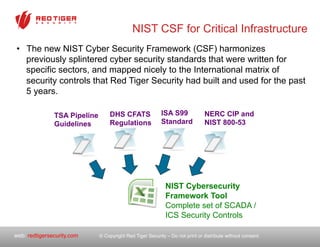
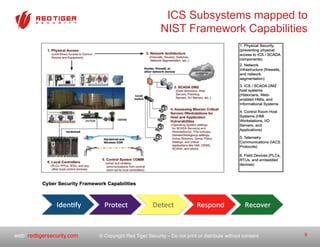
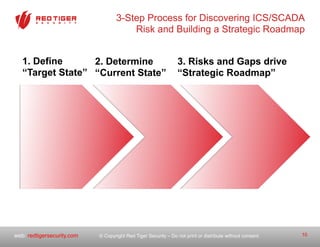
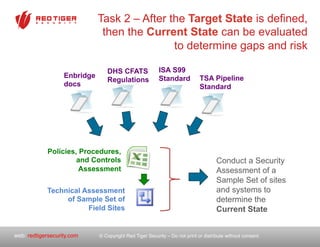
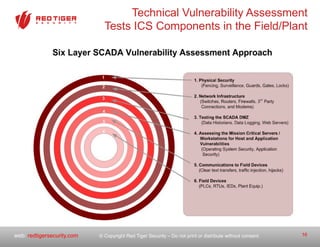
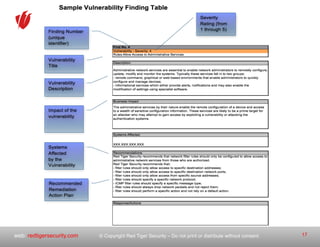
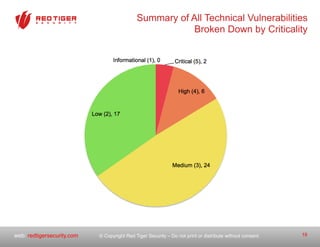
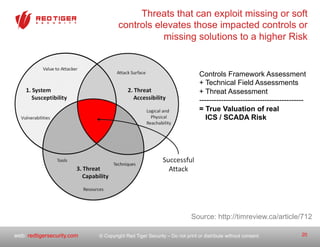
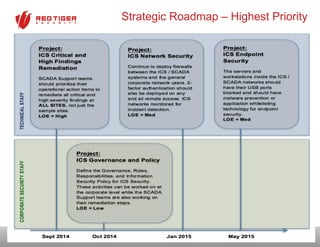
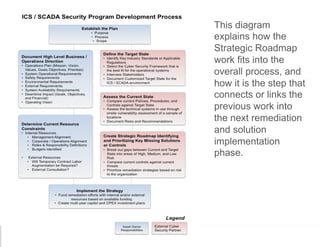
The document outlines a strategic roadmap for securing critical infrastructure using the NIST Cybersecurity Framework (CSF) by assessing the current security posture of industrial control systems (ICS) and SCADA. It emphasizes the need for a comprehensive risk assessment that combines technical assessments, policy evaluations, and risk management strategies, ultimately aiming to develop a prioritized 3-to-5 year plan for security improvements. Key findings indicate that aligning cybersecurity efforts across IT, operational technology, and physical security is essential for a successful security posture.