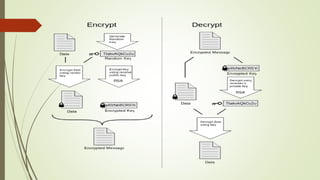
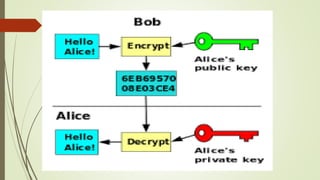
This document discusses email security concepts and PGP. It defines email security as securing email accounts and content. Techniques mentioned include strong passwords, spam filters, and encryption. Threats to email security are loss of confidentiality, integrity, and authentication. The document also discusses specific email security threats like snowshoe spamming, hacktivism, and data breaches. It defines concepts related to PGP like public/private key encryption and how PGP can be used to encrypt emails and files.