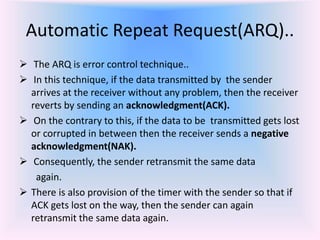
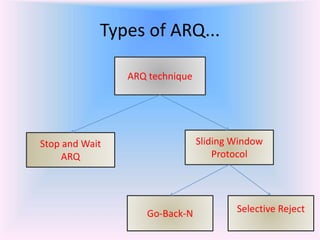
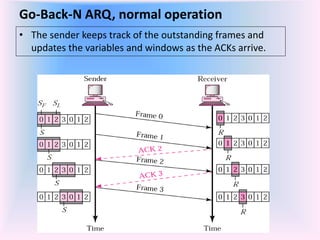
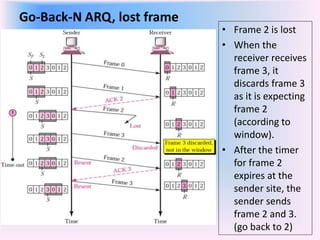
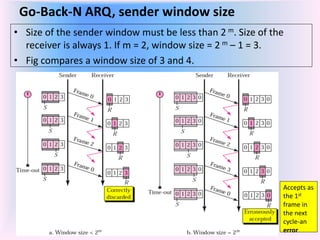
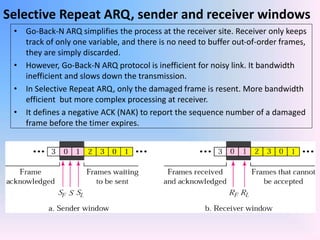
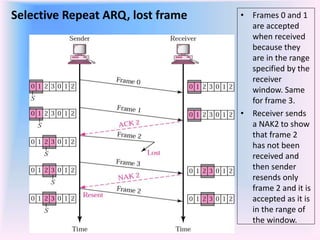
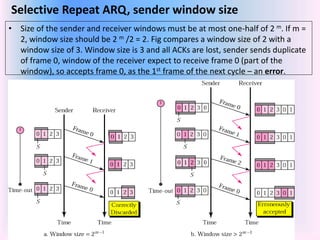
The document discusses different types of Automatic Repeat Request (ARQ) techniques used for error control in data transmission. It describes Stop-and-Wait ARQ, Go-Back-N ARQ, and Selective Repeat ARQ. Go-Back-N ARQ allows sending multiple frames before receiving acknowledgments. If a frame is lost or corrupted, the sender retransmits that frame and all subsequent frames. Selective Repeat ARQ only retransmits the damaged frame, making it more bandwidth efficient but also more complex since the receiver must buffer frames. The sizes of the sender and receiver windows are important parameters that impact the efficiency of the protocols.