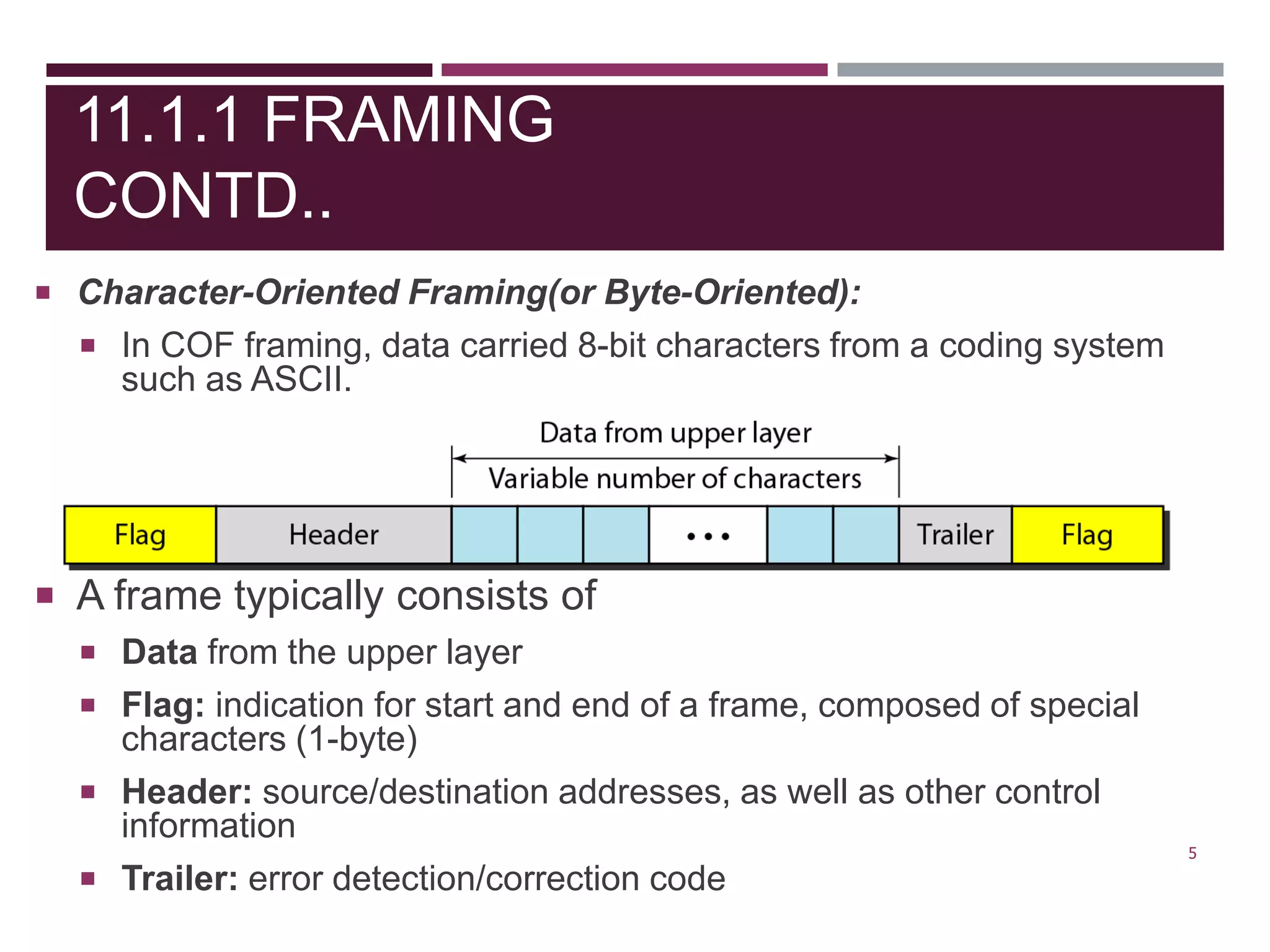
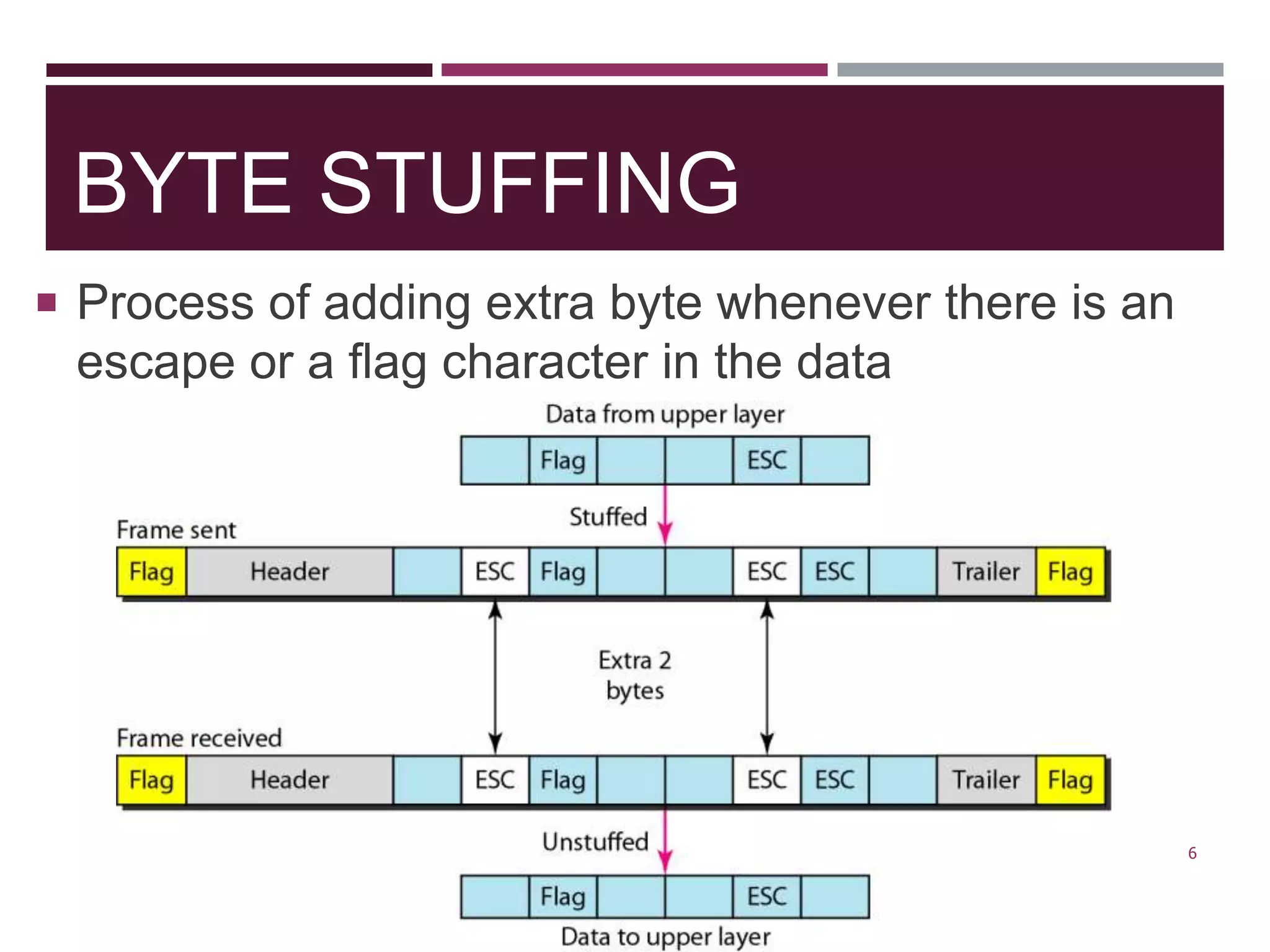
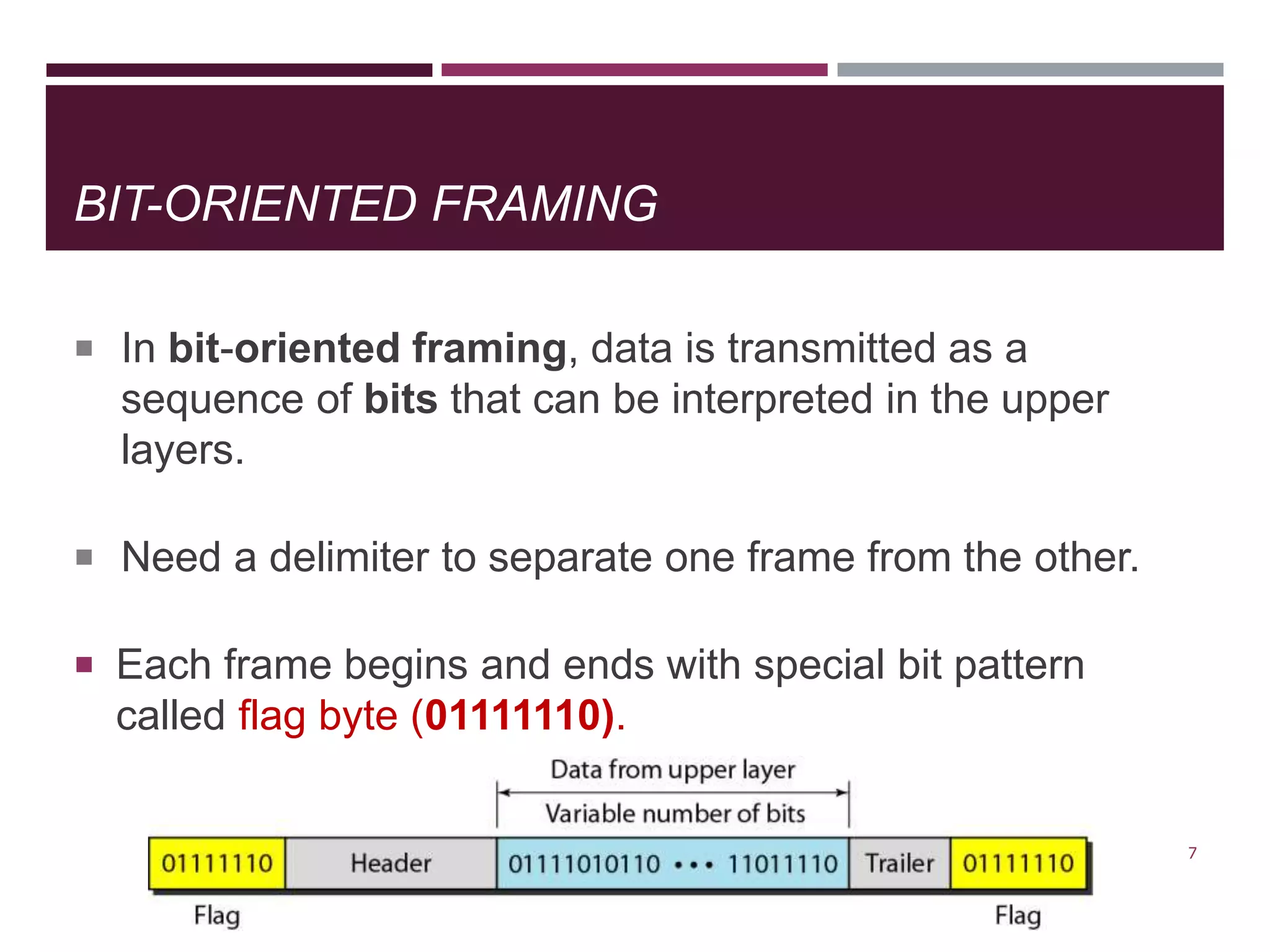
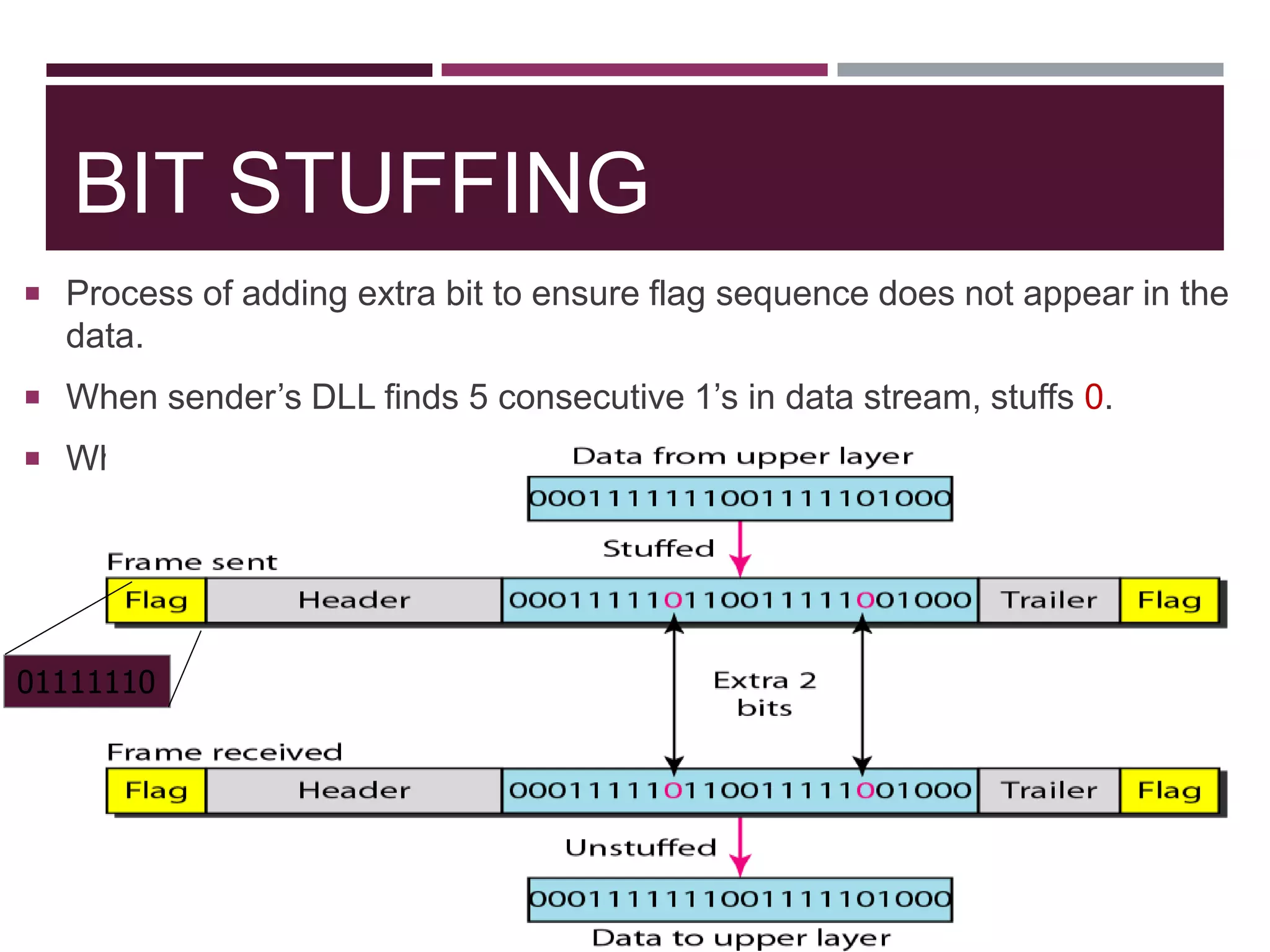
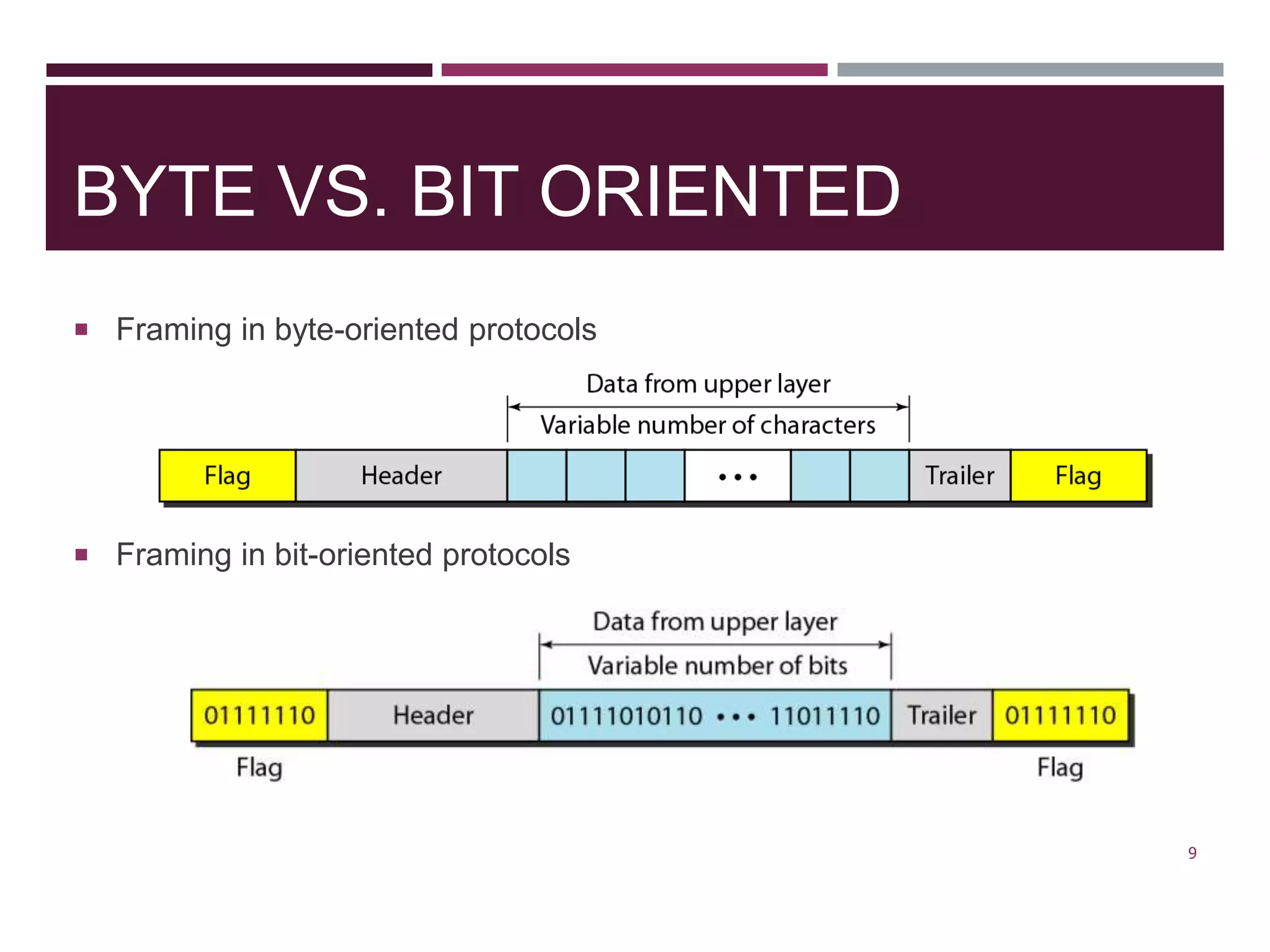
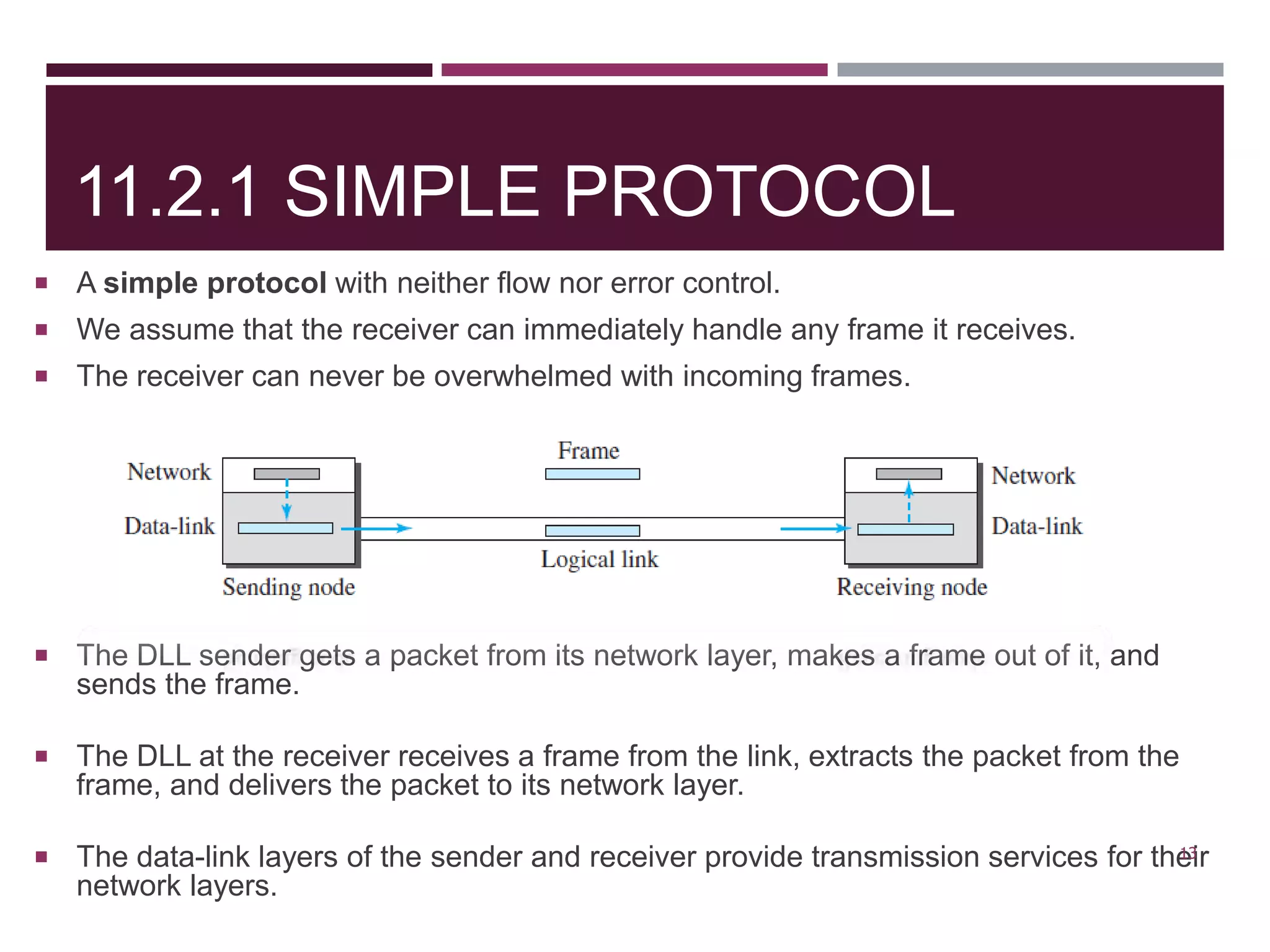
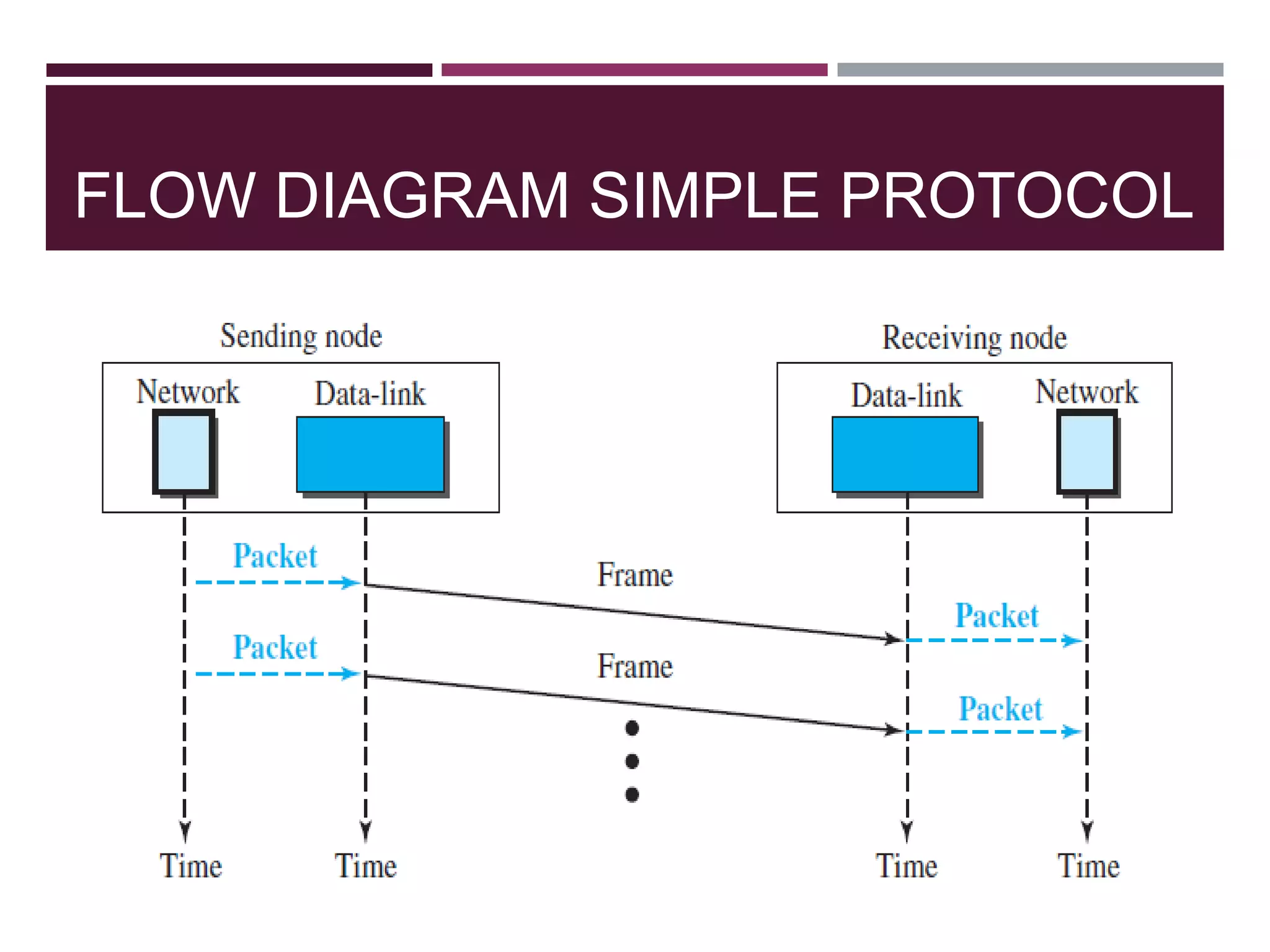
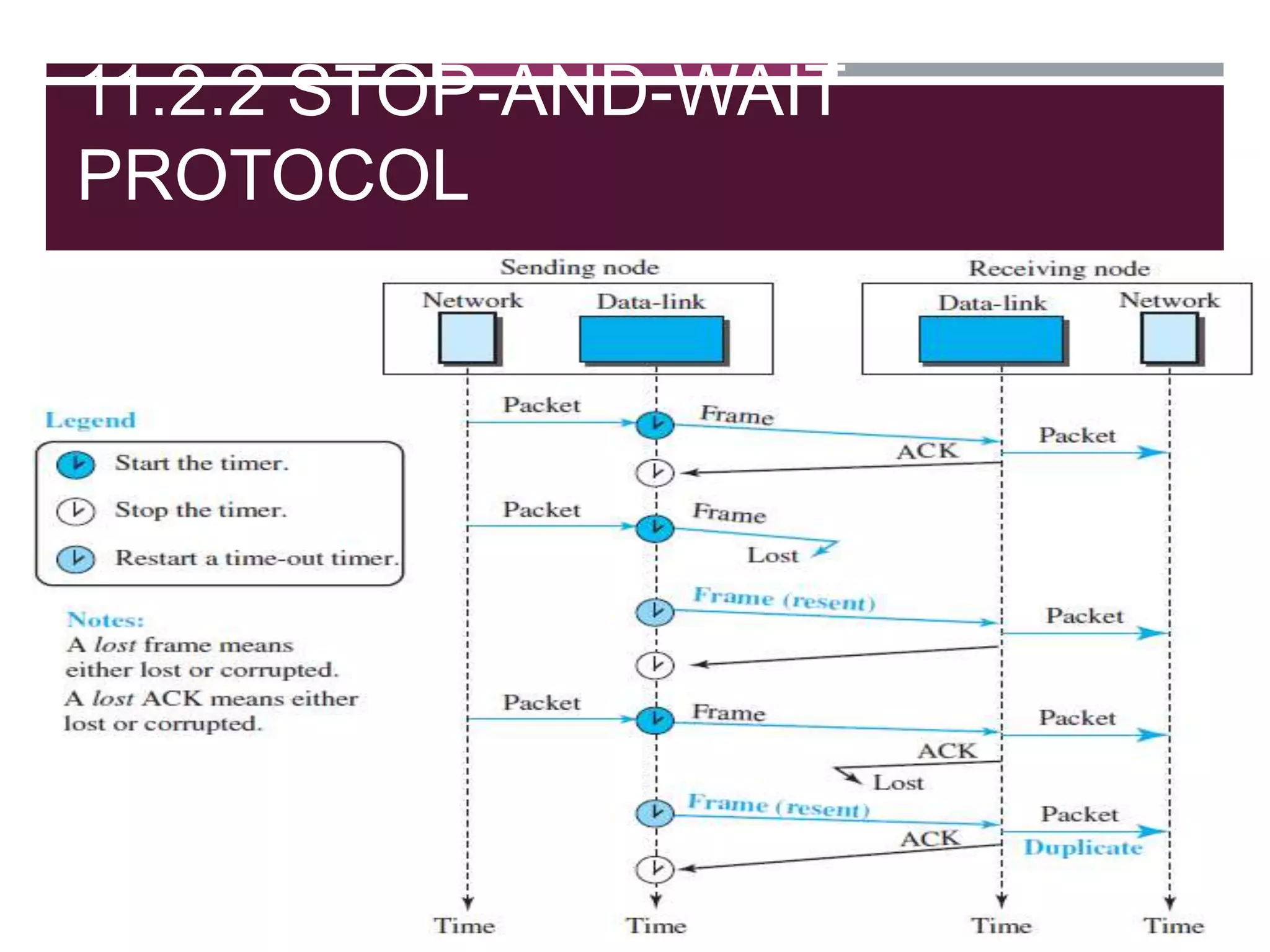
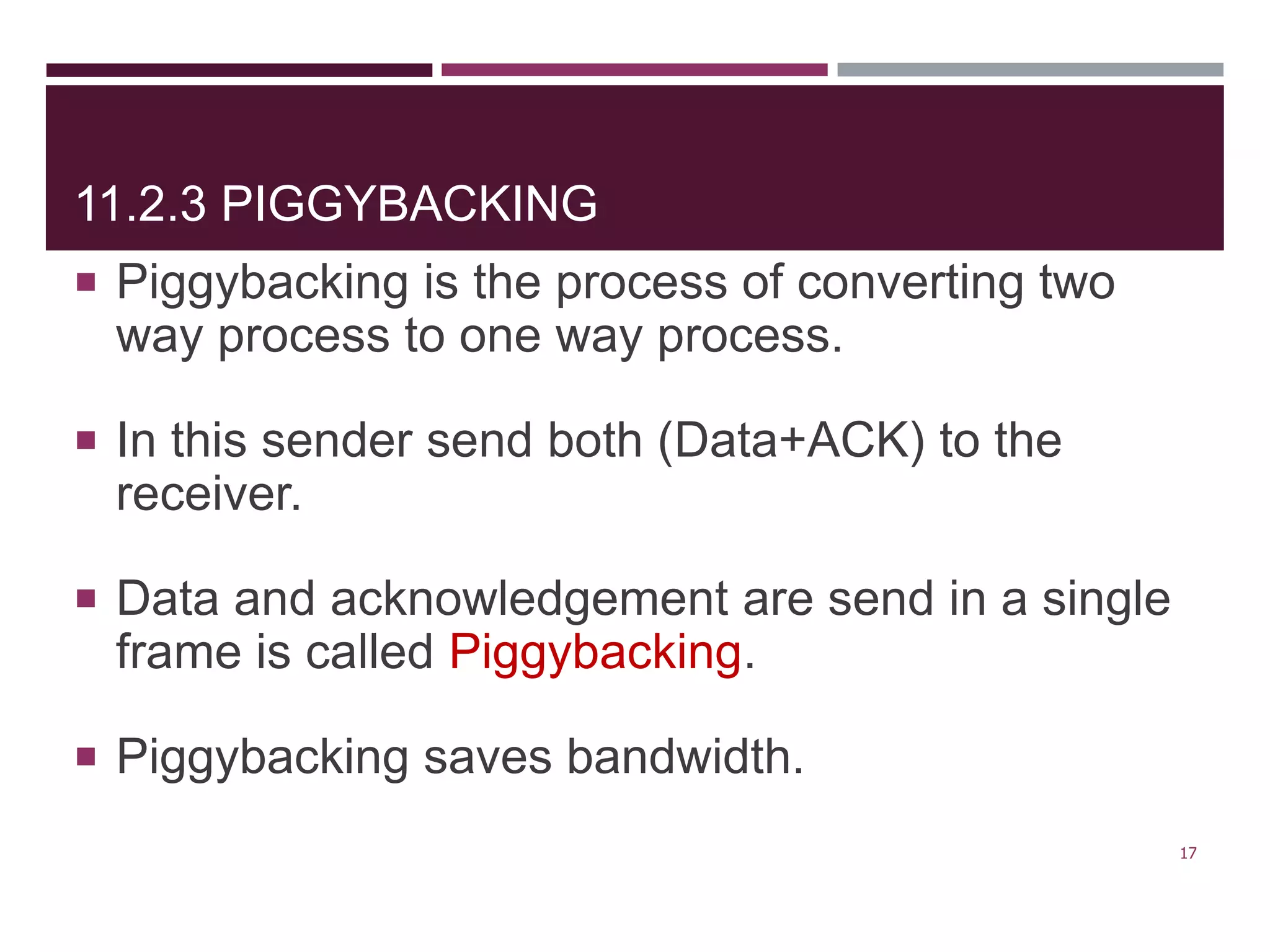
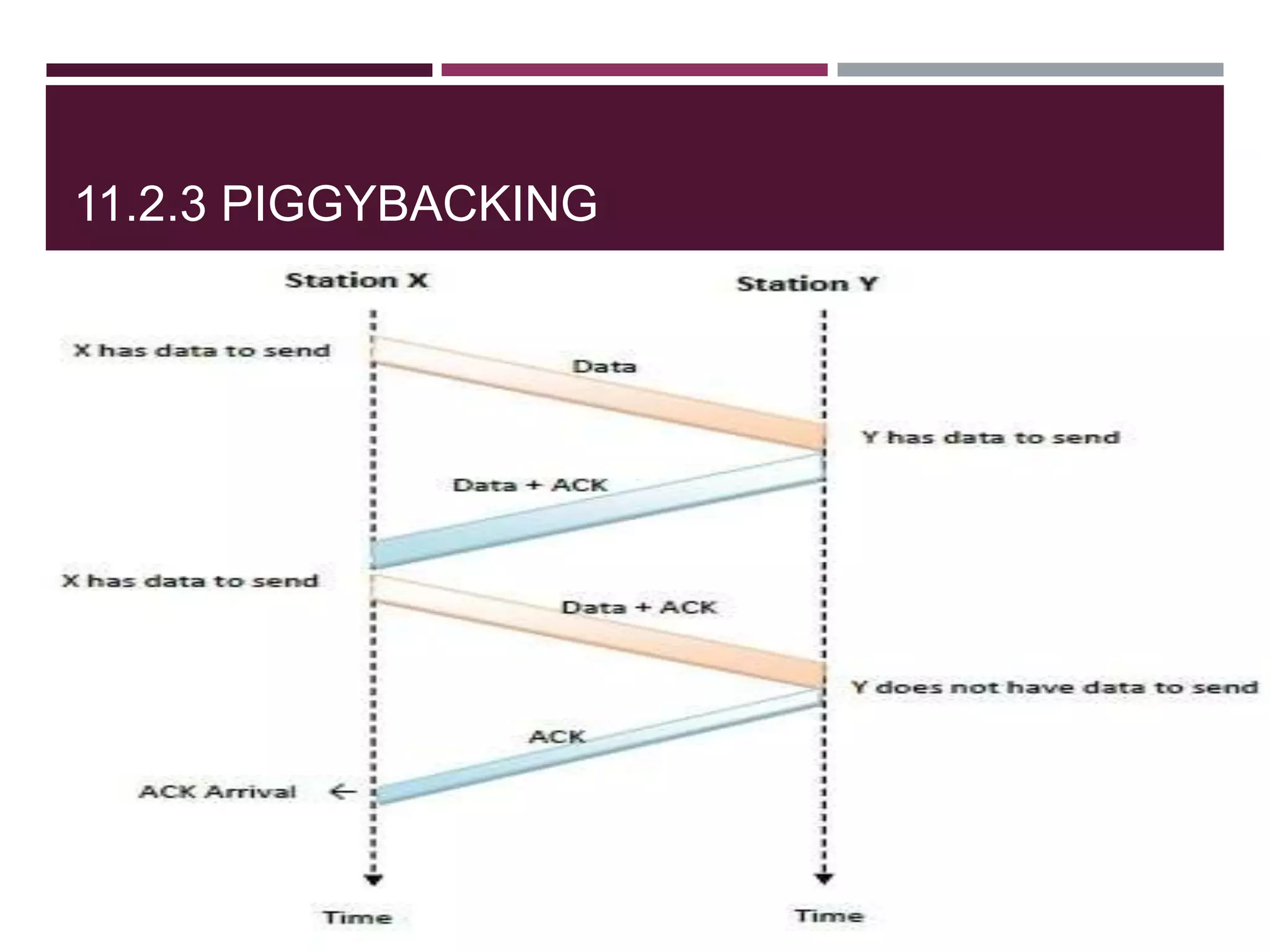
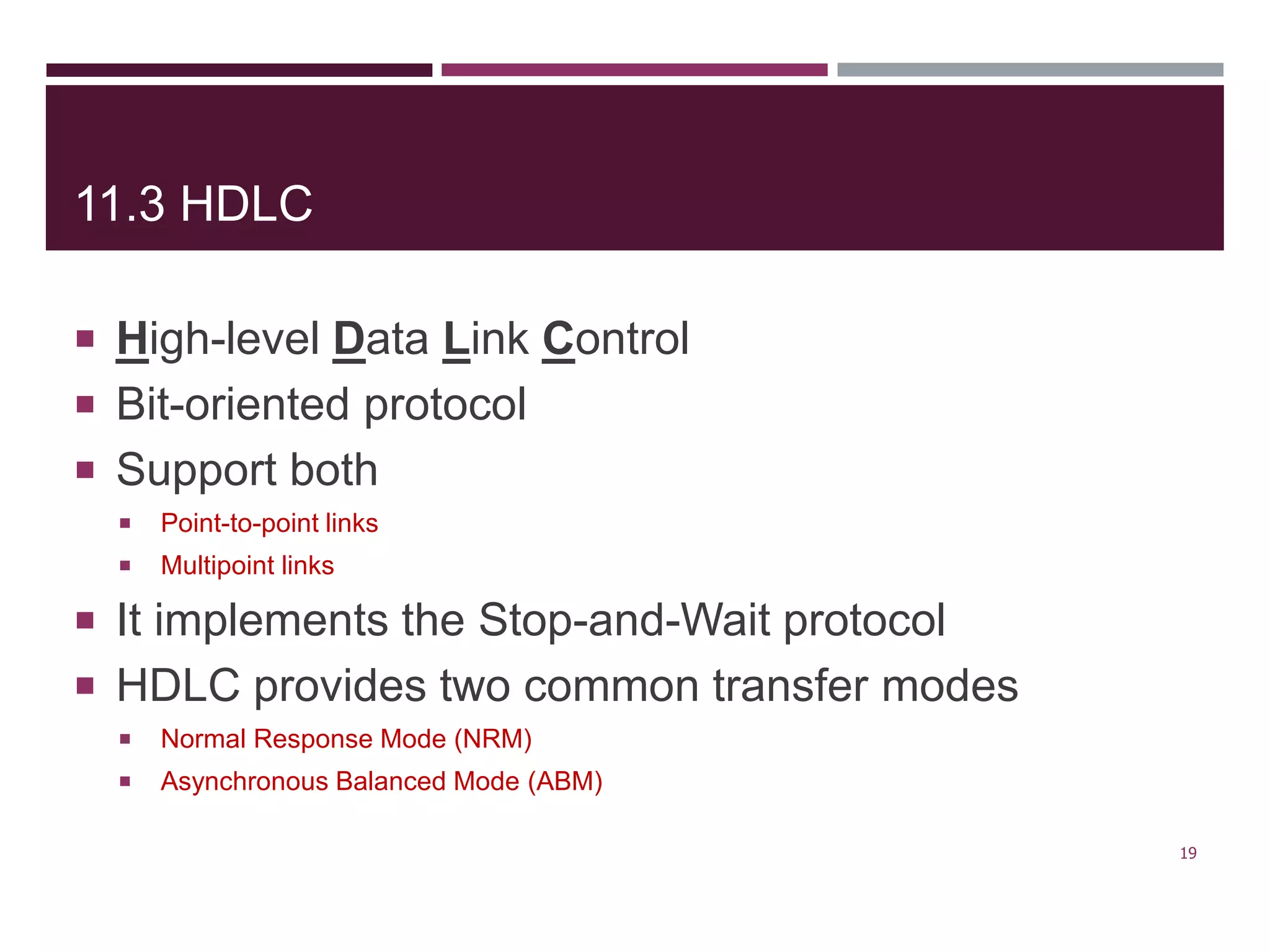
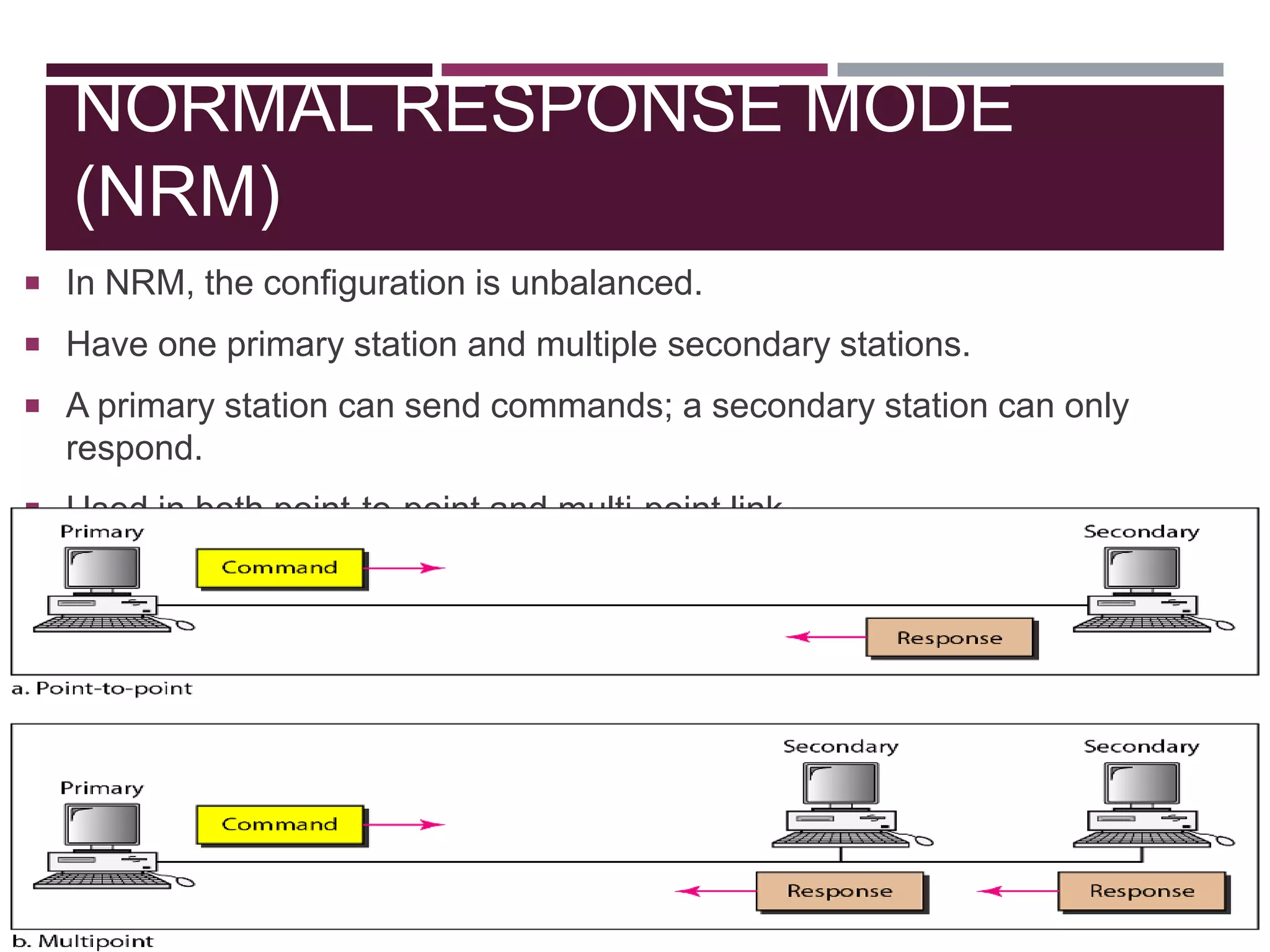
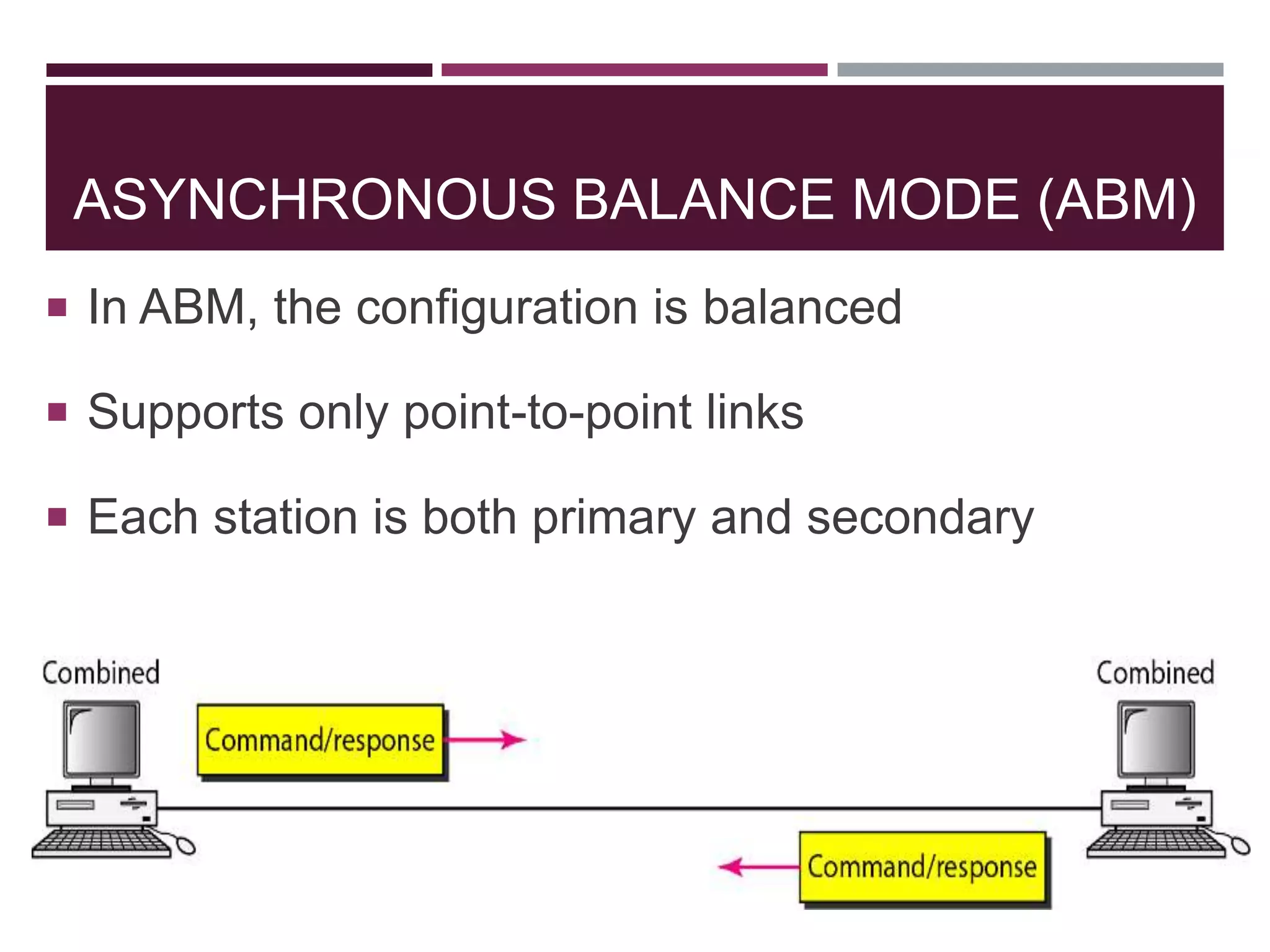
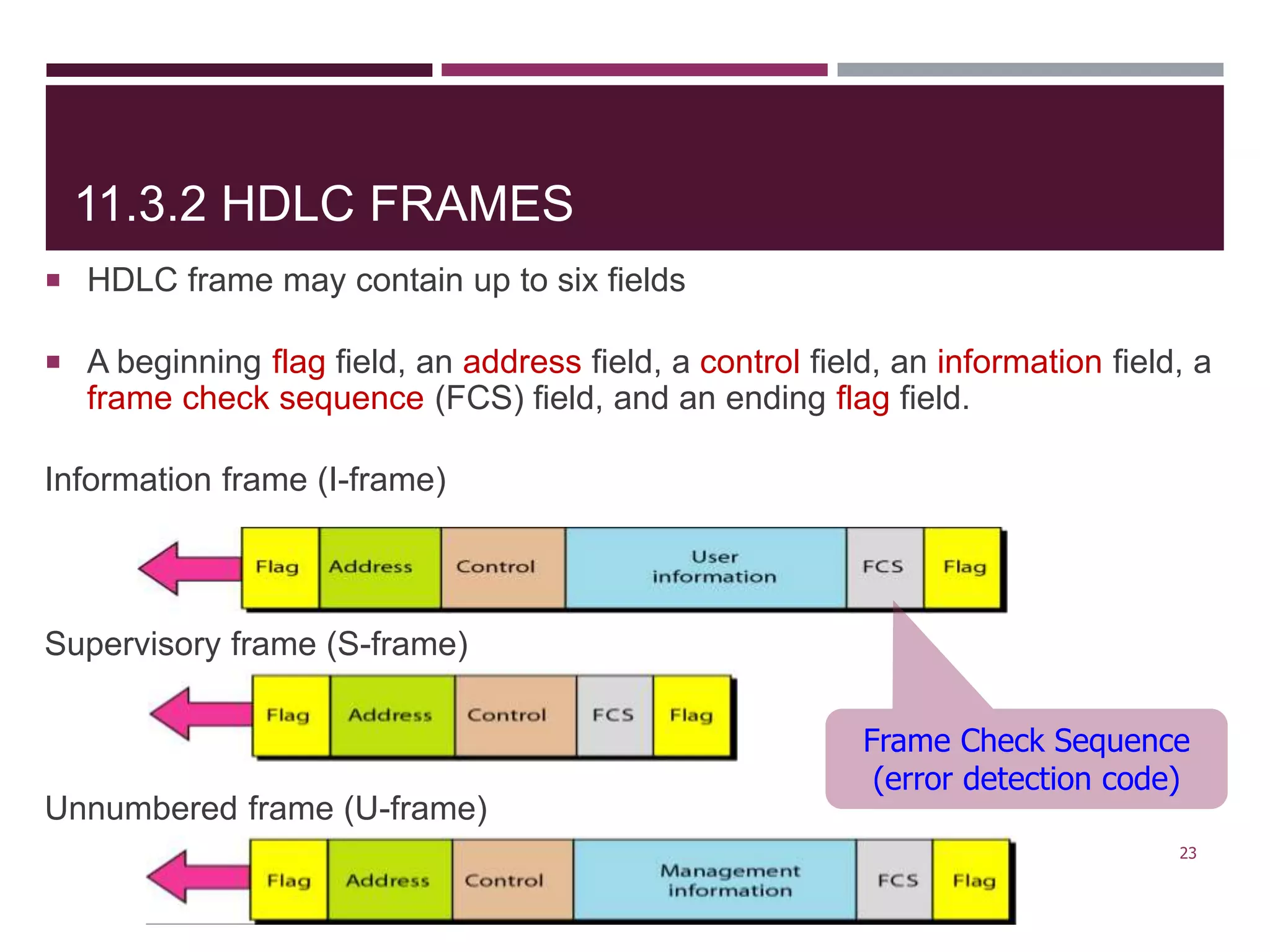
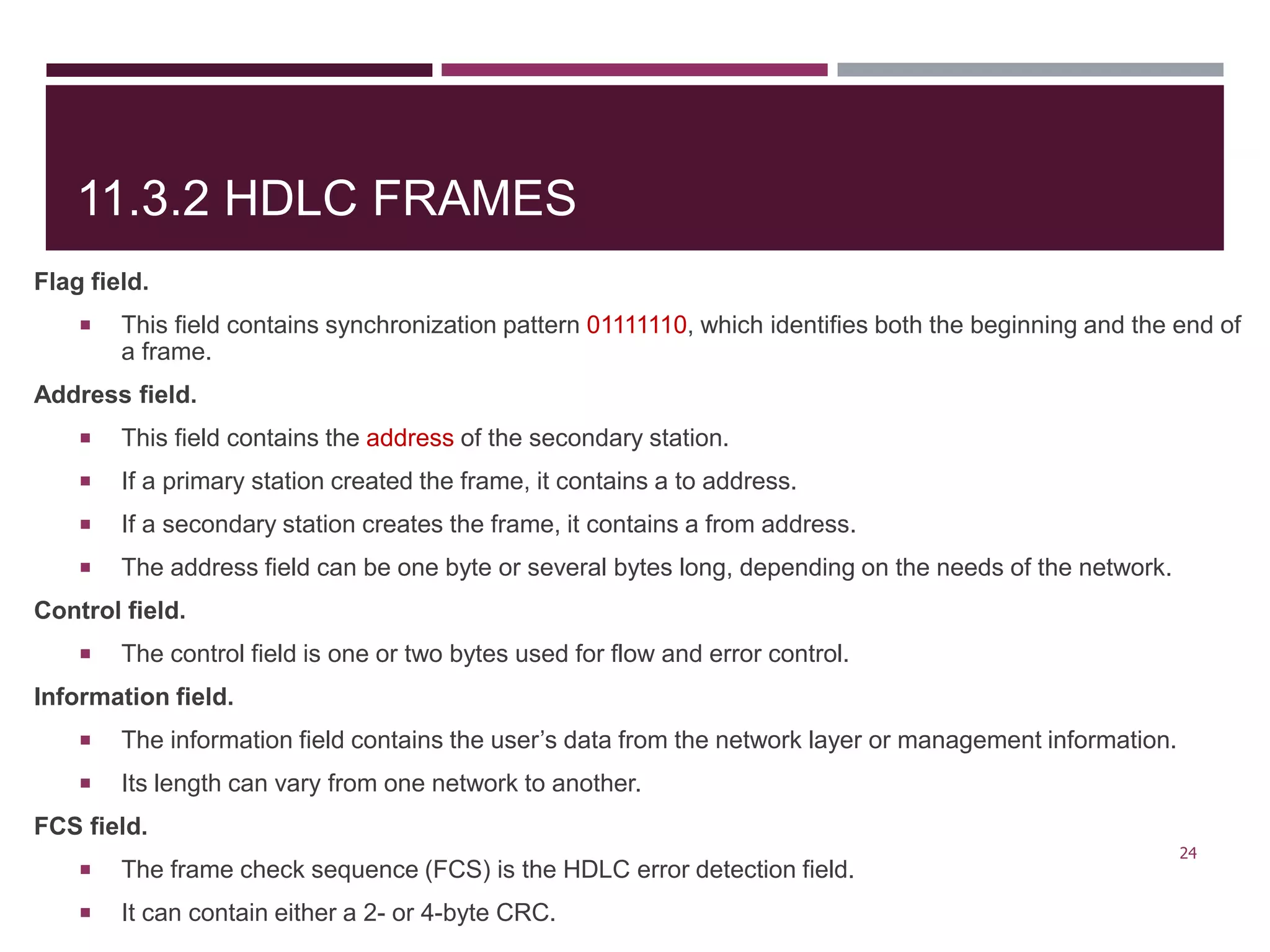
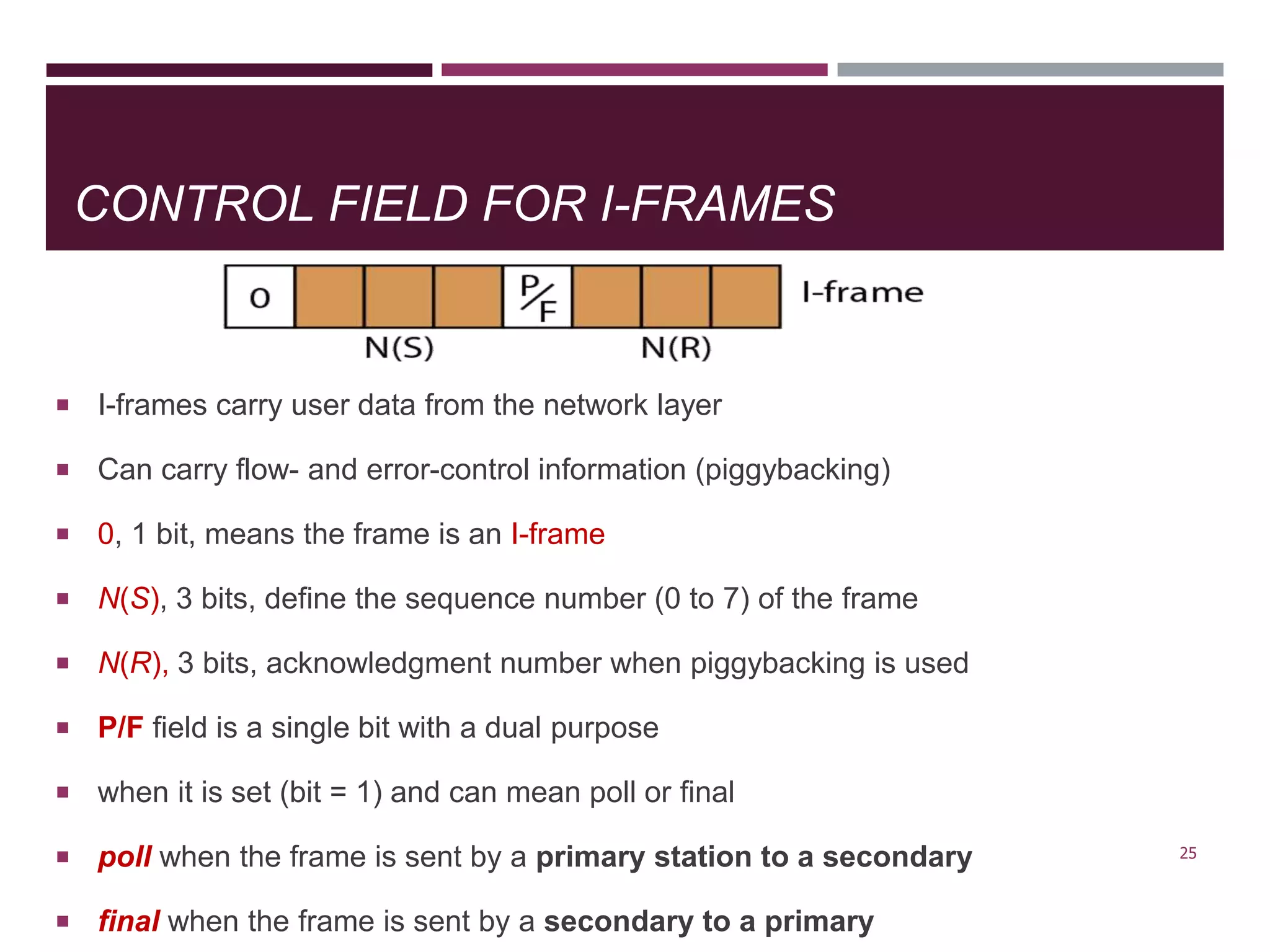
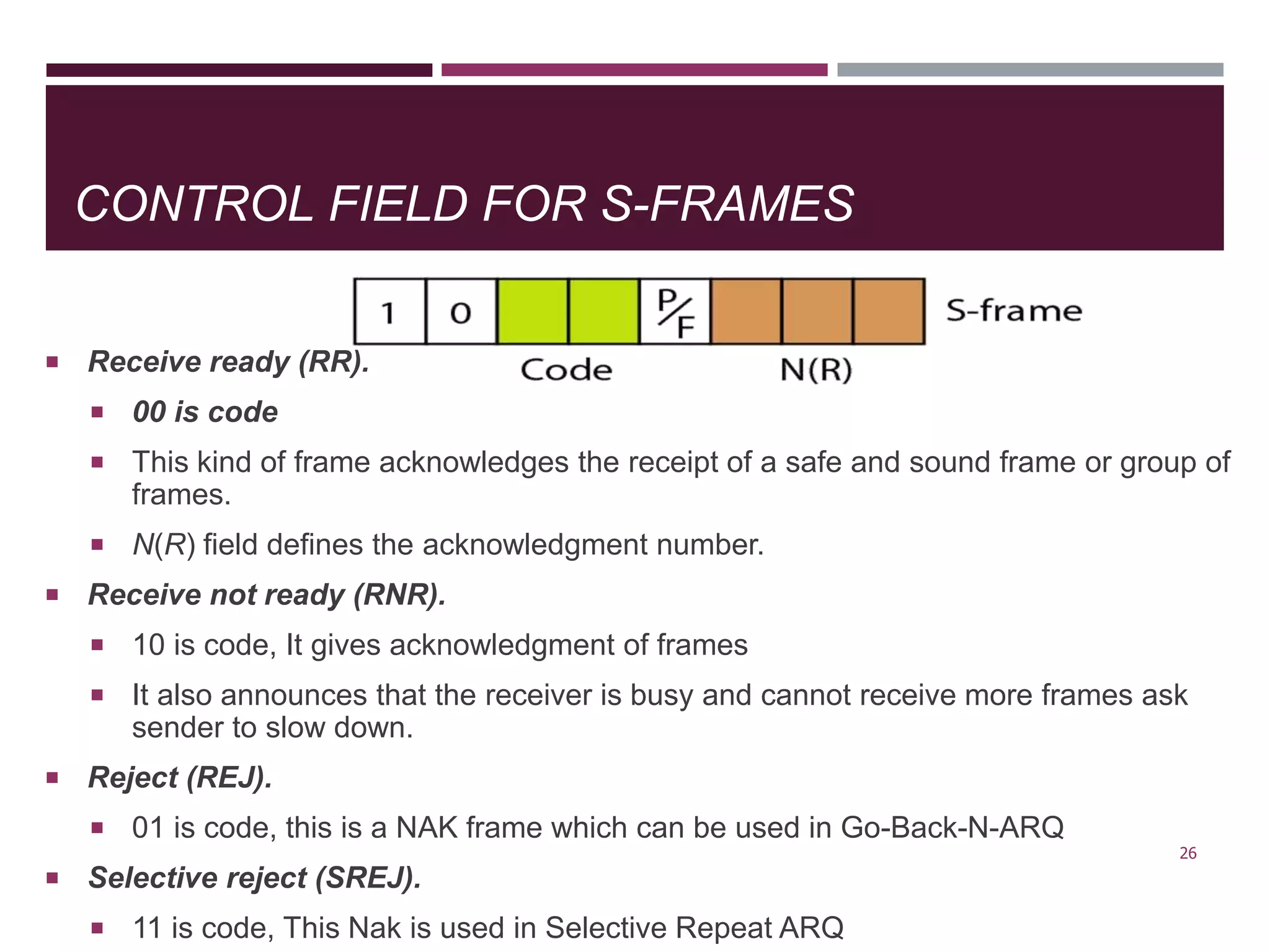
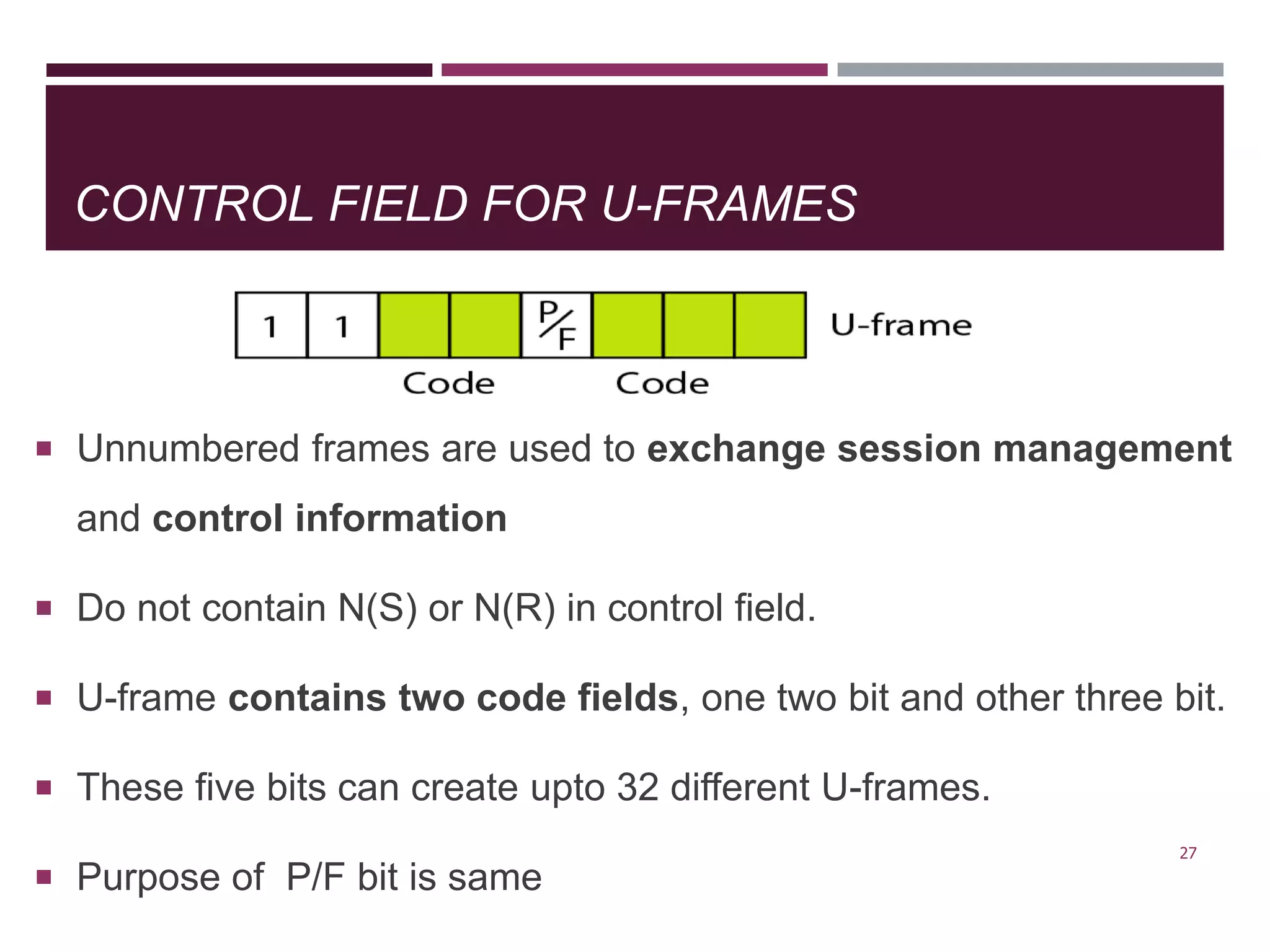
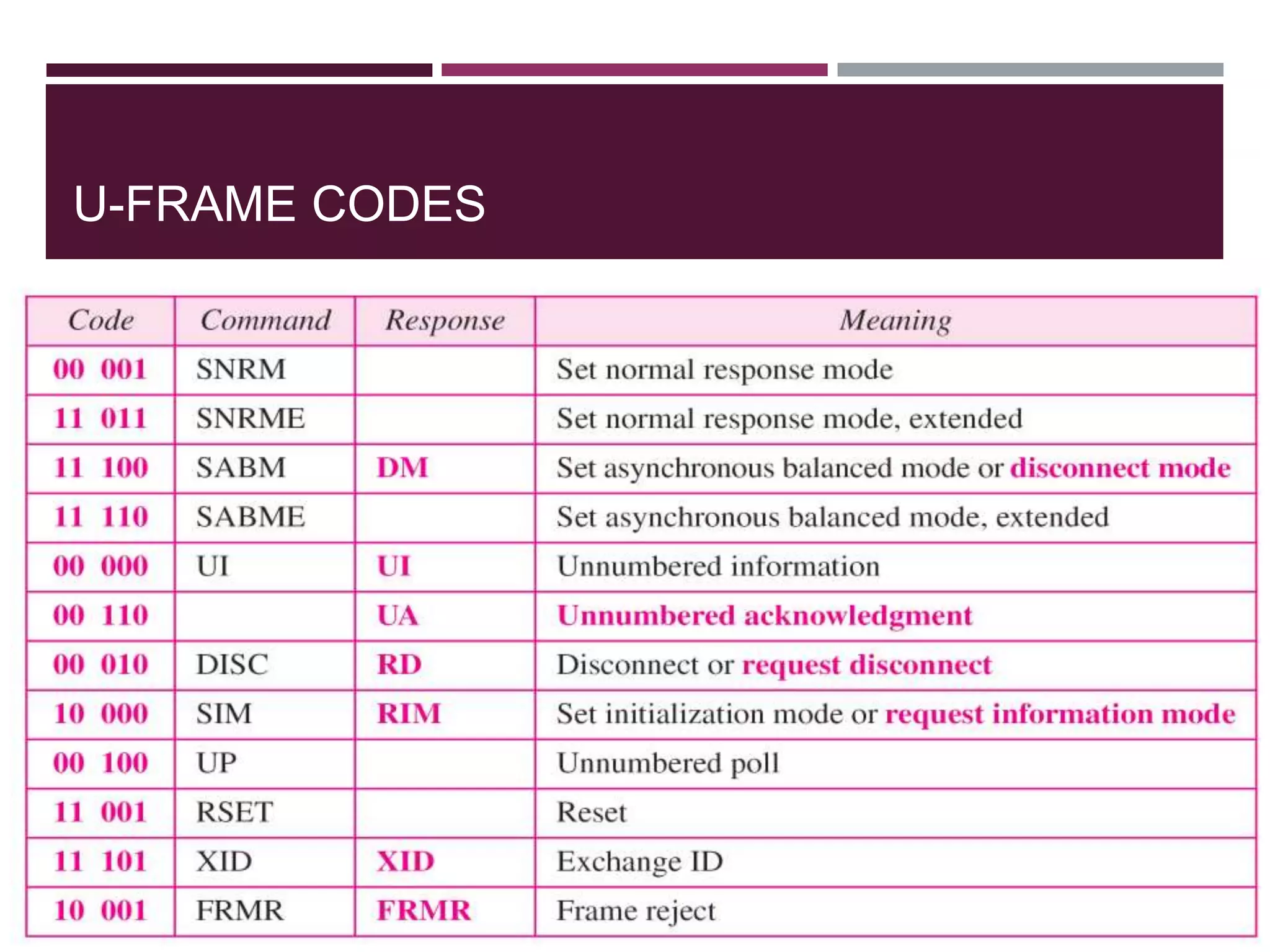
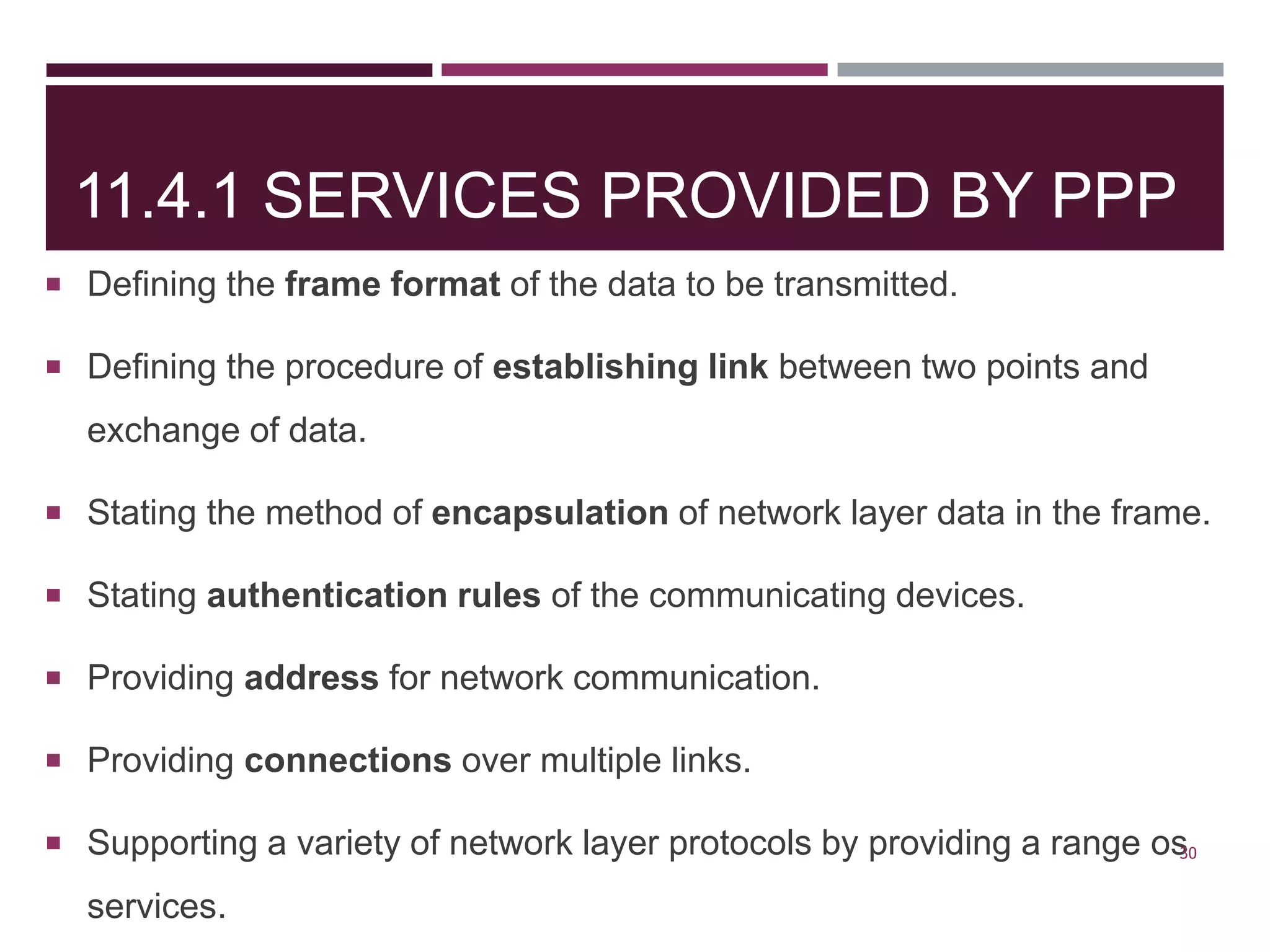
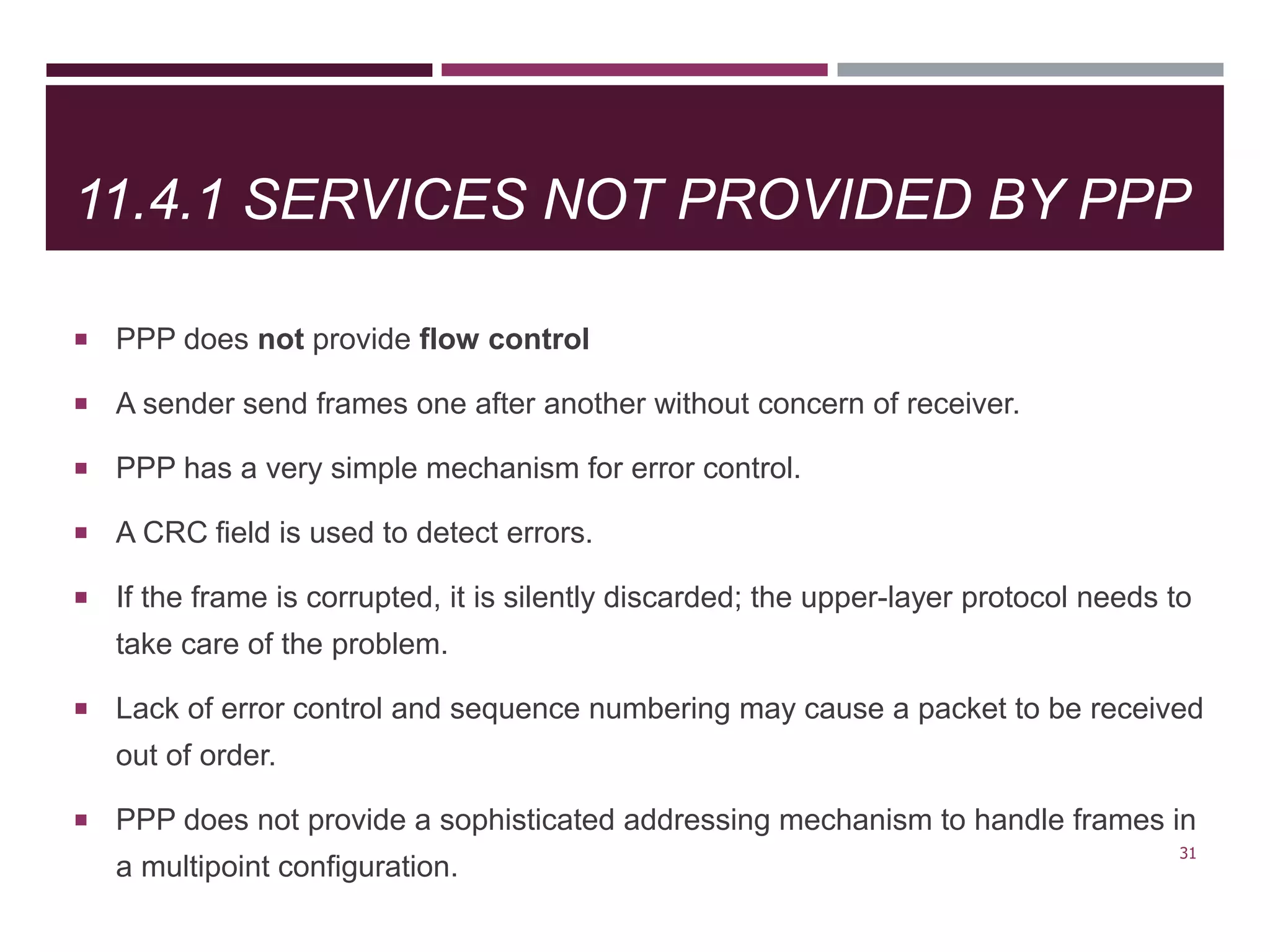
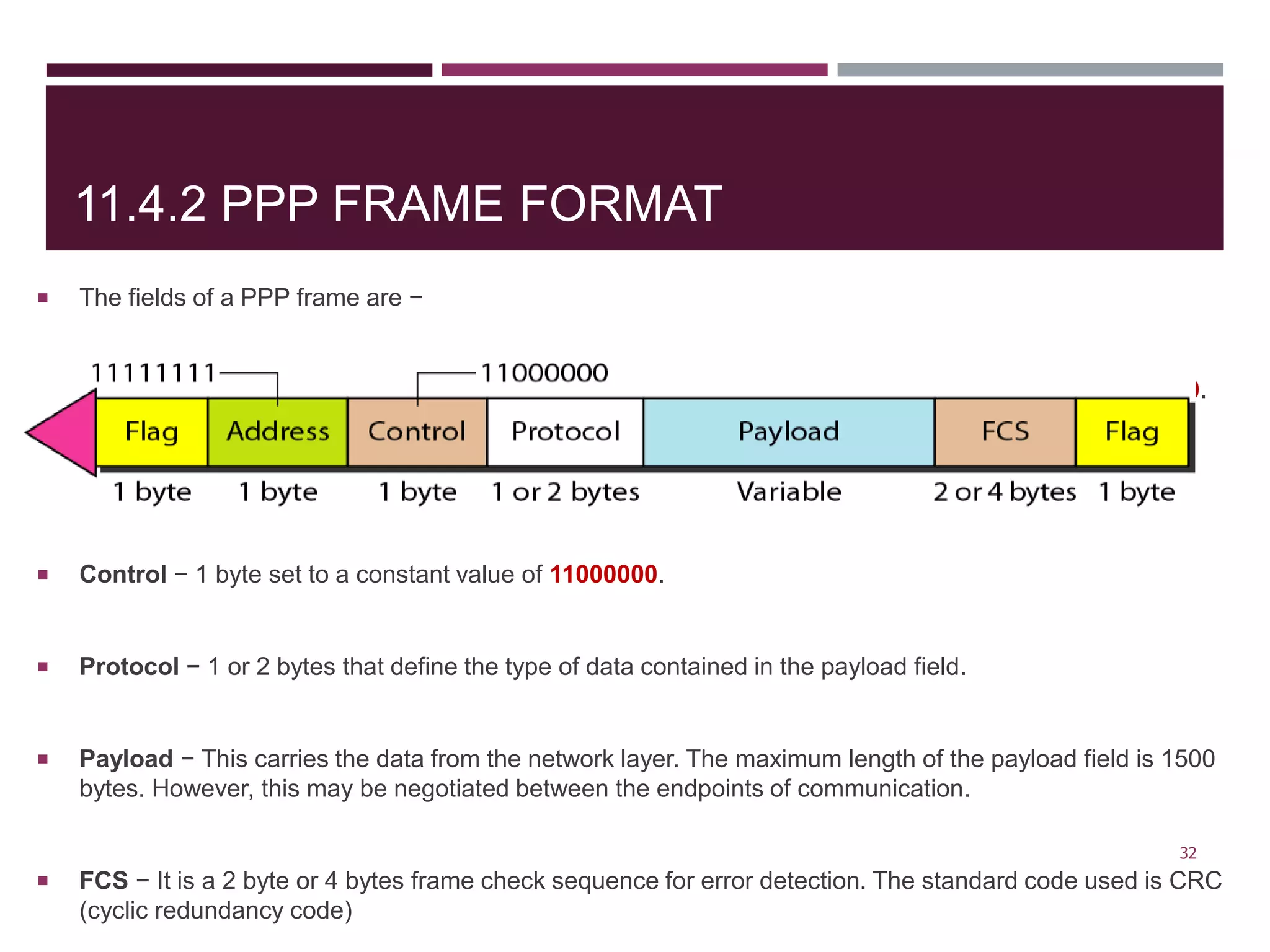
The document discusses the Data Link Layer (DLL) of computer networks, detailing its services, protocols, and functionalities such as framing, flow control, and error control. It explains different protocols like HDLC and PPP, covering aspects such as connection-oriented versus connectionless protocols, framing methods, and control field structures. Key concepts include the processes of framing, piggybacking for efficiency, and error detection mechanisms through checksums.