Embed presentation
Download to read offline





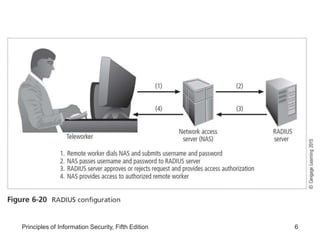

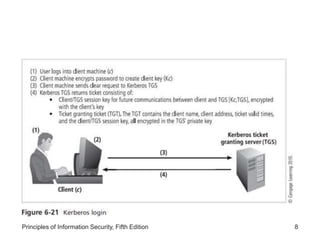
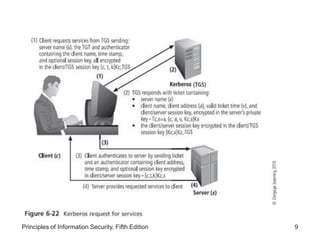



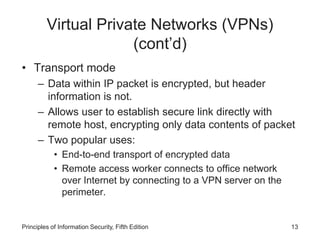
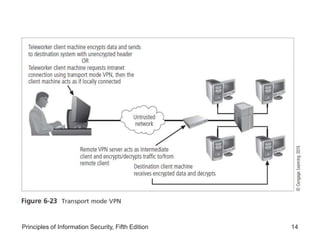

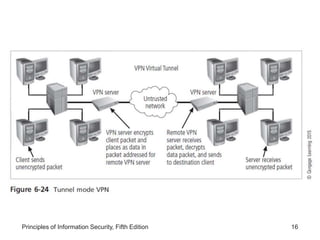
The document discusses remote access security, firewalls, virtual private networks (VPNs), and various authentication methods. It describes how remote access poses risks if unsecured, and technologies like RADIUS, Diameter, TACACS, and Kerberos that help authenticate remote users. The document also explains VPNs and how they can securely extend private networks over public networks using encryption and authentication. Finally, it discusses firewall placement and methods of remote access protection through technologies like content filtering.
















