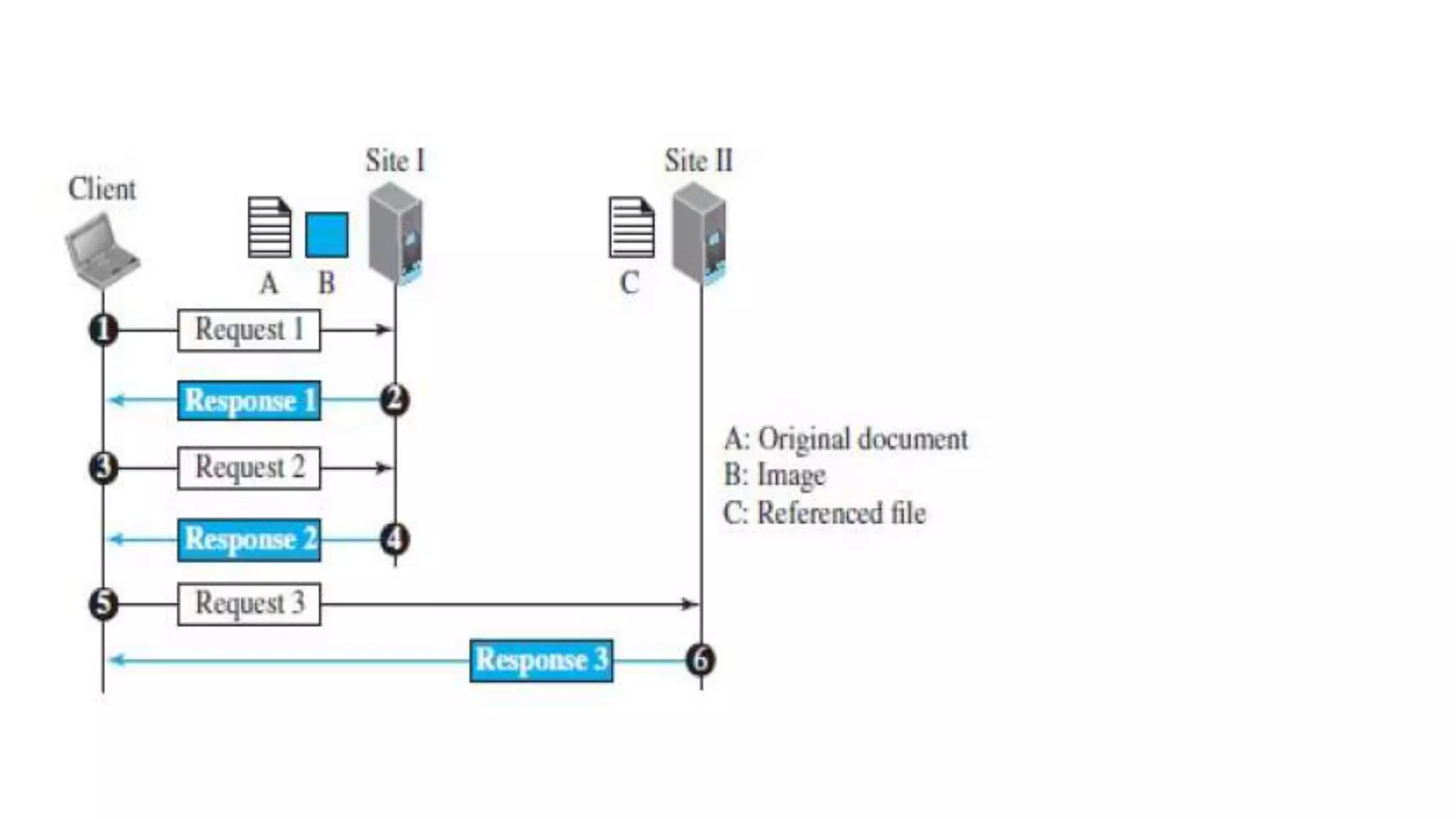
The document provides an overview of the application layer in networking, highlighting its significance in providing services to users through various protocols such as HTTP, FTP, and email. It describes the client-server and peer-to-peer paradigms, as well as the structure and functionality of the World Wide Web, including web browsers, servers, and the role of URL and URI. Additionally, it addresses FTP communication and related security concerns regarding data transfer.