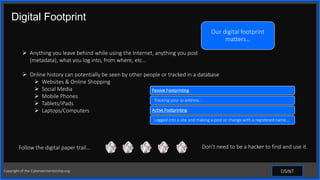
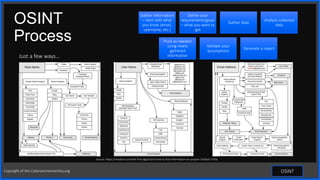
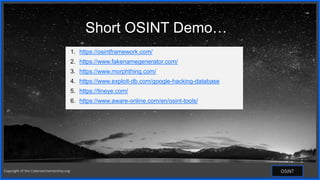
This document discusses open-source intelligence (OSINT) and how it can be used for cybersecurity awareness or against individuals. OSINT involves collecting information from public sources and can be used by cybersecurity professionals, but also by threat actors for attacks like identity theft, account takeover, and social engineering. The document provides examples of OSINT tools and techniques that can be used for both ethical purposes like penetration testing or unethical purposes like criminal phishing campaigns.