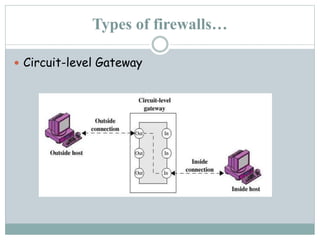
This document discusses firewalls, including their definition, history, types, and purposes. A firewall is a program or hardware device that filters network traffic between the internet and an internal network based on a set of security rules. There are different types of firewalls, including packet filtering routers, application-level gateways, and circuit-level gateways. Firewalls aim to restrict network access and protect internal systems by only allowing authorized traffic according to a security policy.