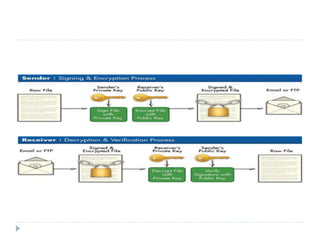
The document discusses various aspects of system security, specifically desktop, email, web, and database security. It highlights principles of security, common threats, and technologies used to safeguard information, emphasizing the need for a comprehensive approach to preserve confidentiality, integrity, and availability of data. Key topics include password management, encryption methods (S/MIME, PGP), and secure electronic transactions.