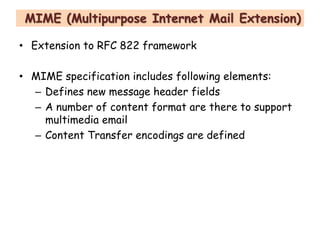
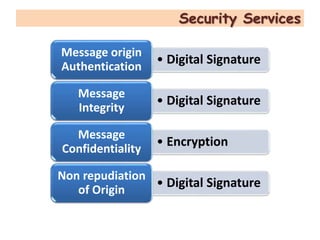
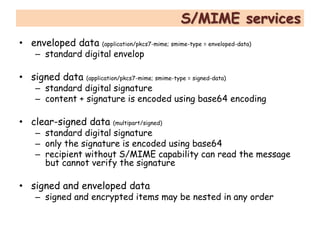
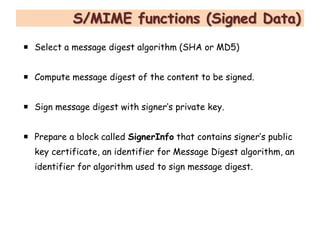
S/MIME and PGP are the two main protocols for securing email. S/MIME was developed by RSA to provide digital signatures, encryption, and other security services to messages following the MIME standard. It uses PKCS #7 and #10 standards and public key cryptography to authenticate senders and ensure message integrity and confidentiality. S/MIME can secure email as well as other protocols using MIME, like HTTP. It provides services like digital signatures, encryption, and non-repudiation of origin.