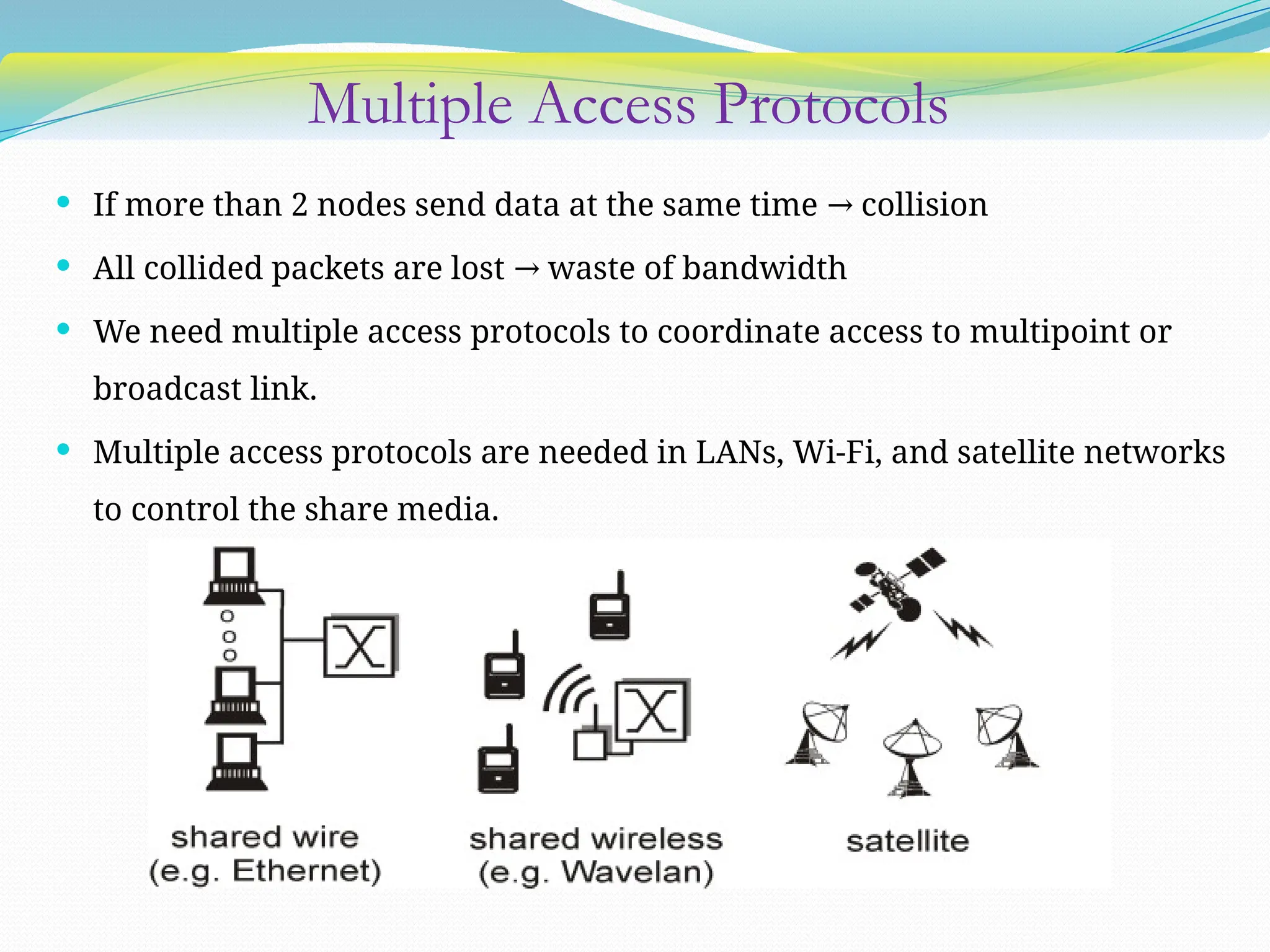
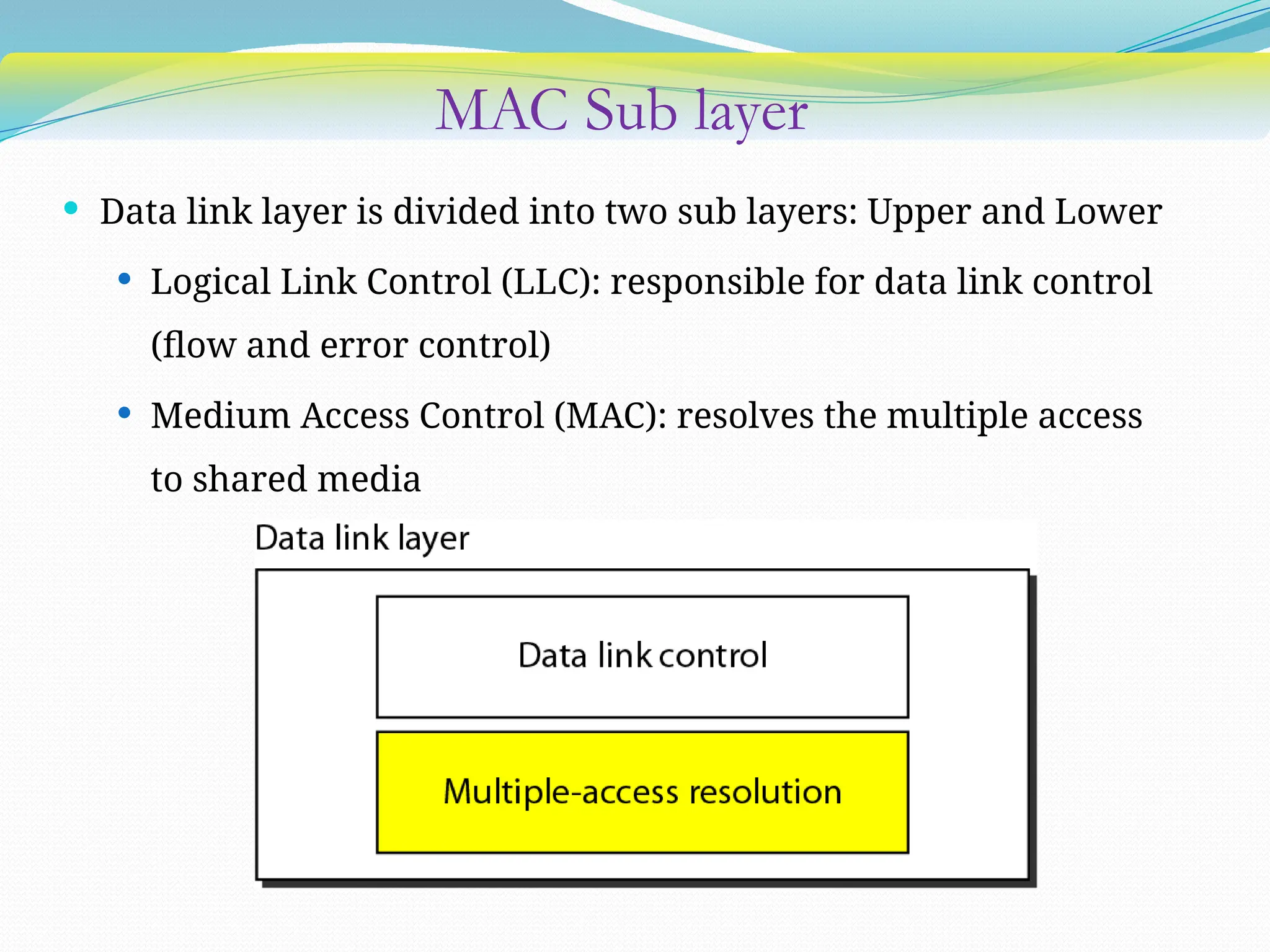
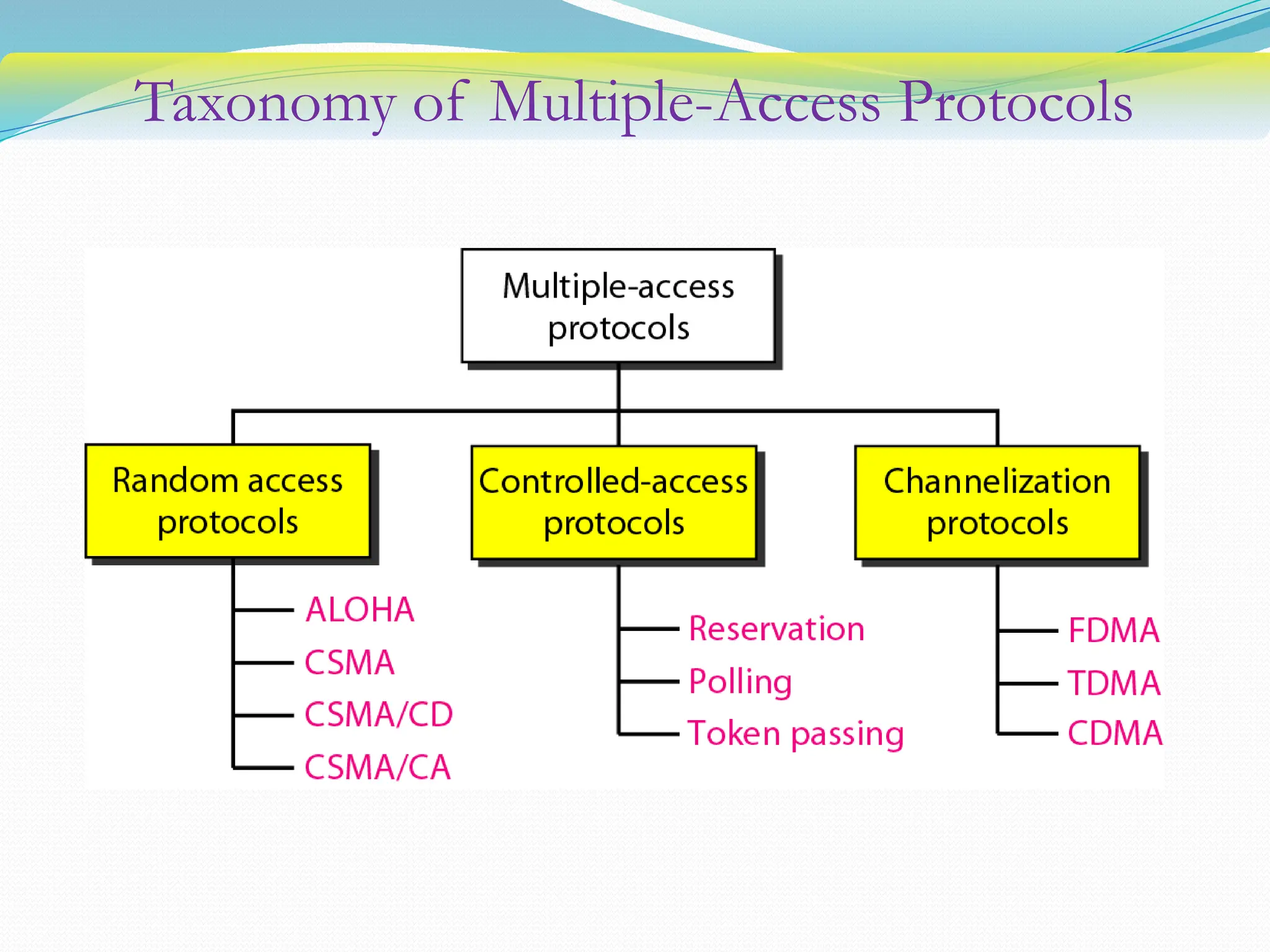
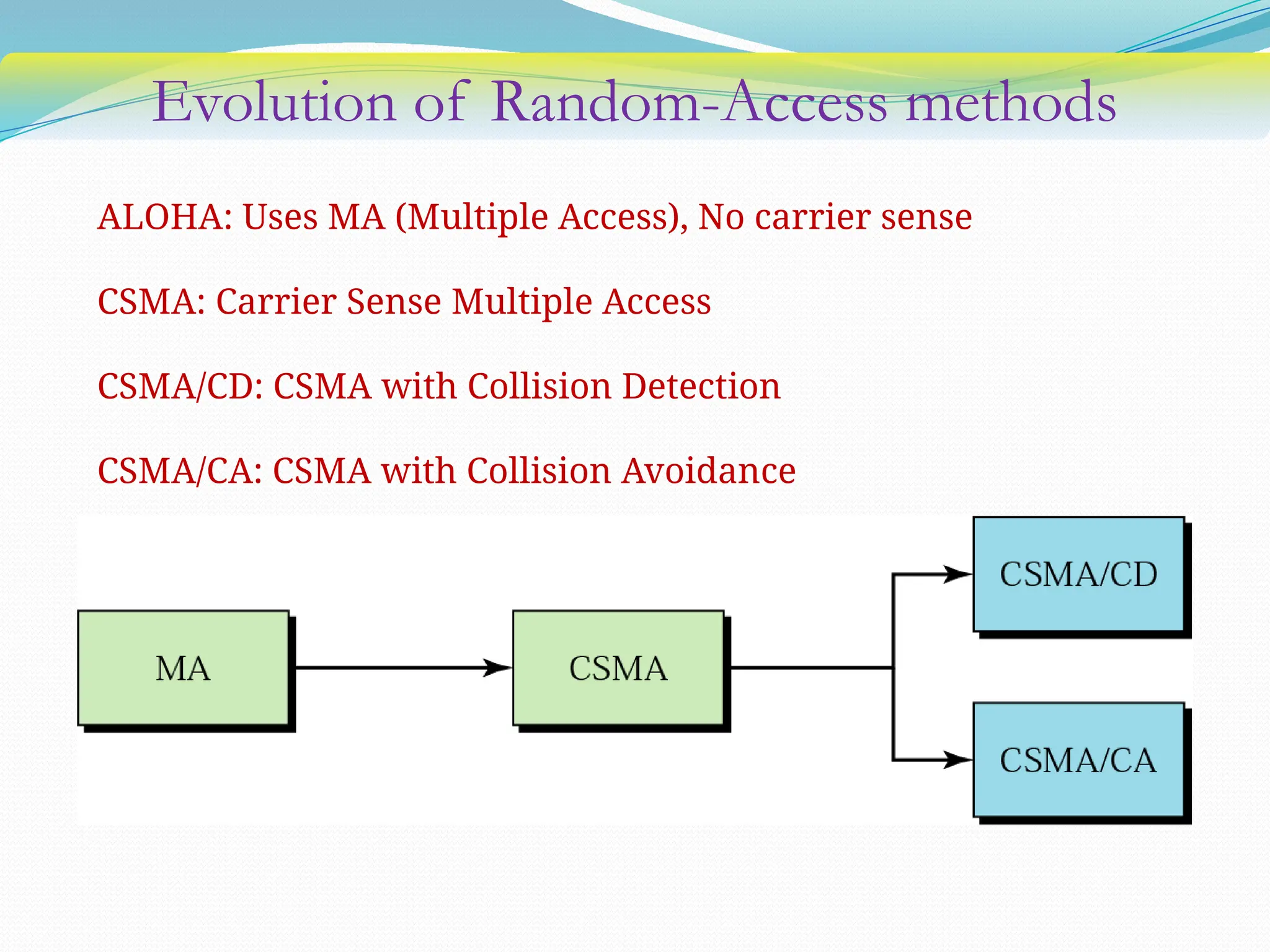
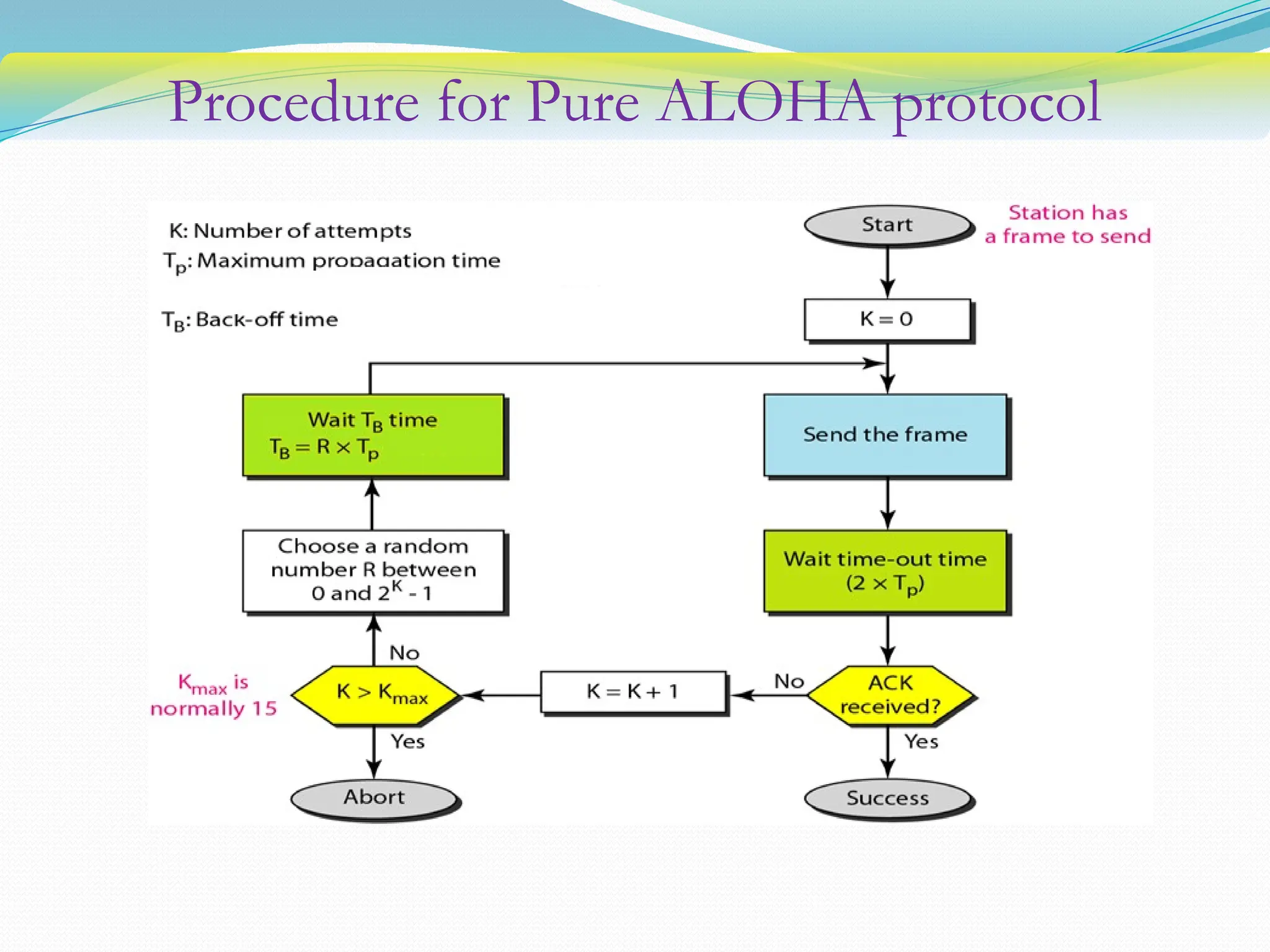
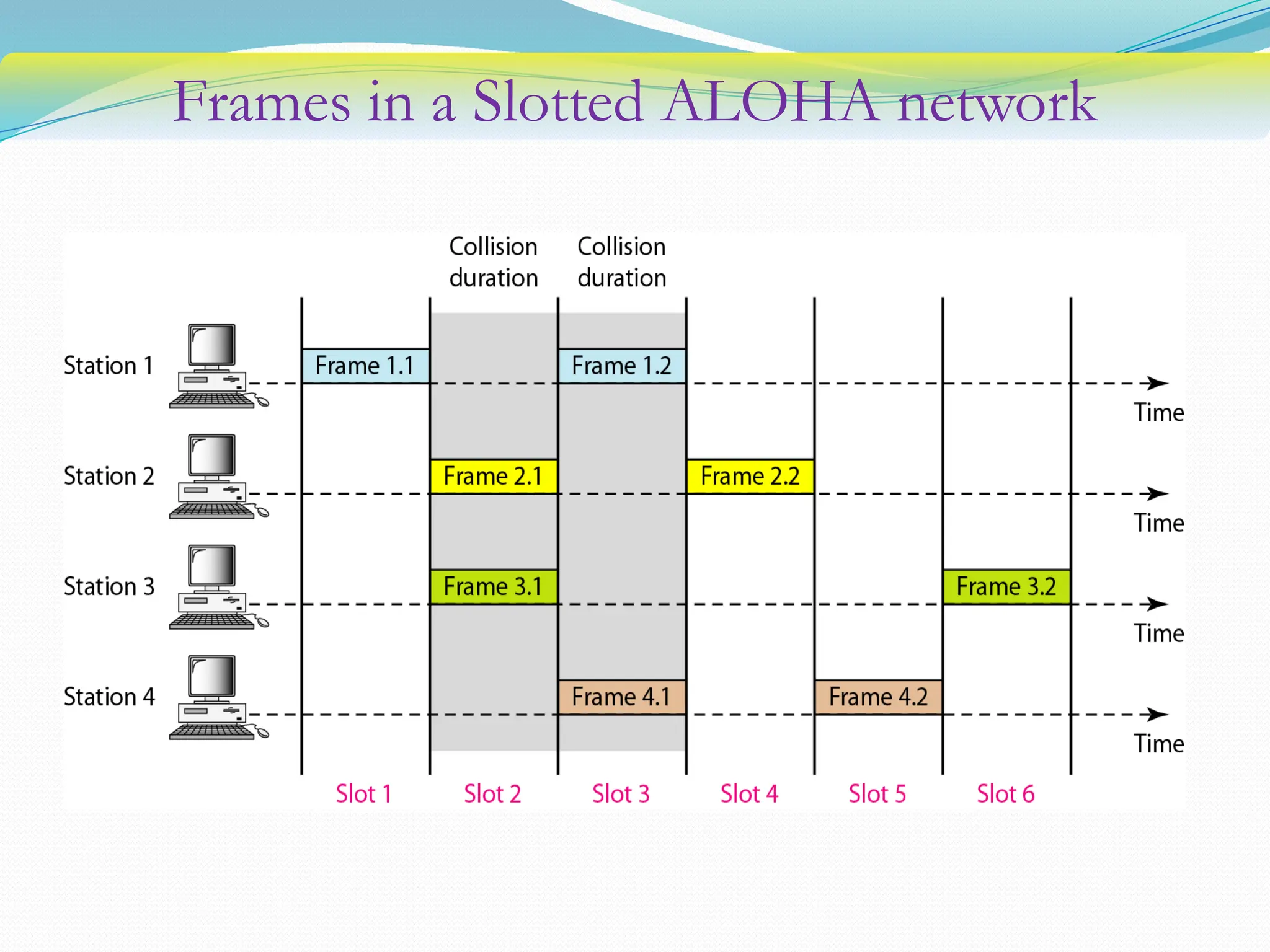
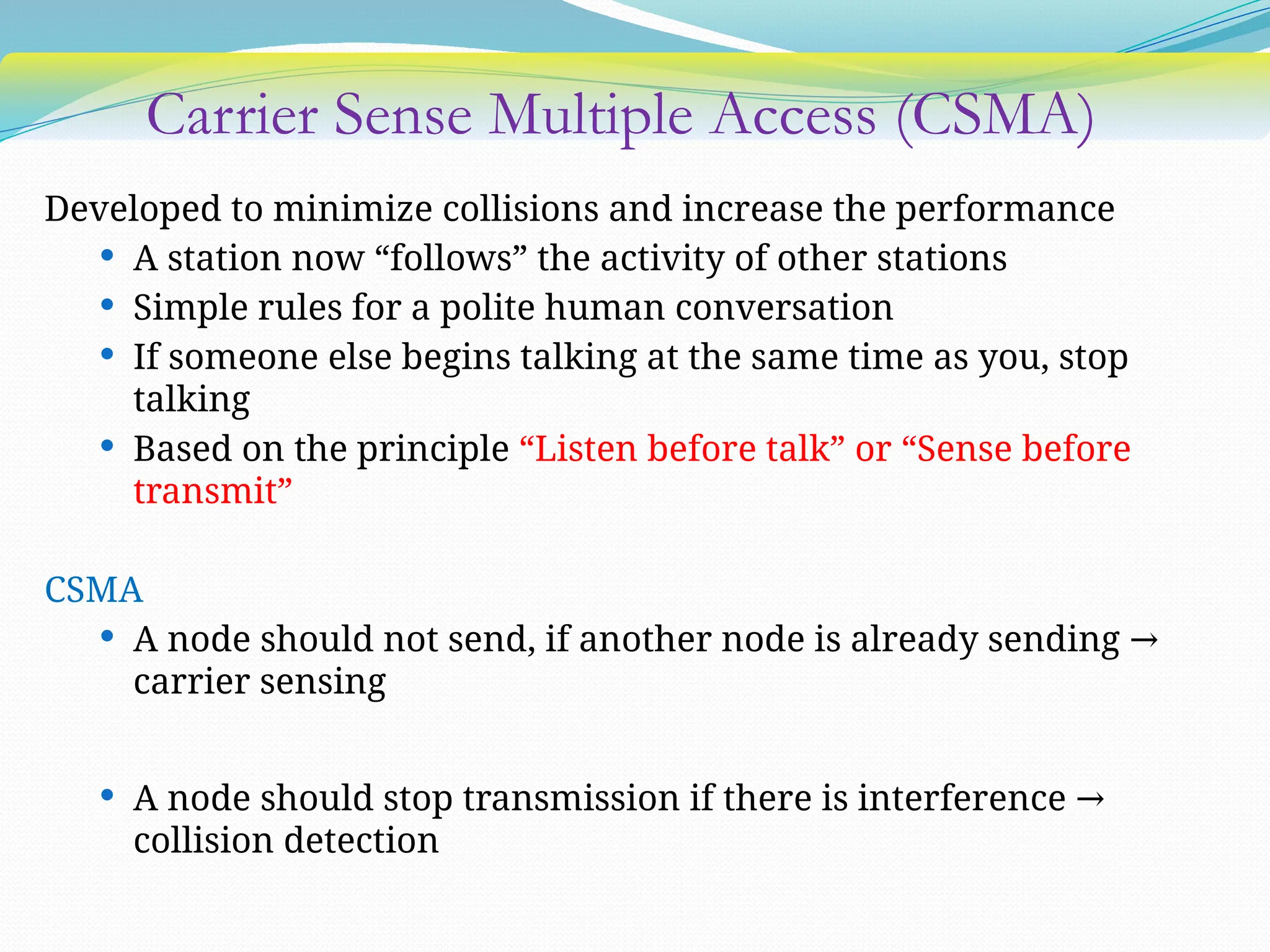
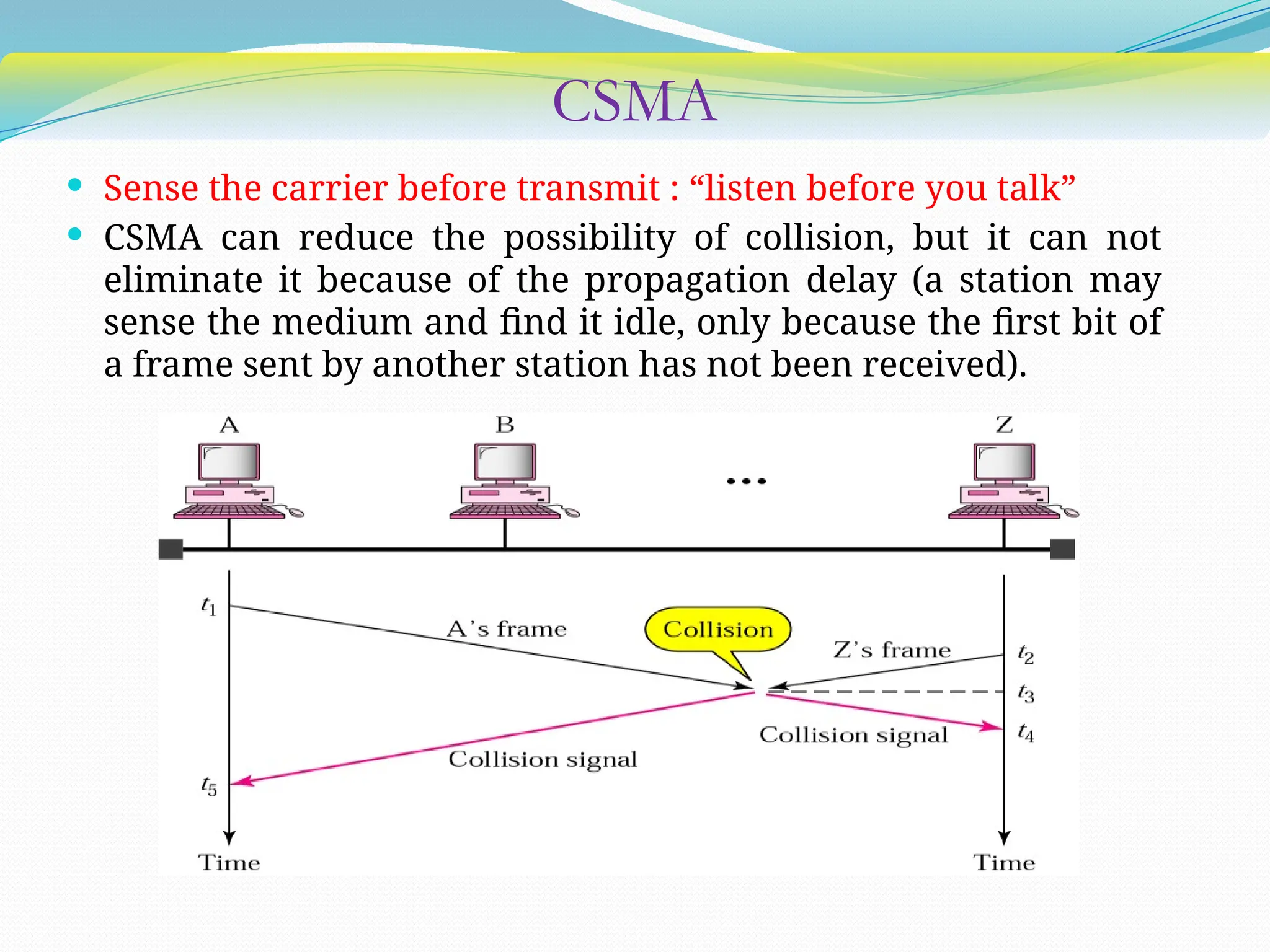
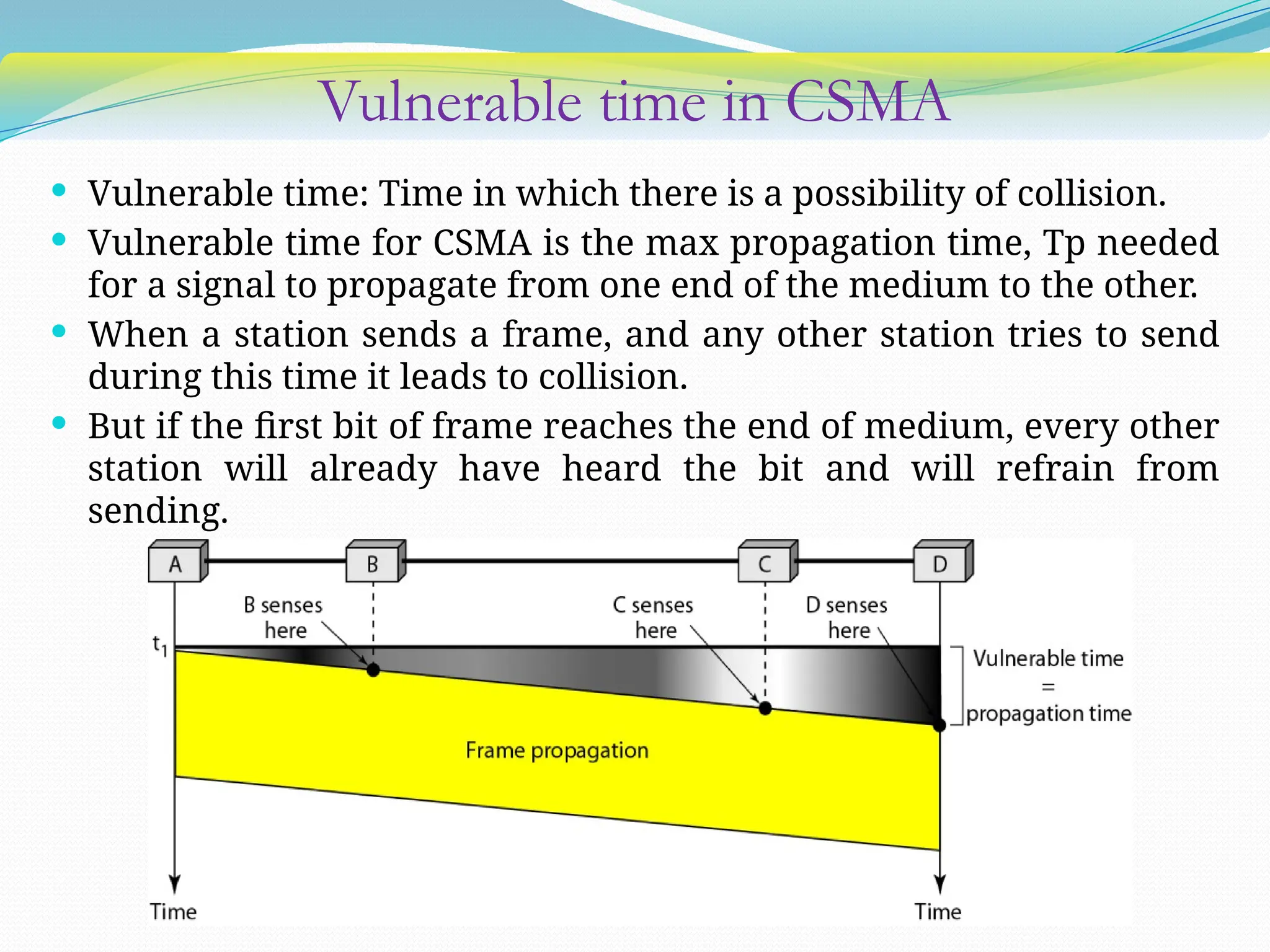
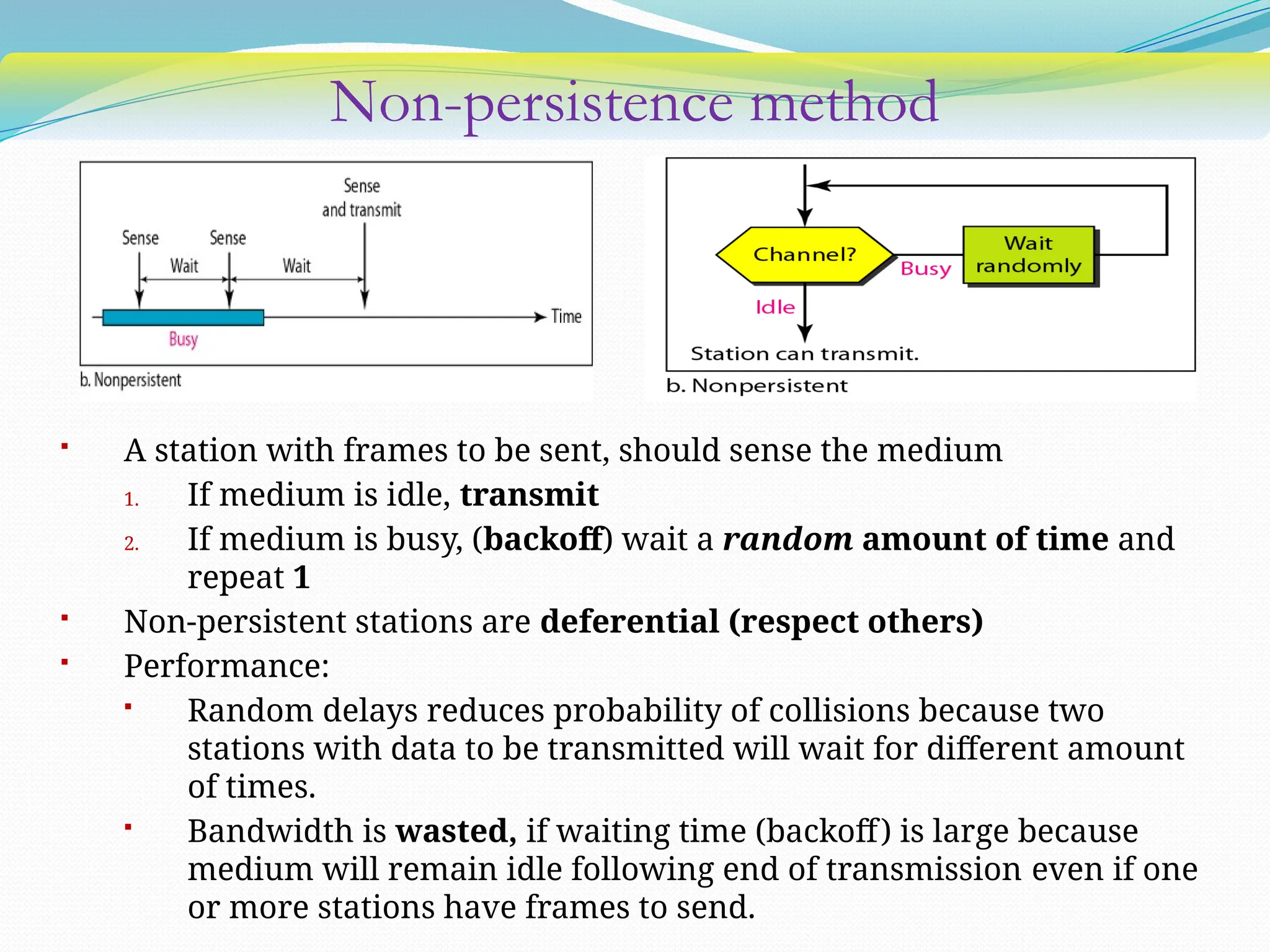
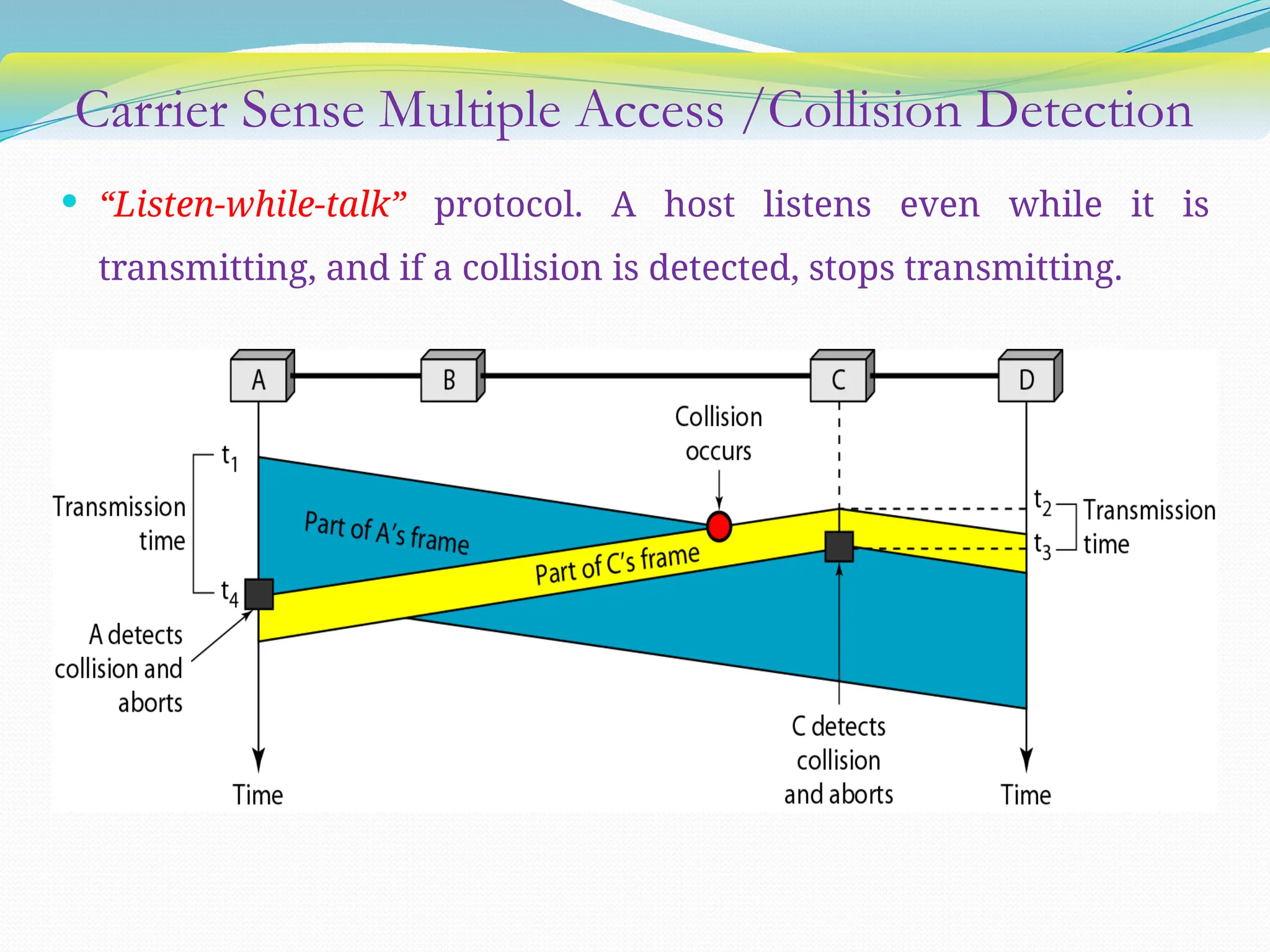
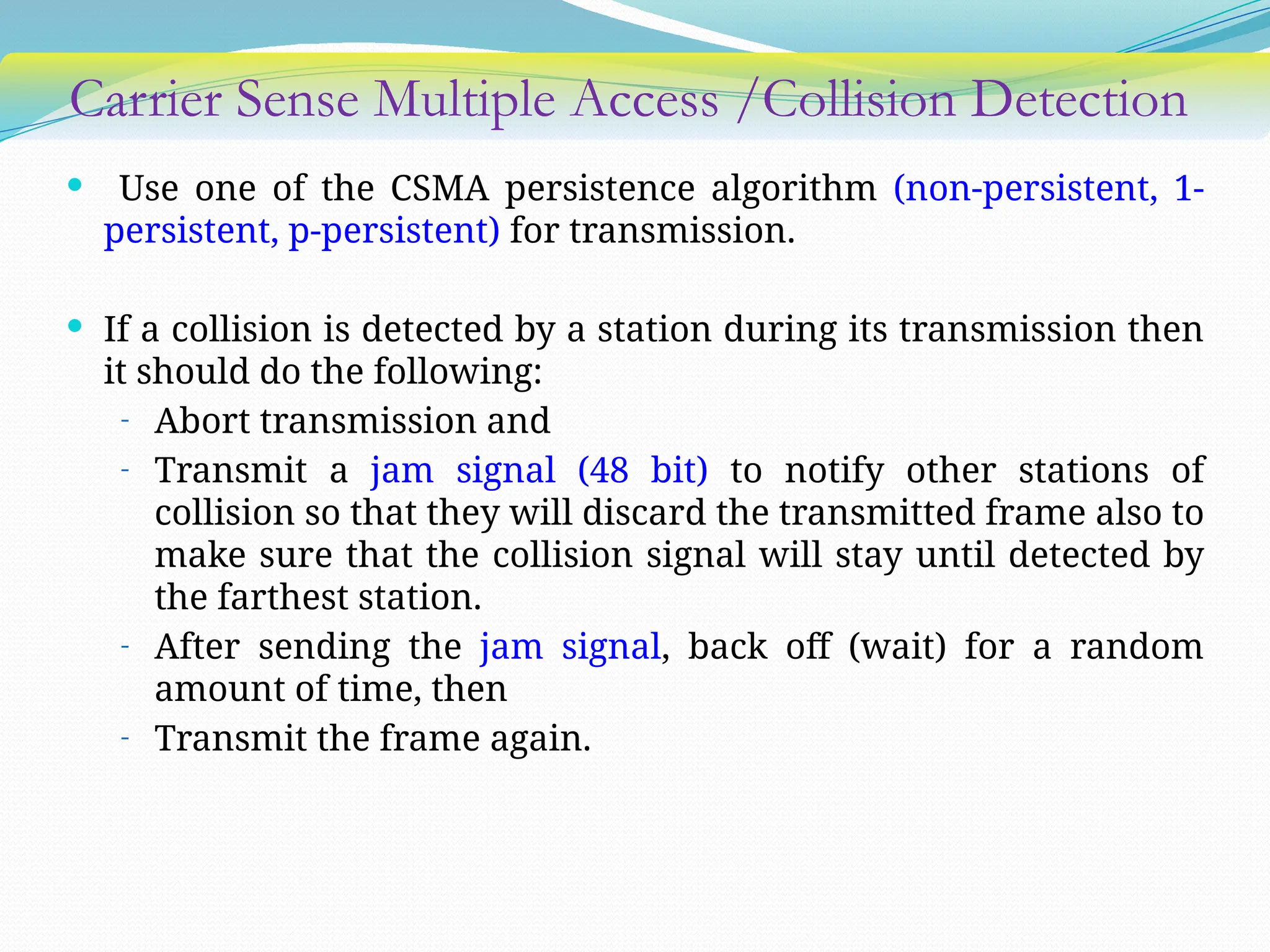
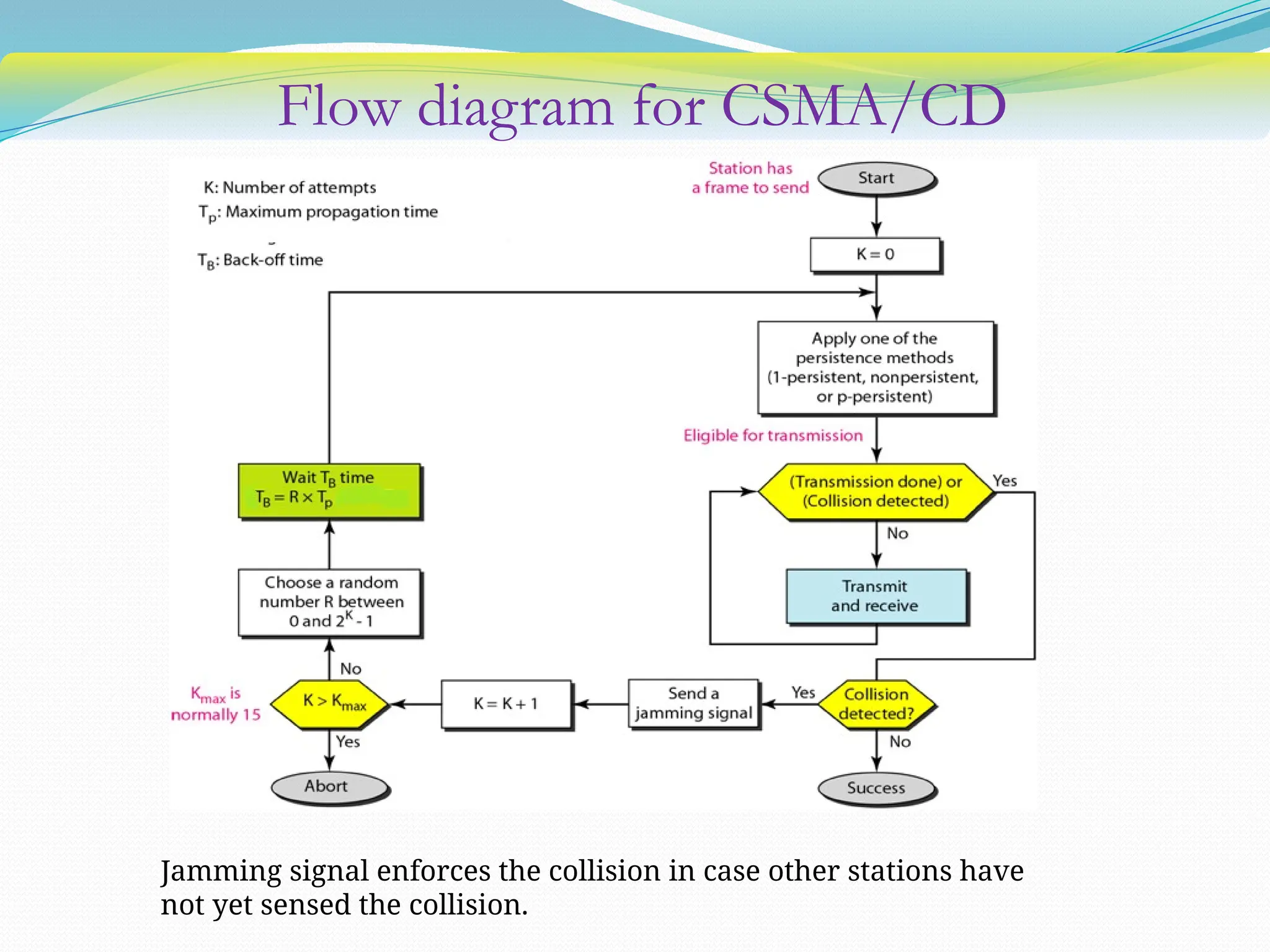
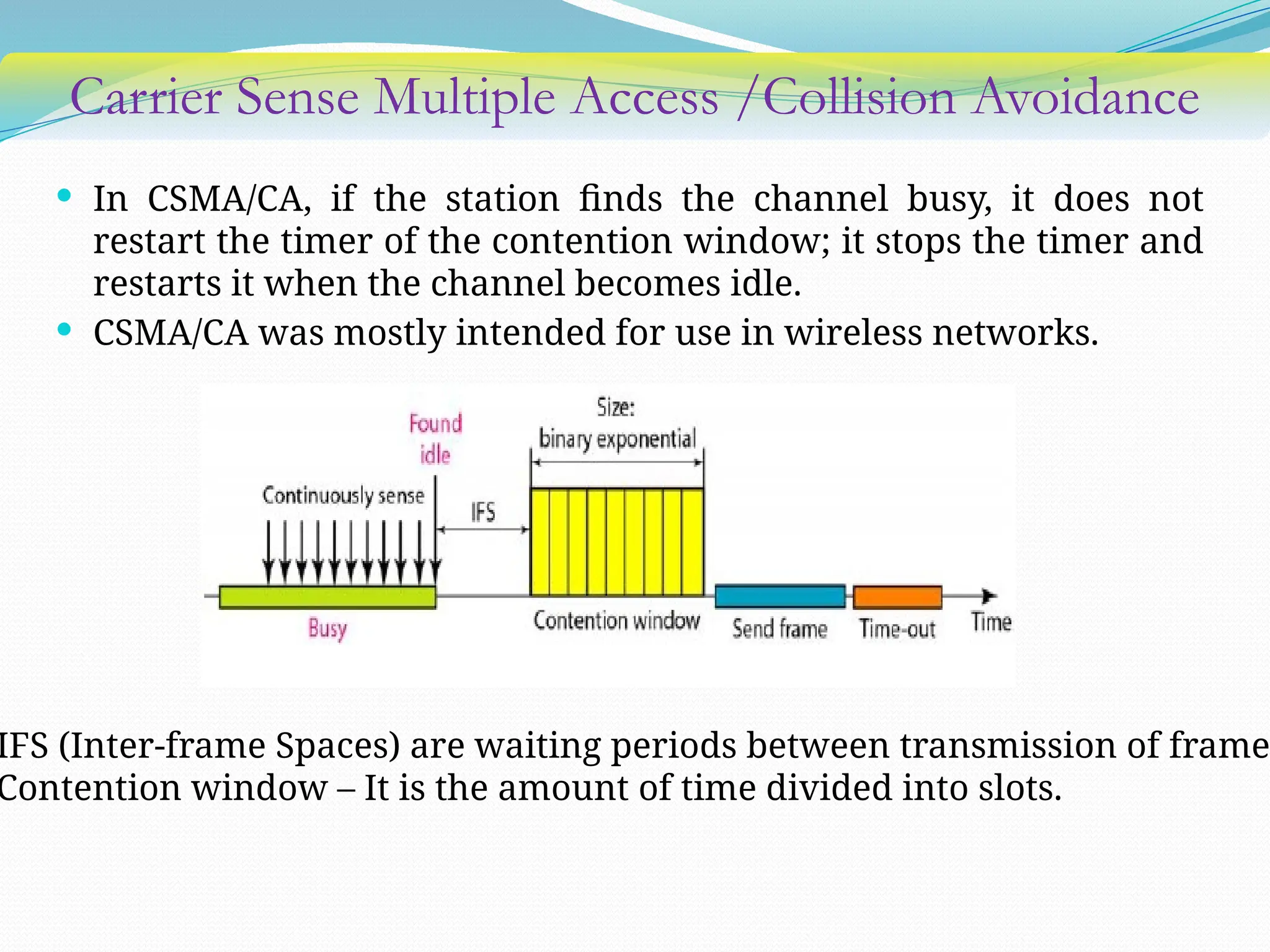
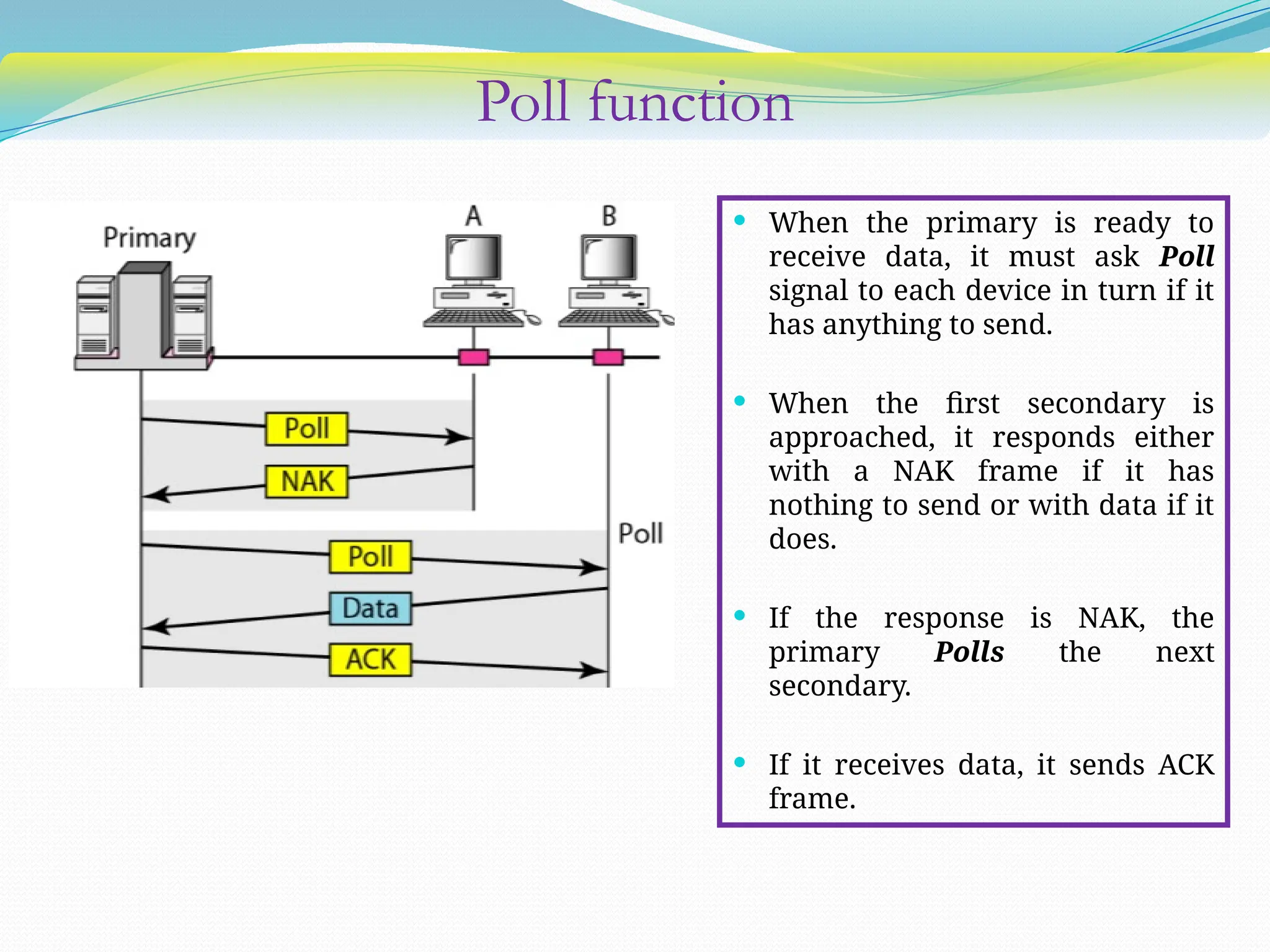
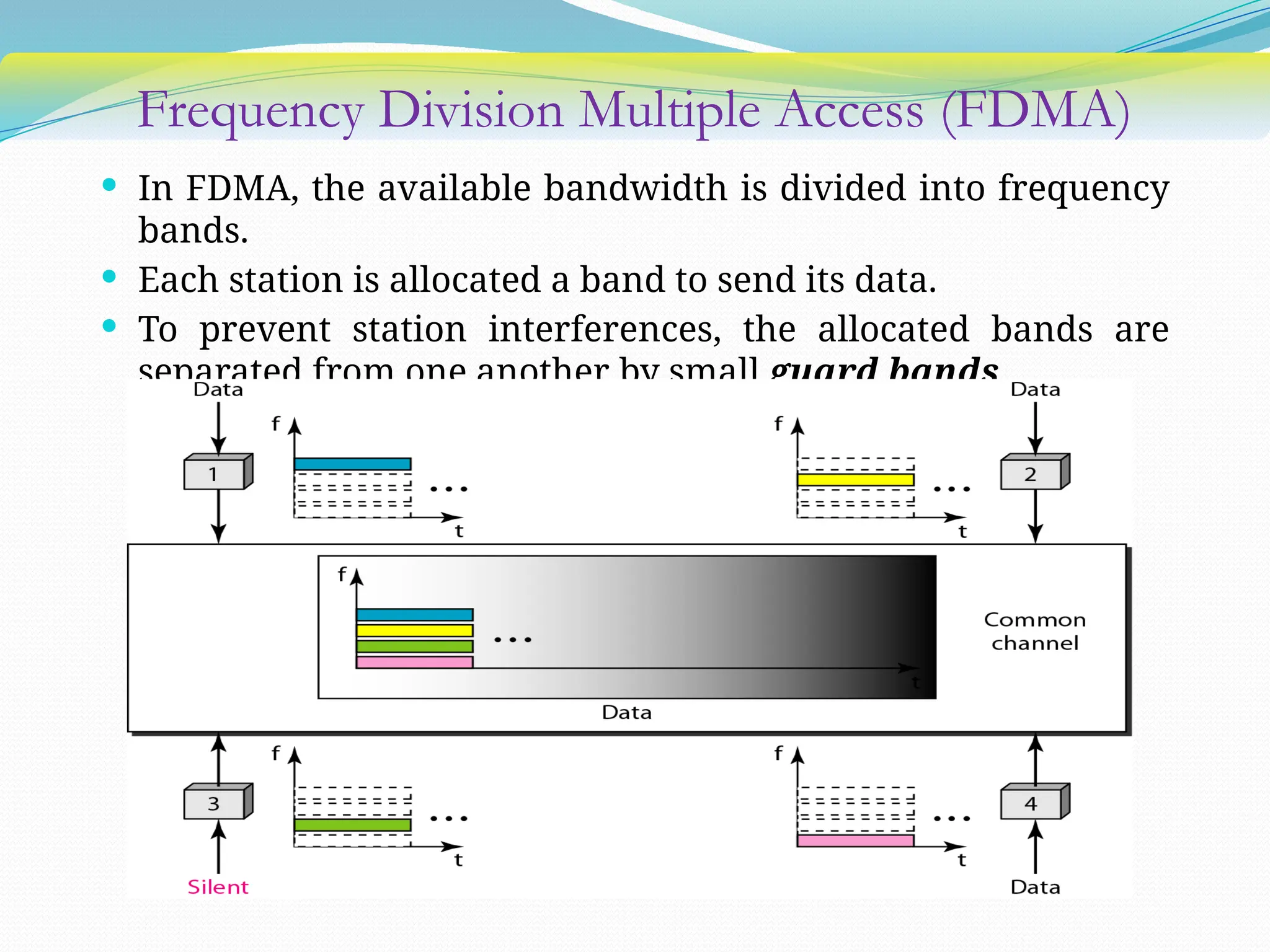
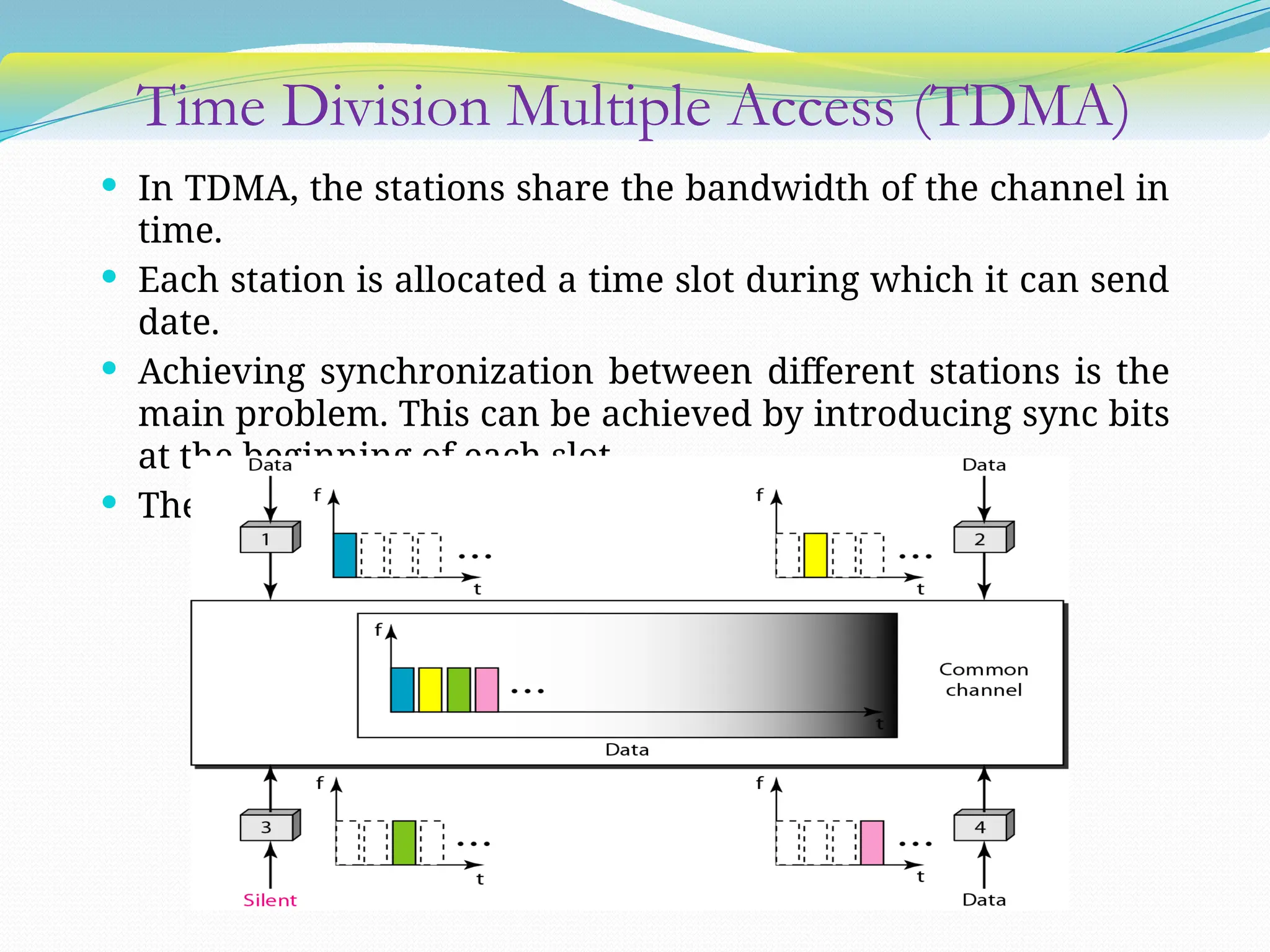
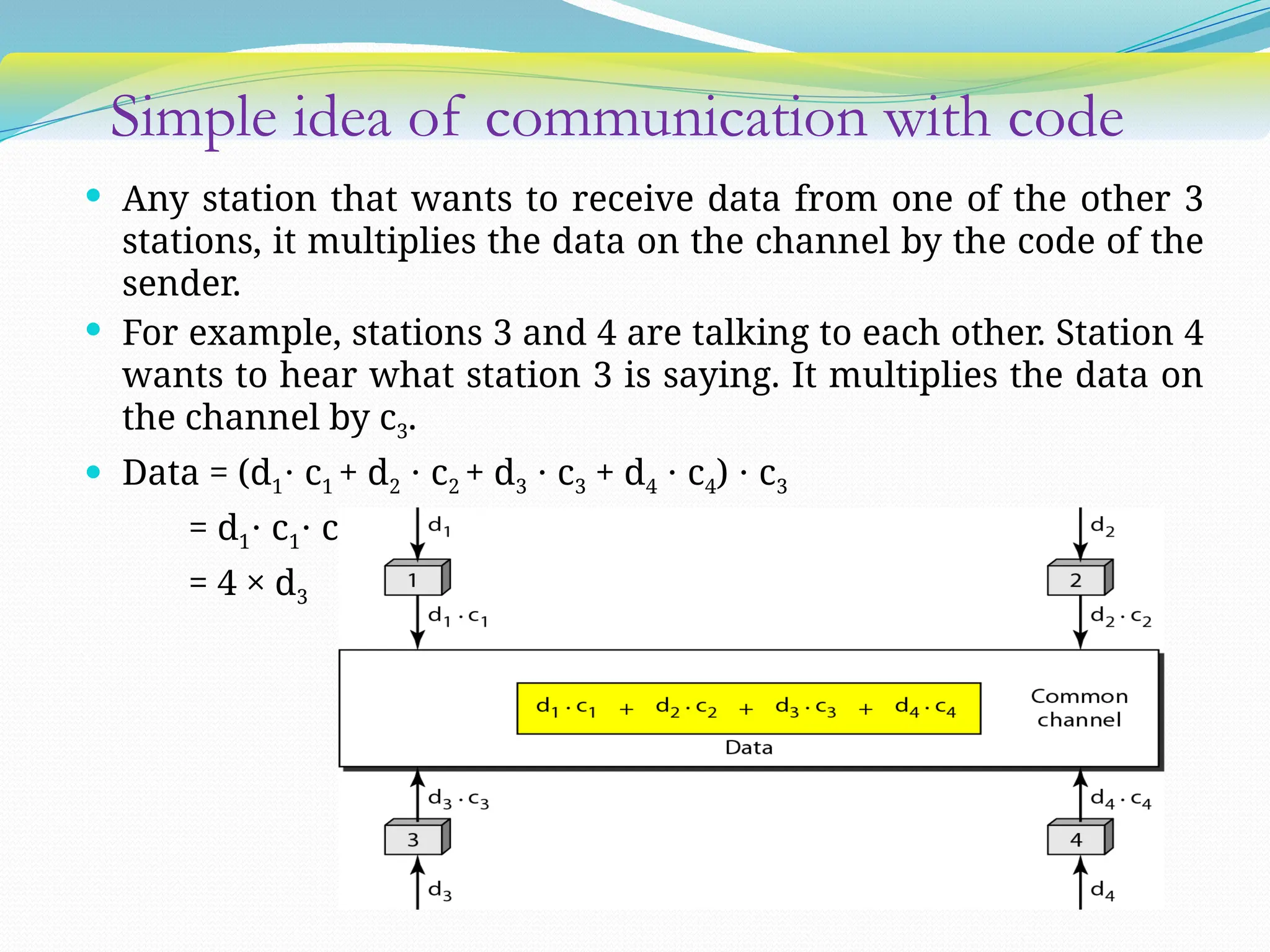
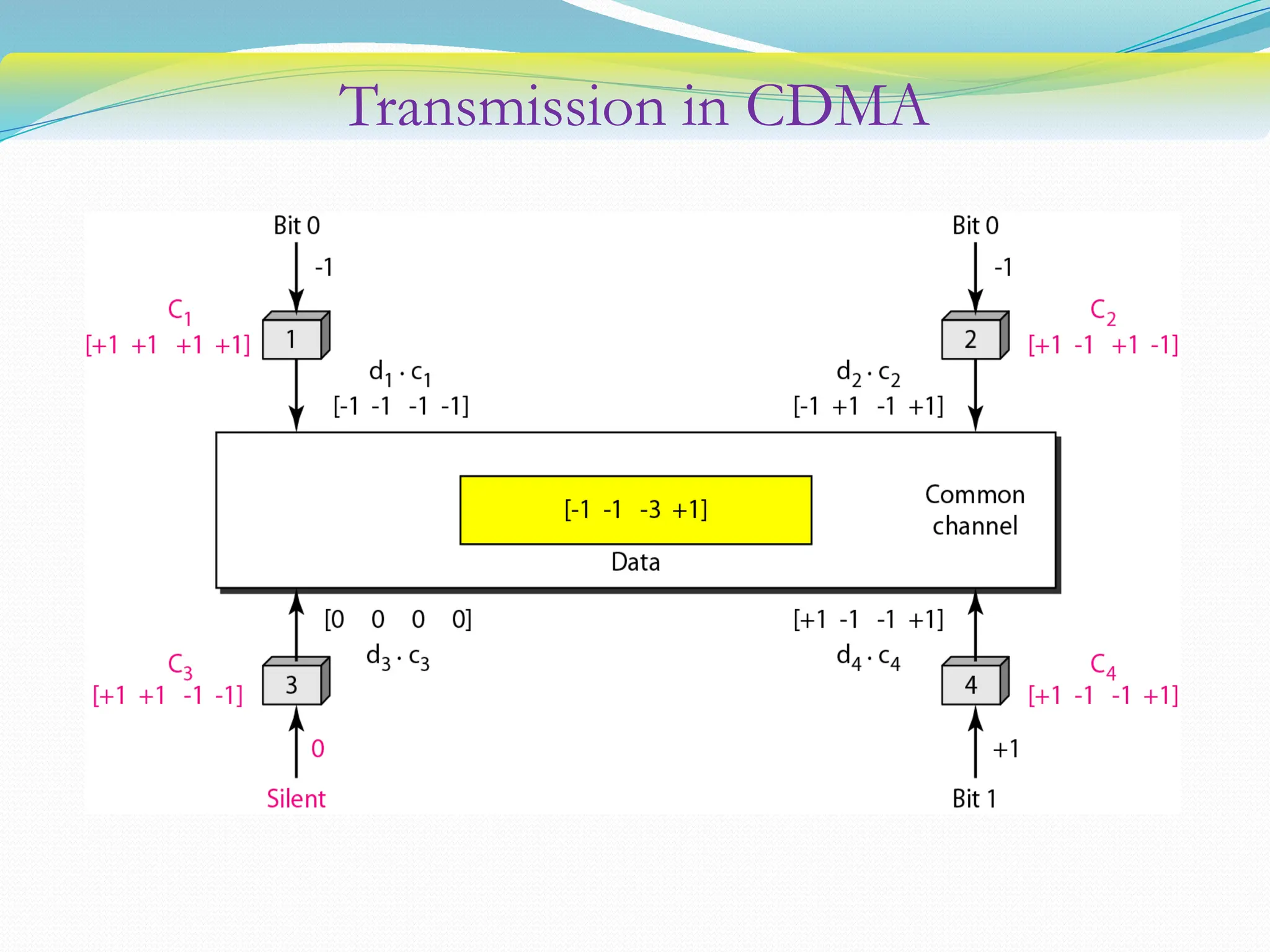
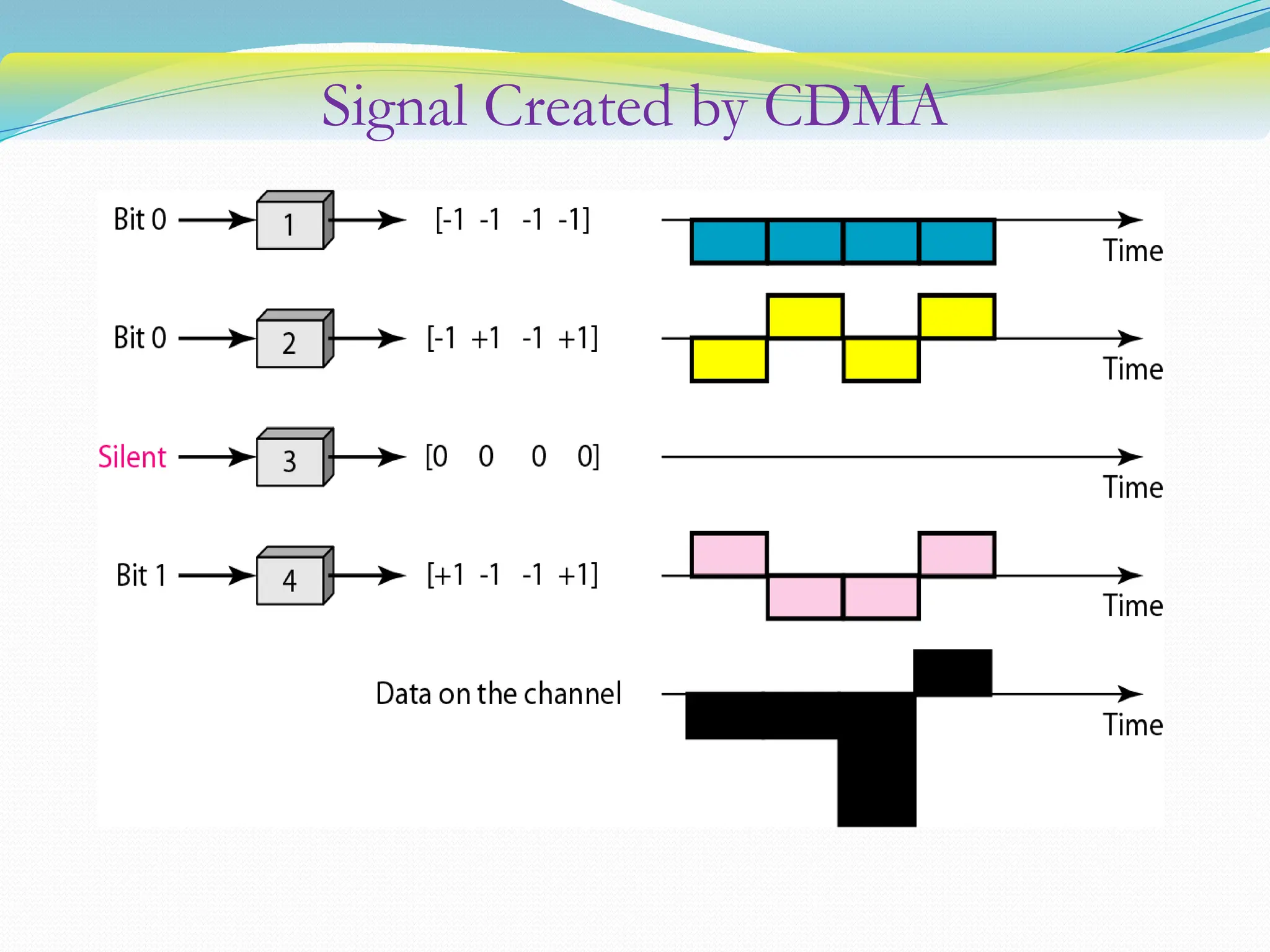
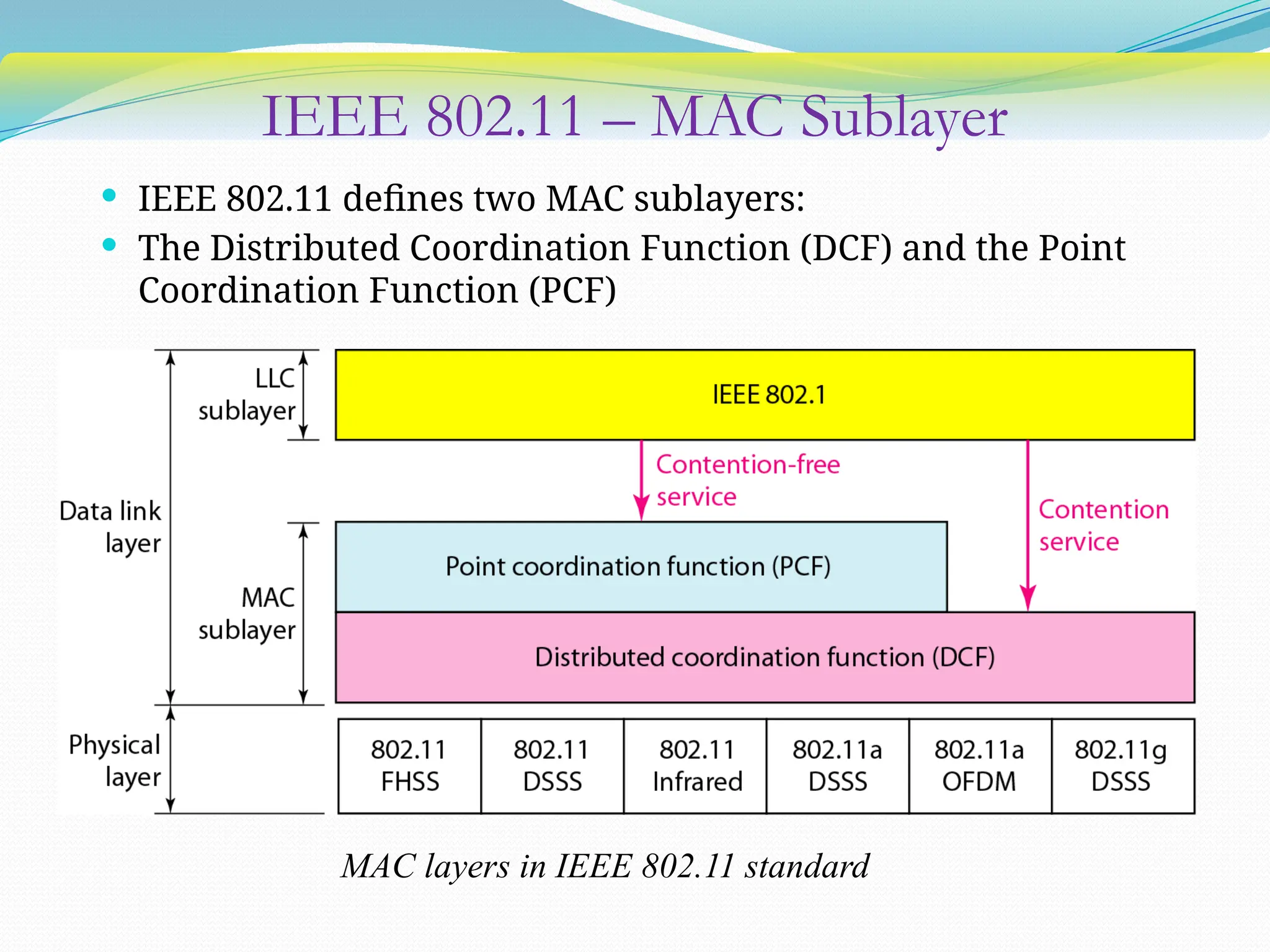
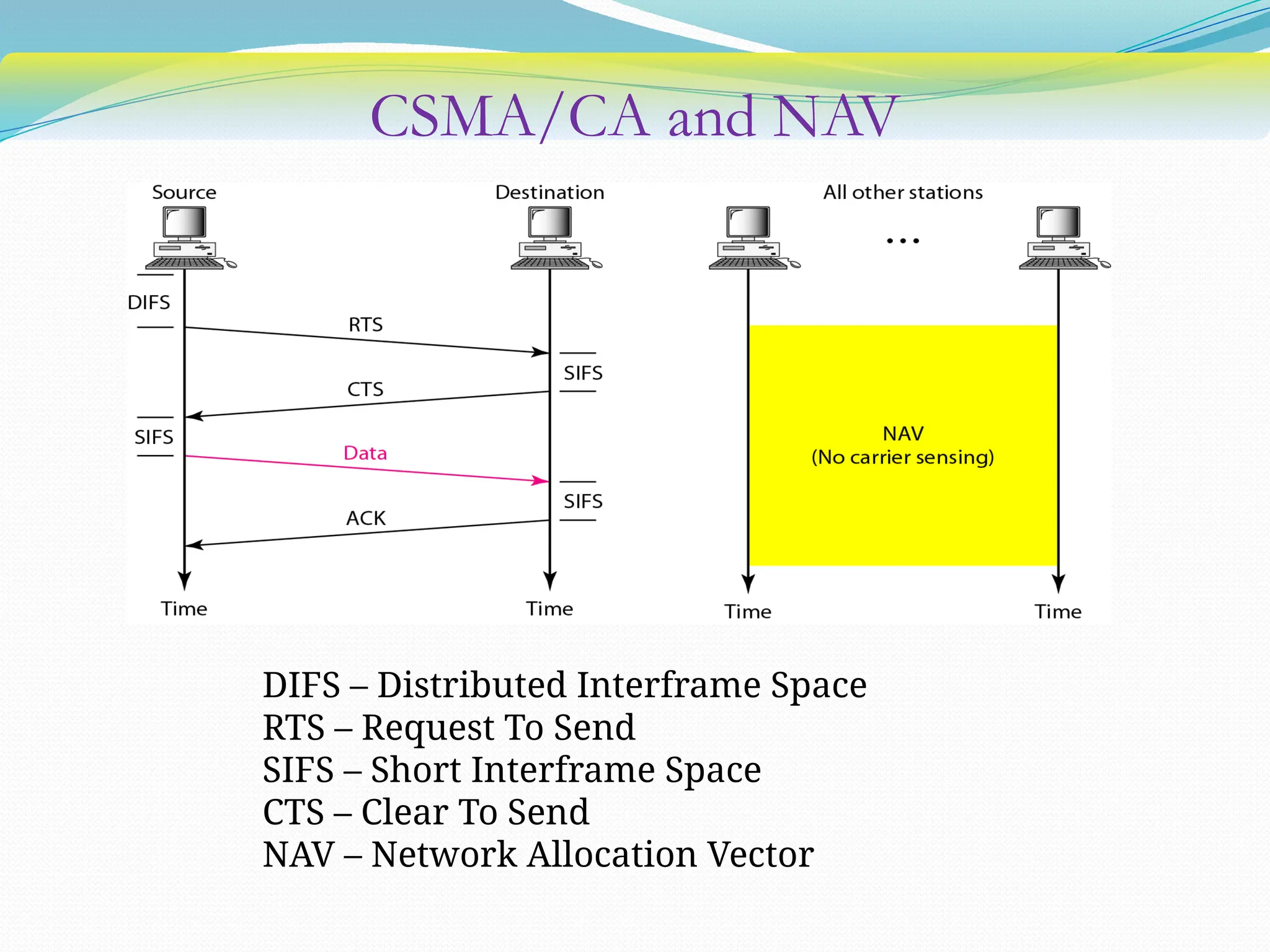
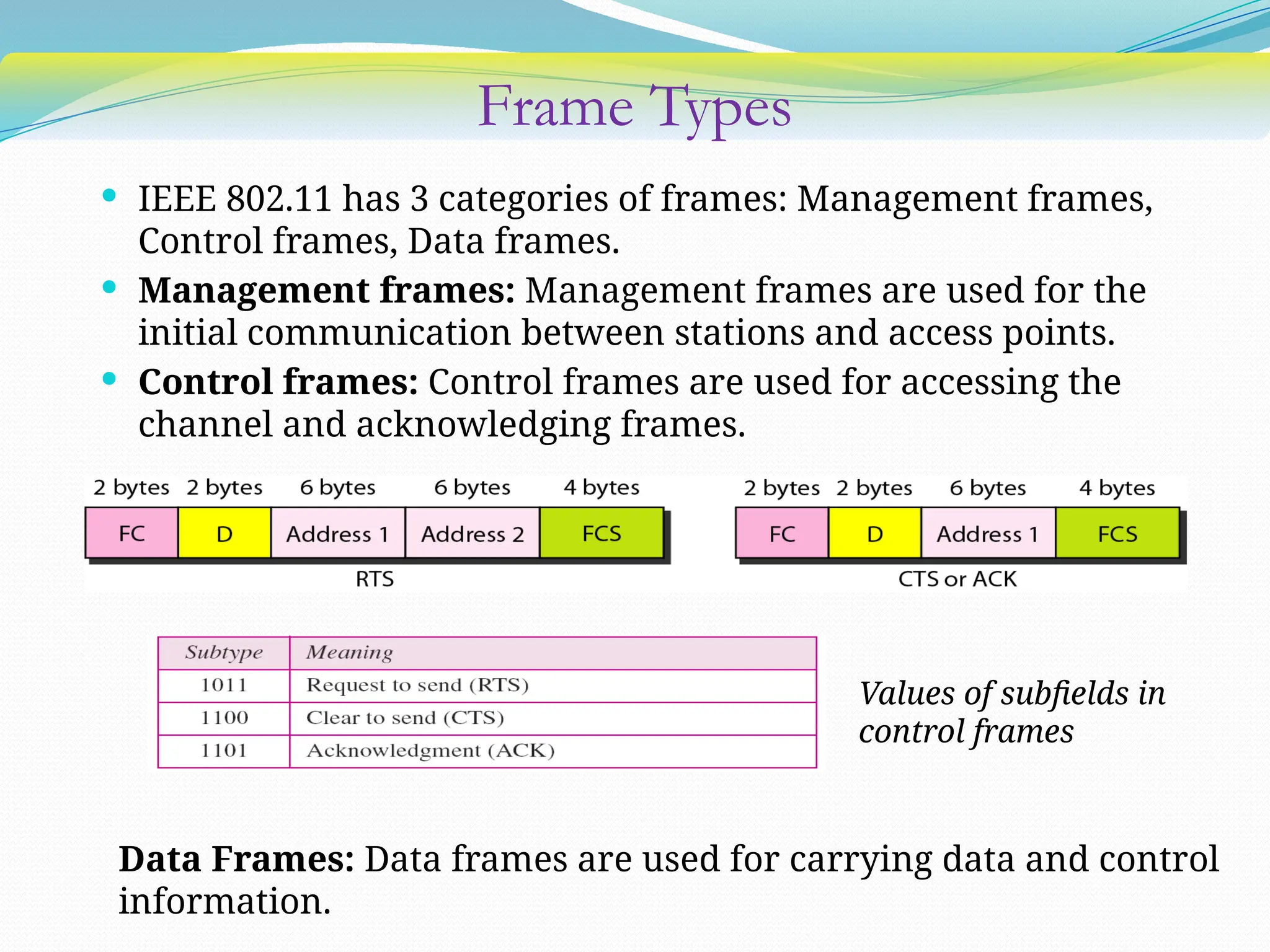
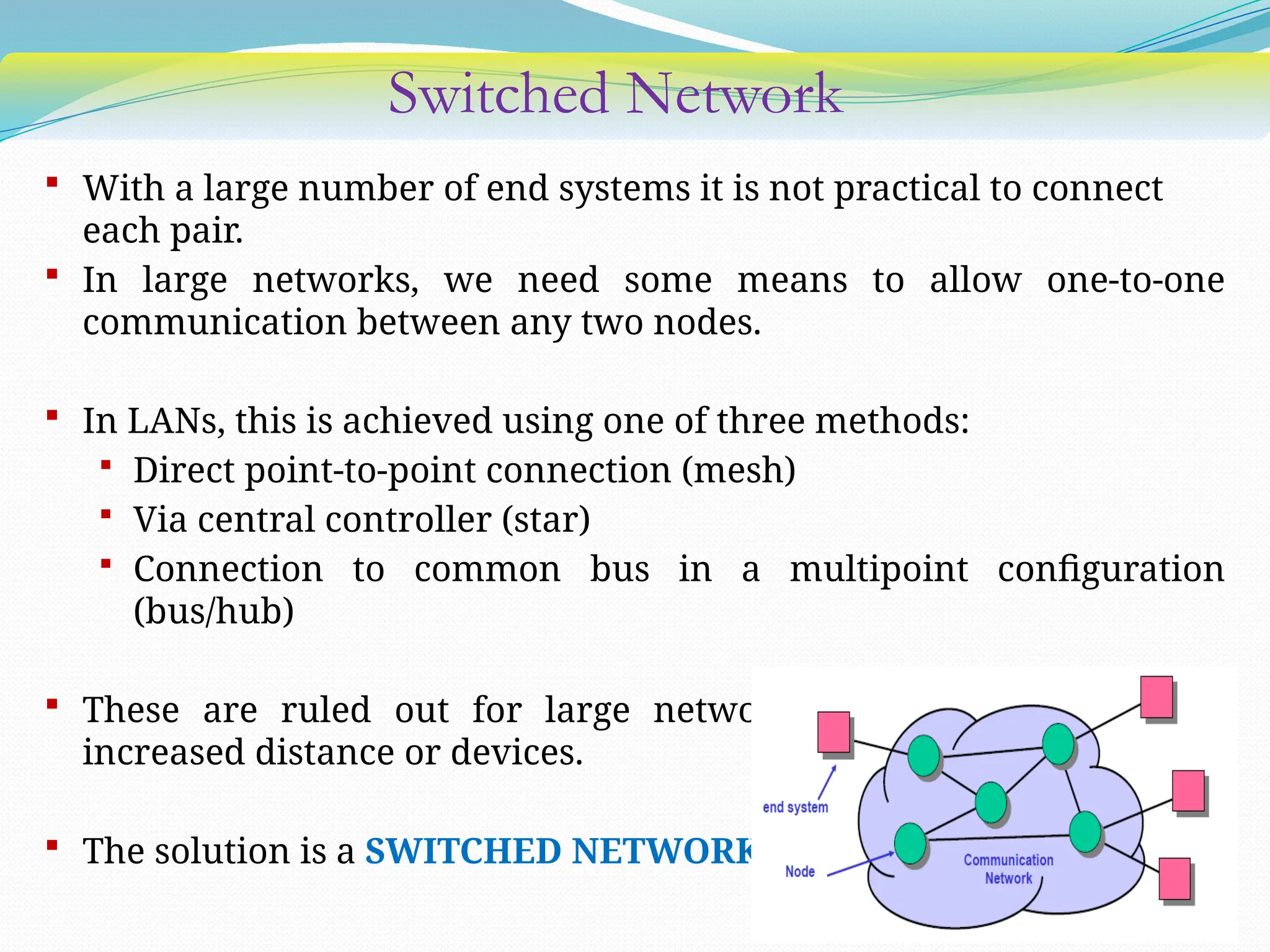
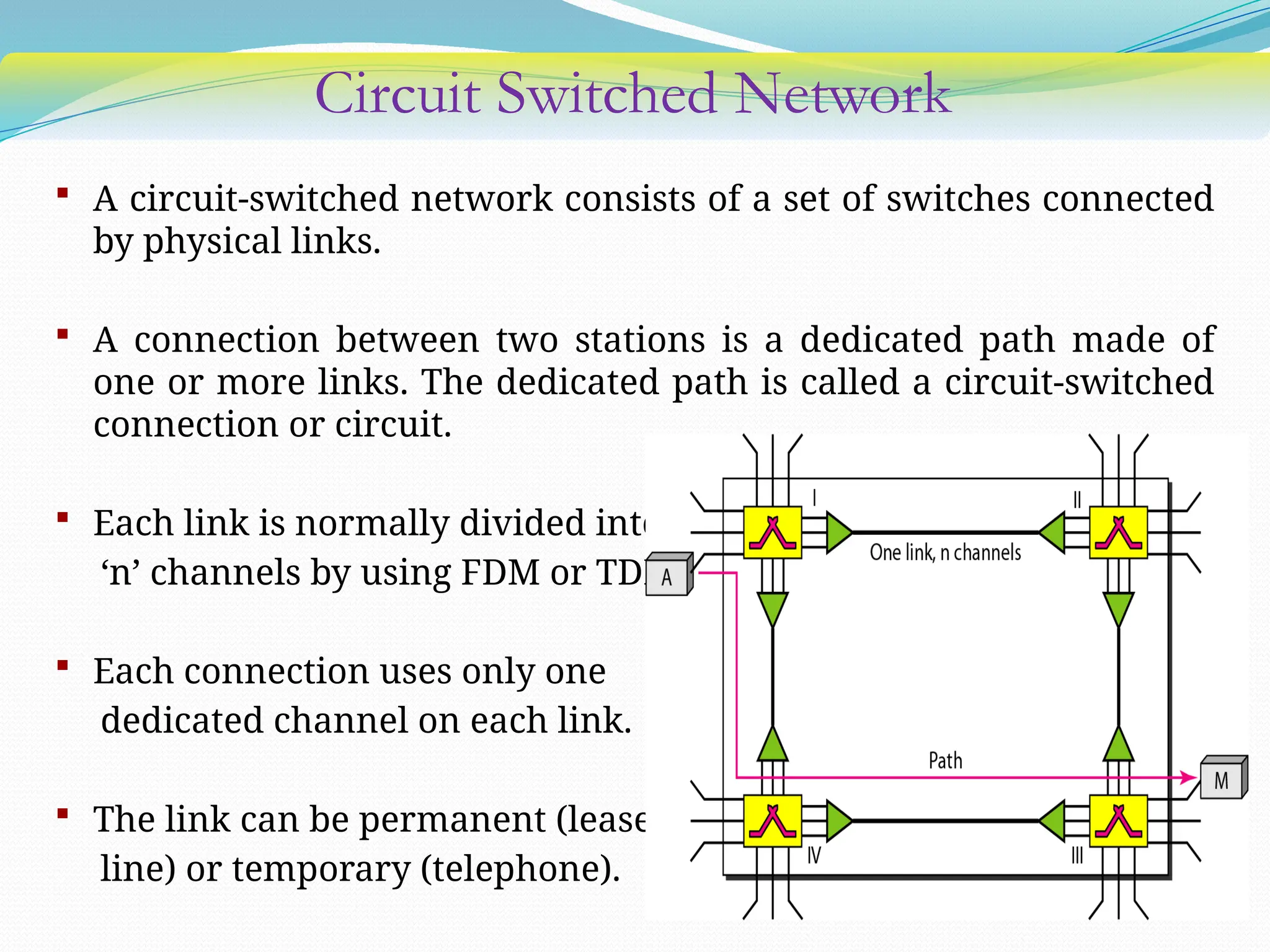
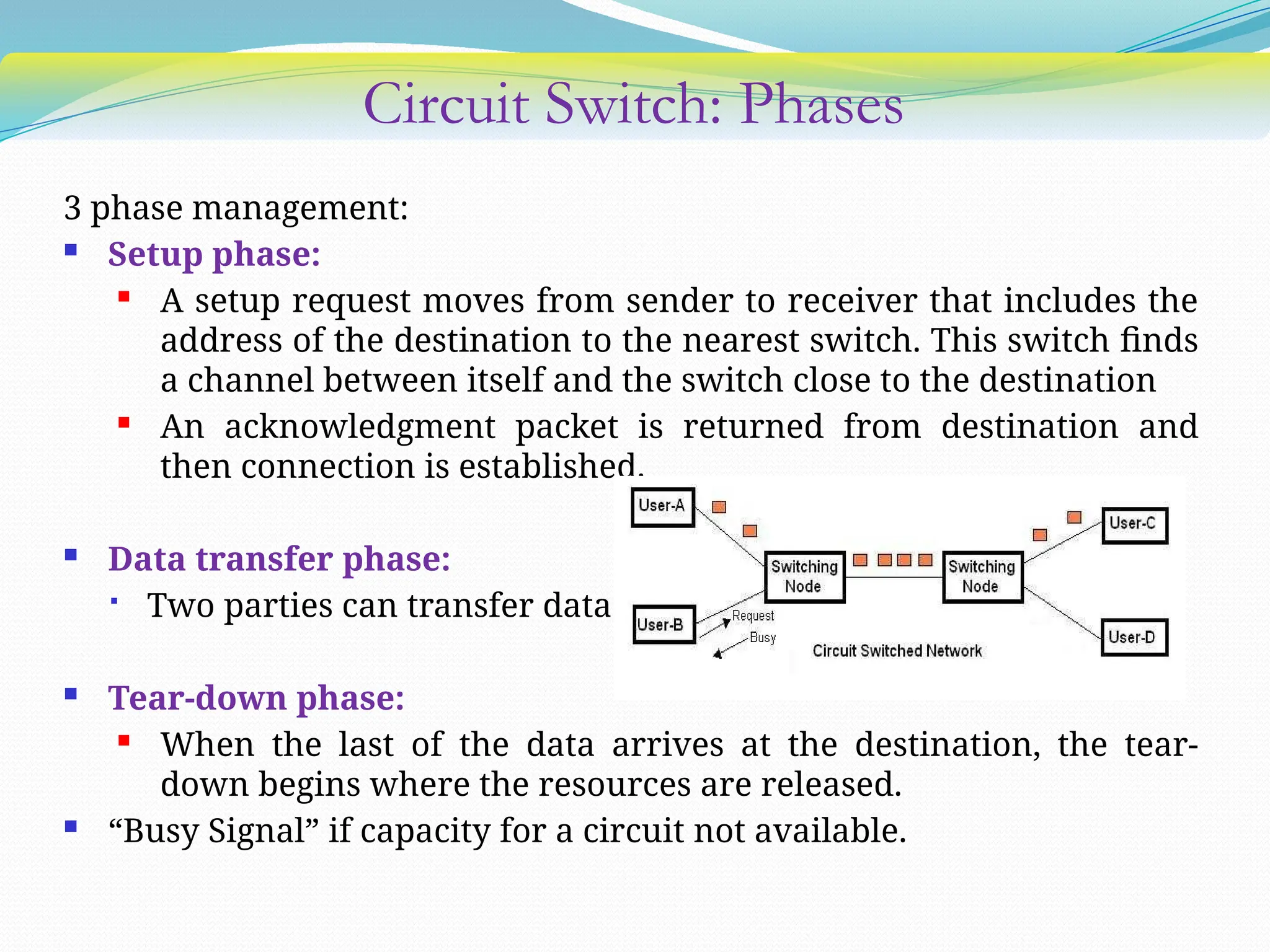
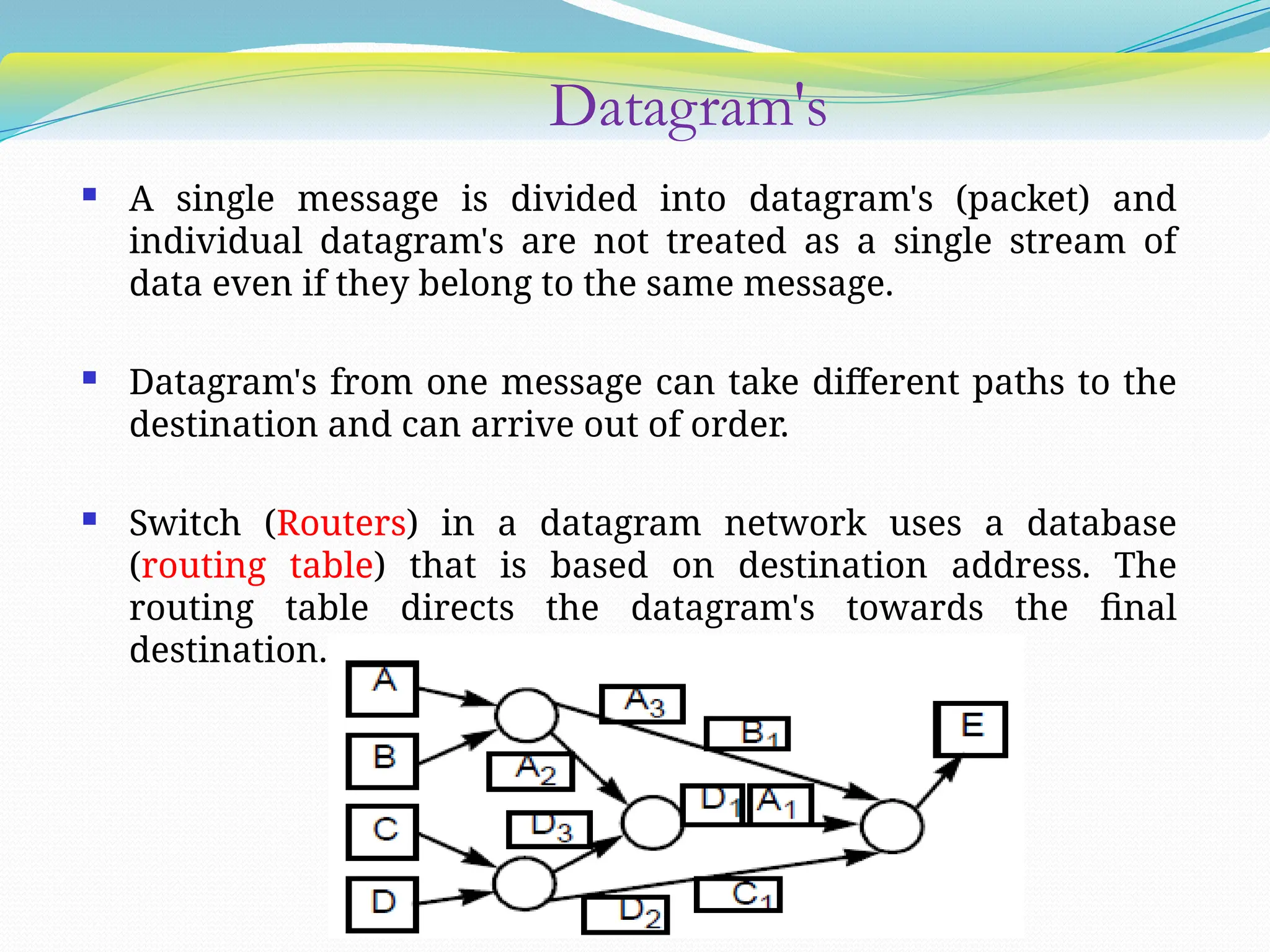
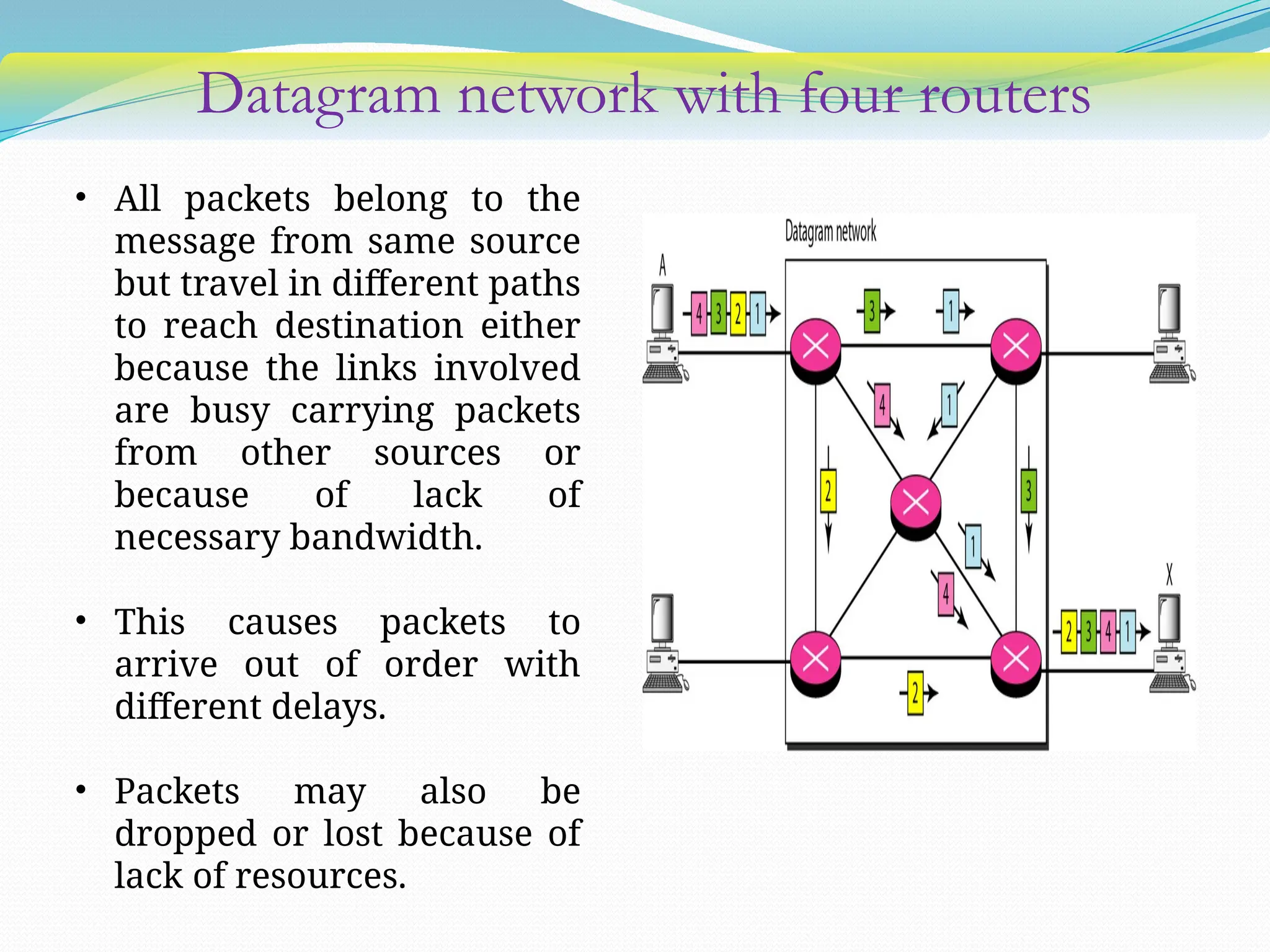
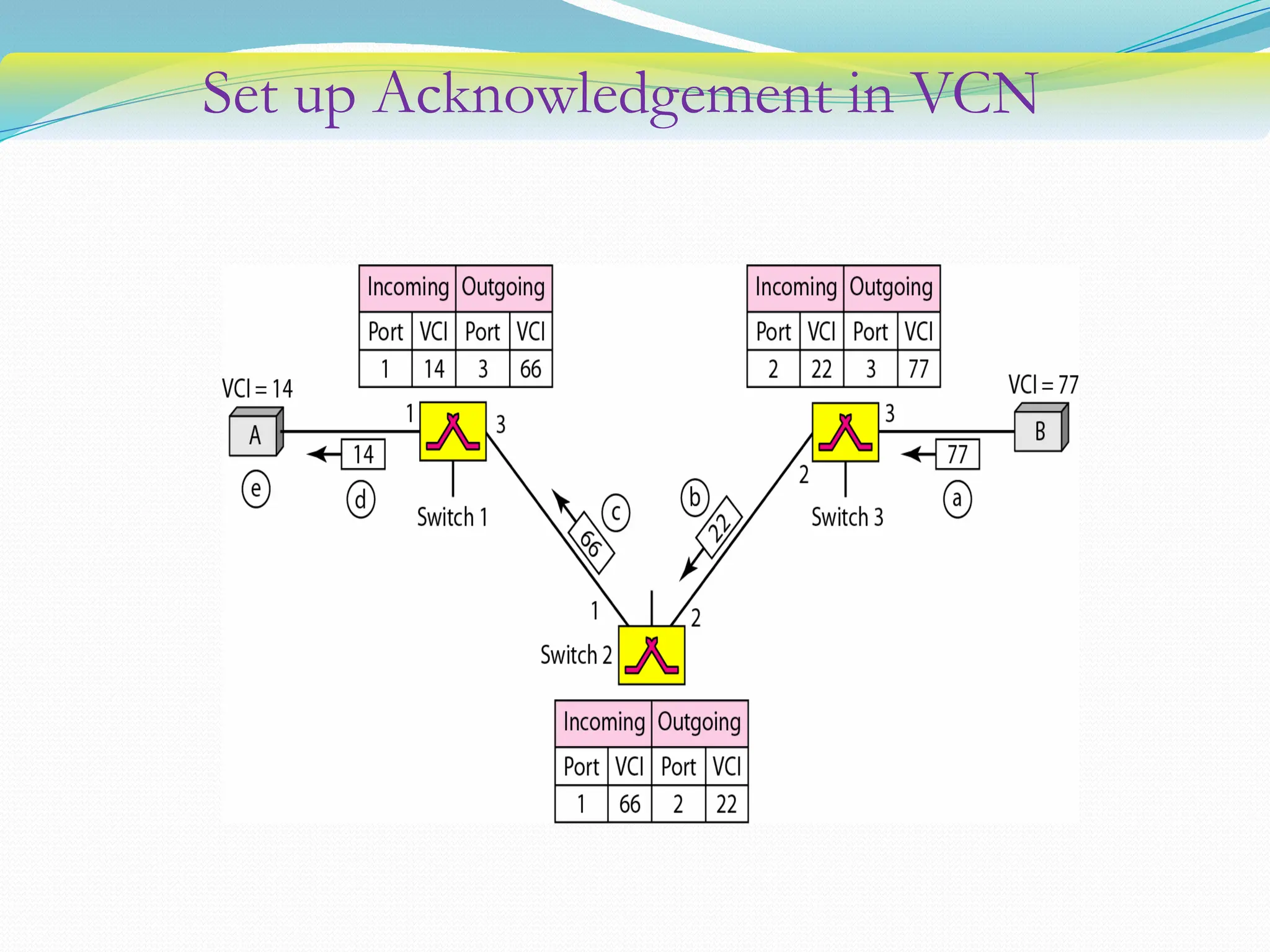
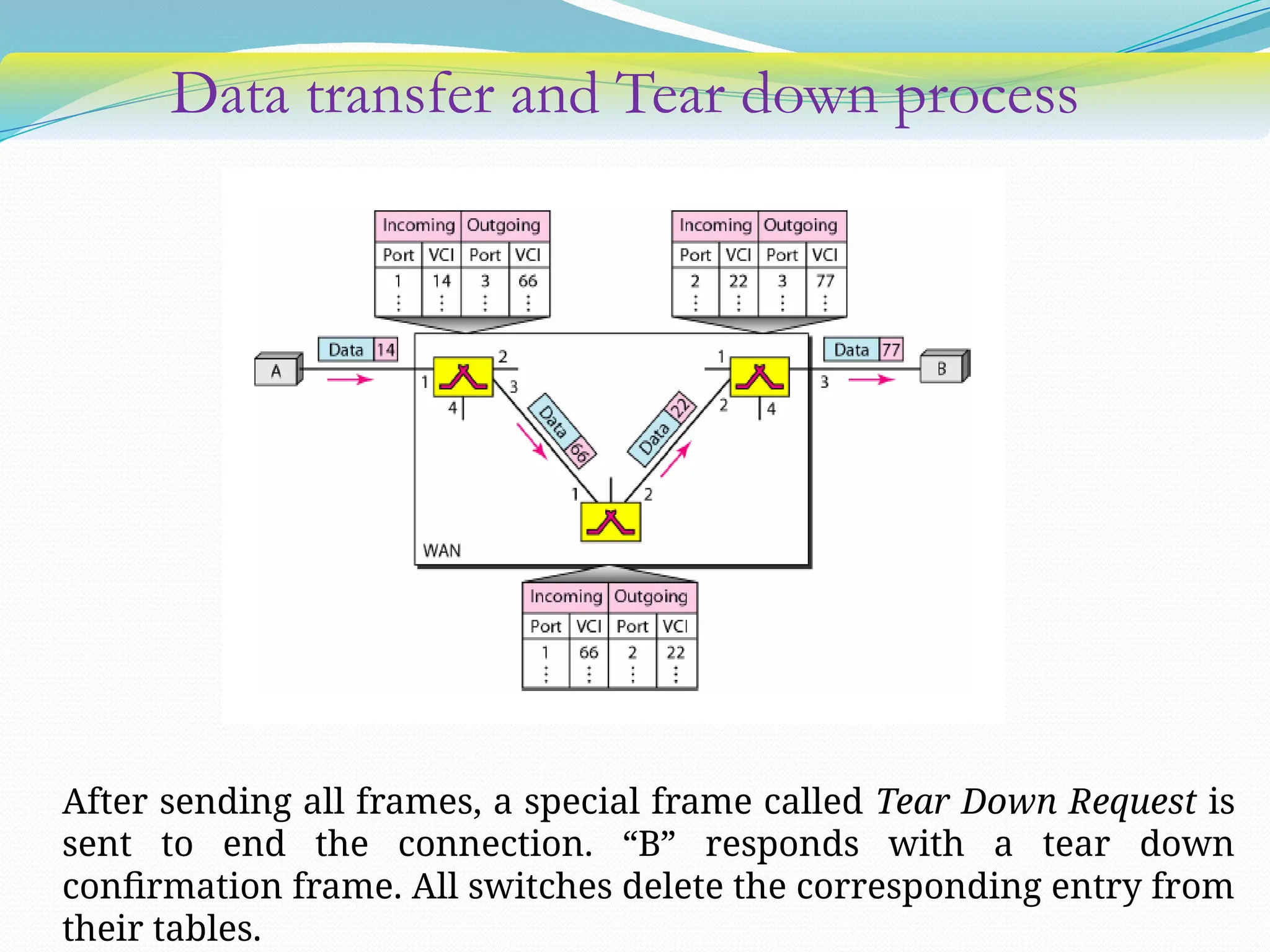
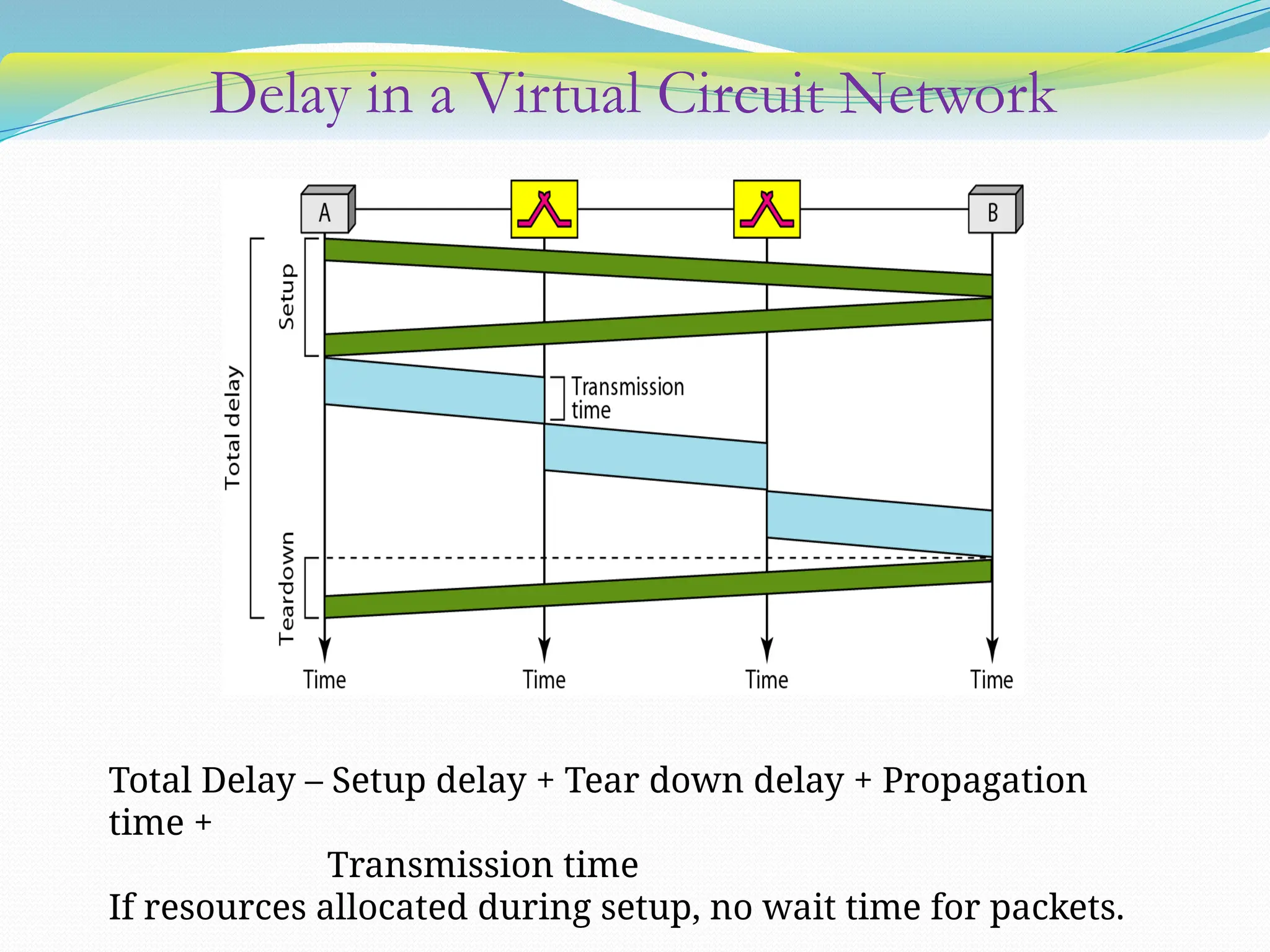
The document discusses media access control (MAC) protocols used in computer networks, particularly focusing on random access methods like Aloha and Carrier Sense Multiple Access (CSMA) with their variants. It elaborates on controlled access mechanisms such as reservation and token passing, and introduces channelization methods including Frequency Division Multiple Access (FDMA), Time Division Multiple Access (TDMA), and Code Division Multiple Access (CDMA). Finally, it covers the IEEE 802.11 wireless LAN standard, detailing its specifications and terminology.