemery
arabnix [at] gmail](https://image.slidesharecdn.com/day05-recon-231219112930-8b2e26c3/75/hacking-techniques-and-intrusion-techniques-useful-in-OSINT-pptx-1-2048.jpg)