Embed presentation
Download to read offline






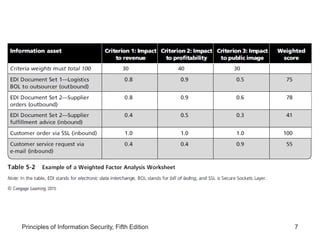

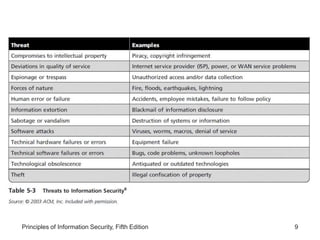


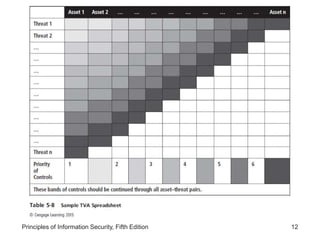

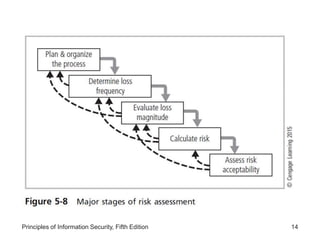


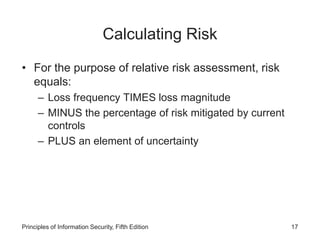



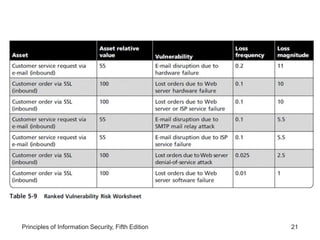
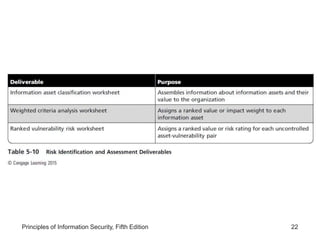
This document discusses the process of risk assessment for information assets. It involves identifying the organization's key information assets, threats against those assets, and vulnerabilities that could be exploited. Assets are prioritized based on their importance to the organization. Threats are also prioritized based on their potential danger and cost. Vulnerabilities of each asset are then identified through brainstorming sessions. A risk assessment evaluates the likelihood and potential impact of each threat to determine an overall risk rating. The results are documented in a risk worksheet to guide further risk management actions.





















