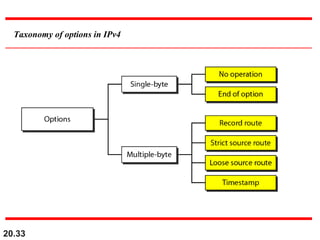
This document discusses internetworking and the Internet Protocol version 4 (IPv4). It covers key topics such as:
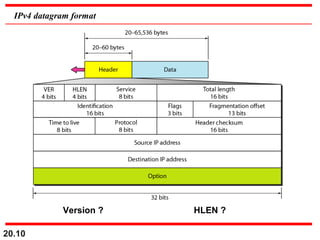
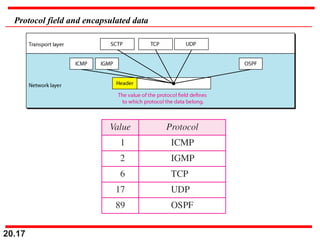
- IPv4 uses datagram packets that are independently routed and can be fragmented. Each packet contains a header with fields for source/destination addresses, protocol type, and more.
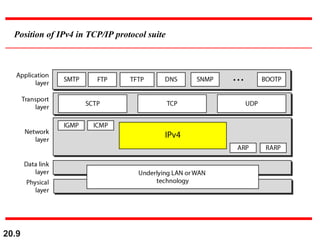
- IPv4 provides unreliable, best-effort delivery that must be paired with TCP for reliability. It positions IP as the network layer in the TCP/IP protocol suite.
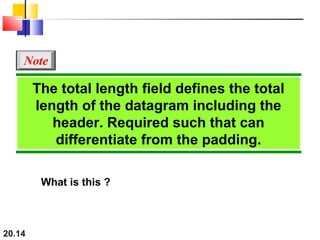
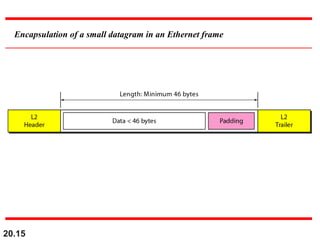
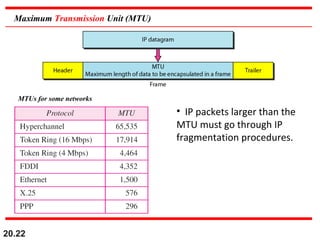
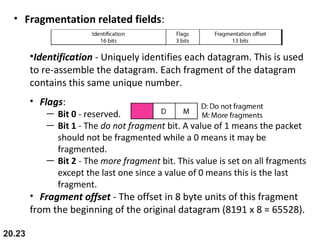
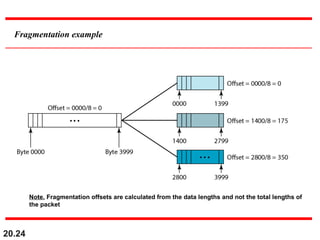
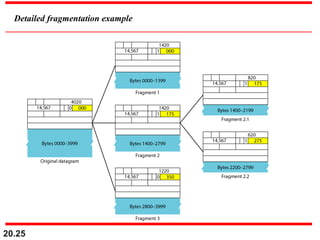
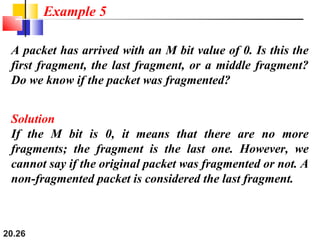
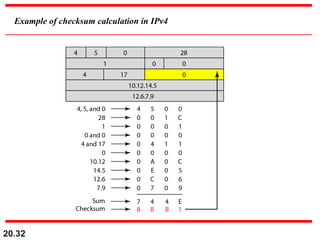
- The header fields like time-to-live, identification, and flags support functions like limiting packet lifetime, reassembling fragmented packets, and indicating last fragments. Fragmentation allows transmission of packets larger than the MTU.
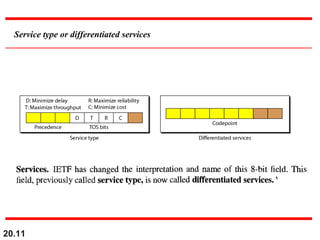
-