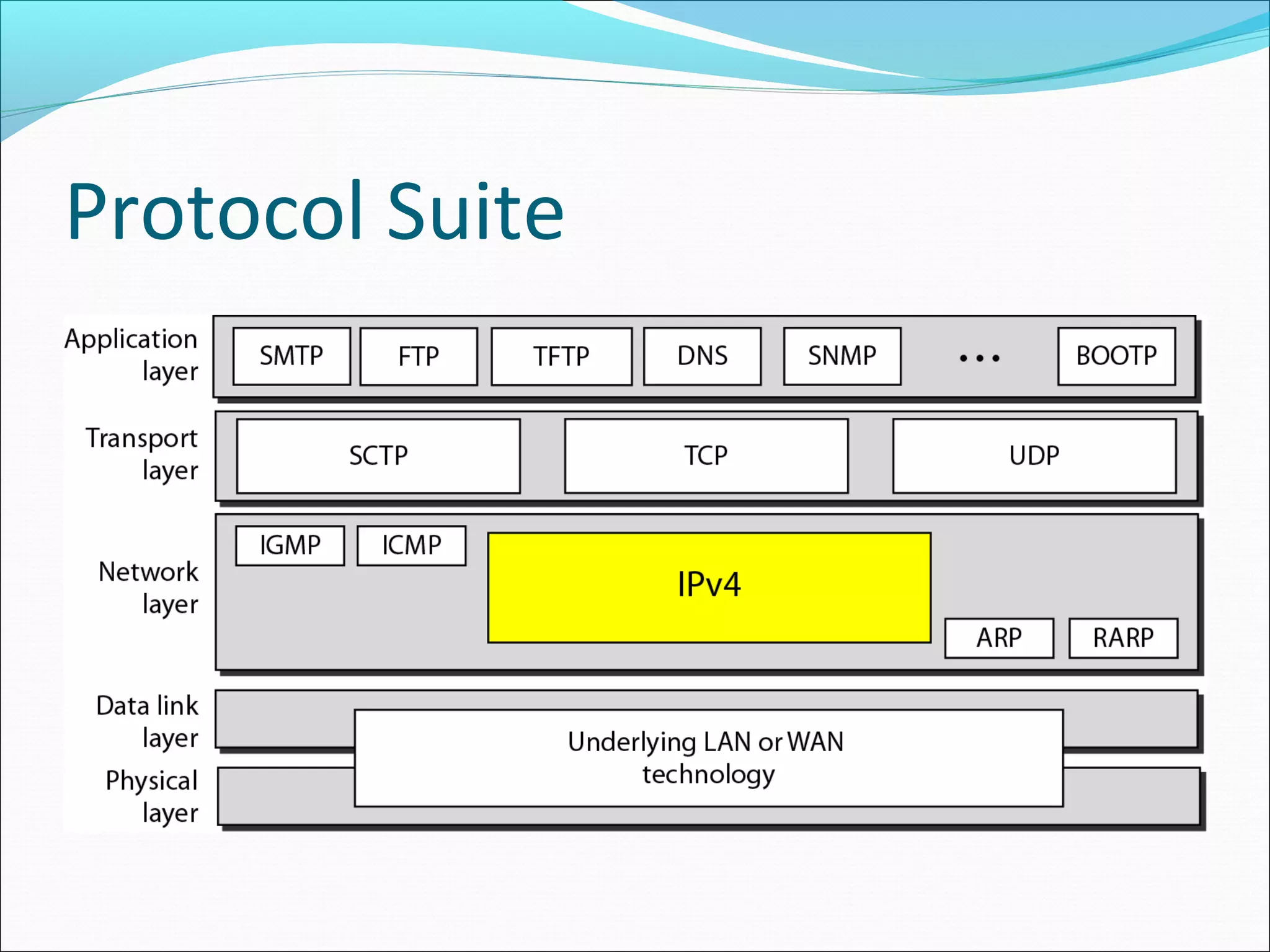
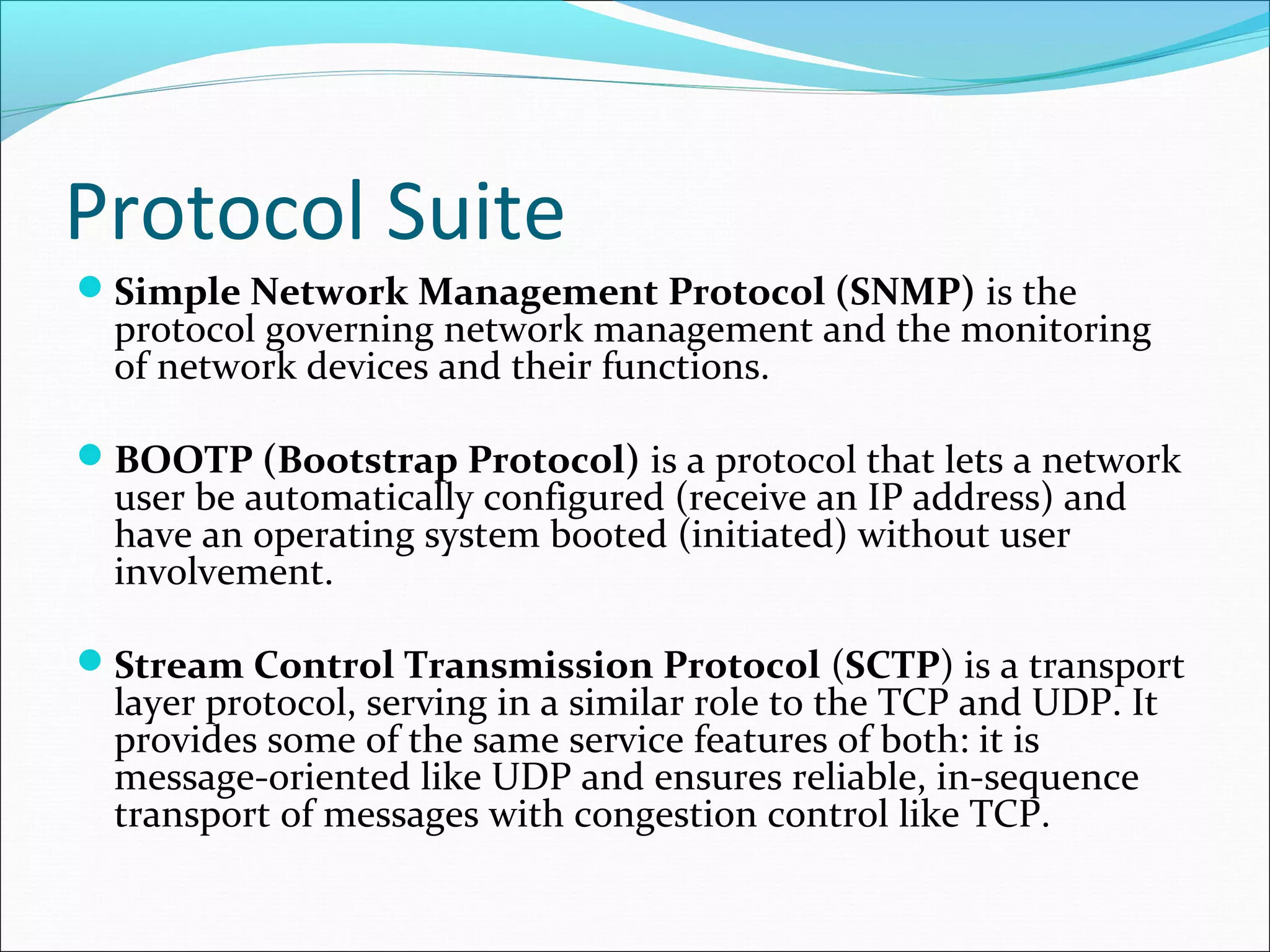
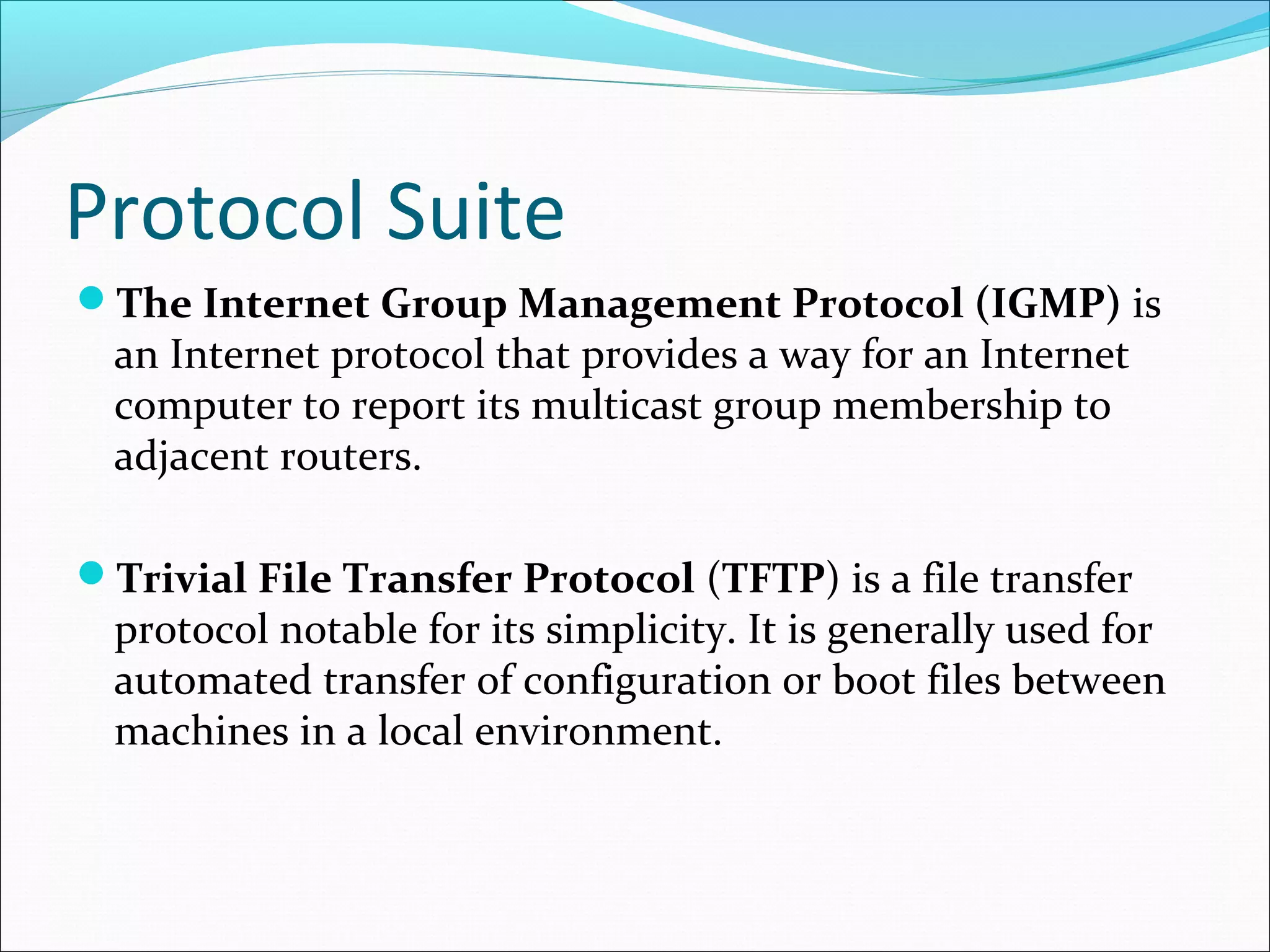
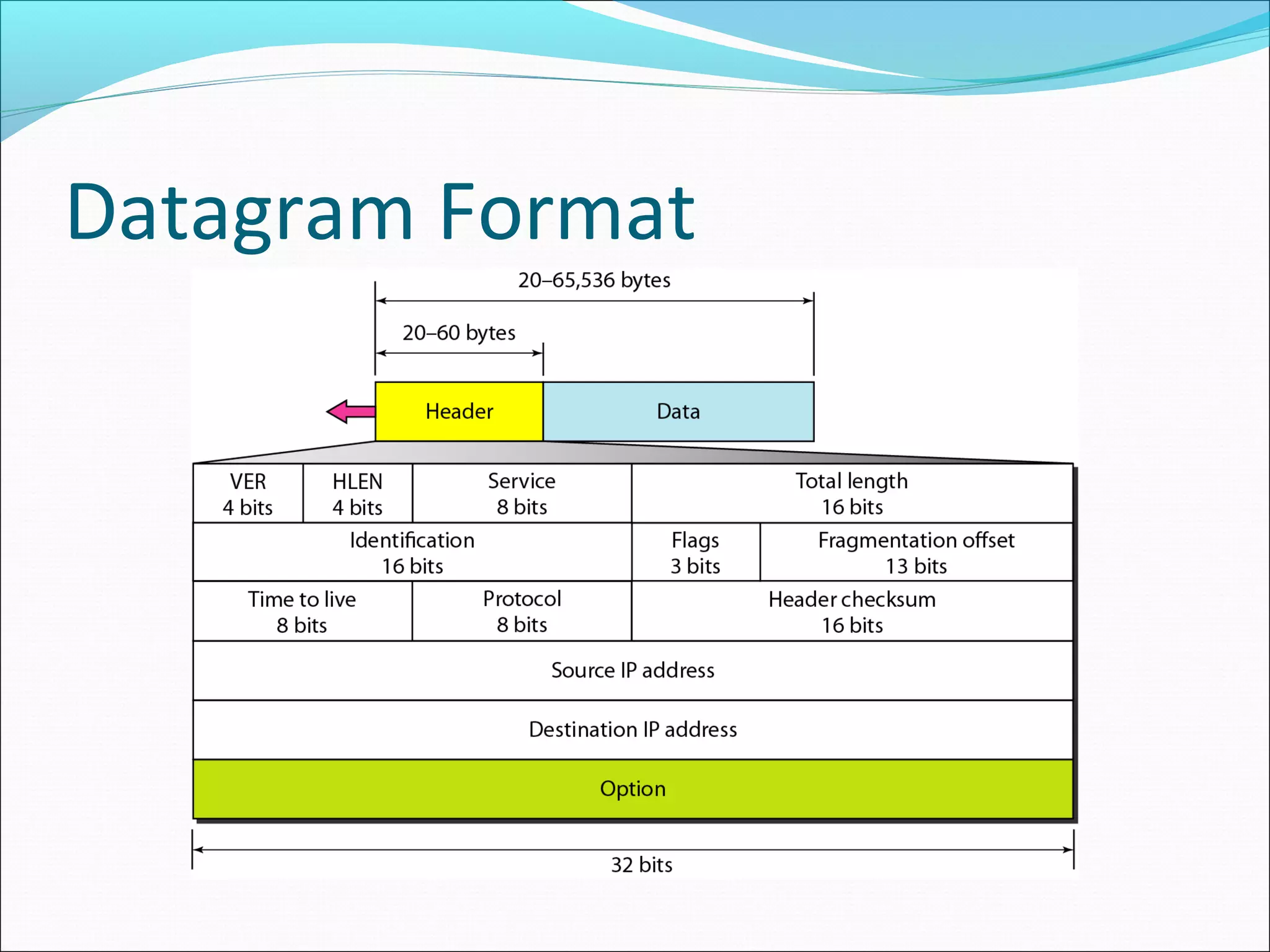
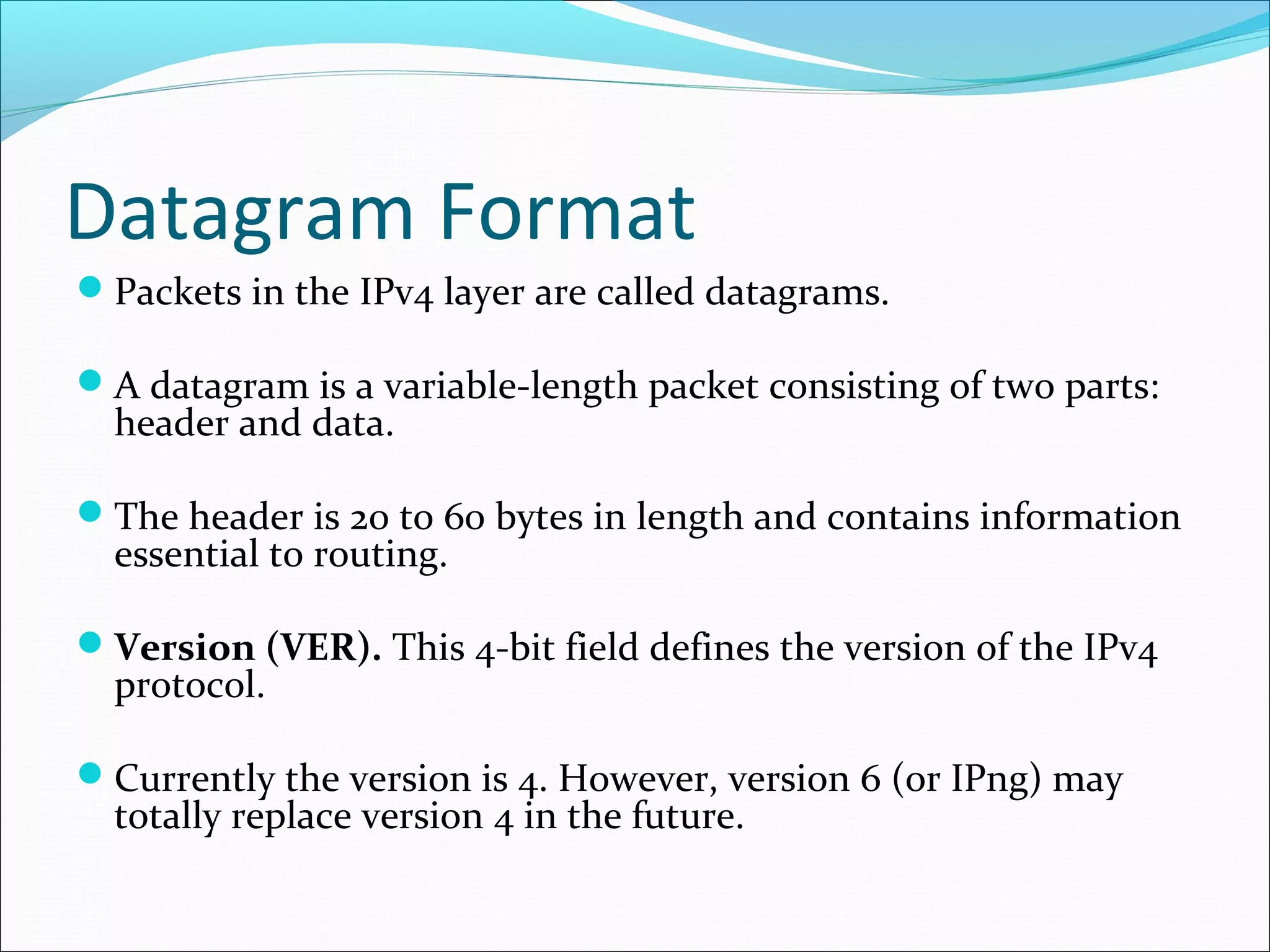
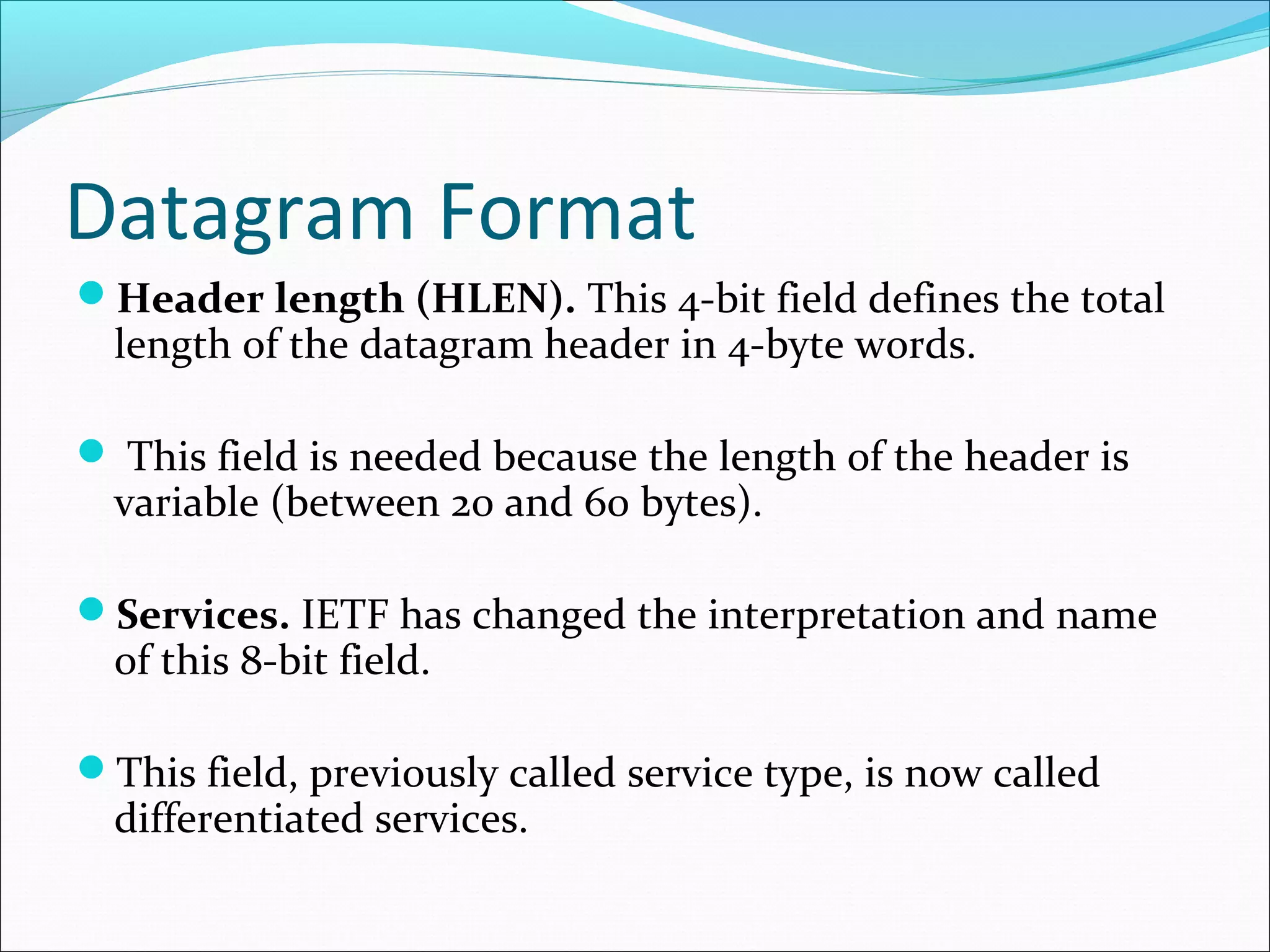
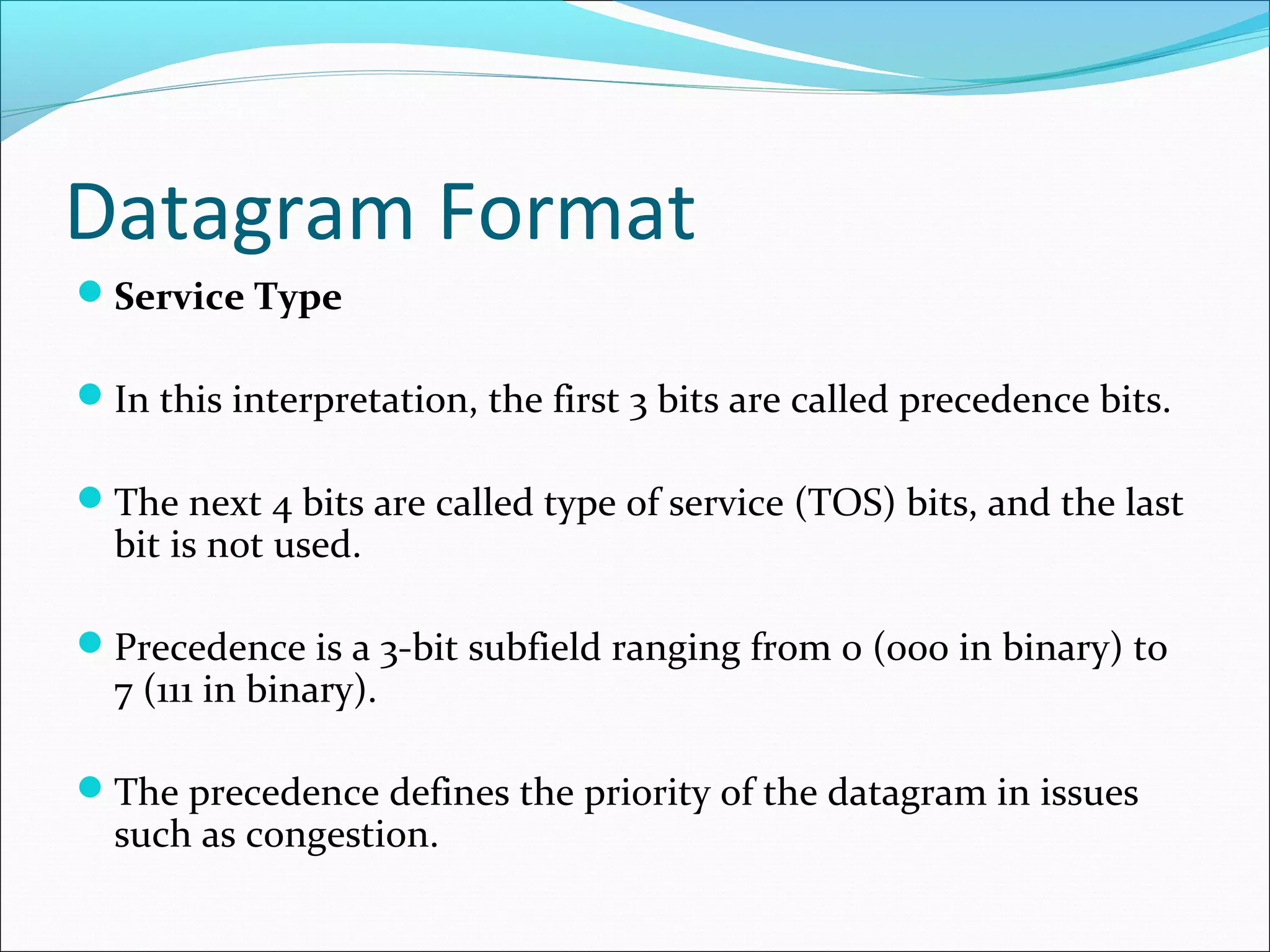
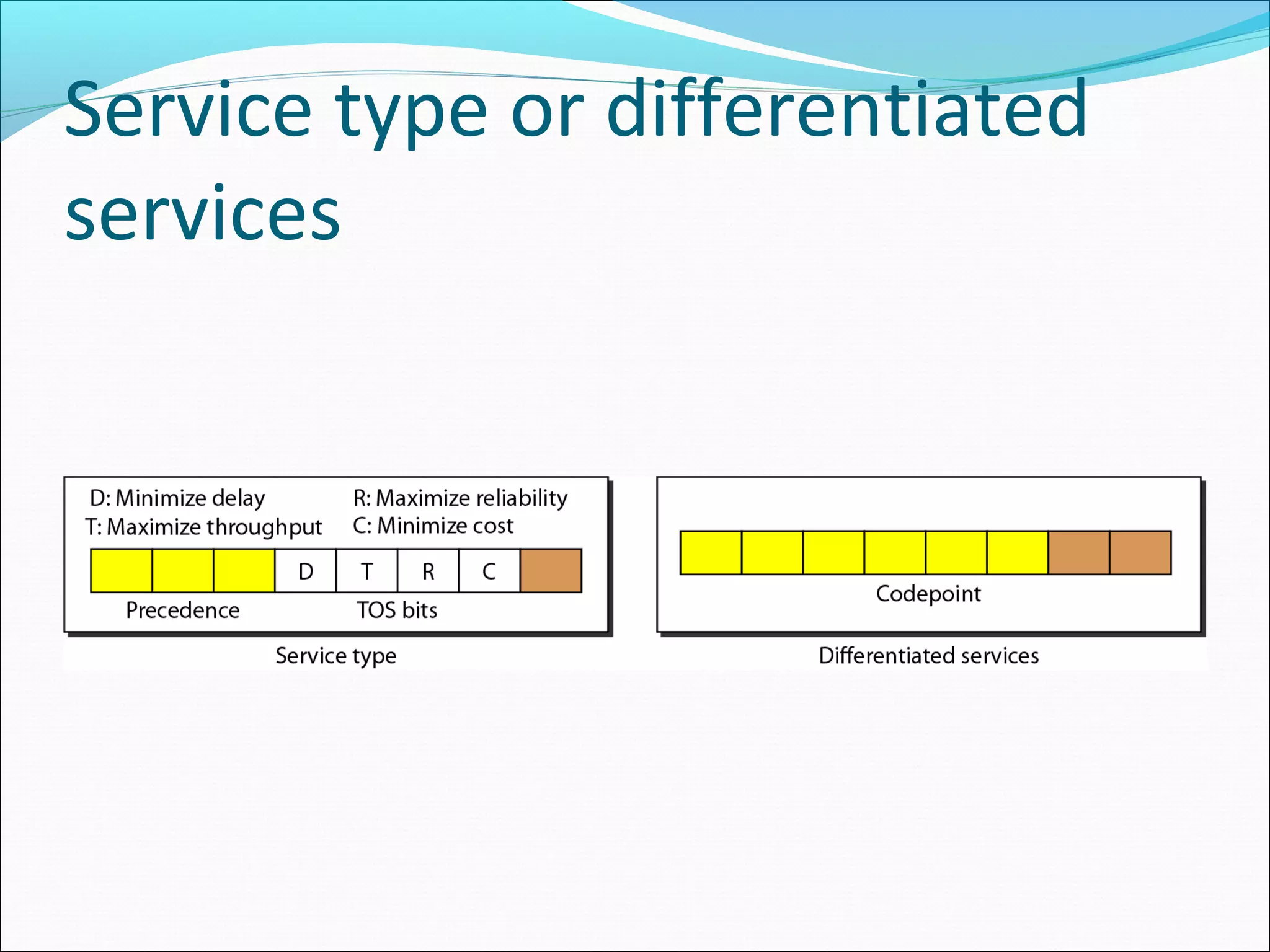
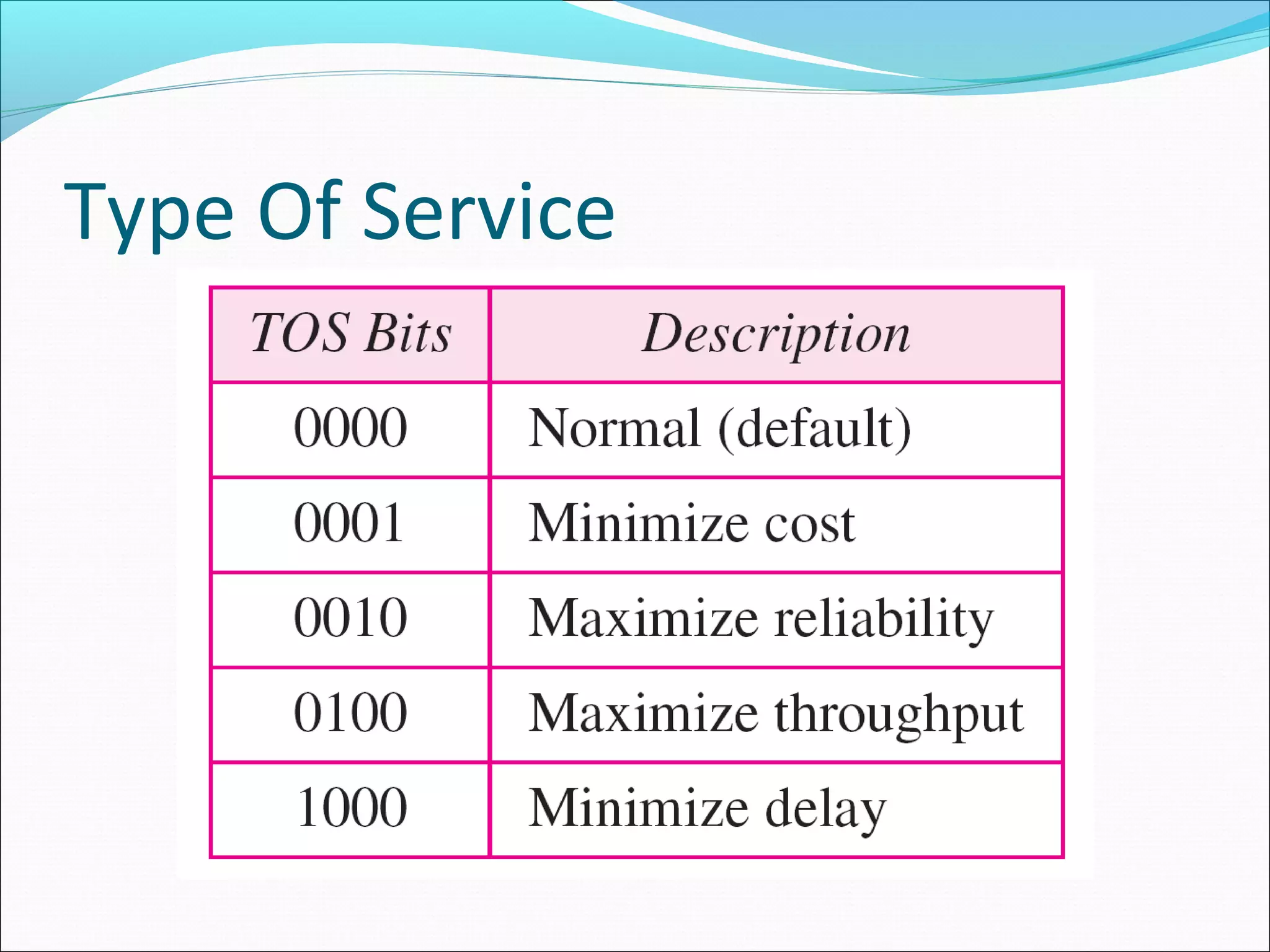
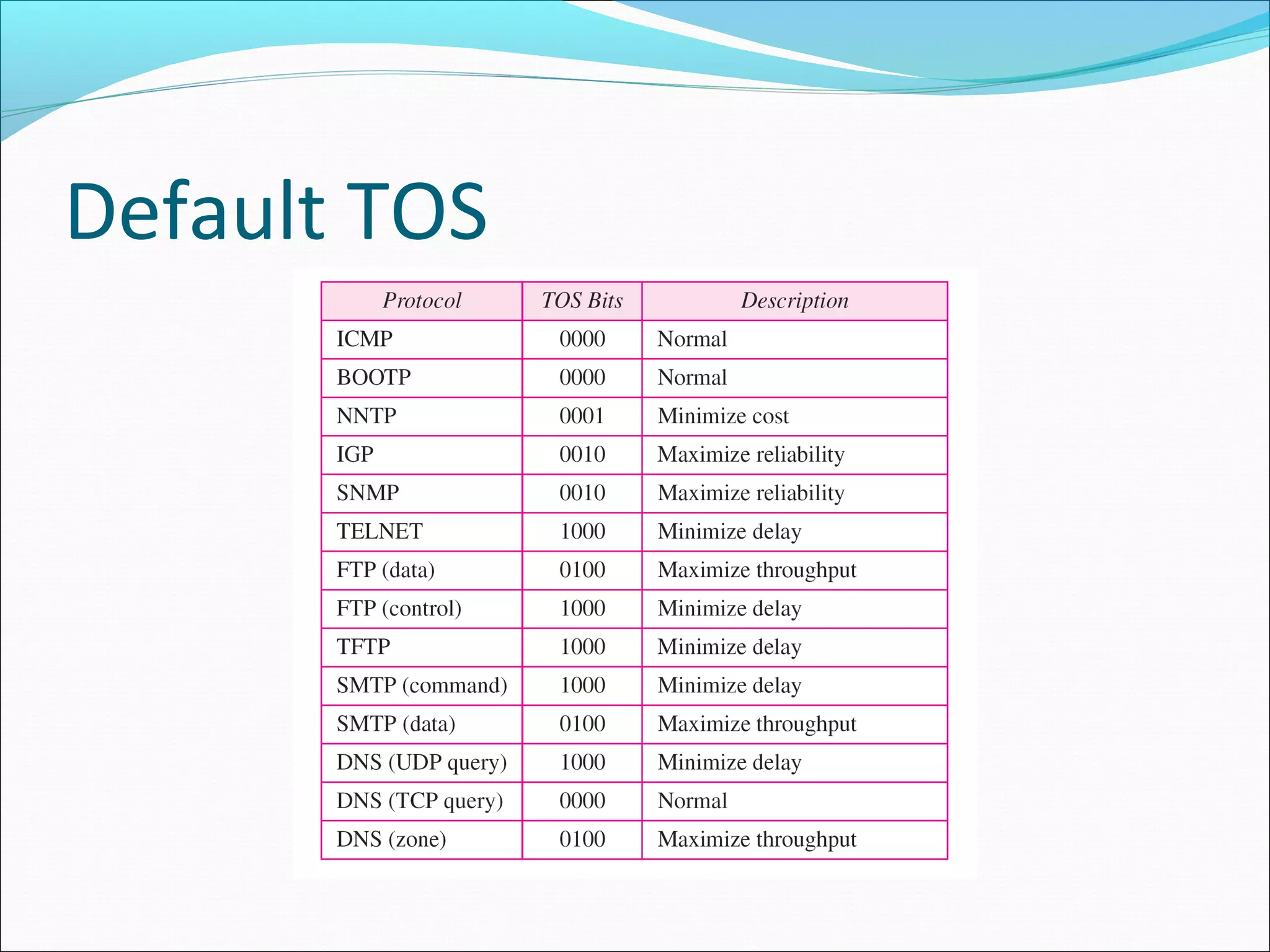
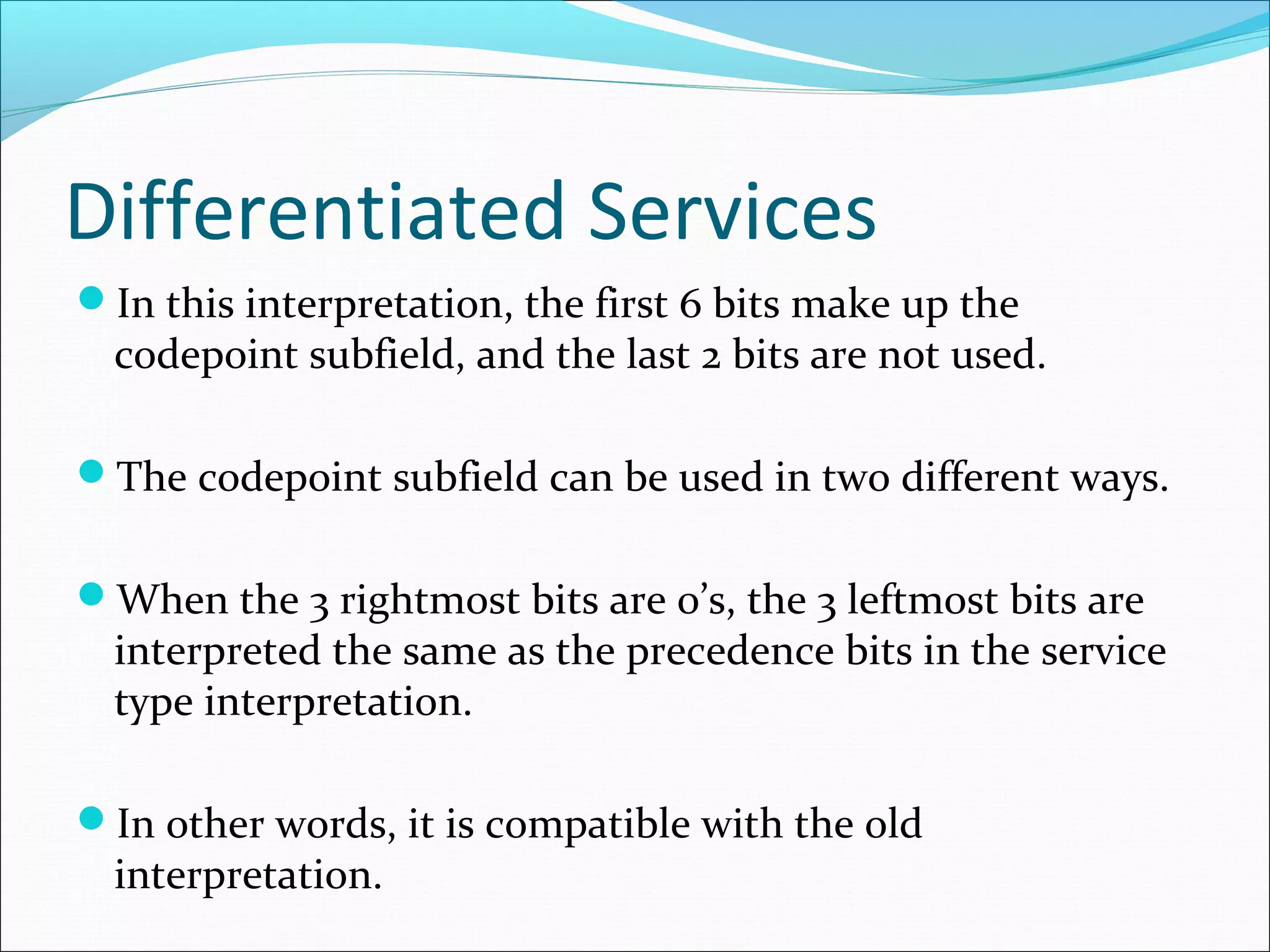
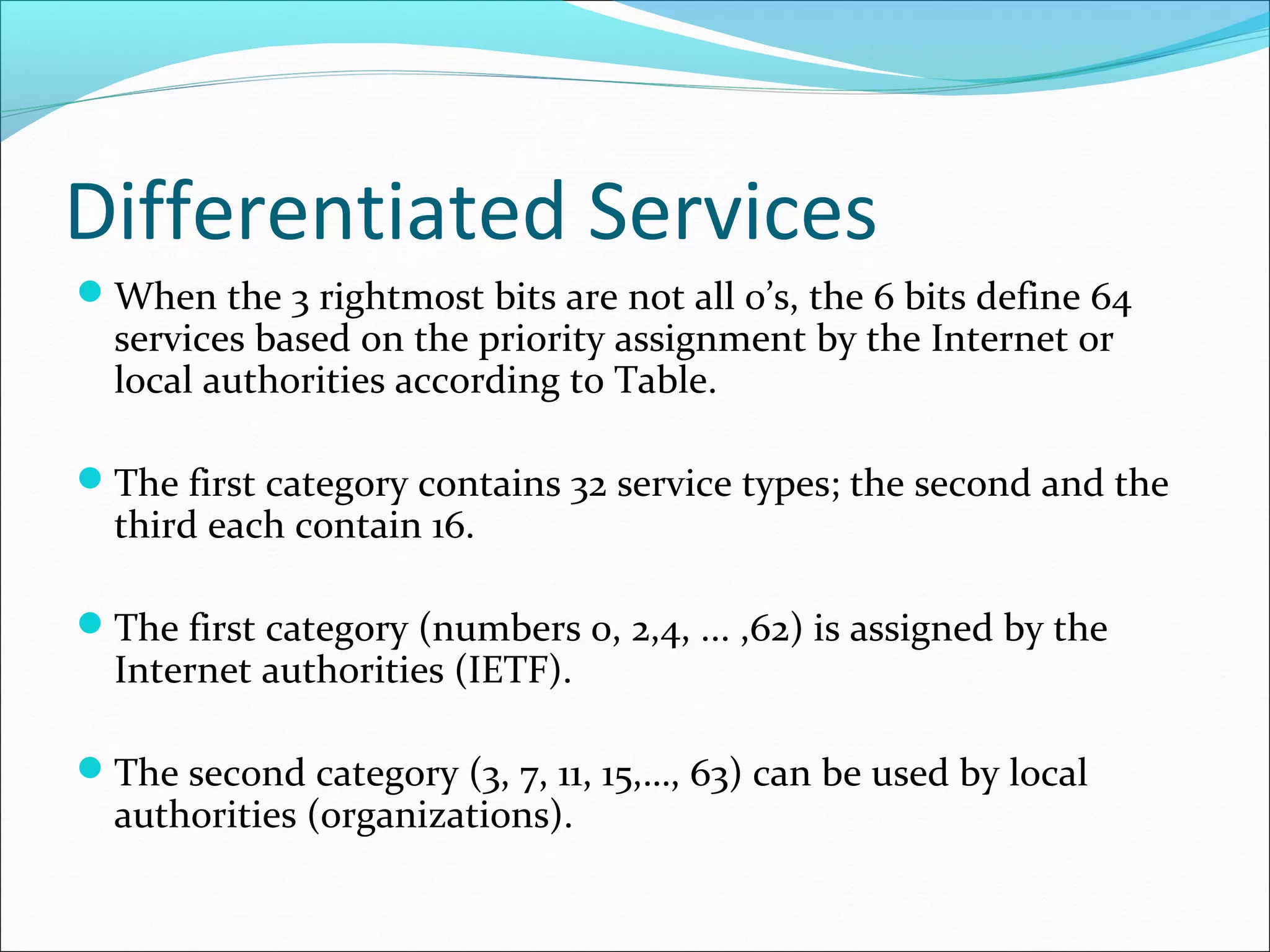
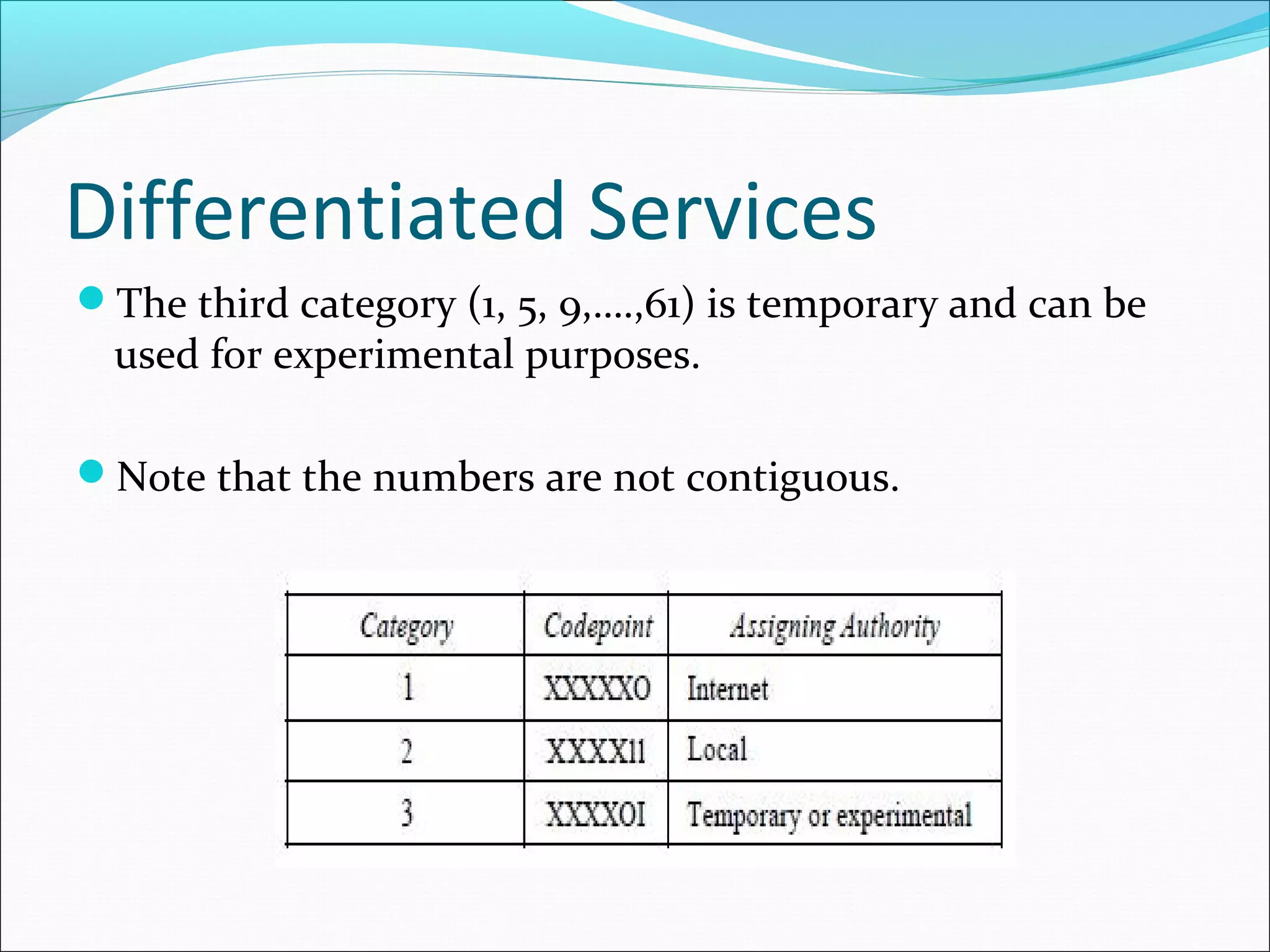
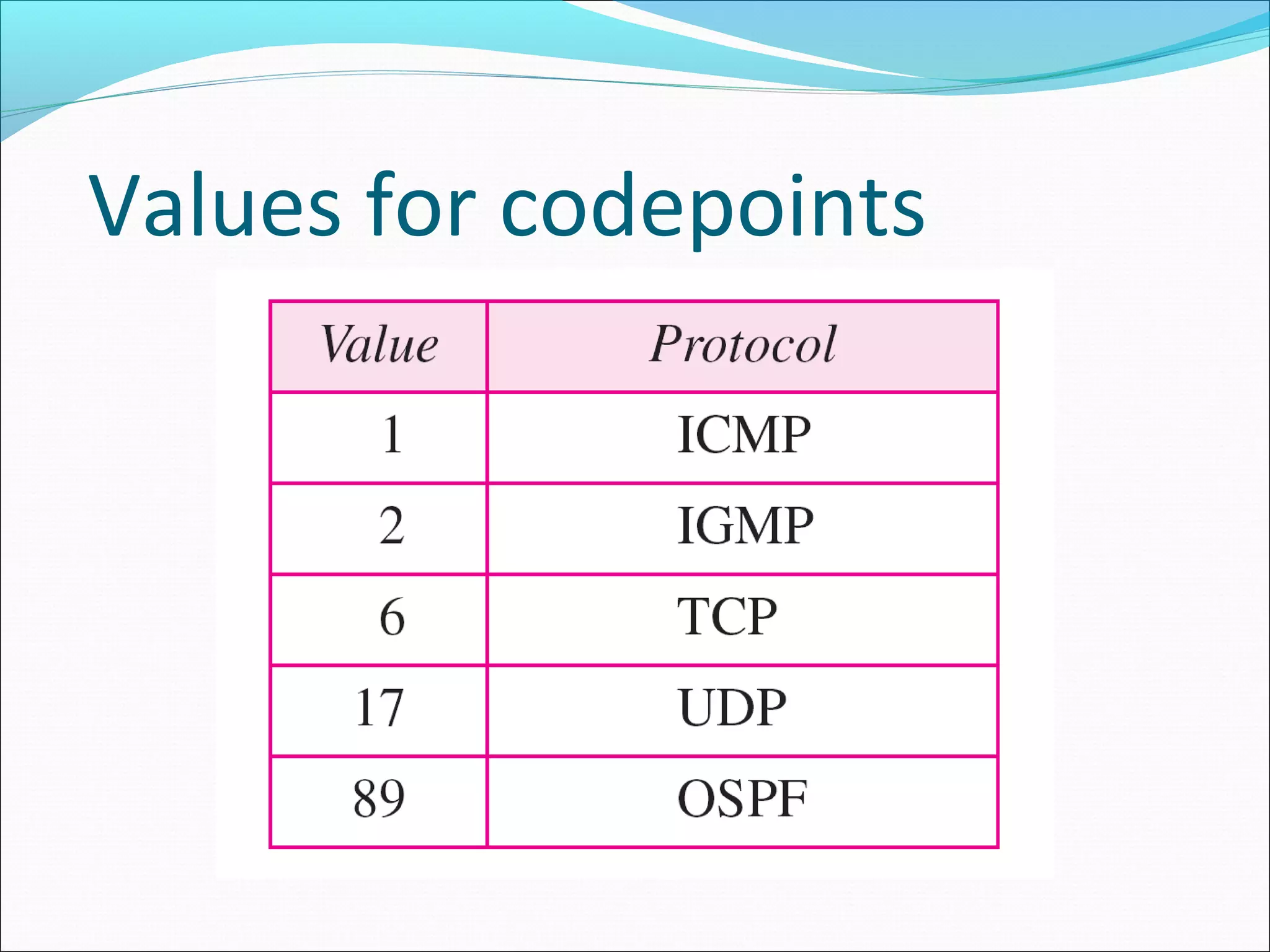
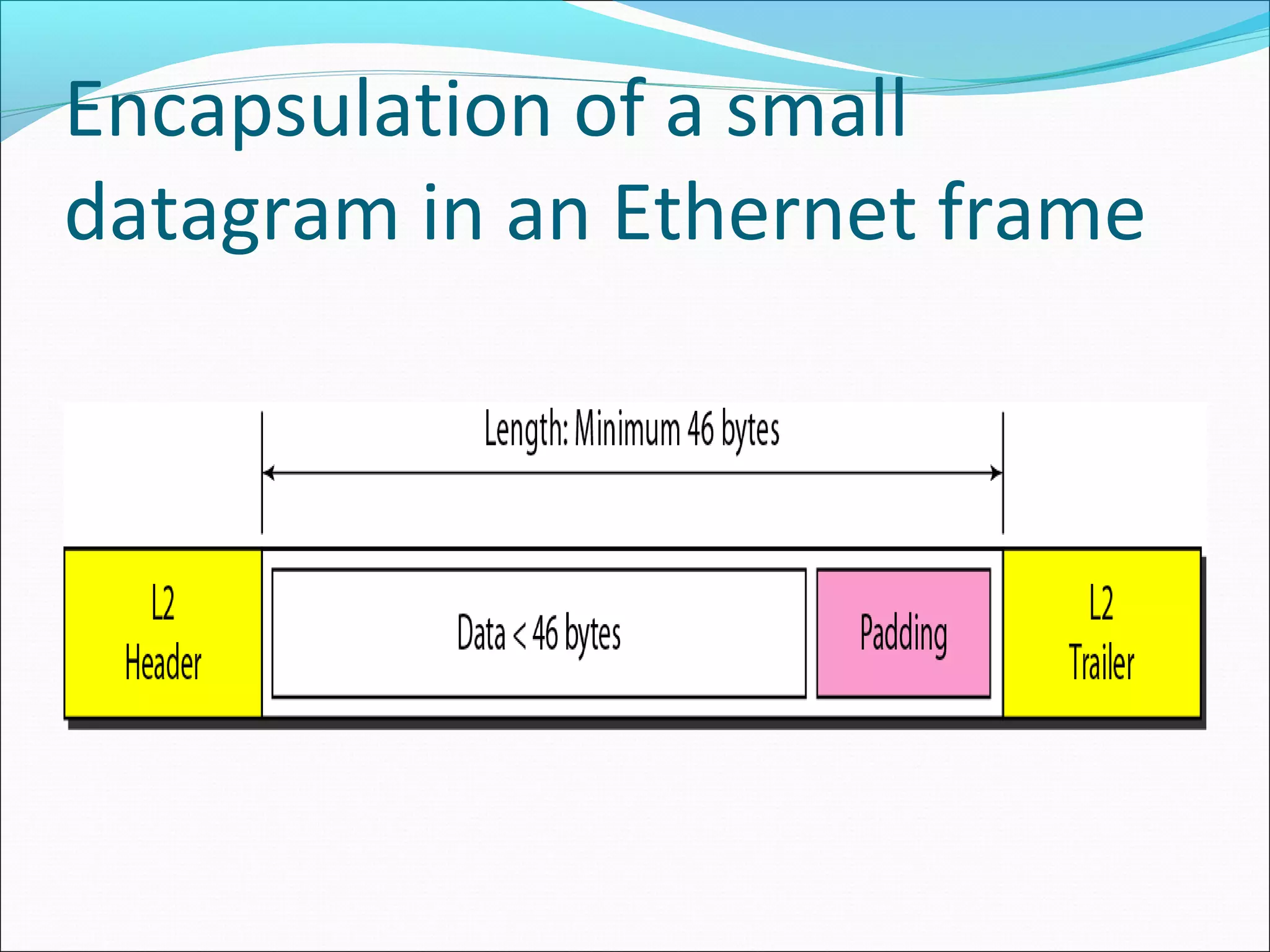
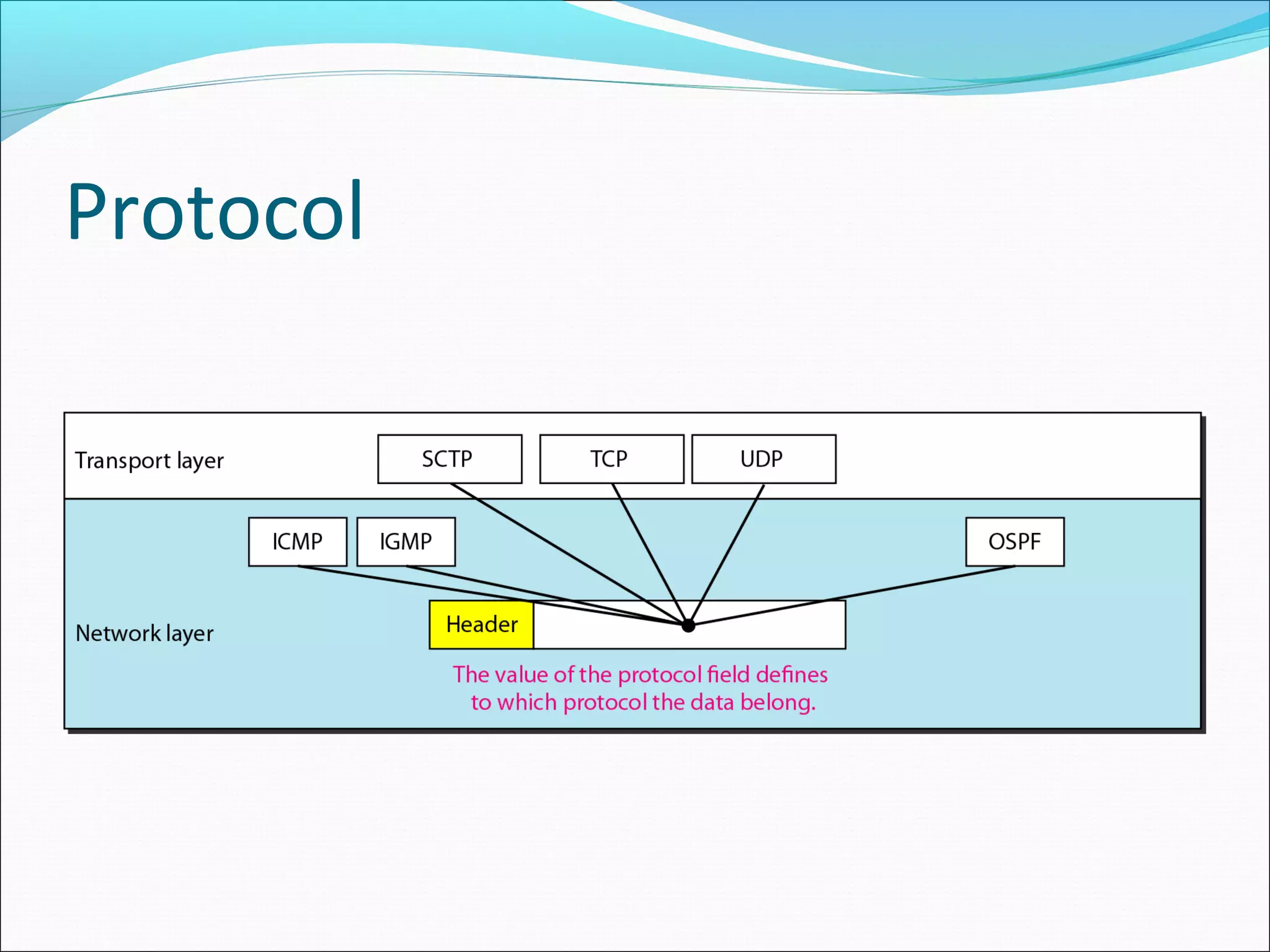
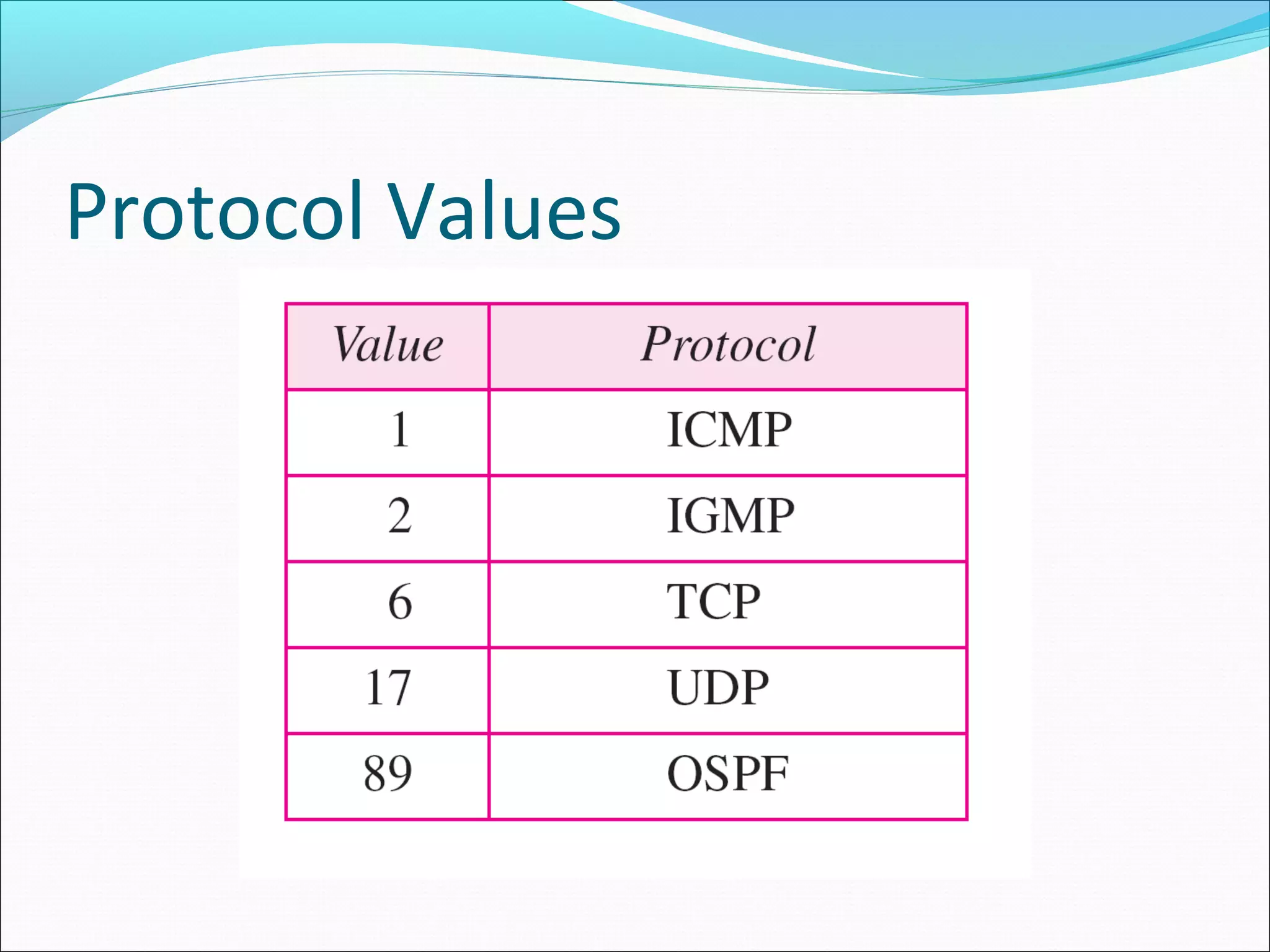
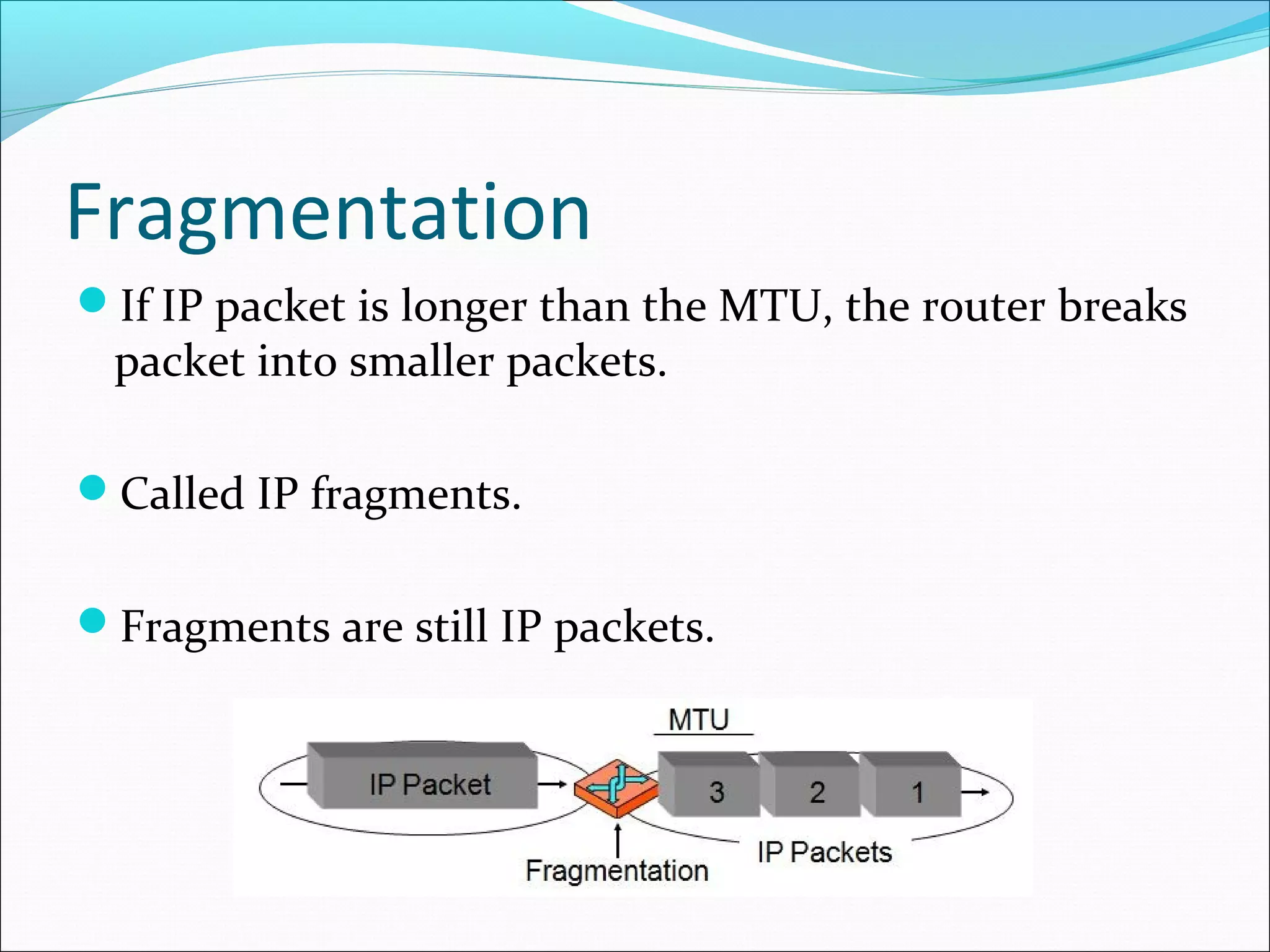
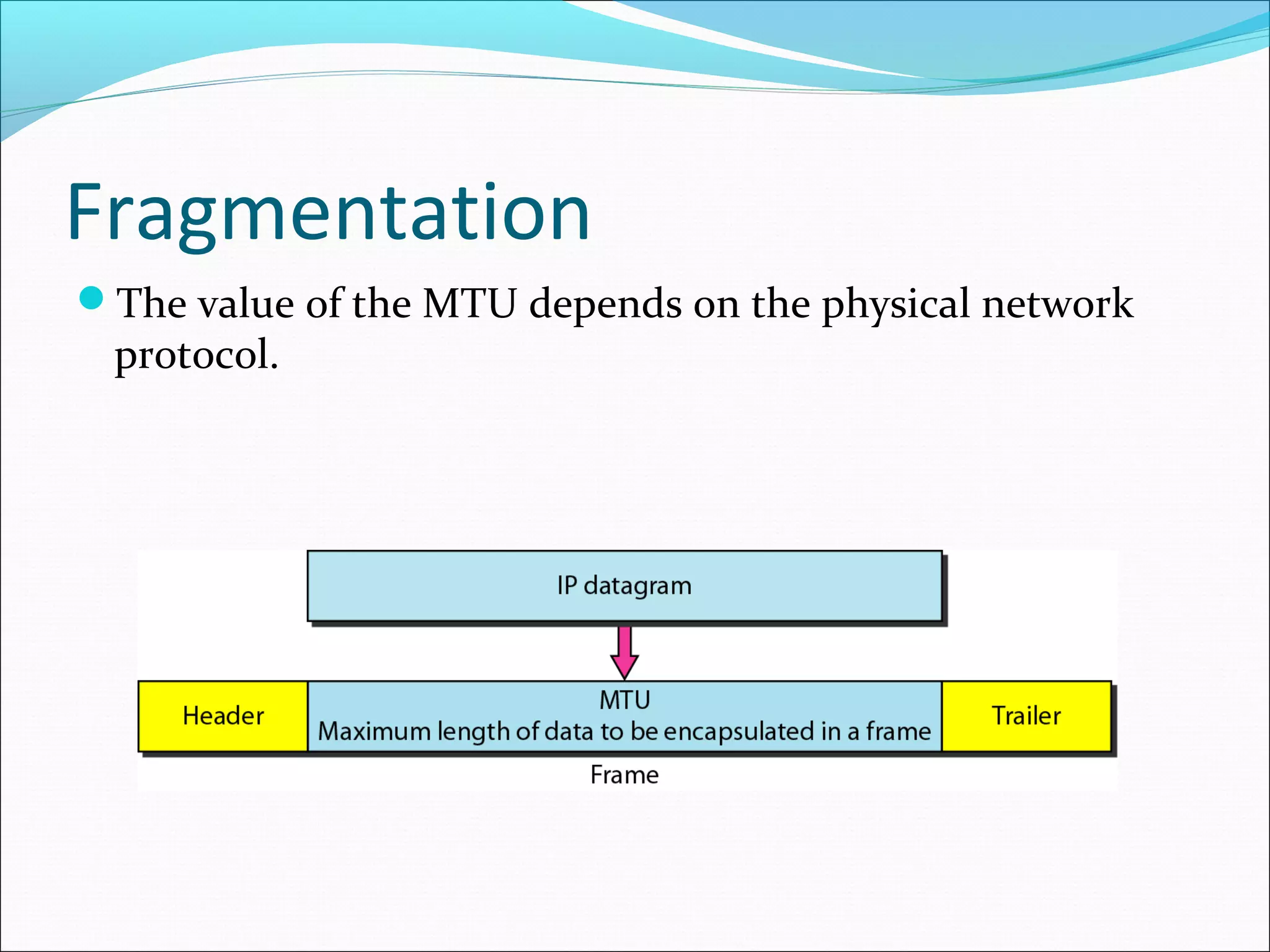
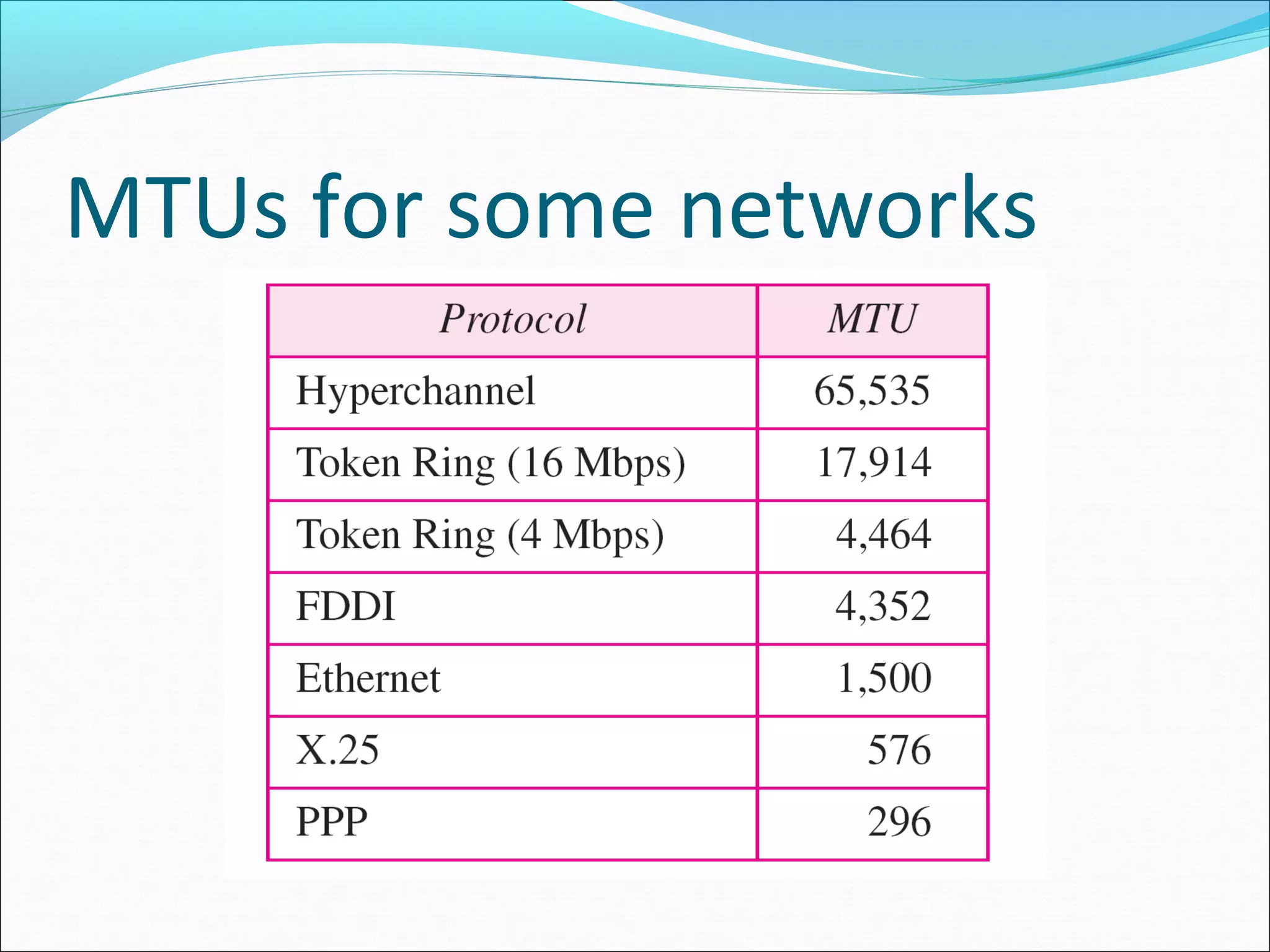
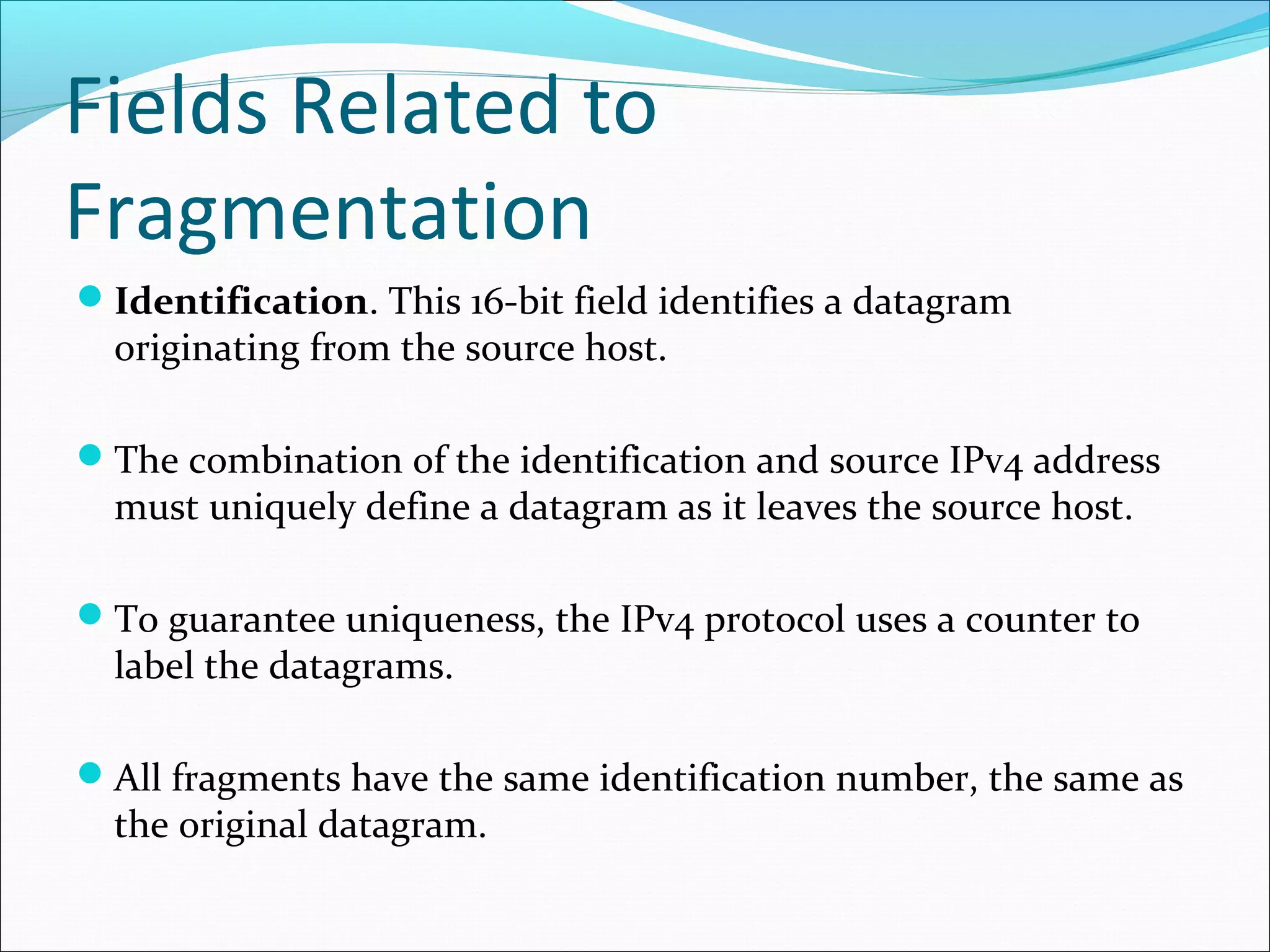
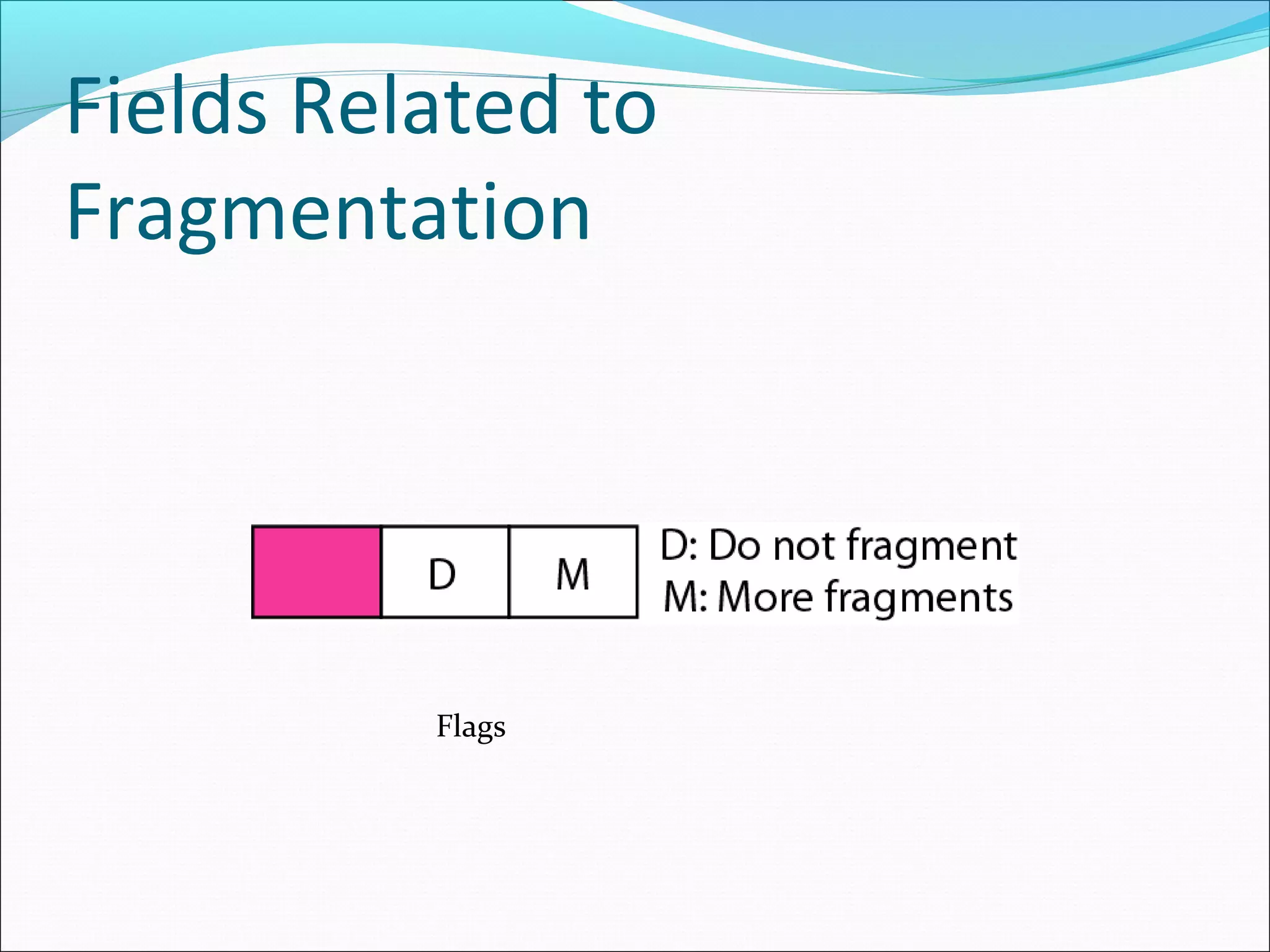
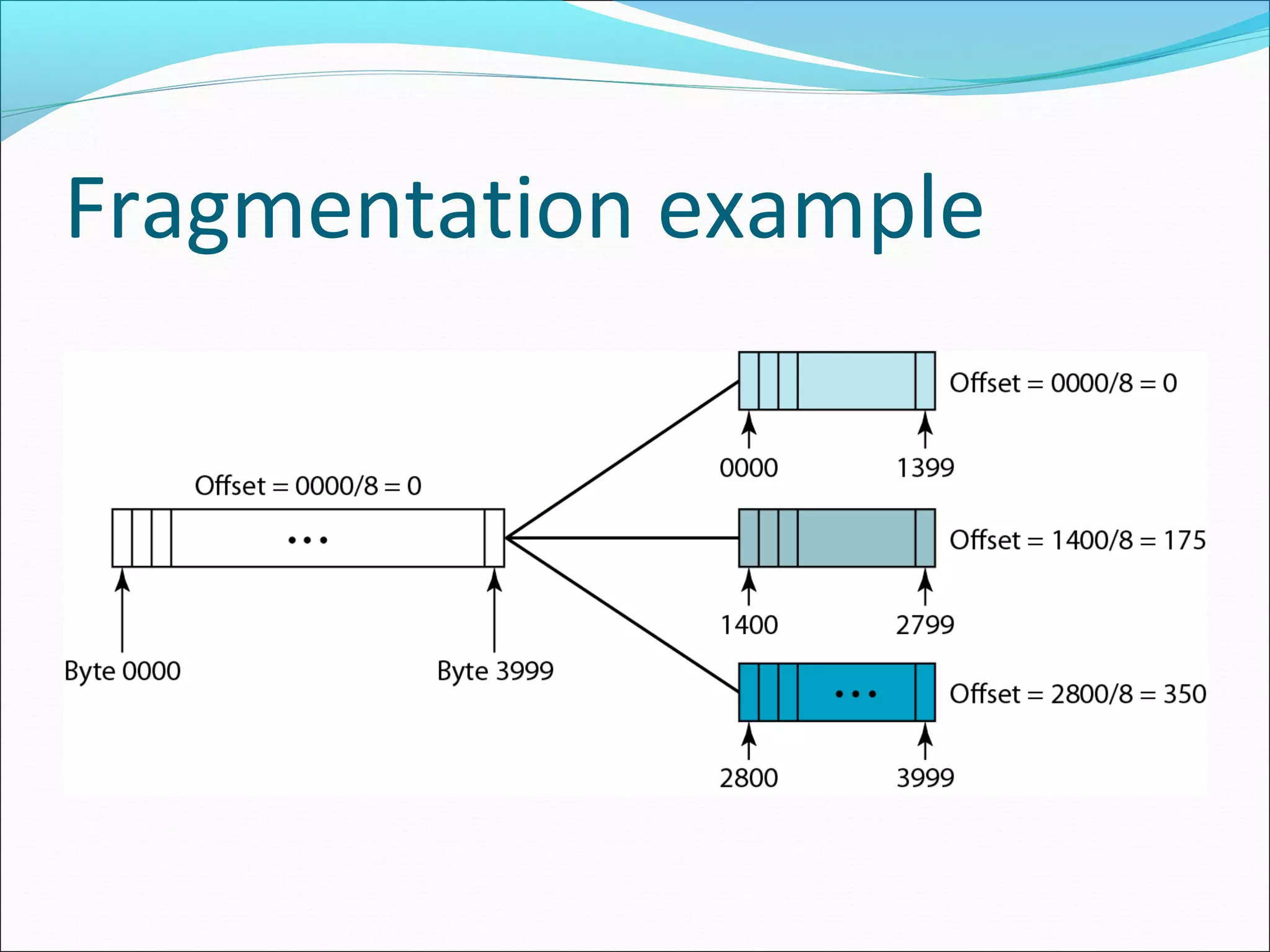
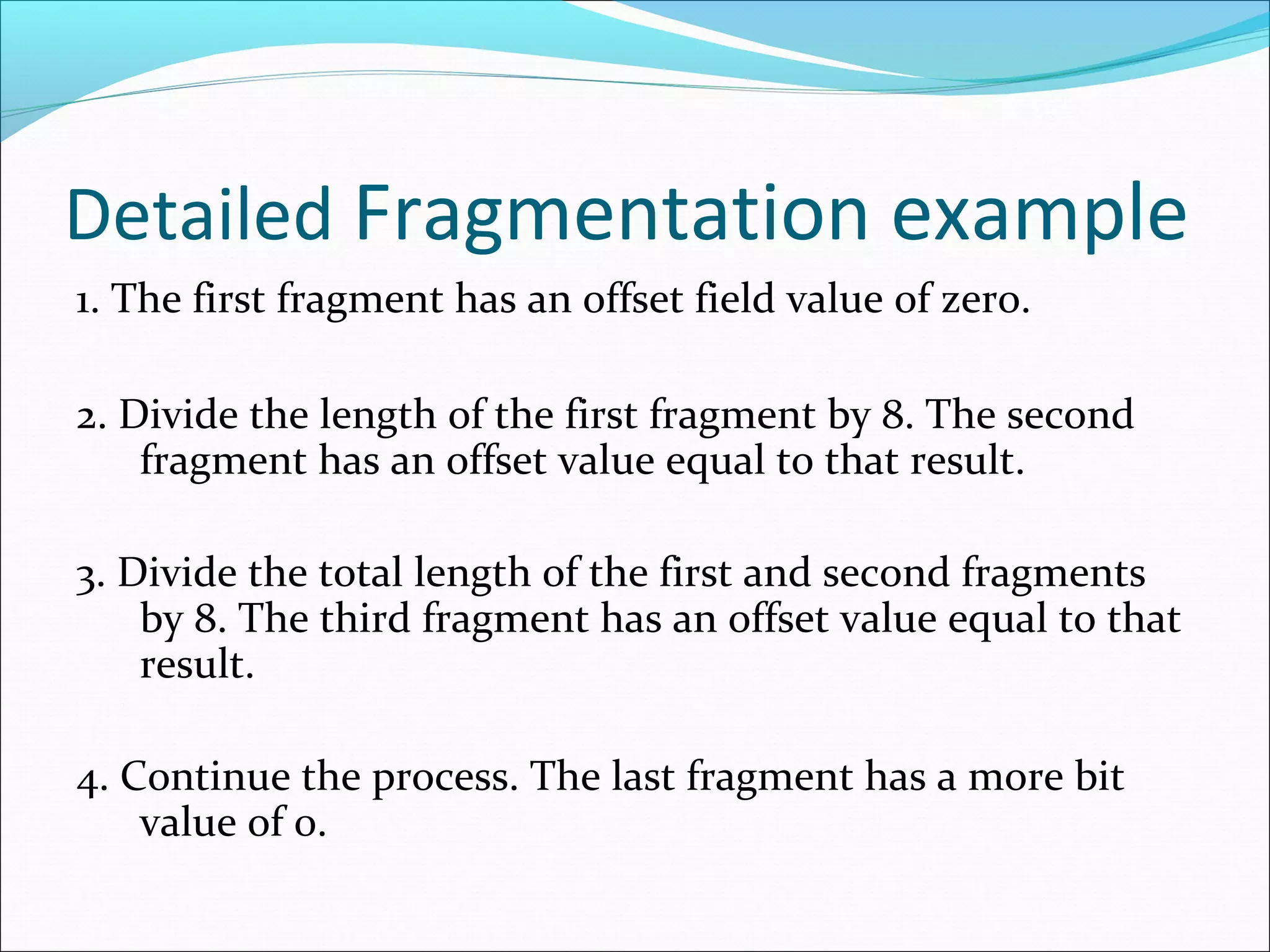
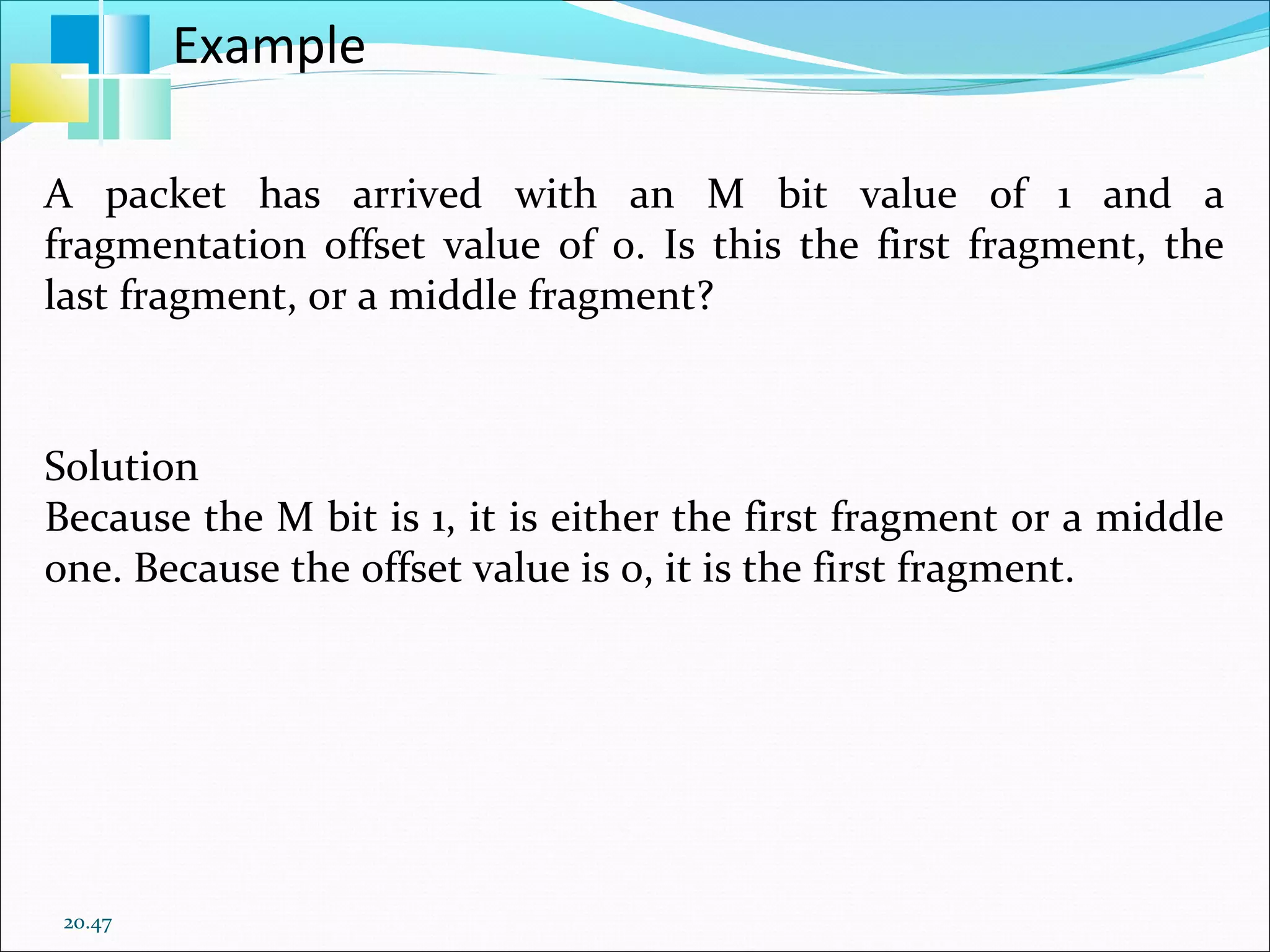
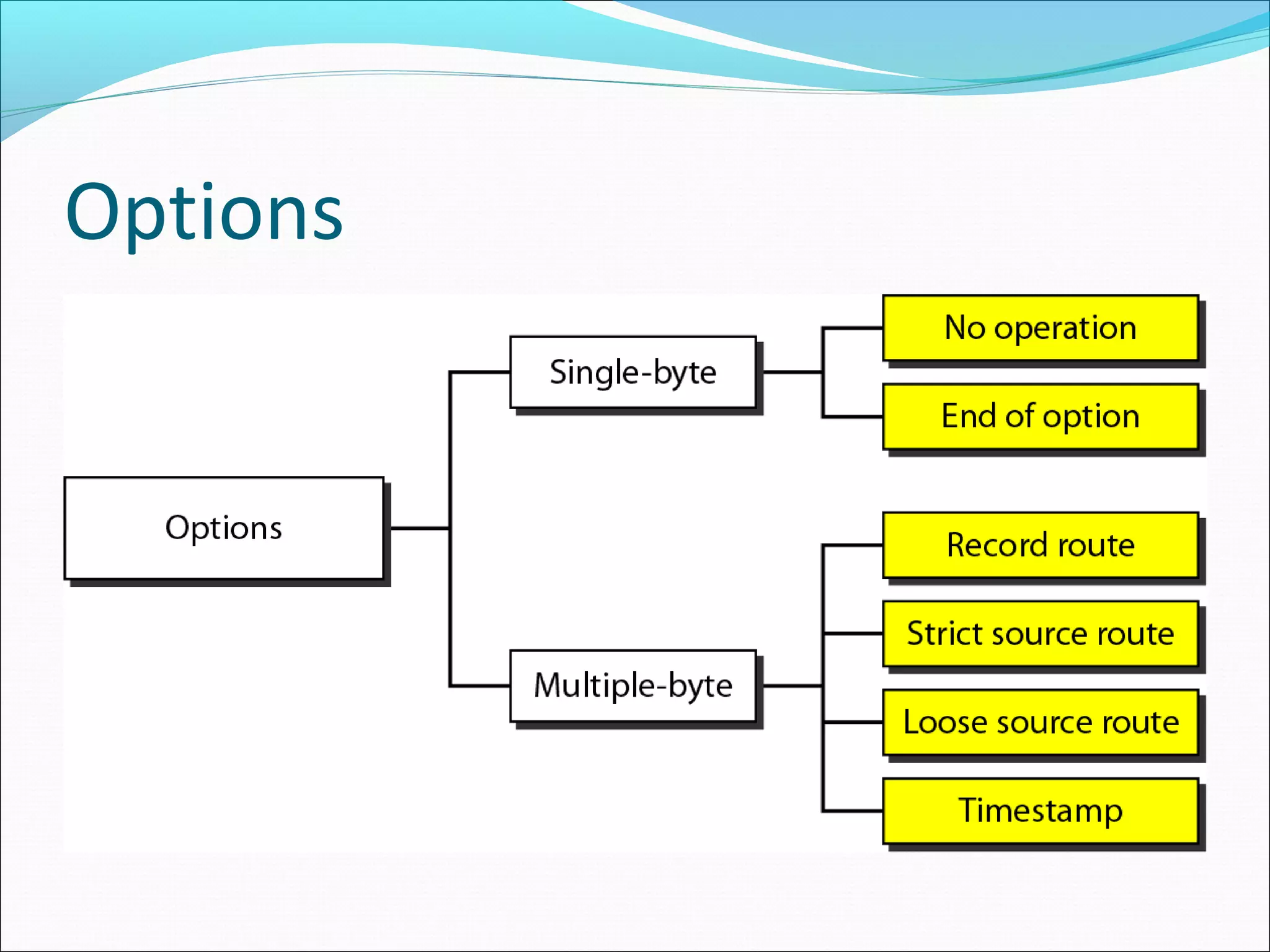
The document discusses IPv4 and its datagram format. It explains that IPv4 is a best-effort, connectionless protocol that provides no error control or flow control. The datagram format includes a header containing fields like version, header length, total length, protocol, source/destination addresses, and an optional data field. It describes fields related to fragmentation, checksum calculation, and optional header fields like timestamps and routing options.