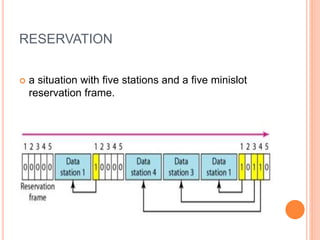
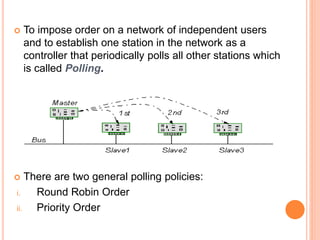
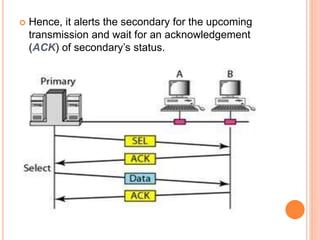
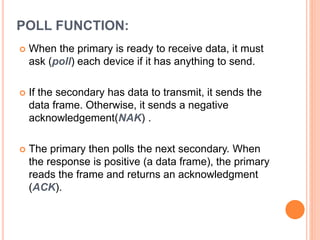
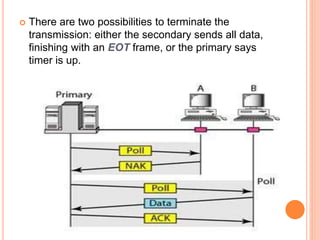
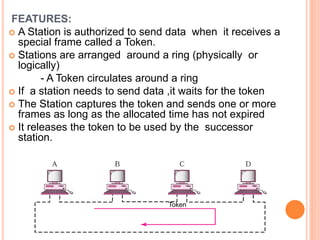
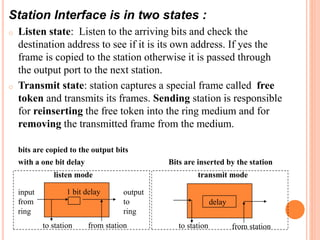
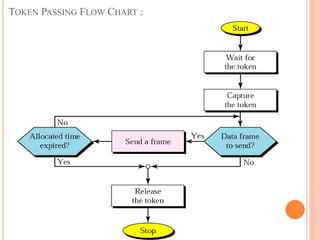
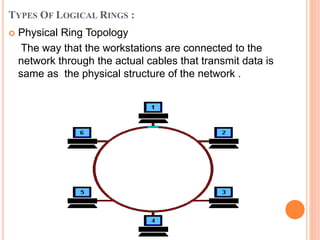
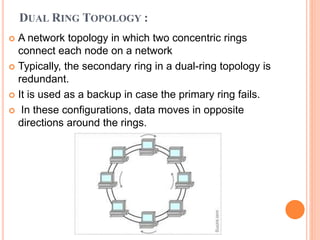
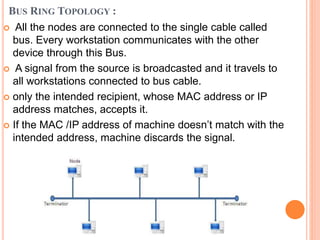
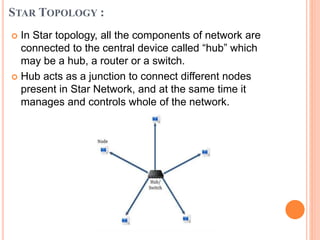
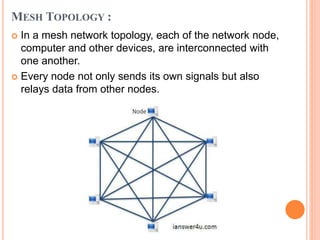
Controlled access protocols allow only one node to send at a time to avoid message collisions. There are three main controlled access methods: reservation, polling, and token passing. Reservation methods divide time into intervals, with reservation frames preceding data frames to reserve slots. Polling methods involve a primary station periodically polling secondary stations for data. Token passing methods use a token frame that circulates between stations, with each station only allowed to transmit when holding the token.