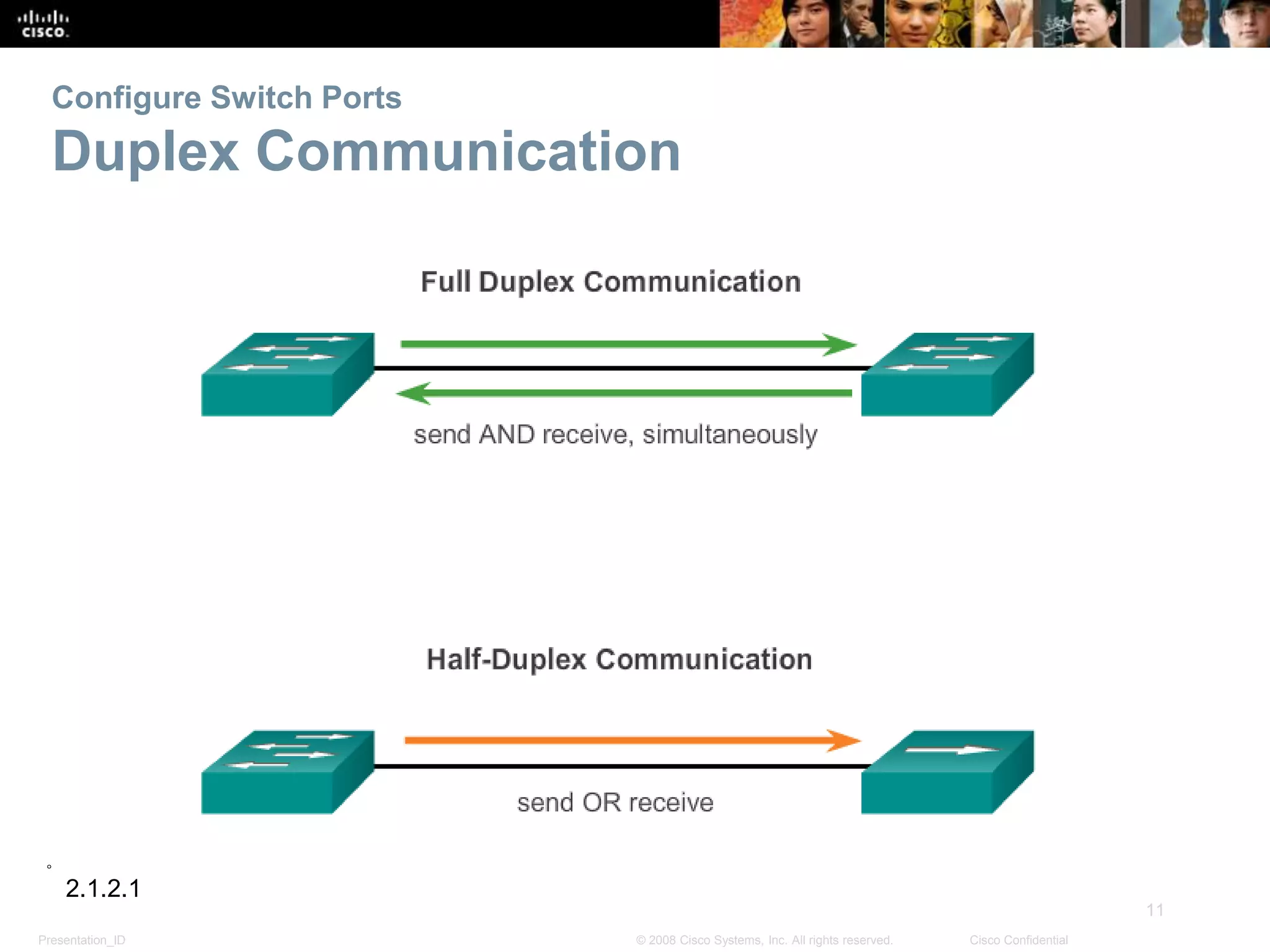
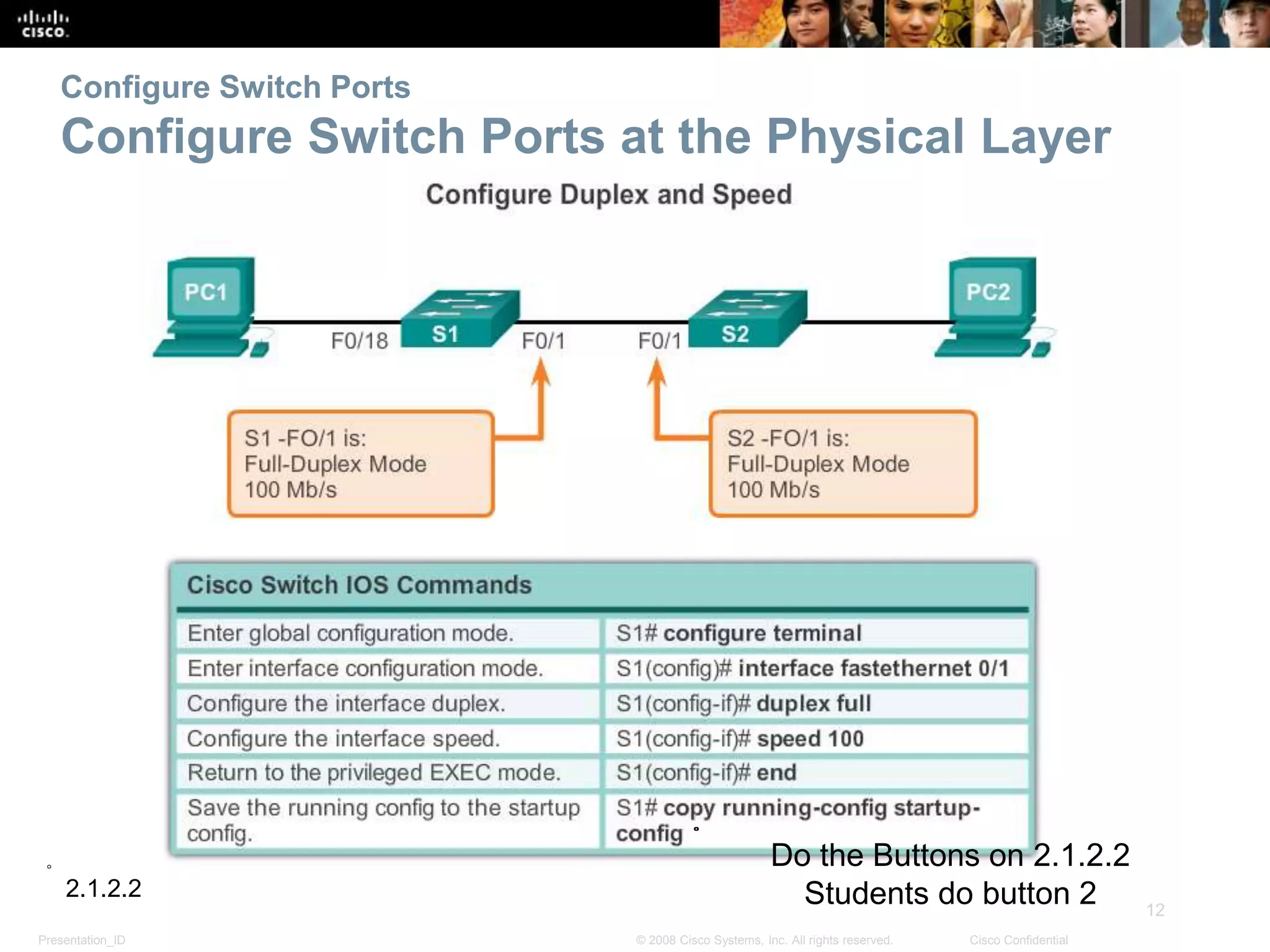
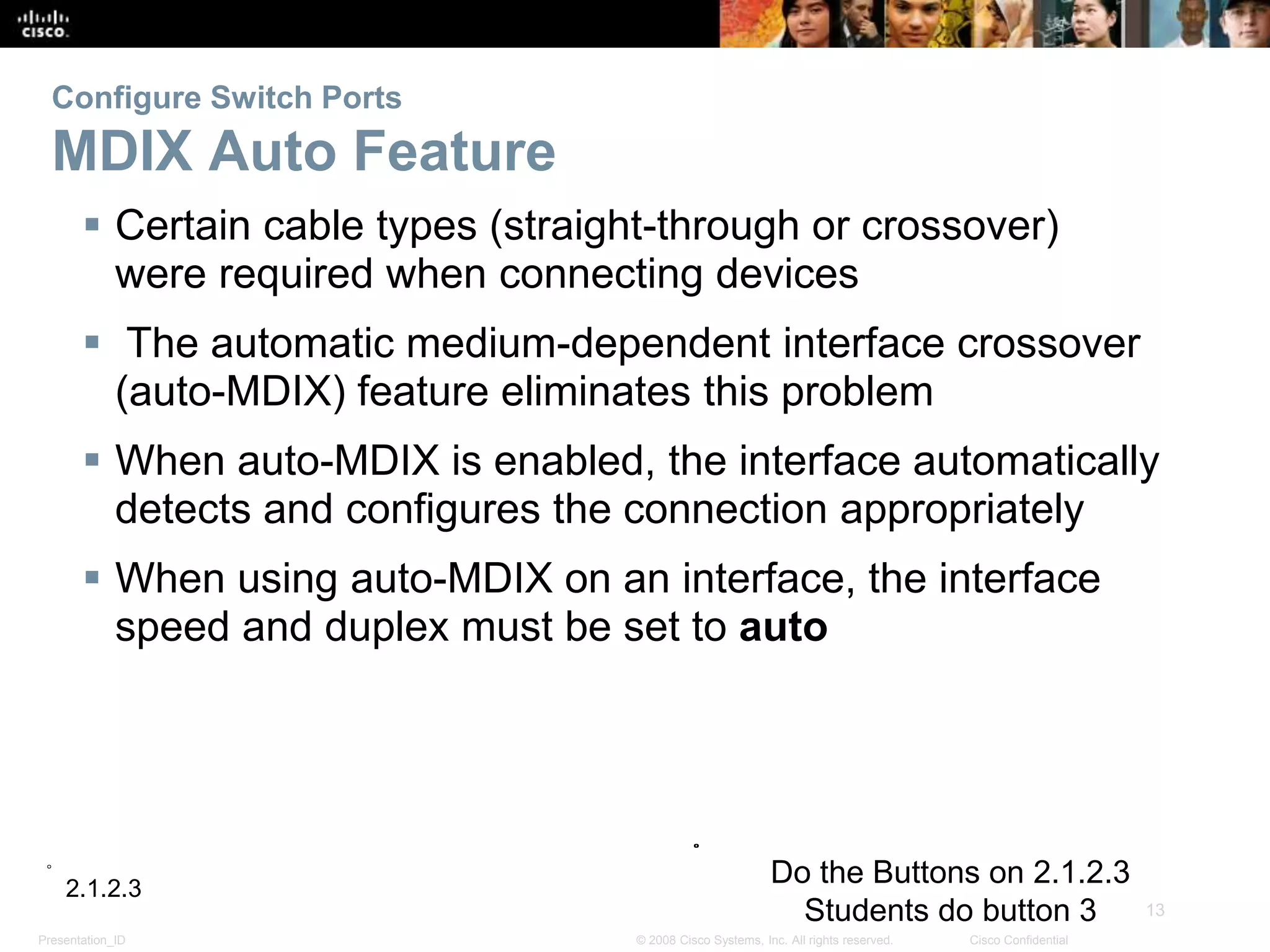
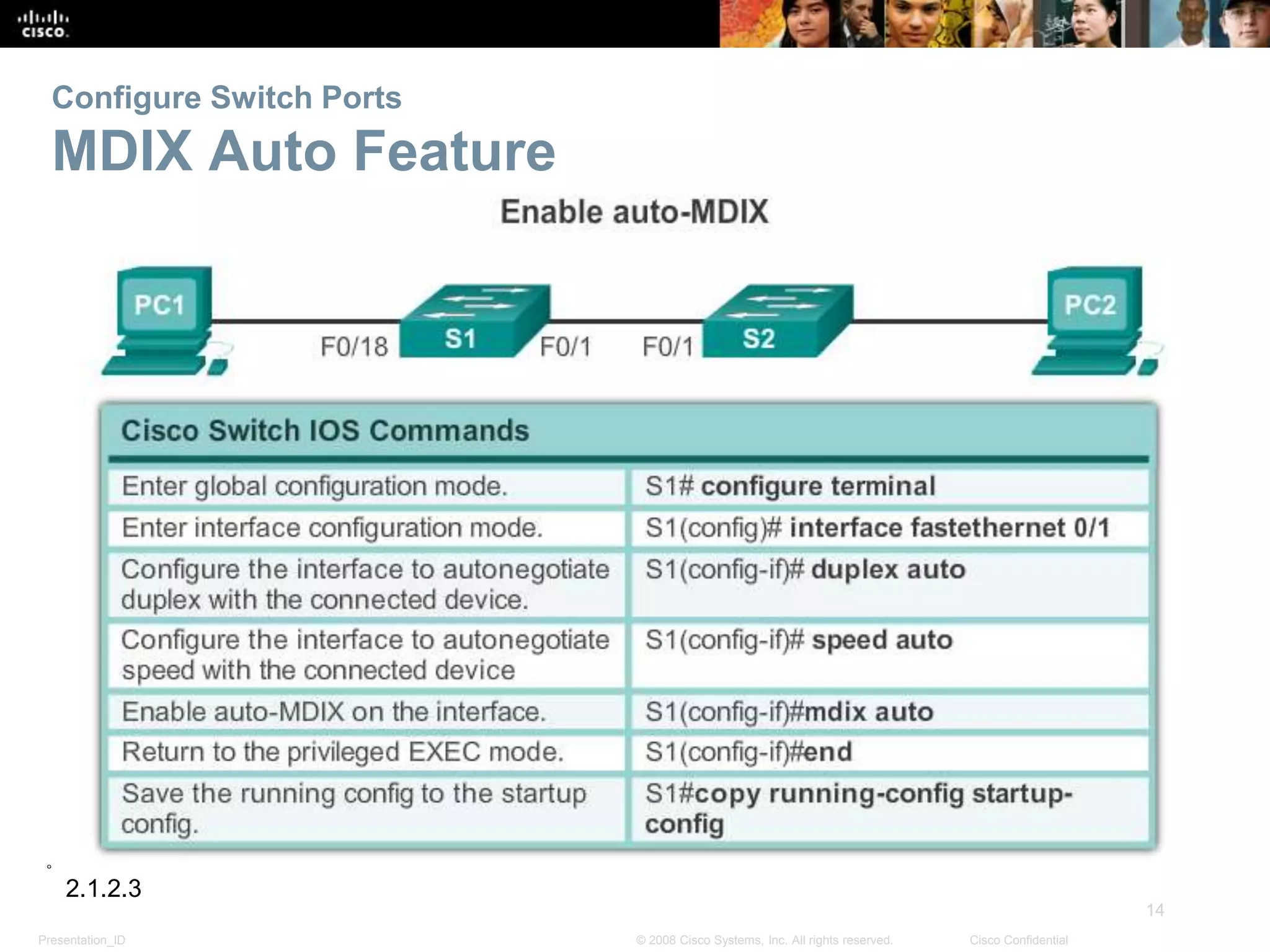
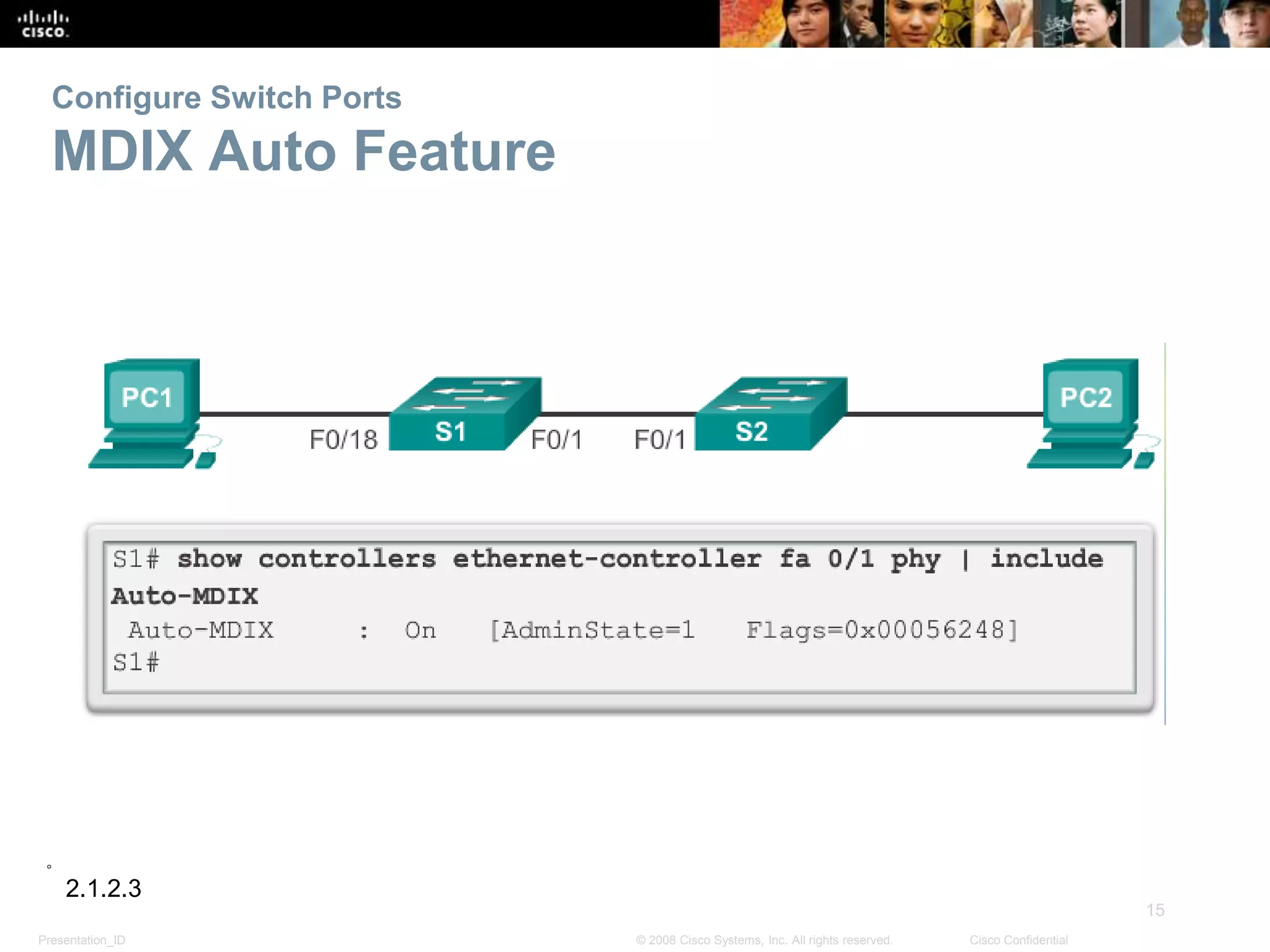
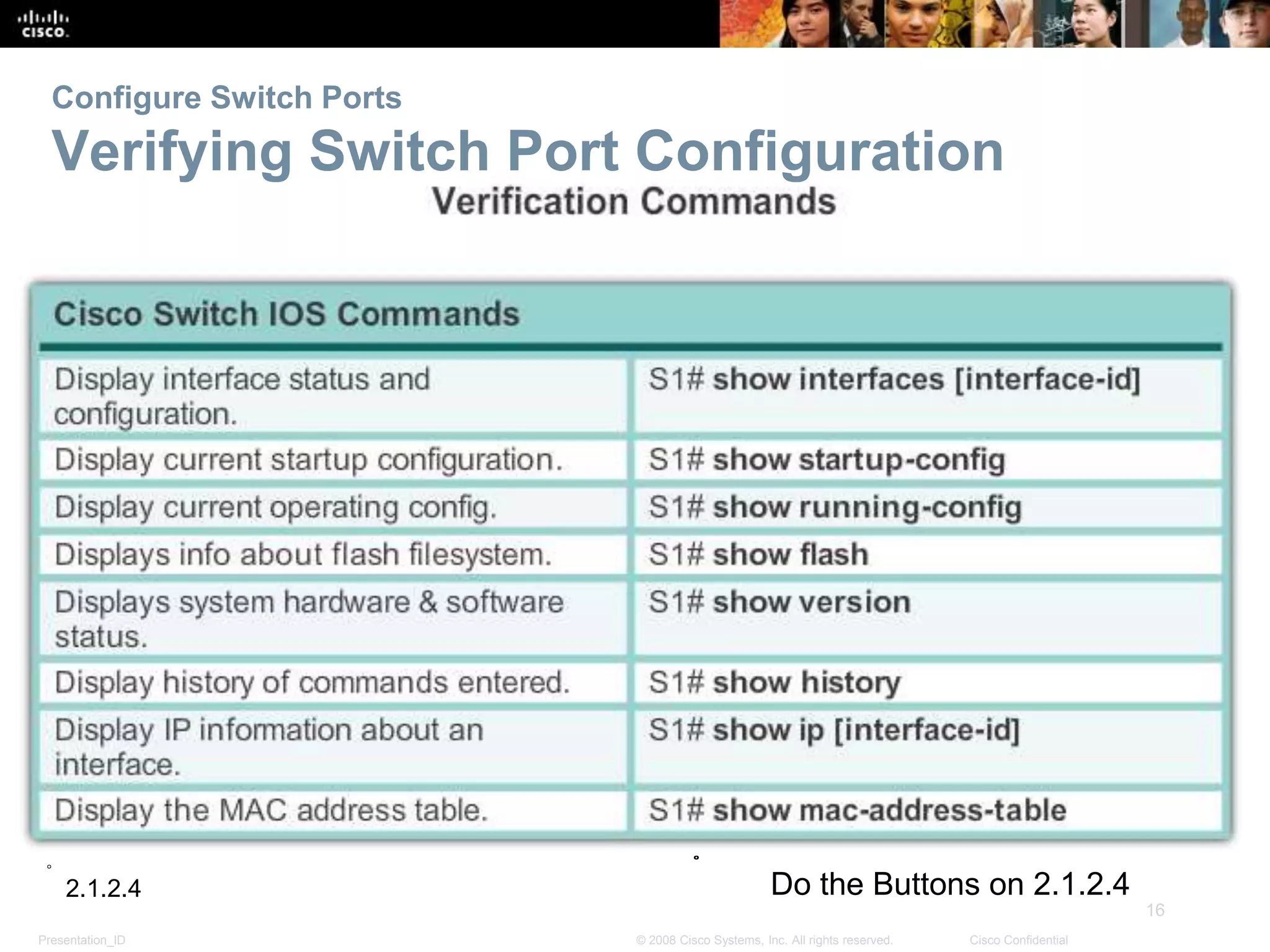
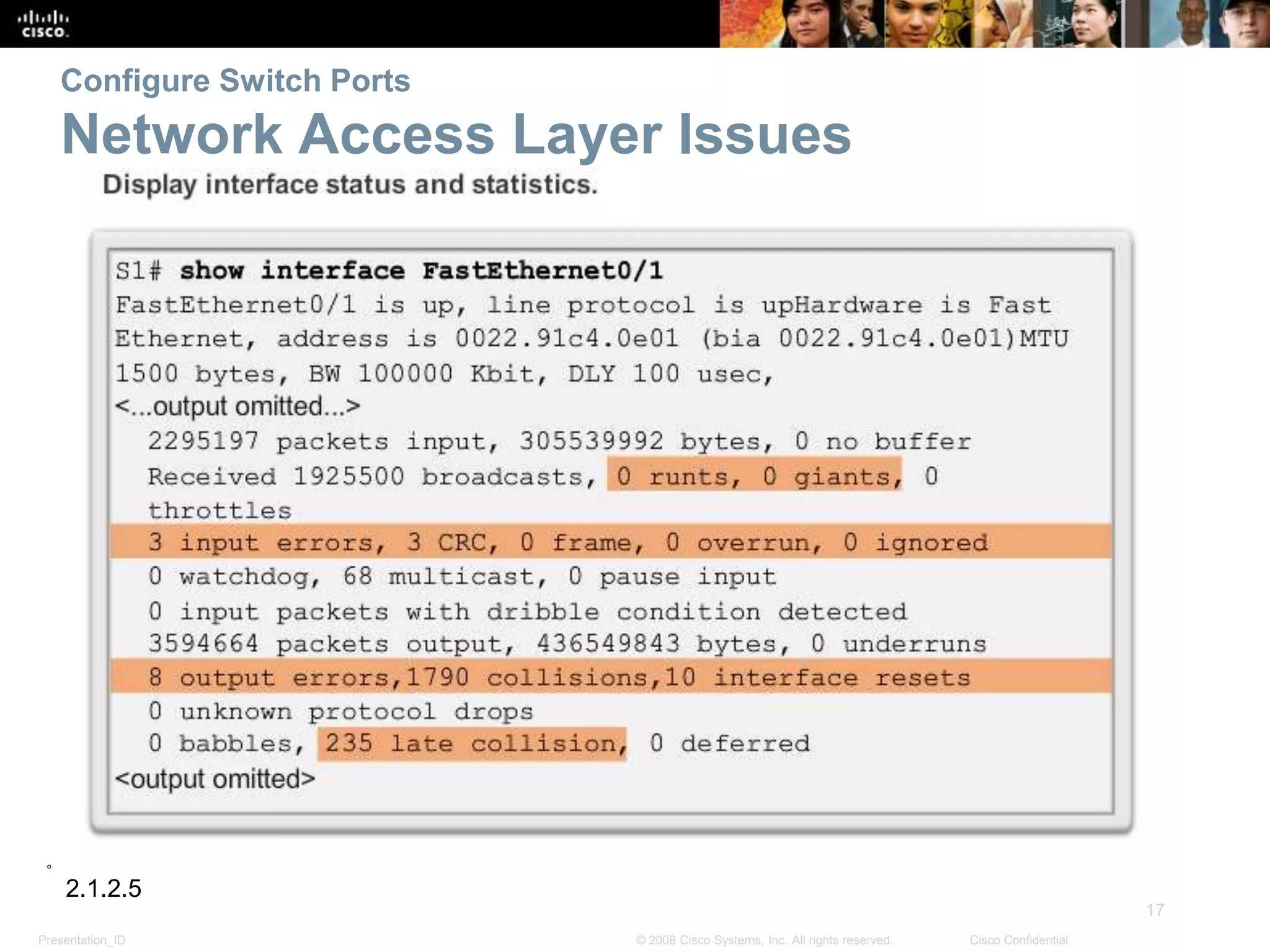
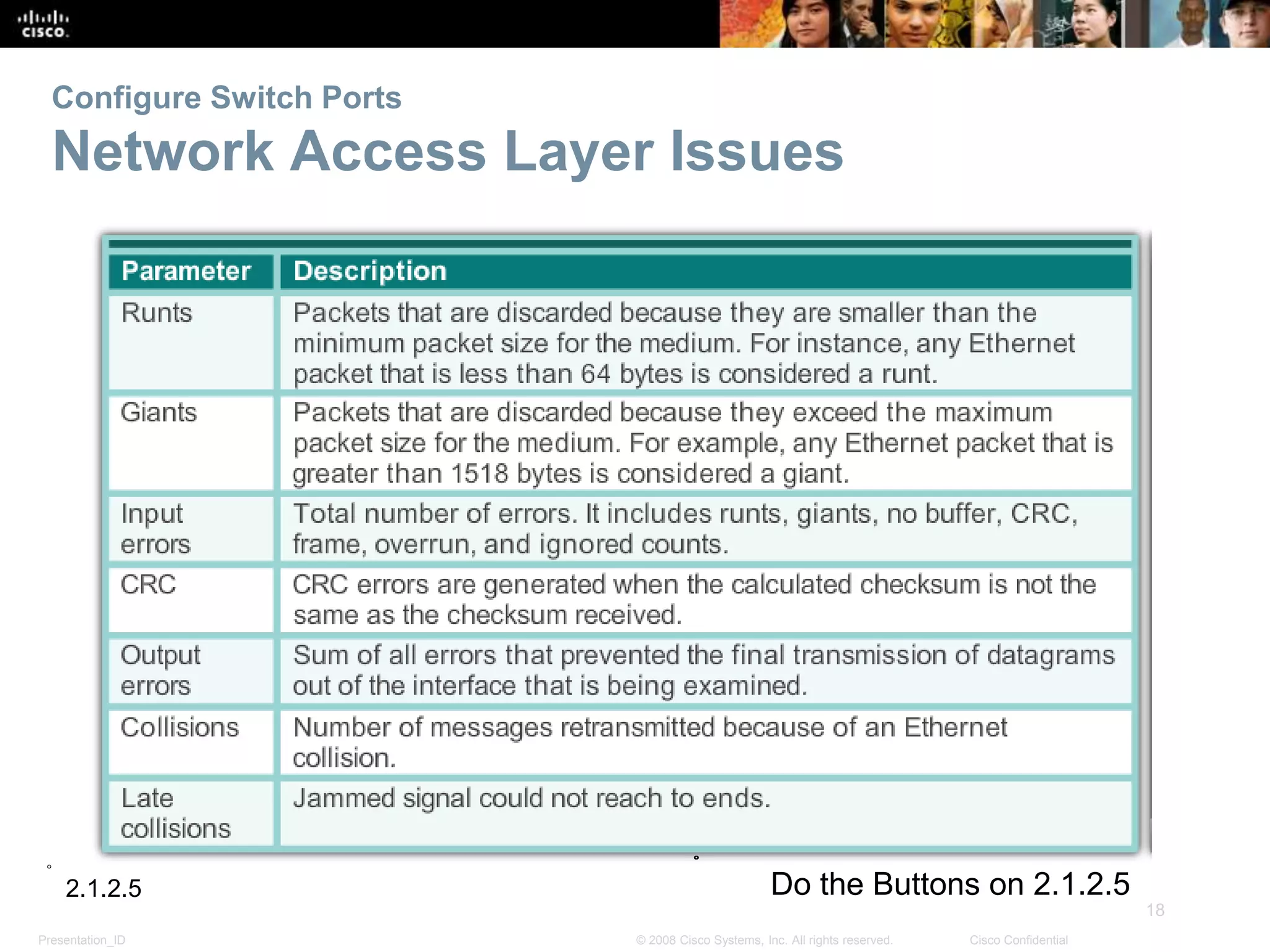
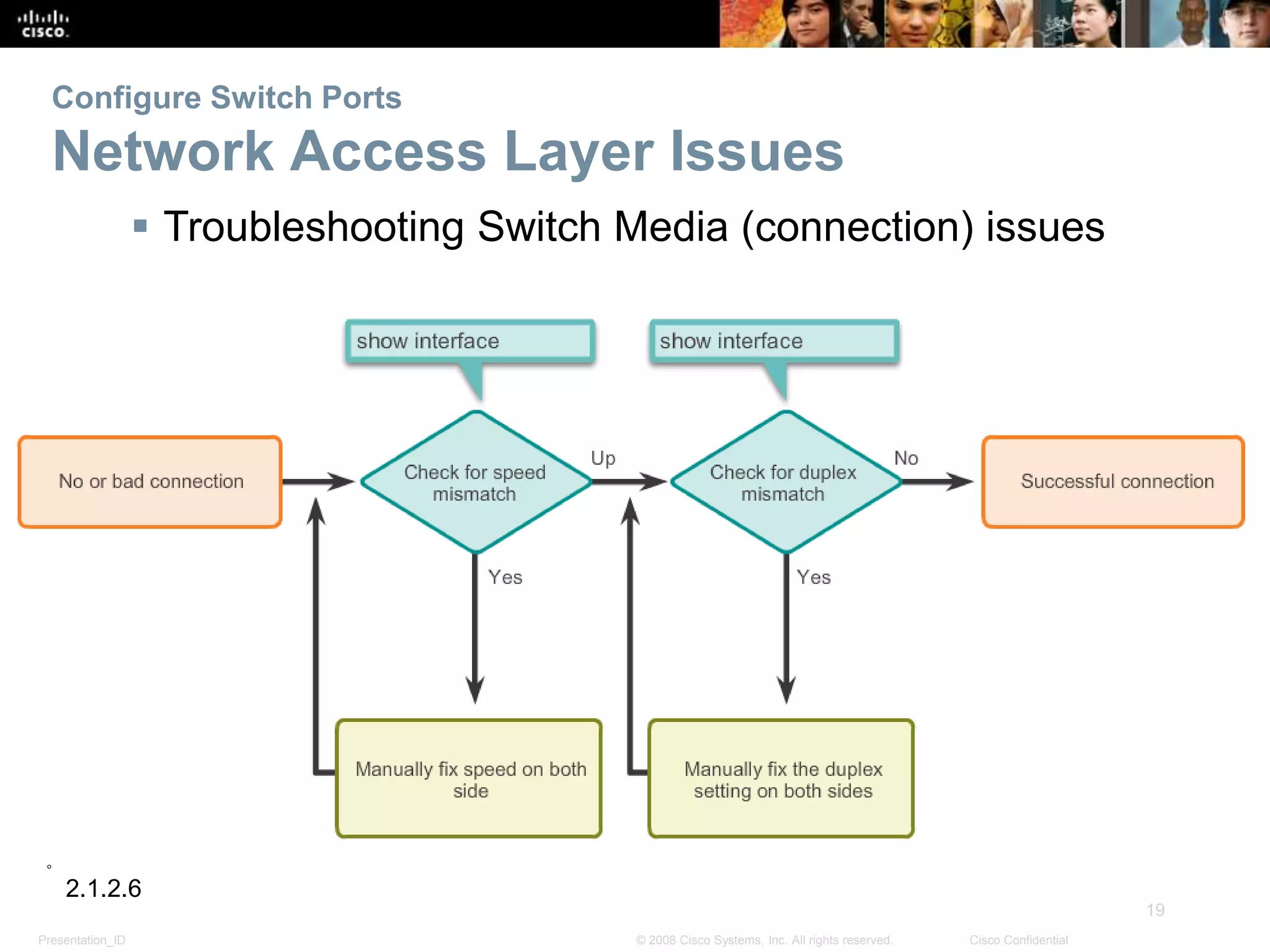
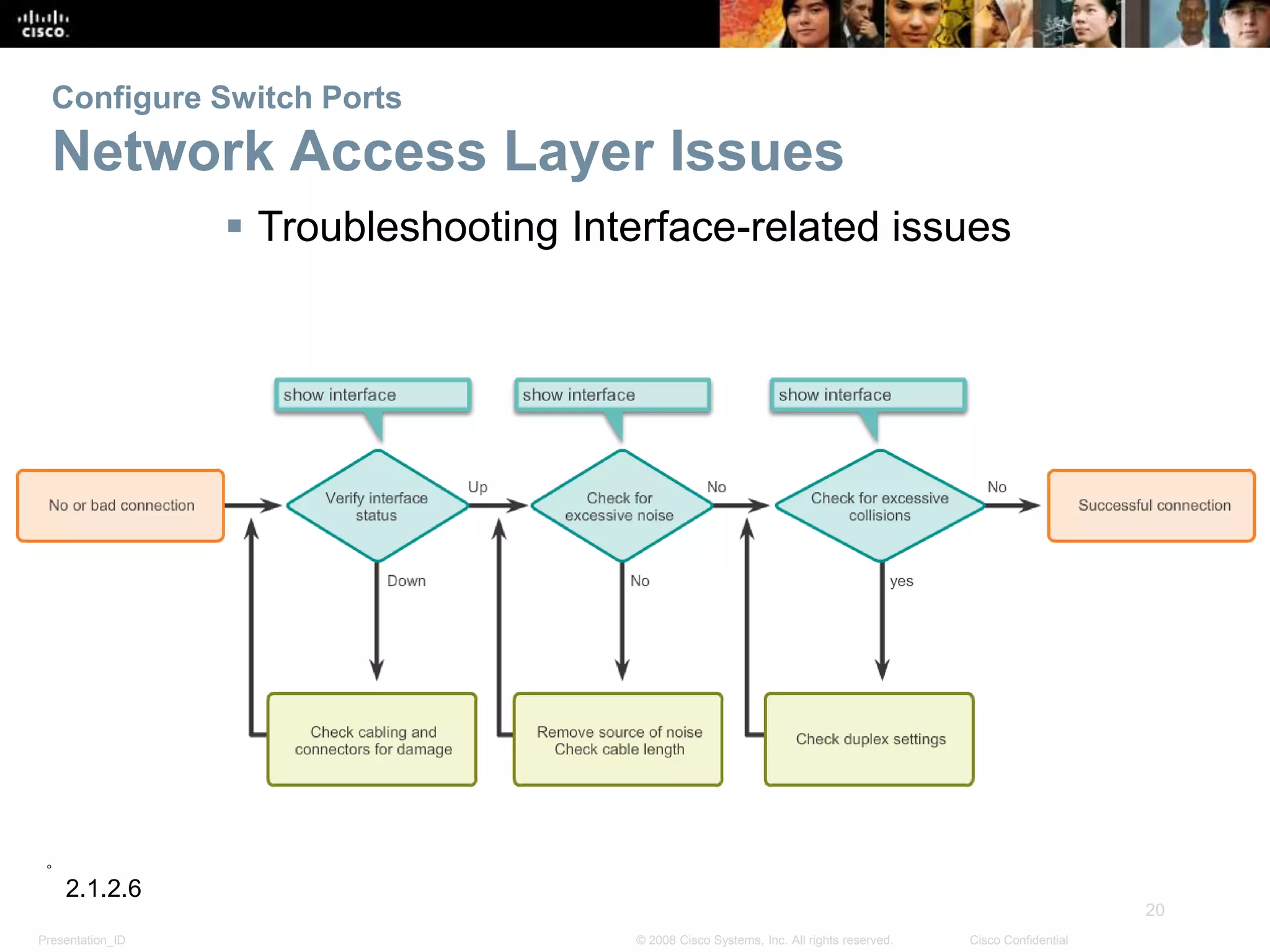
This document discusses configuring and managing Cisco switches. It covers basic switch configuration including the boot sequence, recovering from crashes using the boot loader, and switch LED indicators. It also discusses configuring switch ports including setting duplex and speed, the auto-MDIX feature, and verifying port settings. Additionally, it addresses network access layer issues and troubleshooting media and interface-related problems.