This document provides an overview of Kerberos, including:
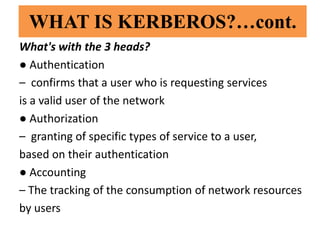
- Kerberos is an authentication protocol that uses symmetric encryption and timestamps to allow nodes communicating over an insecure network to verify each other's identity securely.
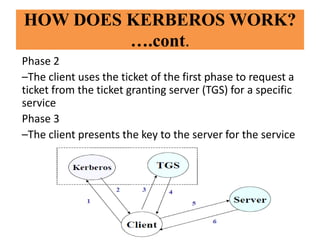
- It works by having a client first authenticate with an authentication server to obtain a ticket-granting ticket, then uses that ticket to obtain additional tickets for access to other services.
- Kerberos addresses the need for secure authentication in distributed network environments where the workstations themselves cannot be fully trusted.



















![VERSION 4
• Technical deficiencies
– Double Encryption (Bellovin and Merritt [Bel90])
– PCBC encryption
– Authenticators and replay detection
– Password attacks
– Session keys
– Cryptographic checksum
– Kerberised](https://image.slidesharecdn.com/kerberos-131122231918-phpapp02/85/Kerberos-22-320.jpg)




