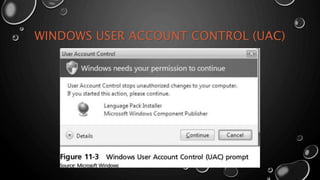
This document discusses access controls and various access control models. It defines access control as granting or denying approval to use specific resources. It describes common access control models like discretionary access control (DAC), mandatory access control (MAC), and role-based access control (RBAC). It also discusses access control terminology, technical processes, and best practices for implementing access controls.