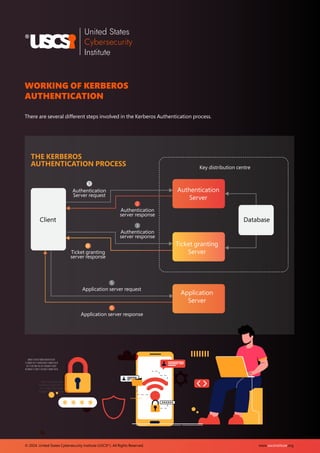
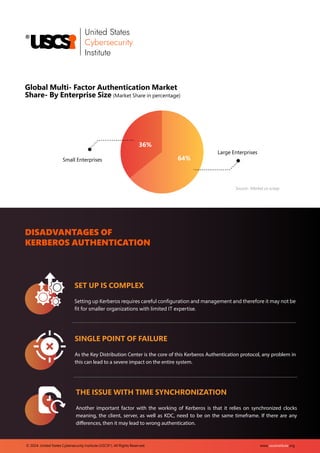
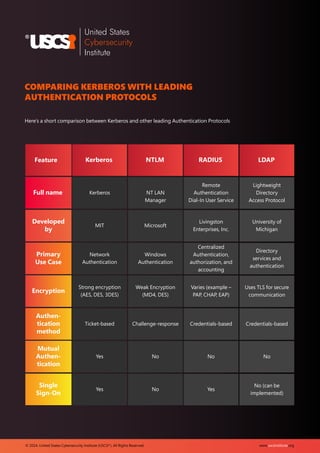
The document provides an overview of Kerberos, a widely used network authentication protocol developed by MIT, emphasizing its significance in securing access to systems and resources. It discusses the global authentication service market, expected to grow significantly, and outlines the benefits of Kerberos, such as enhanced security and single sign-on capabilities, while also acknowledging its disadvantages, including complexity and potential points of failure. Lastly, it highlights best practices for securing Kerberos, underscoring the importance of ongoing updates and monitoring for robust cybersecurity.