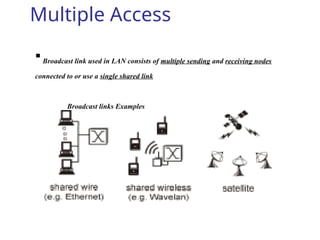
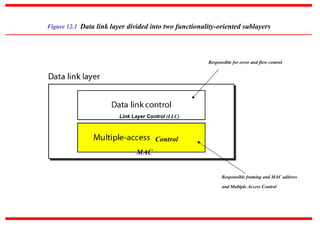
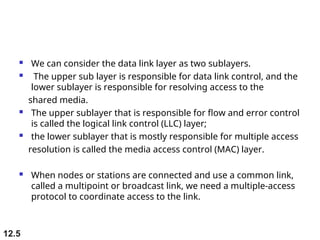
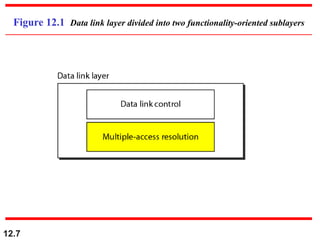
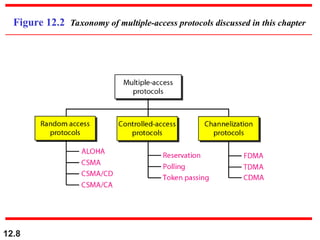
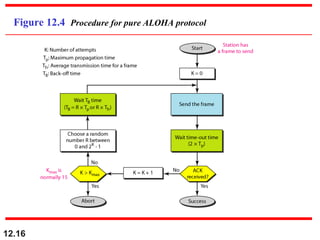
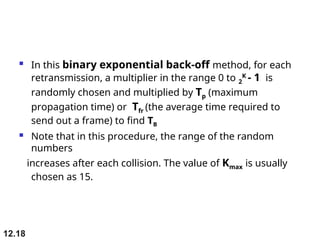
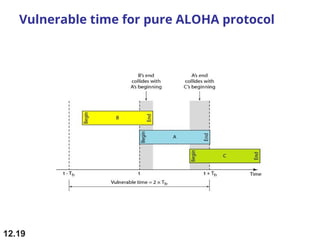
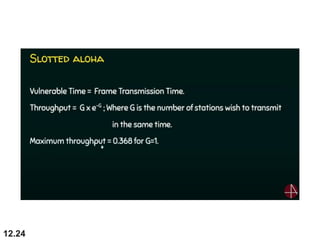
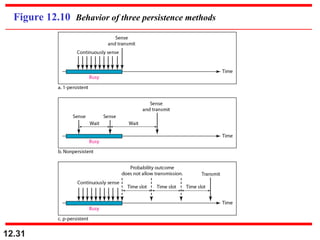
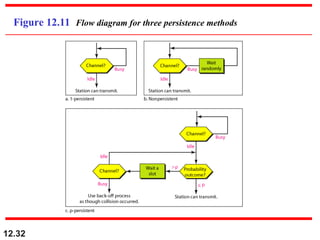
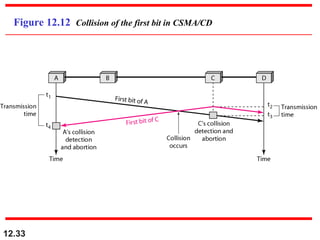
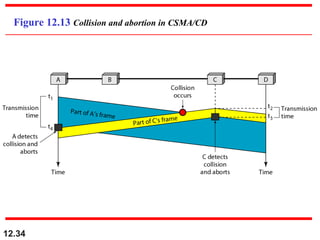
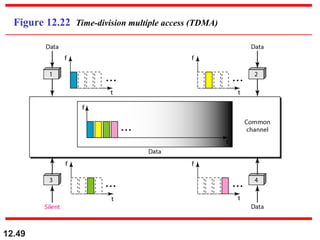
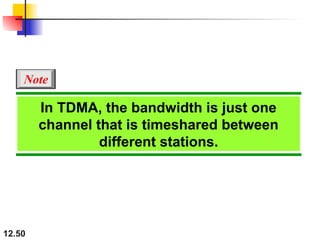
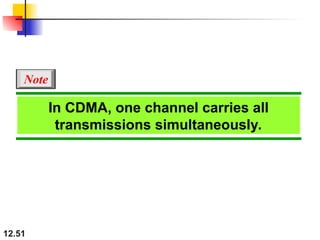
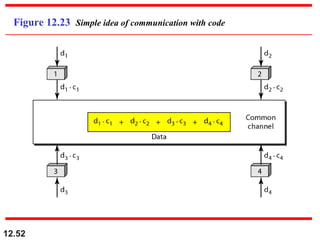
Multiple Access Protocols allow multiple devices to share a common communication channel efficiently. They prevent collisions and manage access. Types include Random Access (e.g., ALOHA, CSMA), Controlled Access (Polling, Token Passing), and Channelization (FDMA, TDMA, CDMA). Each method ensures fair, organized, and reliable data transmission in networks.

















![12.60
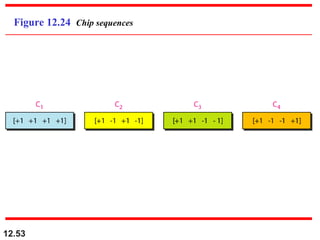
Find the chips for a network with
a. Two stations b. Four stations
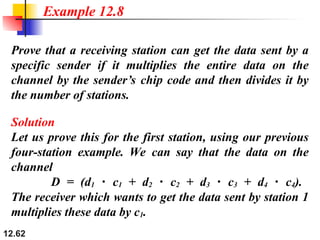
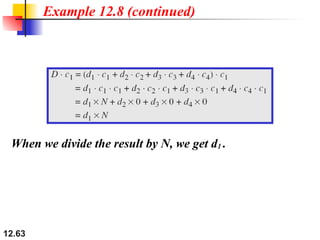
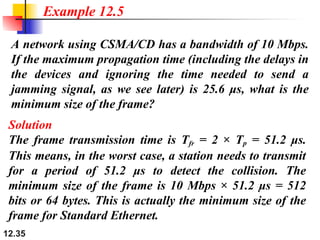
Example 12.6
Solution
We can use the rows of W2 and W4 in Figure 12.29:
a. For a two-station network, we have
[+1 +1] and [+1 −1].
b. For a four-station network we have
[+1 +1 +1 +1], [+1 −1 +1 −1],
[+1 +1 −1 −1], and [+1 −1 −1 +1].](https://image.slidesharecdn.com/multipleaccessprotocols-unit2updated-251008134428-afee8f35/85/Multiple-Access-protocols-IN-COMPUTER-NETWORKS-ppt-59-320.jpg)