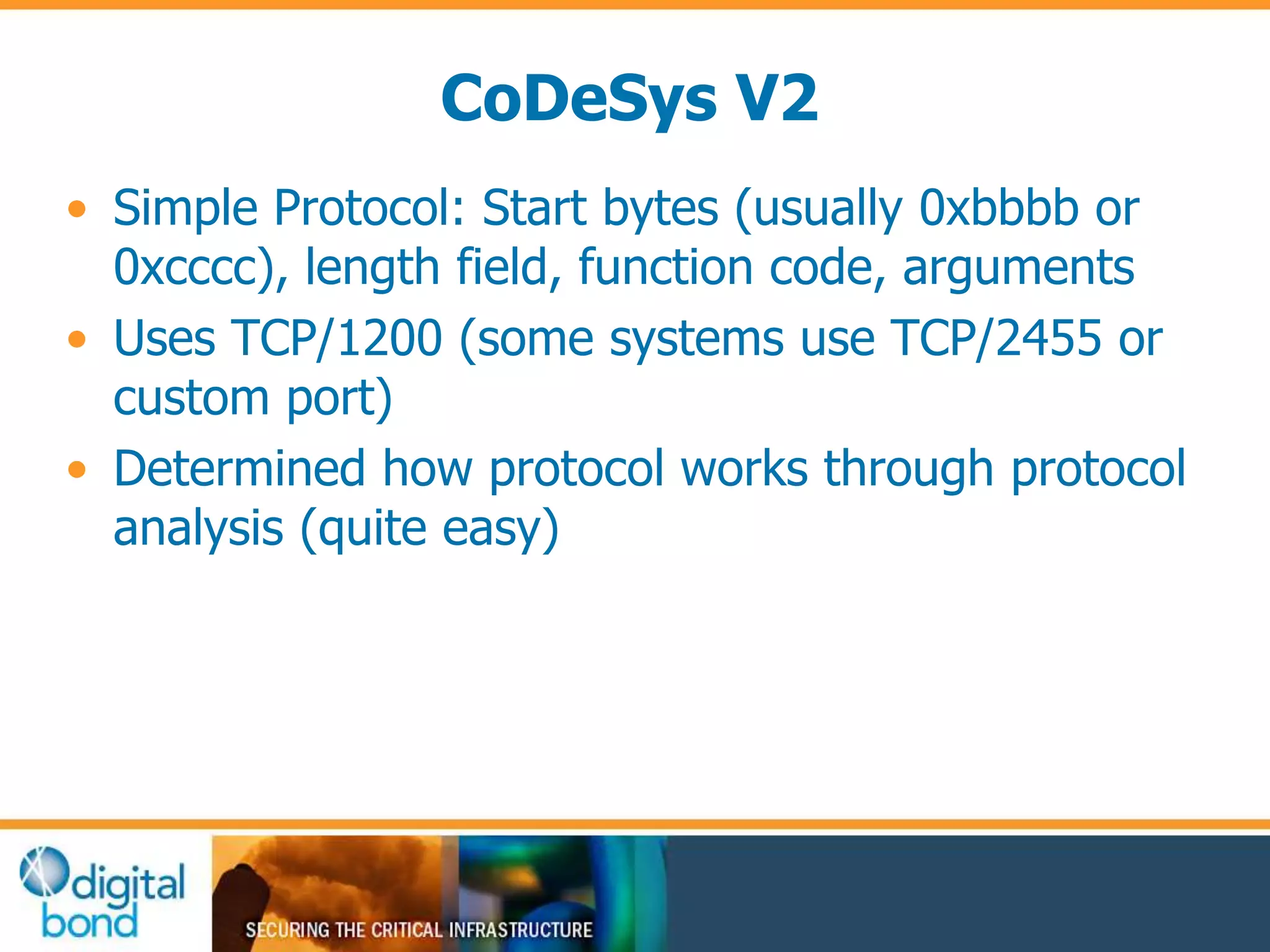
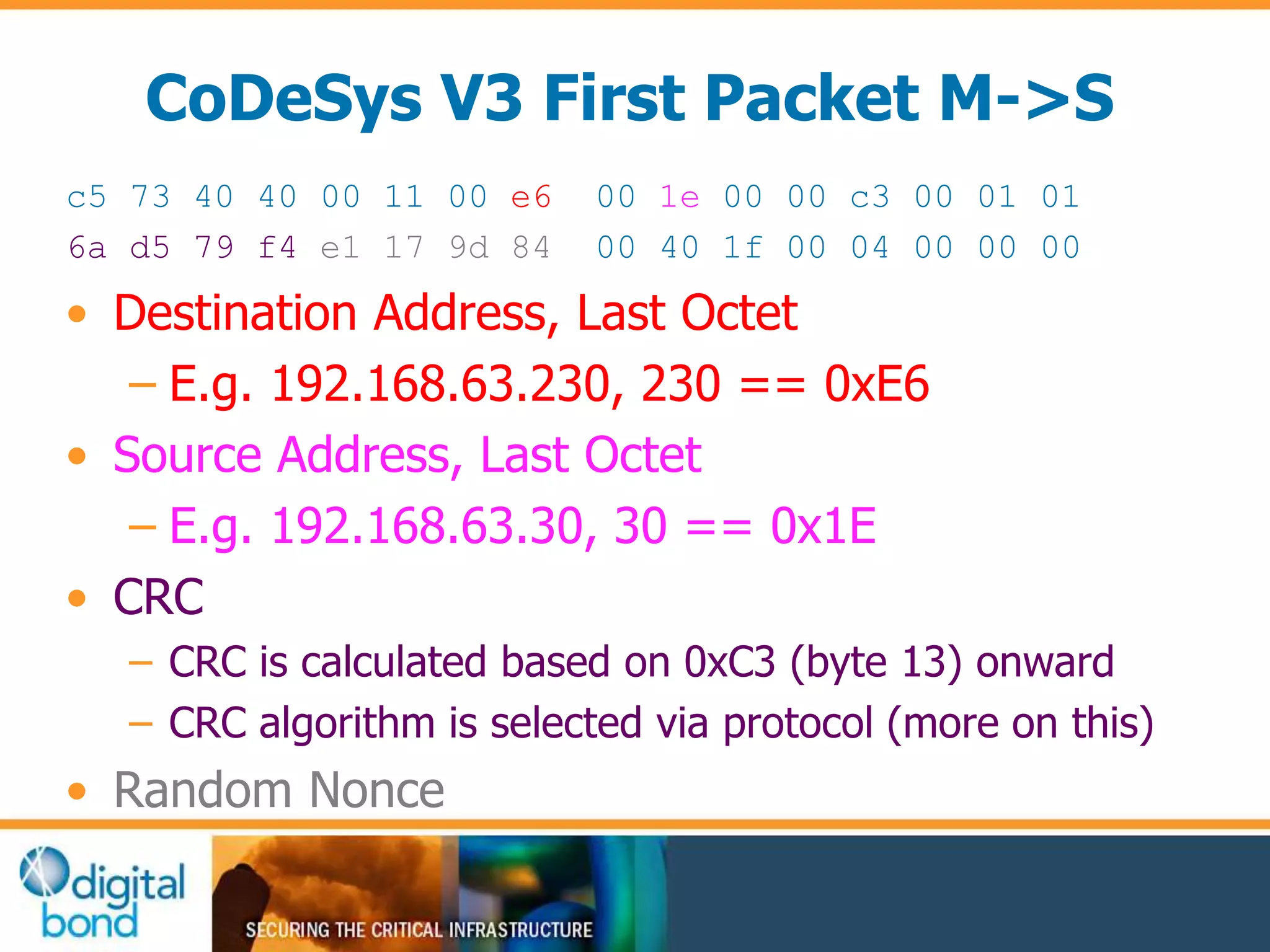
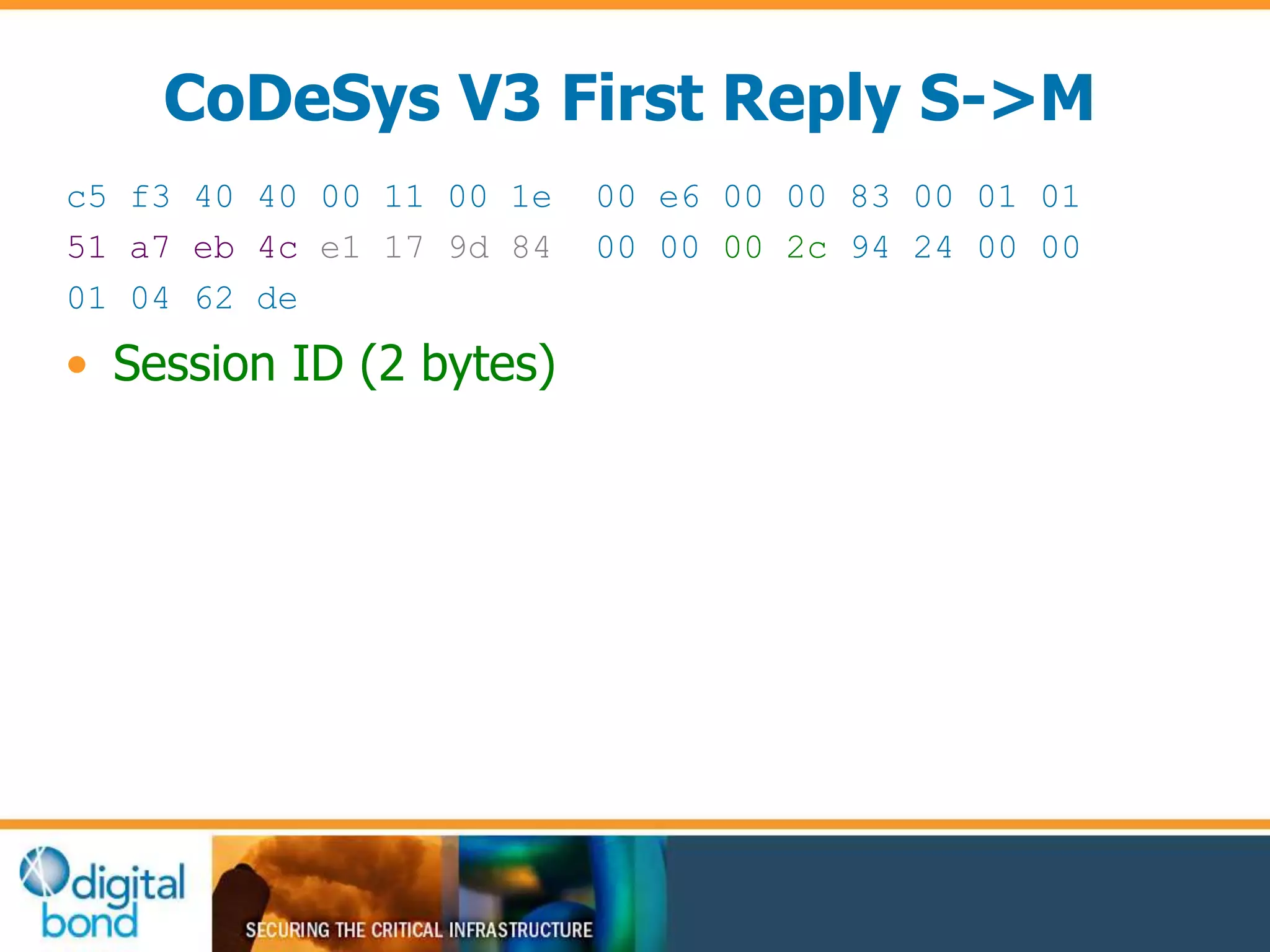
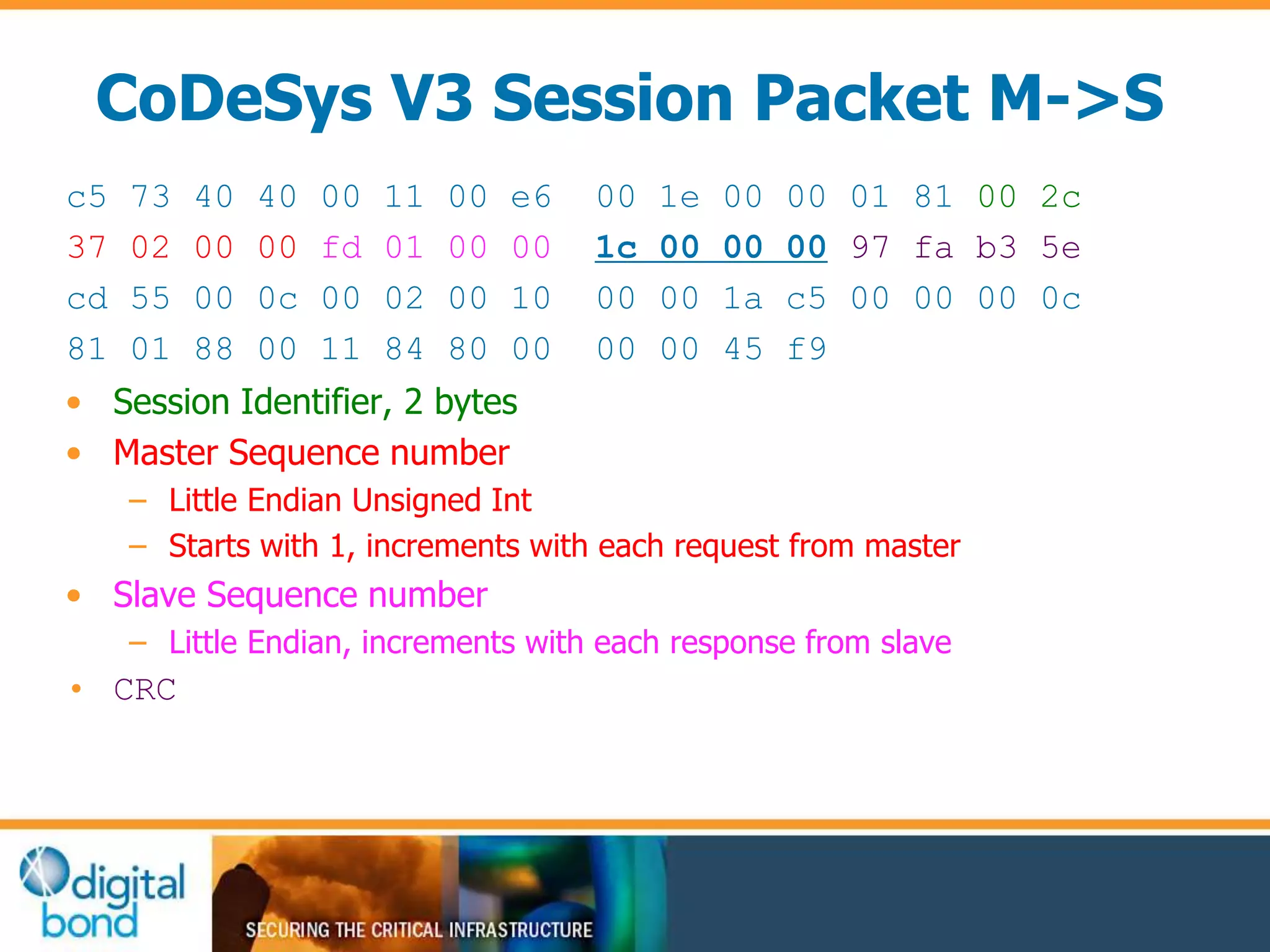
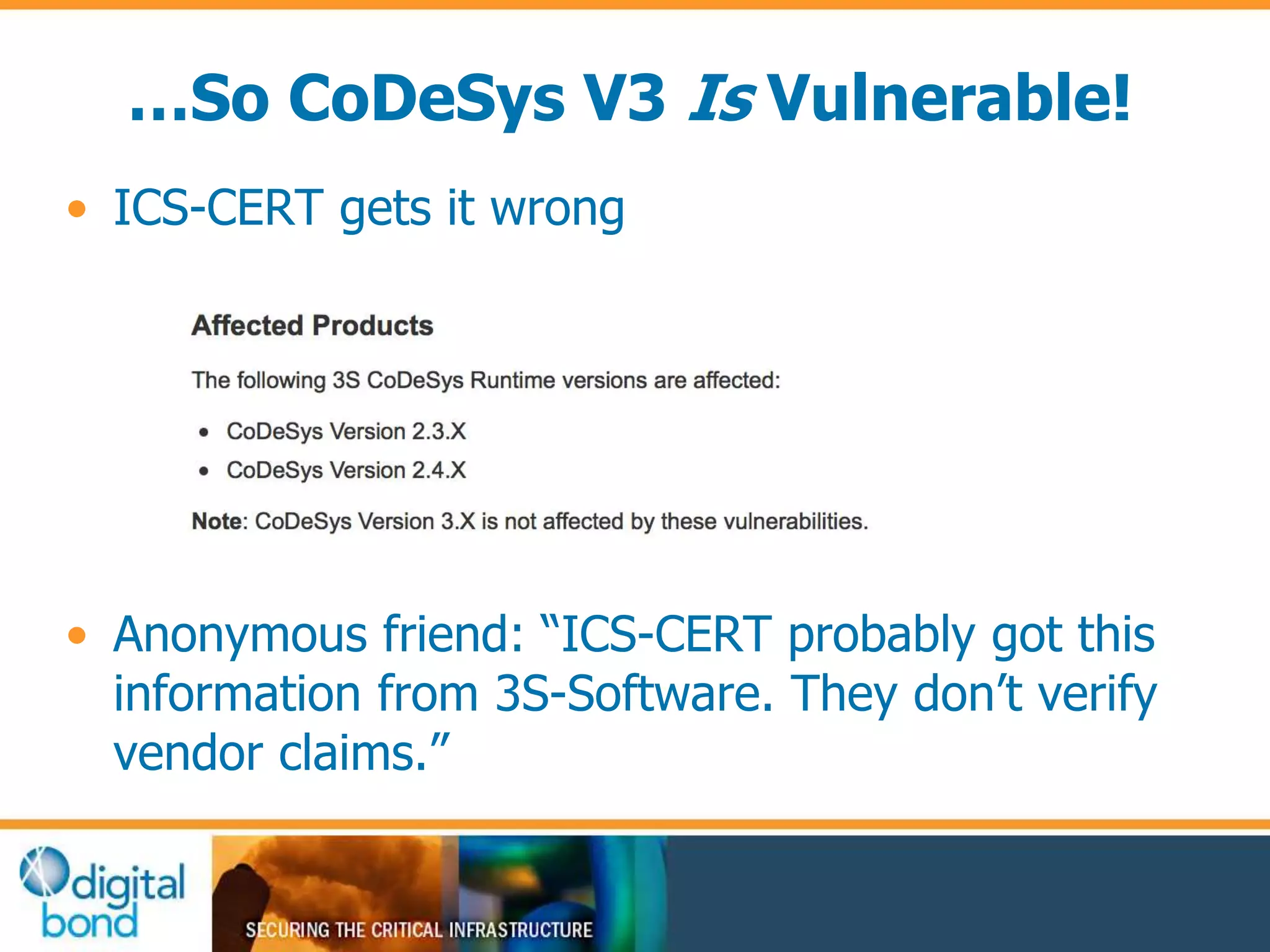
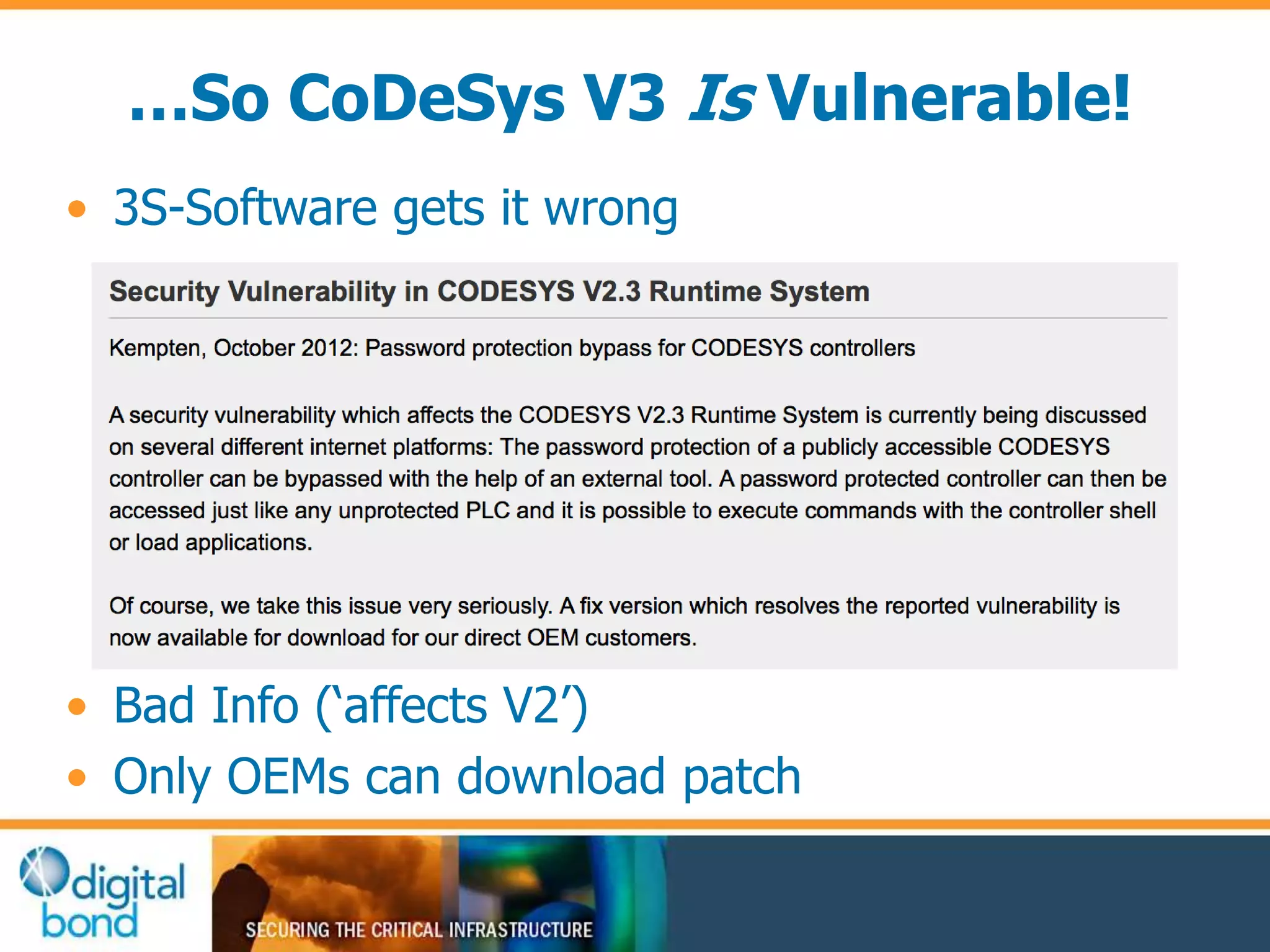
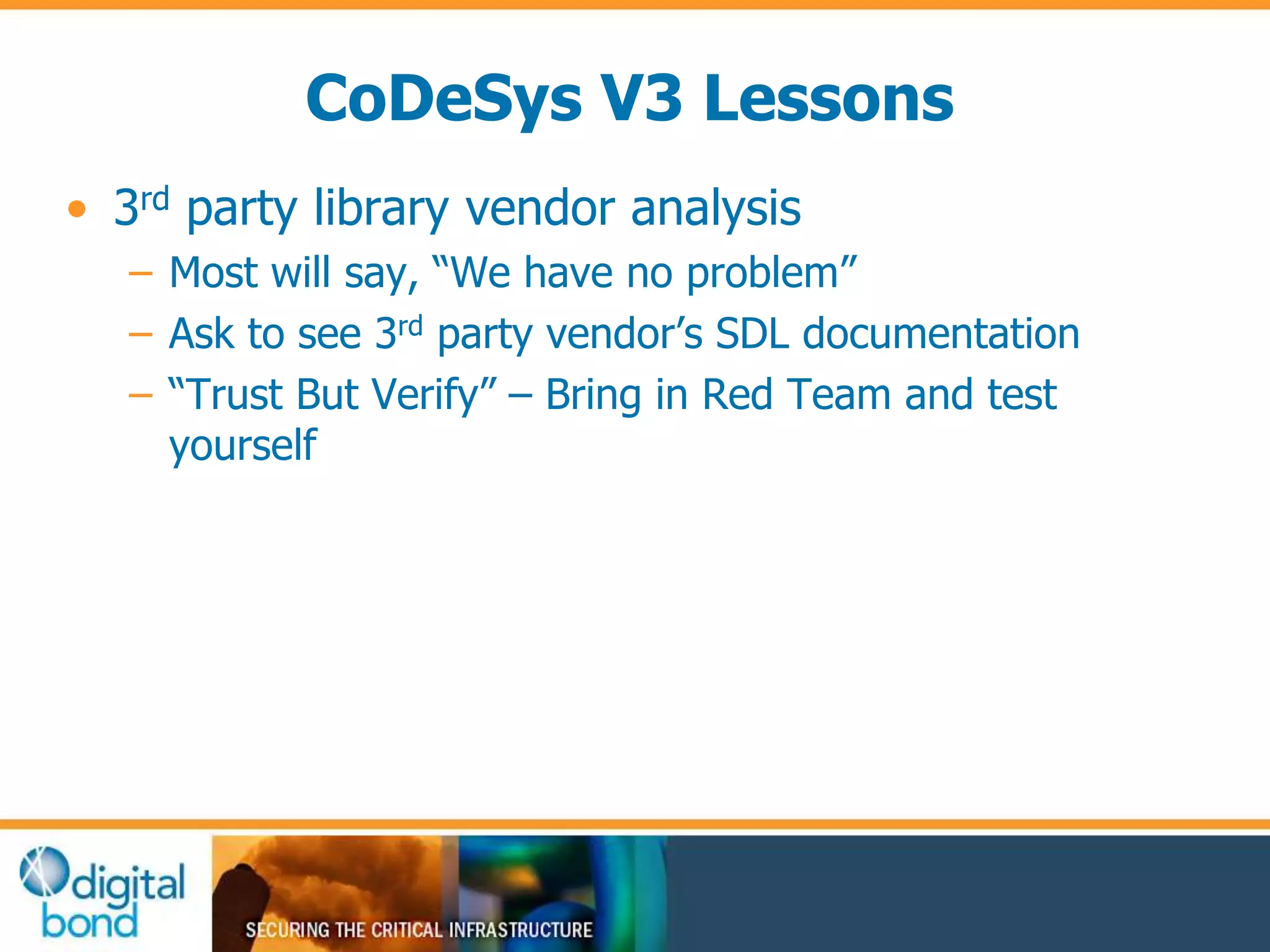
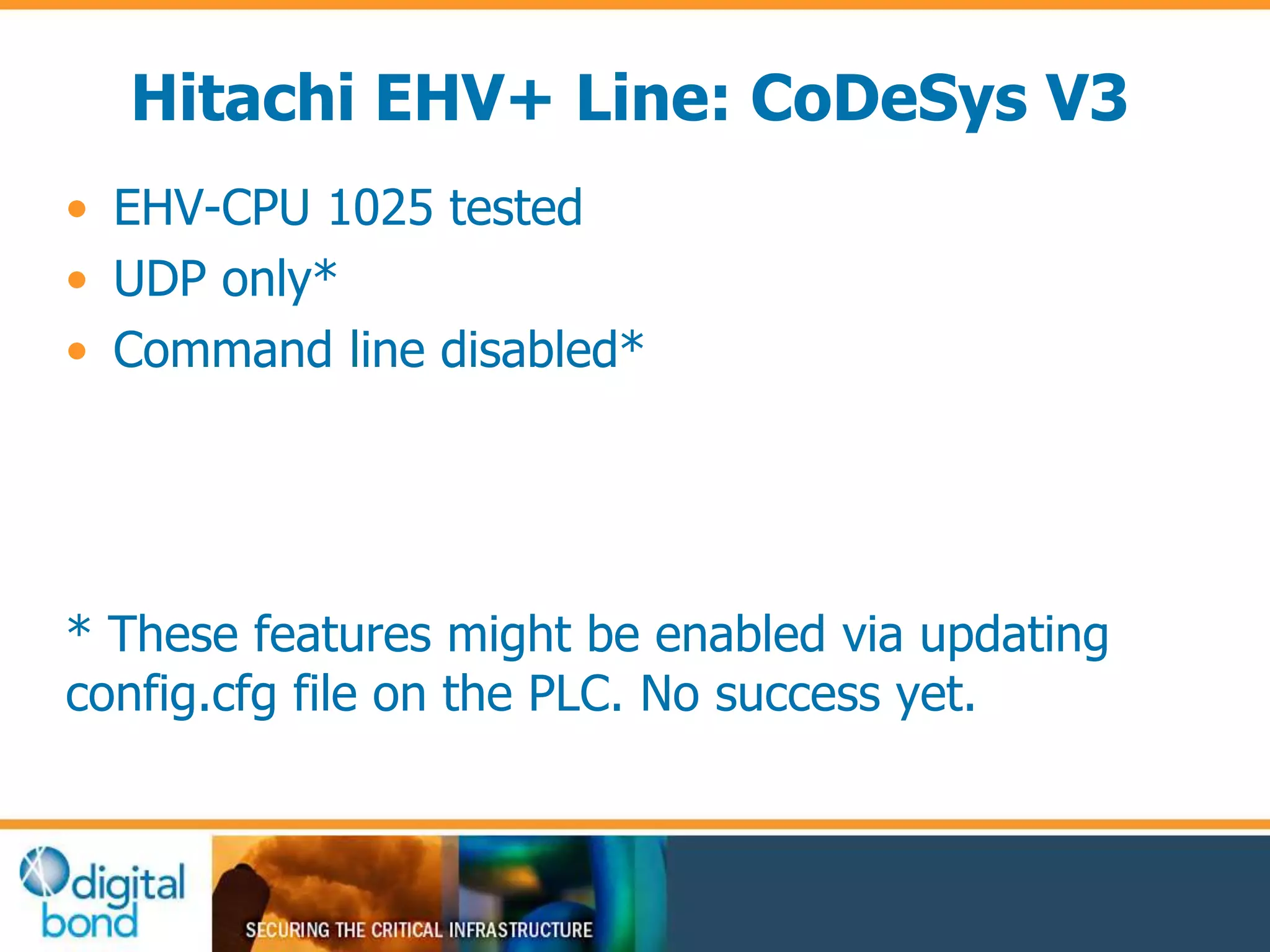
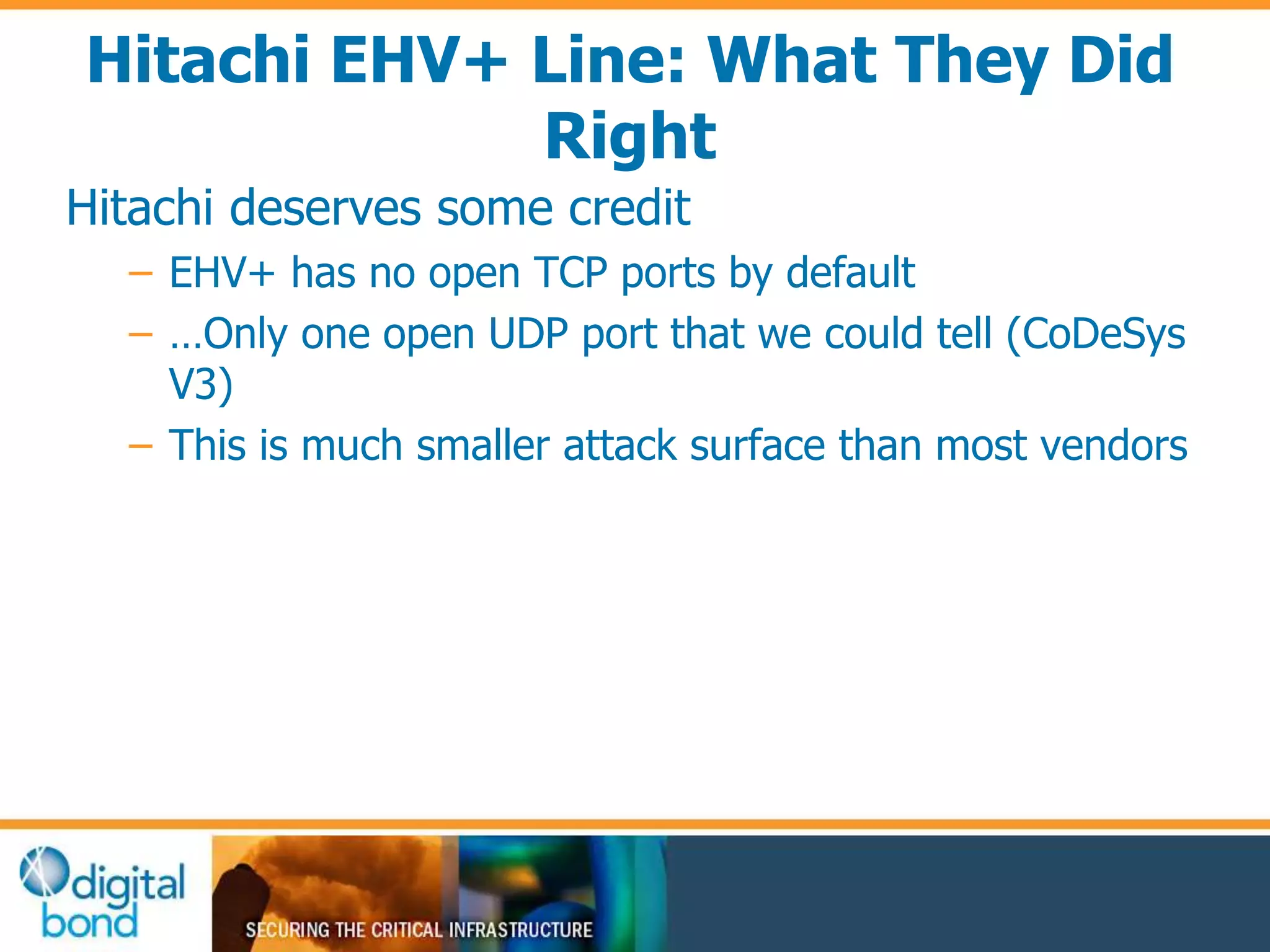
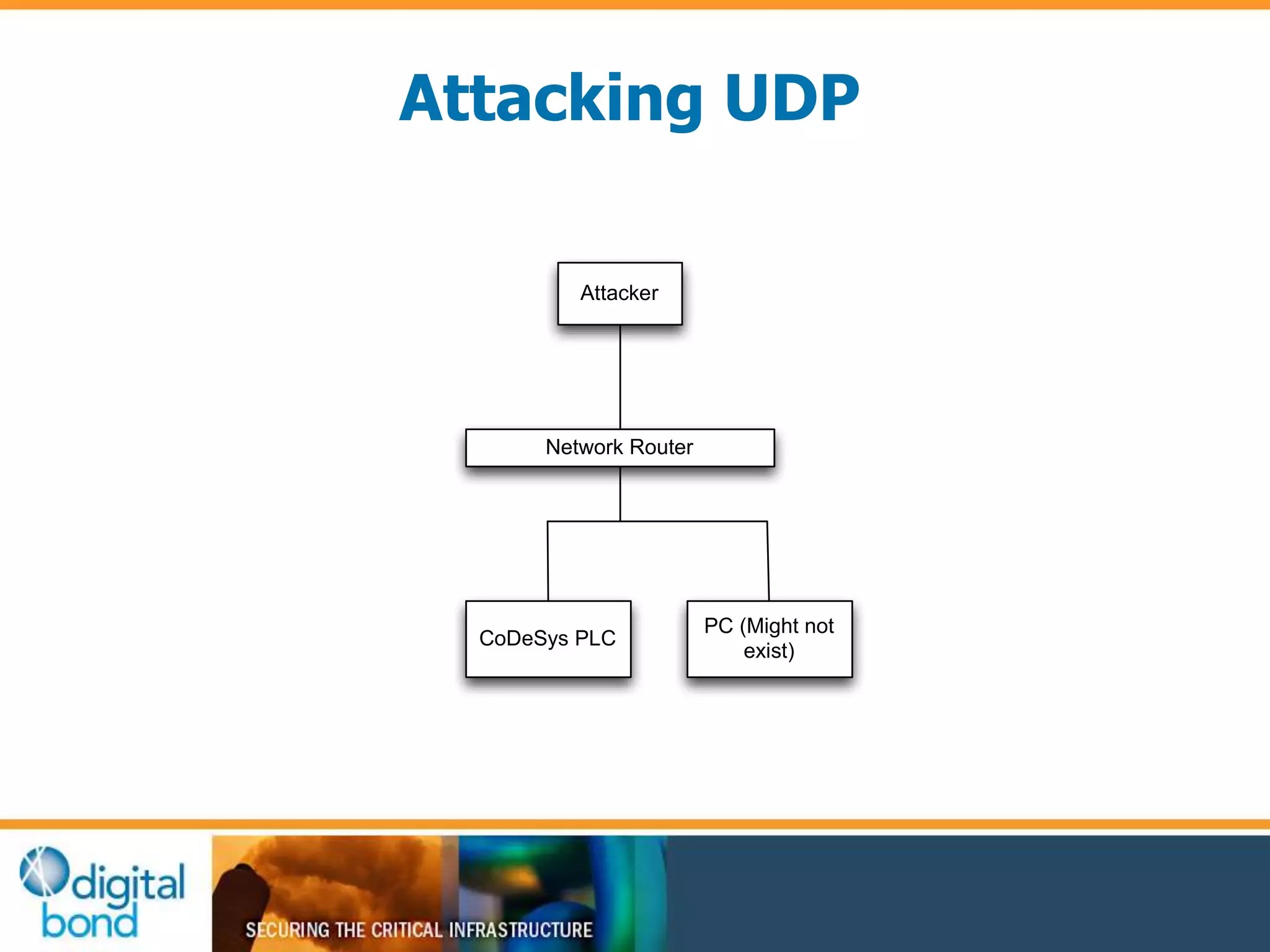
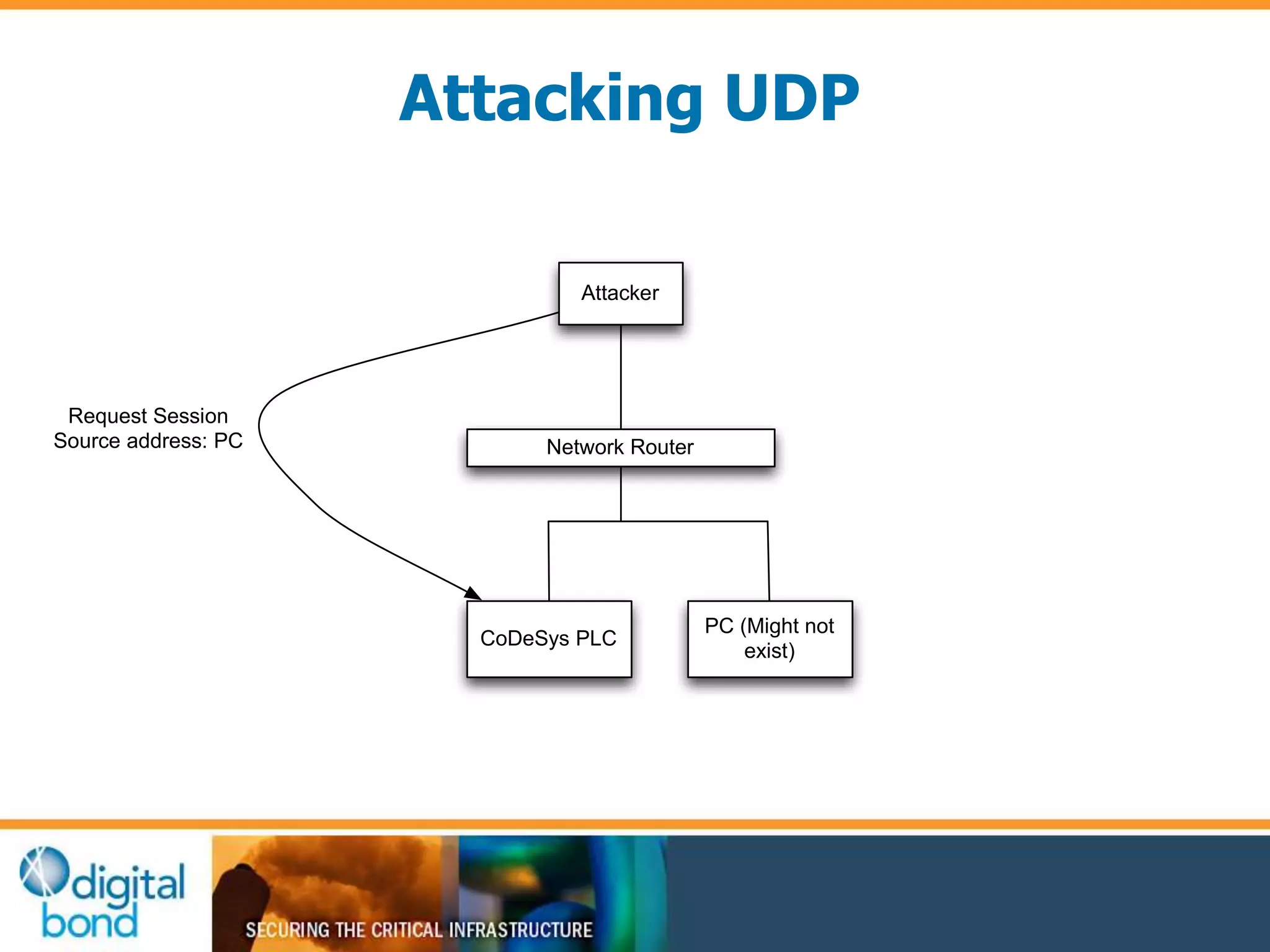
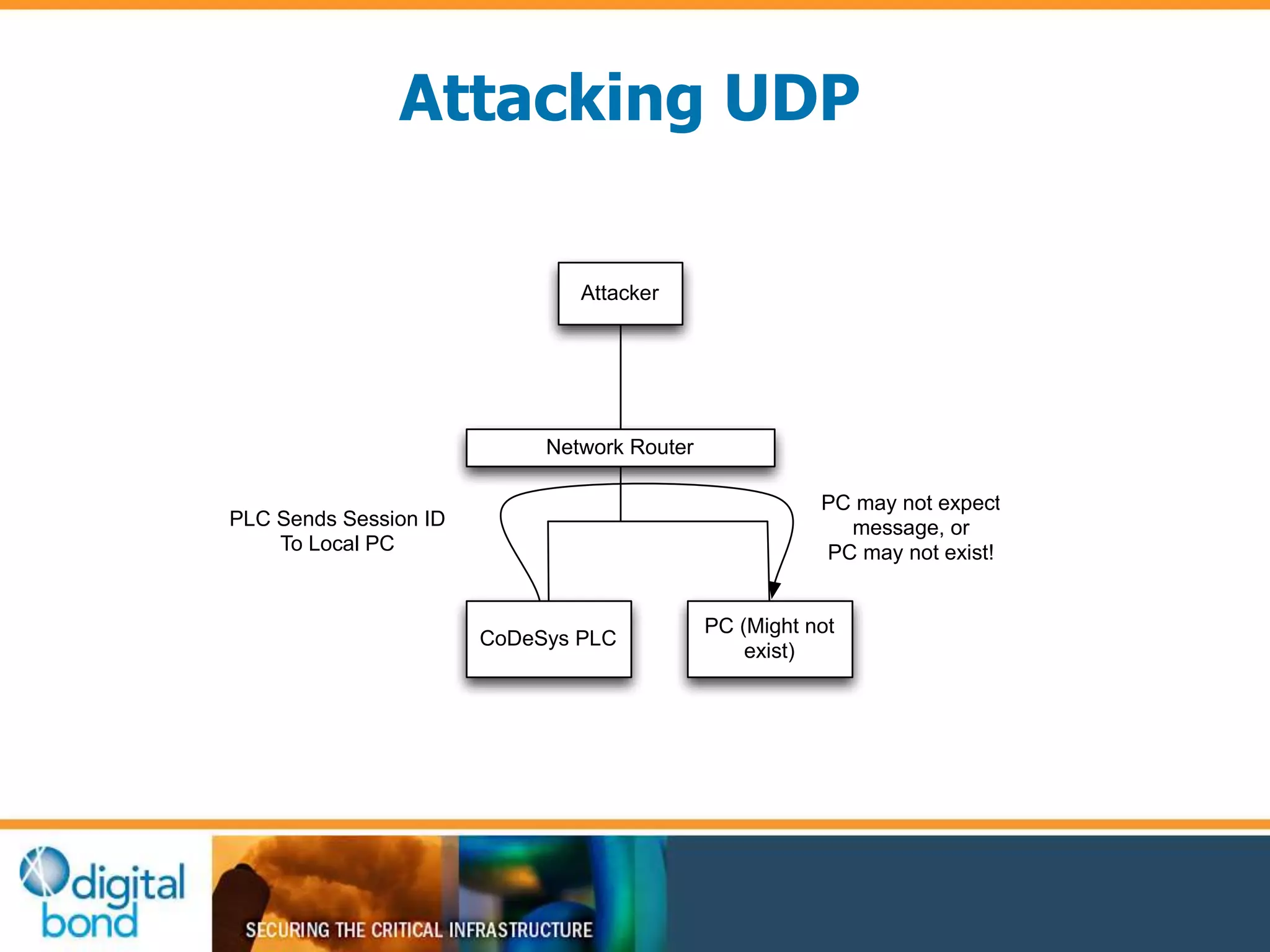
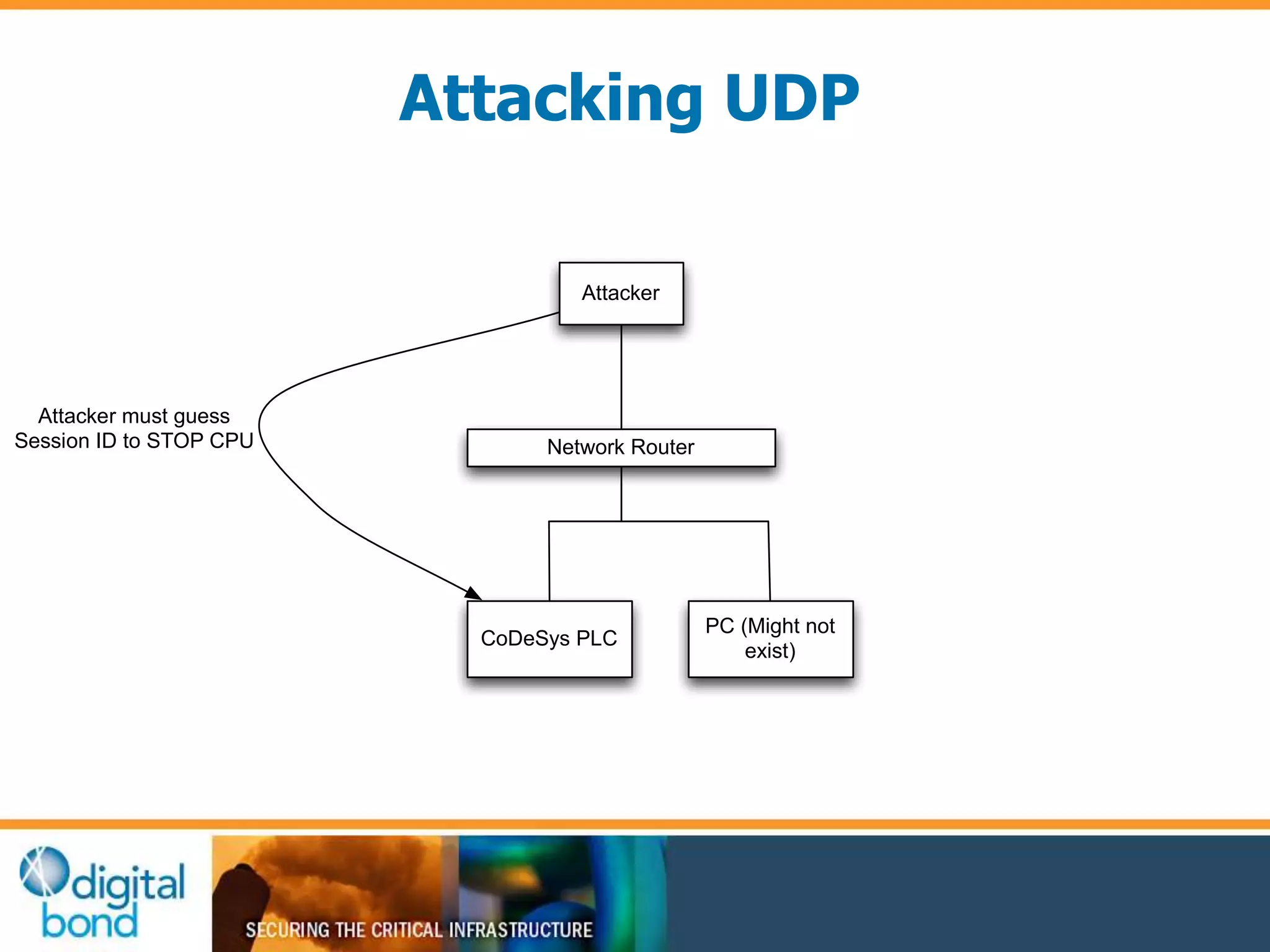
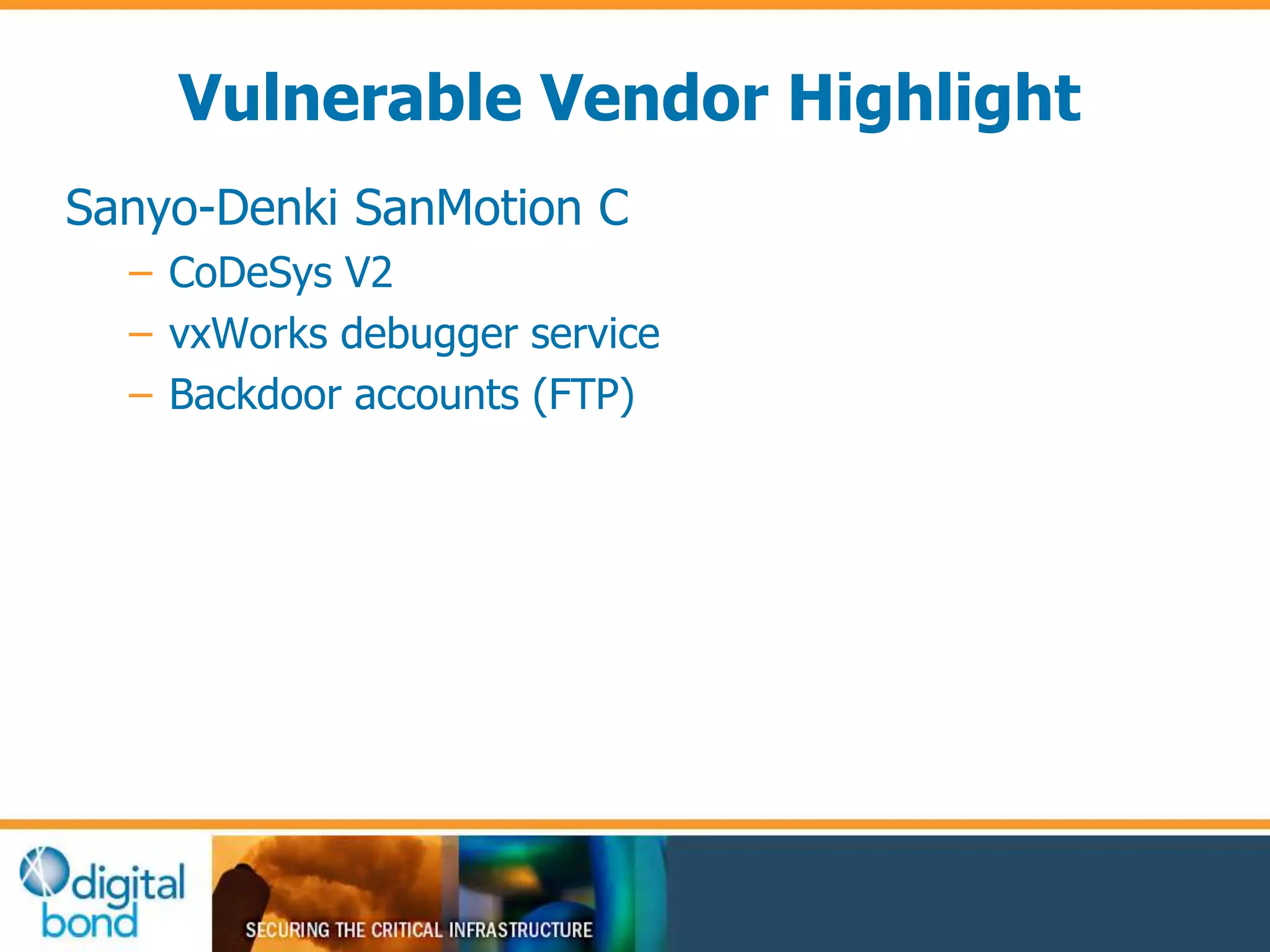
This document discusses vulnerability inheritance in programmable logic controllers (PLCs) from third-party libraries and software. It provides a specific example of vulnerabilities found in the CoDeSys runtime and engineering software used by hundreds of industrial control system vendors. The document outlines how two major Japanese PLC vendors were found to be affected by these vulnerabilities due to their use of CoDeSys, and concludes that vendors need to implement secure development practices like security testing to prevent inheriting vulnerabilities from third-party components.