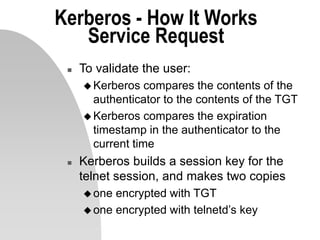
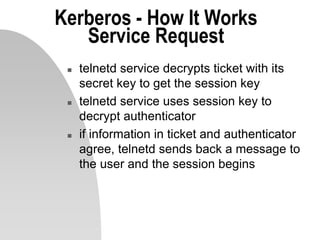
This document discusses network security and the Kerberos authentication protocol. It provides an introduction to Kerberos, describing how it works to allow users and services to authenticate over a network. Kerberos uses secret key cryptography and issues tickets to allow users to securely access remote services without sending passwords over the network in clear text. The document outlines the initialization process when a user requests a ticket-granting ticket from the Kerberos server, and how that ticket is then used to request and access remote services. It also discusses some of the limitations of Kerberos and enhancements being made.