Embed presentation
Download to read offline











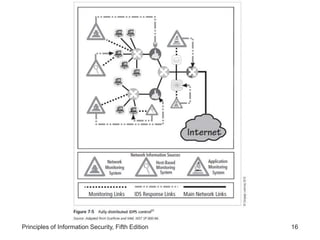
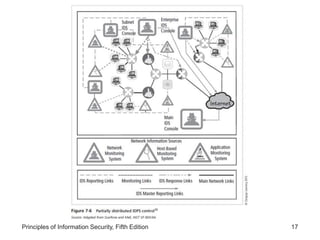

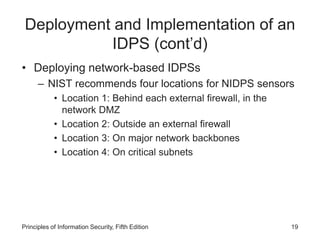
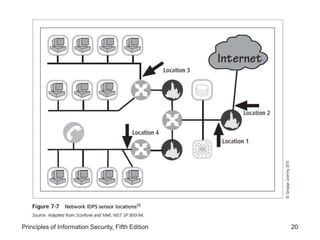
The document discusses intrusion detection and prevention systems (IDPS), including their detection methods, response behaviors, selection considerations, strengths and limitations, and deployment. It describes the main detection approaches used by IDPS like signature-based, anomaly-based, and stateful protocol analysis. It also covers log file monitors, active vs passive responses, and factors to consider when selecting and deploying an IDPS.




















