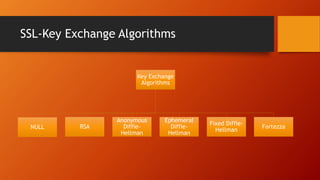
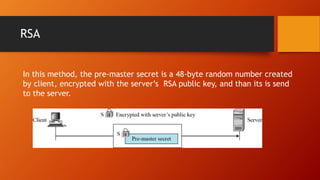
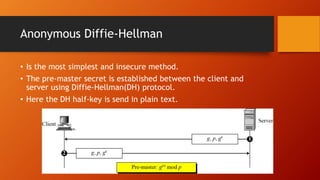
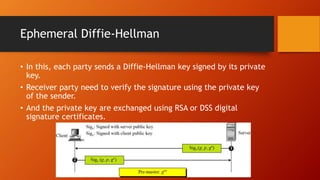
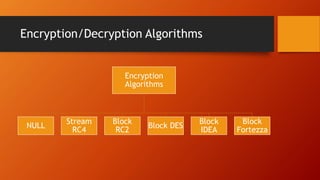
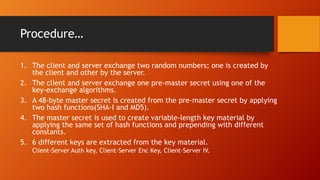
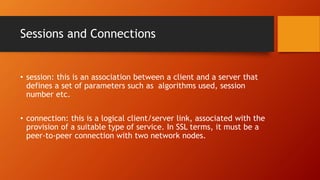
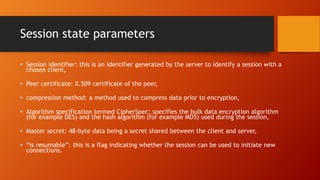
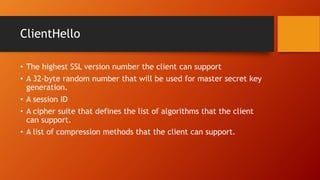
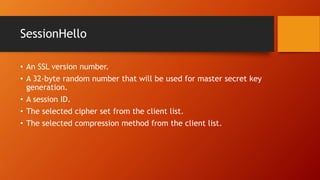
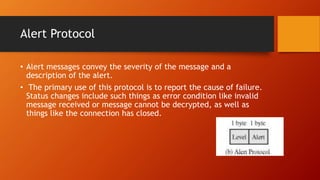
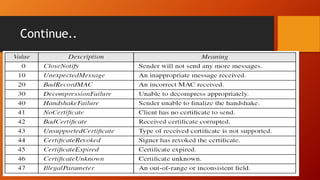
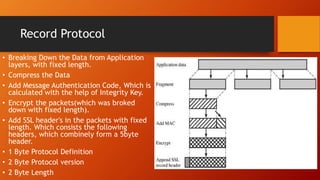
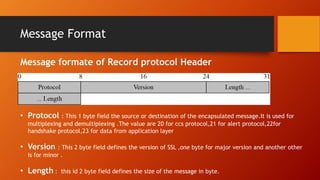
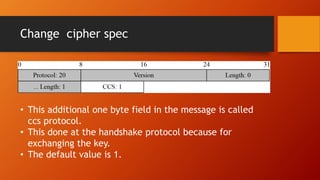
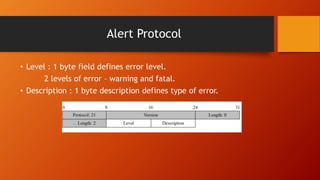
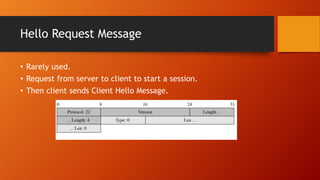
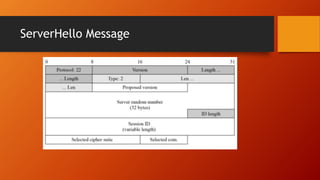
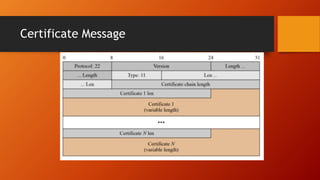
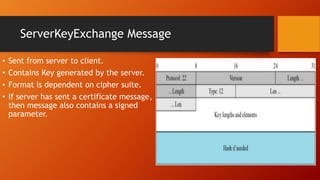
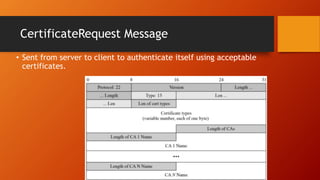
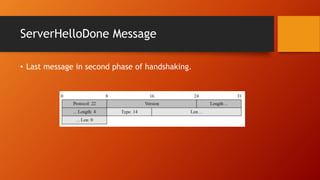
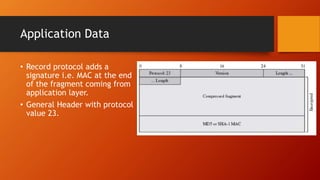
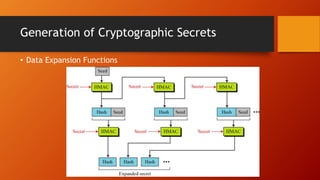
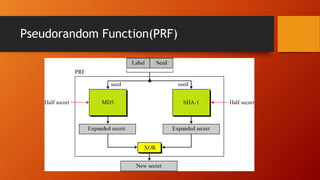
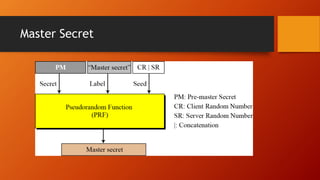
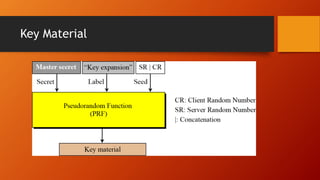
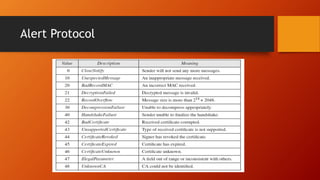
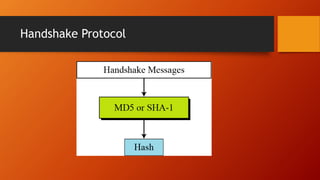
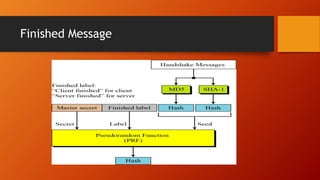
SSL and TLS provide end-to-end security for applications using TCP. They operate at the transport layer and provide services like data encryption, message integrity, and client/server authentication. The key components are the handshake protocol for negotiating encryption parameters and exchanging keys, the record protocol for fragmenting and encrypting application data, and alert and change cipher spec protocols for signaling errors and key changes. Common algorithms include RSA and Diffie-Hellman for key exchange, RC4, 3DES and AES for encryption, and MD5 or SHA for hashing. Sessions define a connection's cryptographic settings while connections are the actual data streams.