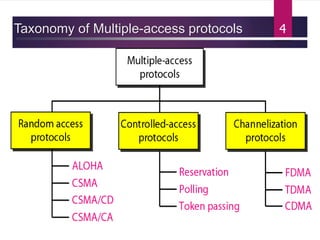
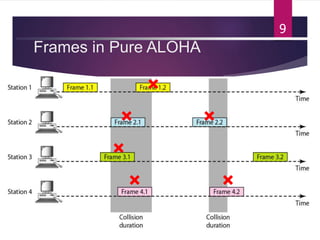
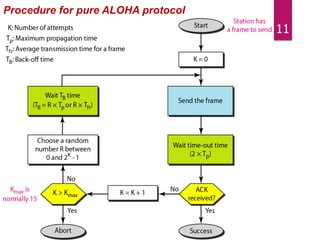
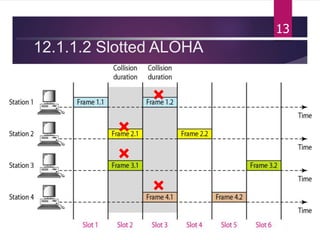
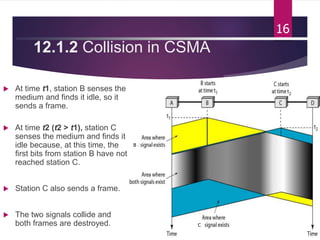
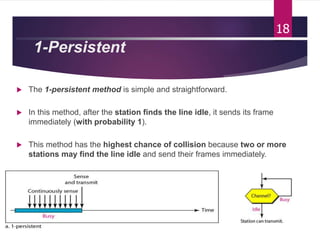
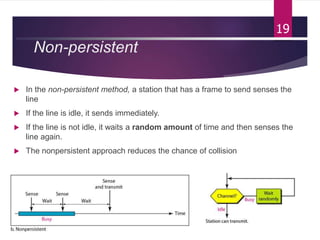
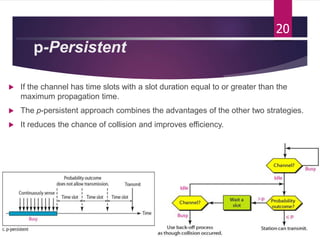
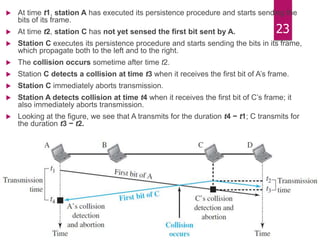
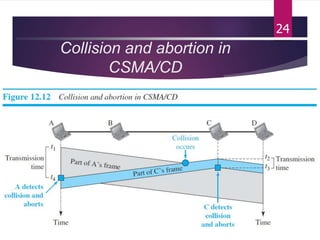
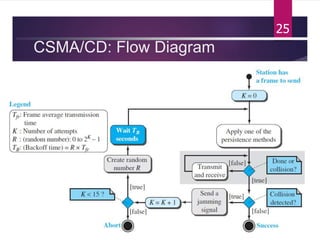
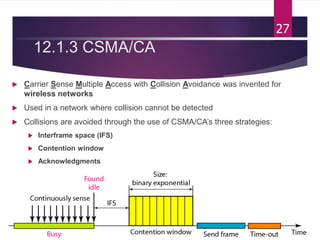
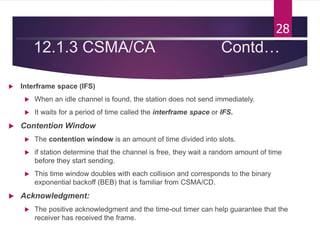
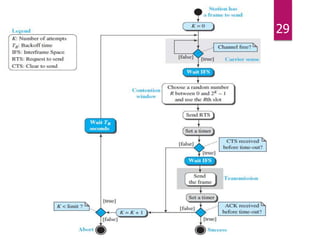
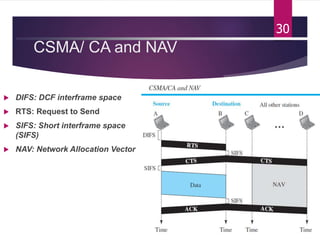
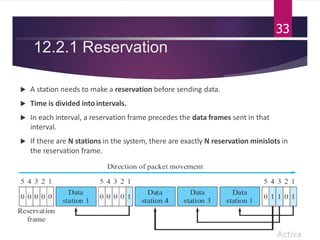
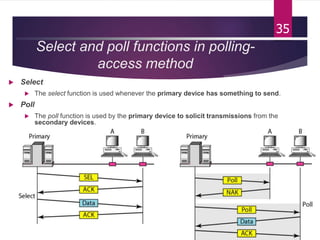
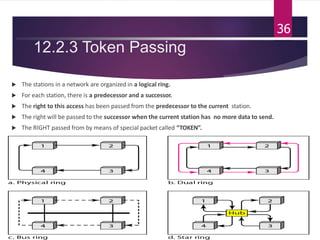
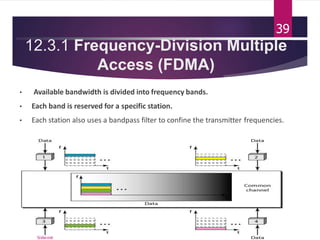
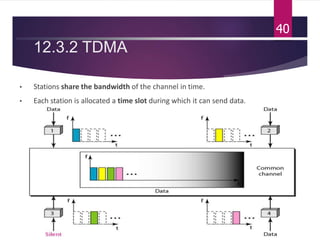
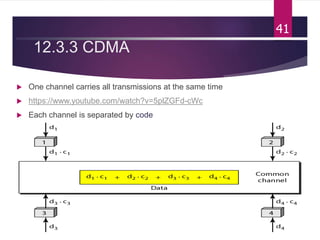
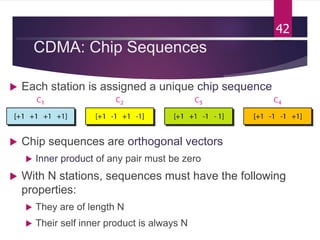
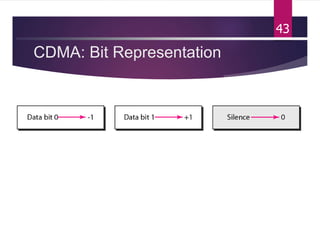
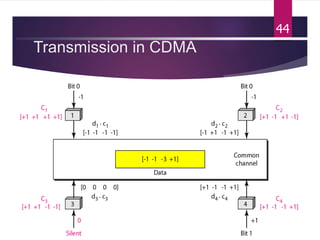
The document outlines various media access control (MAC) protocols, which are critical for managing how multiple stations access a shared communication medium without conflict. It covers random access methods like ALOHA and CSMA, controlled access methods, and channelization techniques such as FDMA, TDMA, and CDMA. Each method is designed to reduce collisions and manage data transmission effectively in multipoint networks.