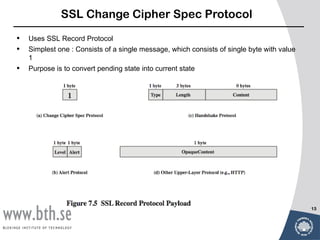
The document provides an overview of web security concepts including:
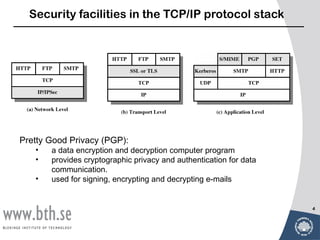
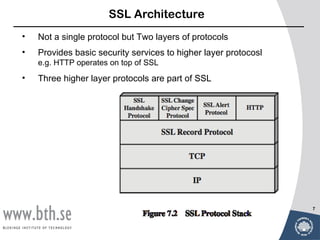
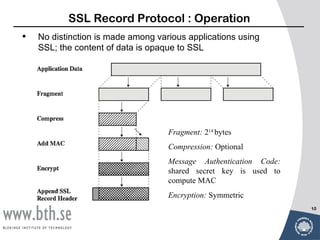
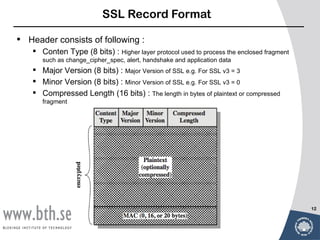
- Secure Socket Layer (SSL) and Transport Layer Security (TLS) which provide data encryption, server authentication, integrity and confidentiality over TCP.
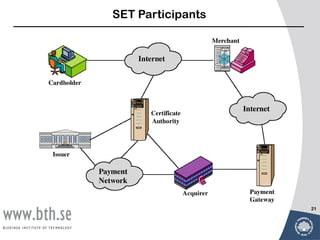
- Secure Electronic Transaction (SET) which defines security protocols and formats to protect credit card transactions on the internet involving cardholders, merchants, issuers, acquirers and certificate authorities.
- The SSL/TLS handshake protocol establishes a secure connection between a client and server by authenticating the server, negotiating encryption algorithms, and exchanging keys to encrypt further communication.