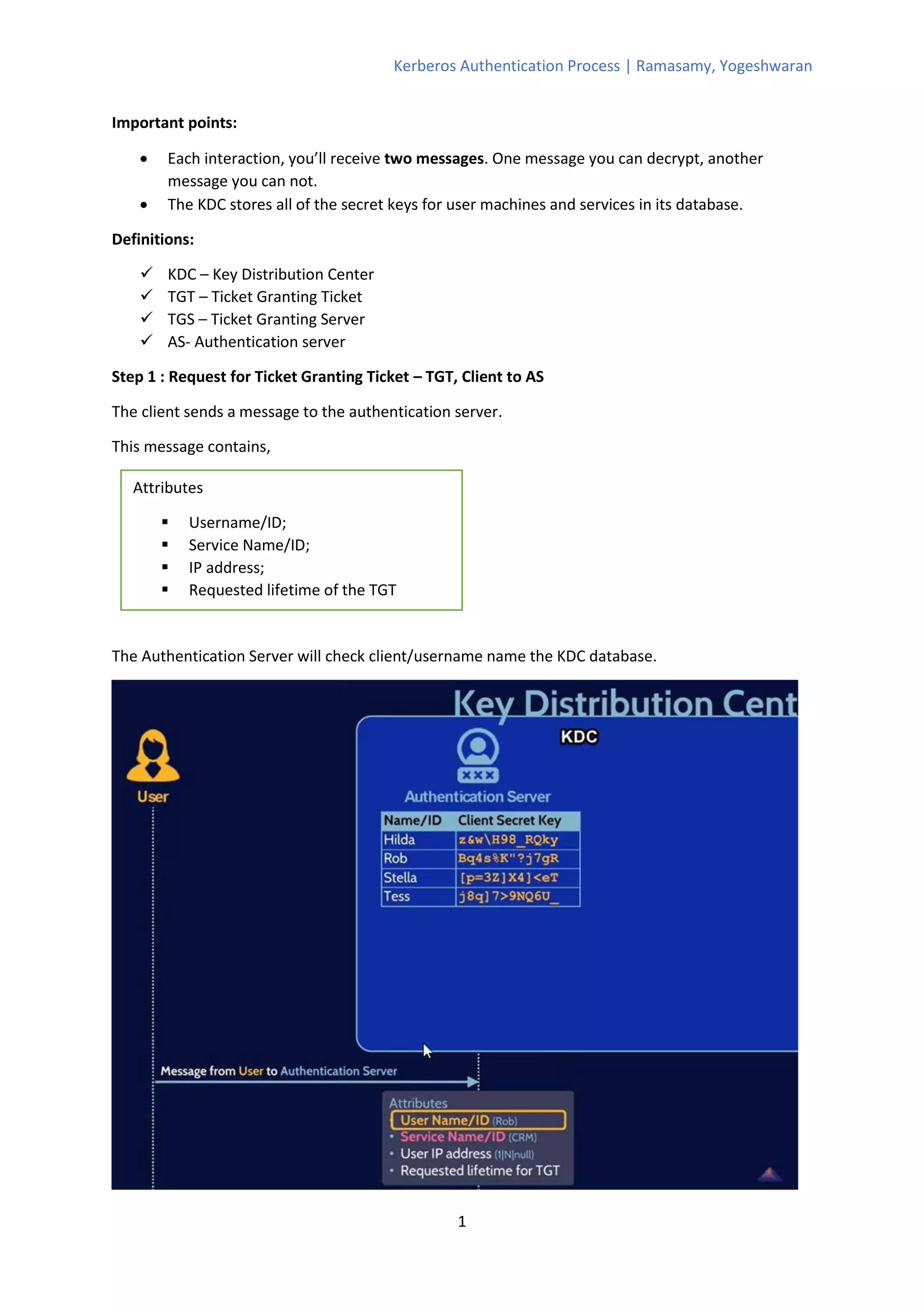
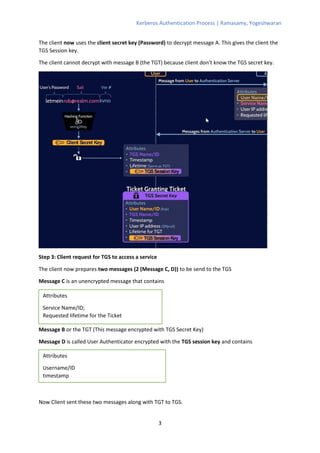
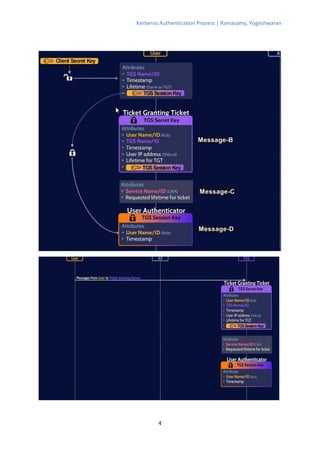
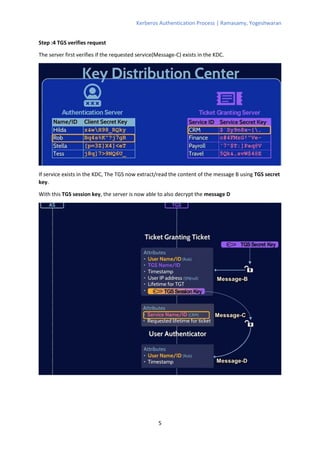
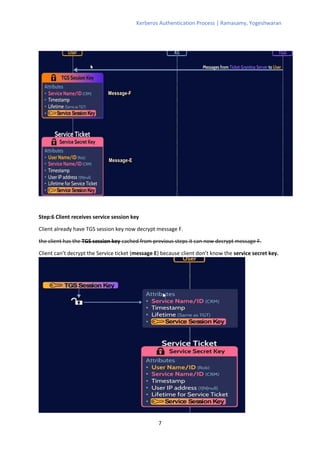
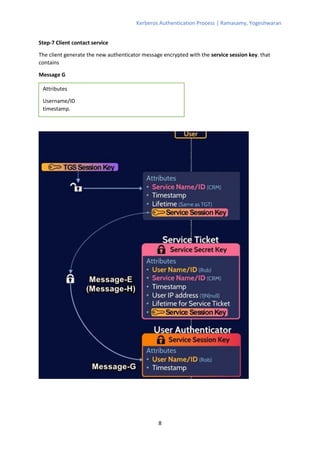
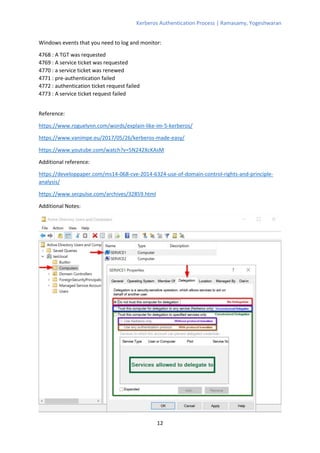
The Kerberos authentication process involves 11 steps where the client authenticates with an authentication server (AS) to obtain a ticket-granting ticket (TGT), which is then used to authenticate with a ticket-granting server (TGS) to get a service ticket for a specific service. The TGS and service both verify the ticket and authenticate the client by decrypting messages encrypted with shared session keys. The AS, TGS, and services all rely on keys stored in a central database managed by the key distribution center (KDC) to verify tickets and authenticate clients.