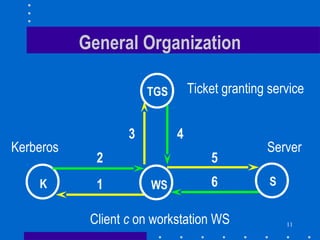
1. Kerberos is an authentication system that uses tickets and session keys to allow clients to authenticate to servers across an open network.
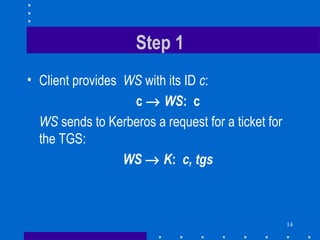
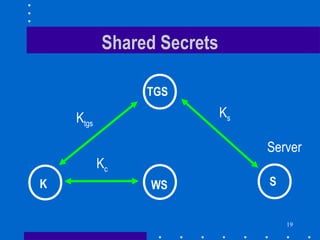
2. It is a two-step process where the client first authenticates to the Kerberos server and receives a ticket and session key to authenticate to the ticket granting service (TGS).
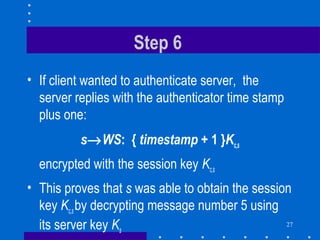
3. The TGS then provides a ticket and session key to authenticate to the desired server. This prevents unauthorized access while also preventing replay attacks through the use of authenticators and timestamps.