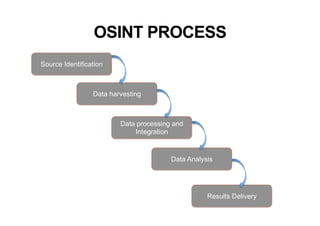
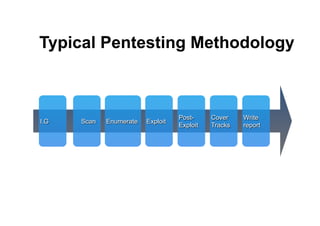
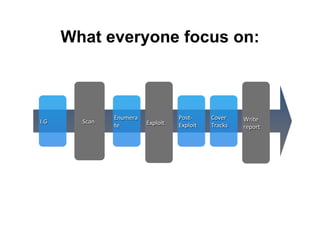
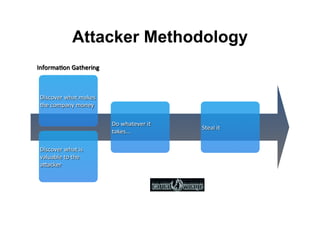
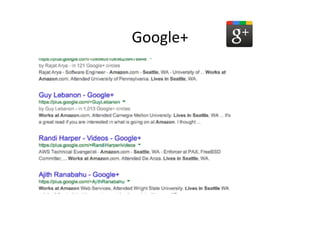
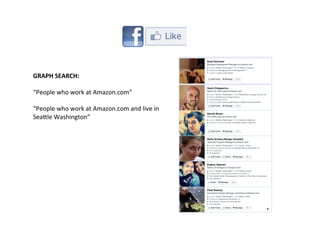
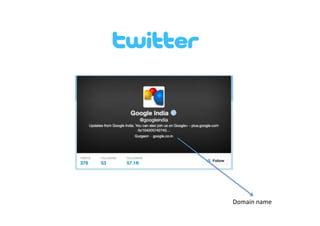
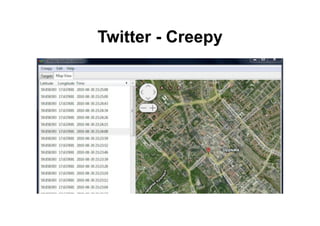
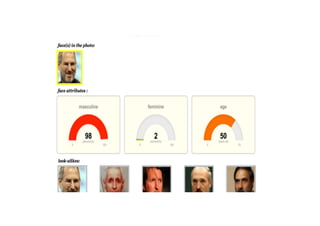
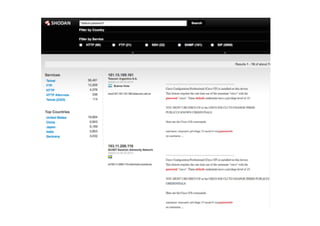
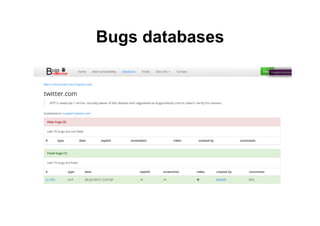
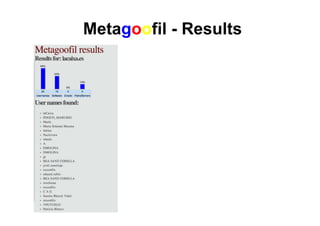
This document provides an overview of offensive open-source intelligence (OSINT) techniques. It defines OSINT and discusses the differences between offensive and defensive OSINT approaches. Offensive OSINT focuses on gathering as much public information as possible to facilitate an attack against a target. The document outlines the OSINT process and details specific techniques for harvesting data from public sources, including scraping websites, using APIs, searching social media, analyzing images and metadata, and researching infrastructure components like IP addresses, domains, and software versions. The goal of offensive OSINT is to discover valuable information like employee emails, usernames, relationships, locations and technical vulnerabilities to enable attacks like phishing, social engineering, and infiltration.