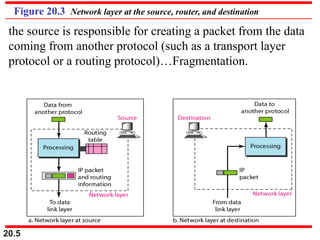
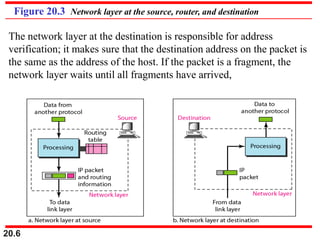
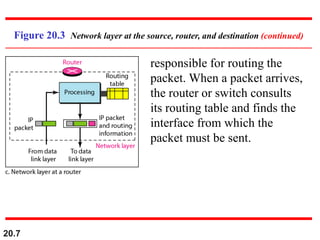
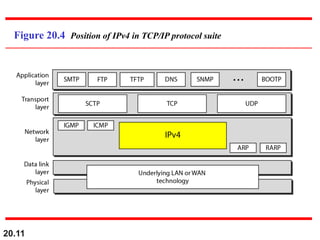
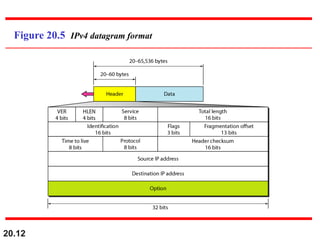
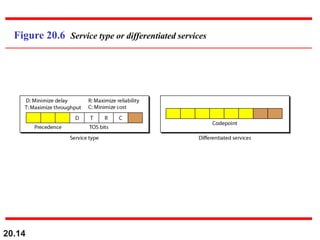
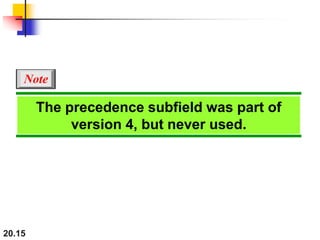
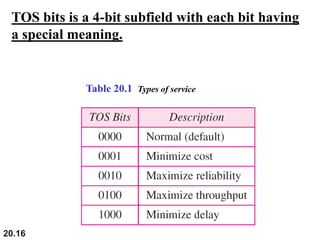
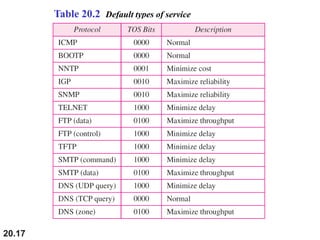
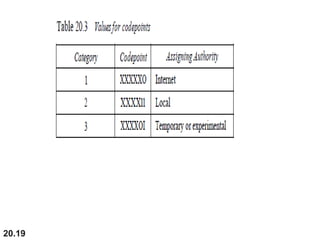
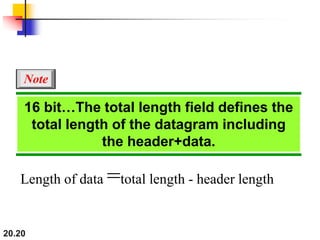
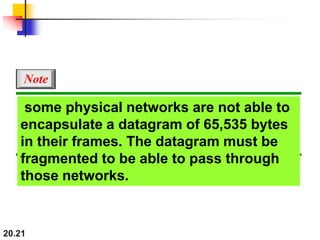
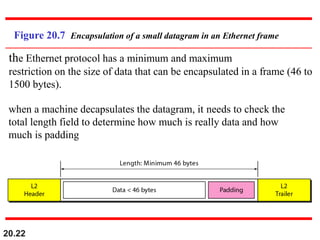
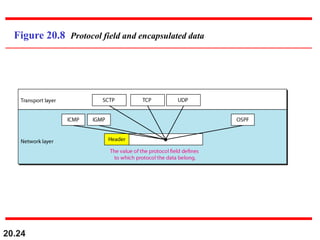
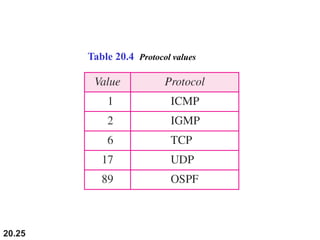
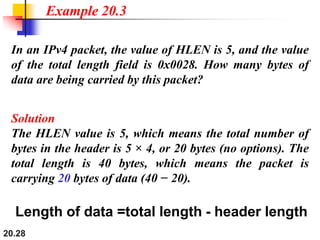
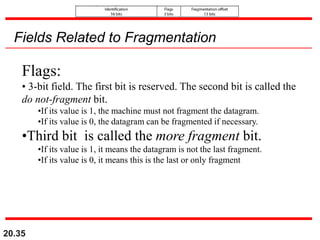
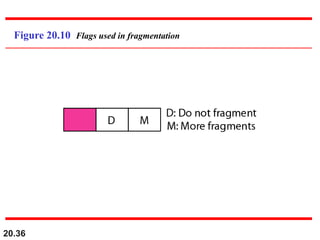
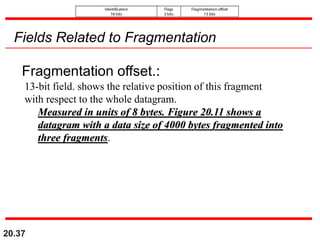
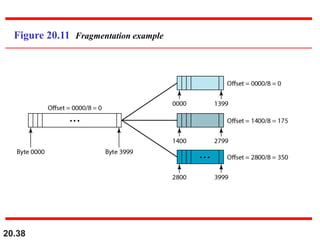
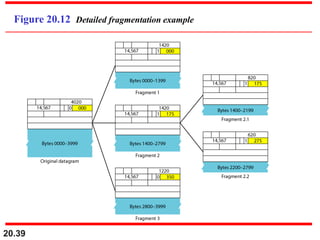
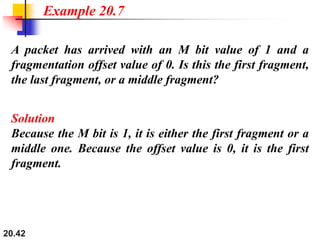
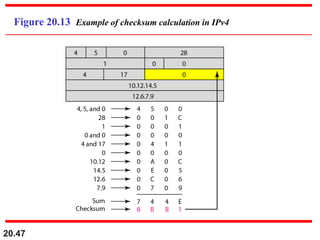
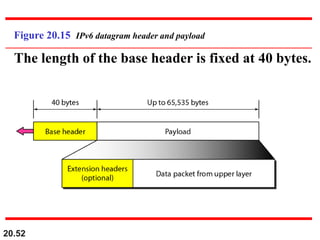
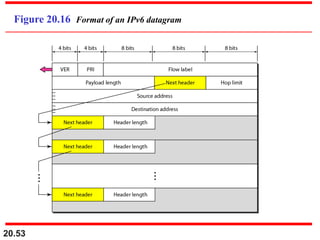
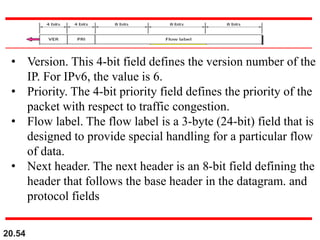
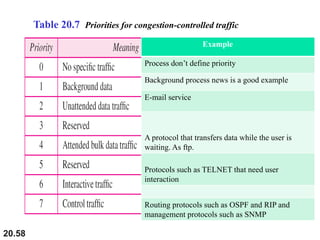
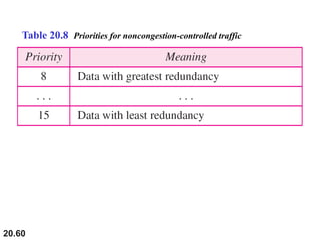
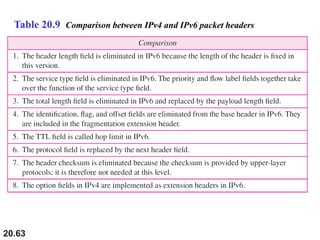
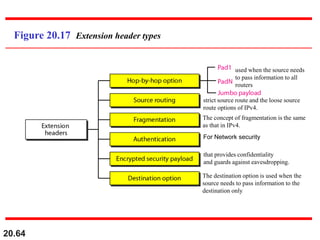
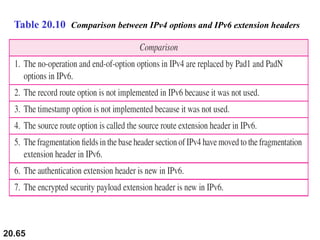
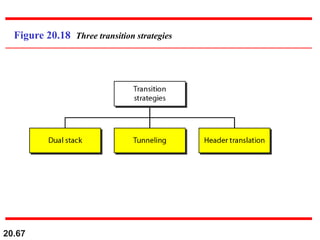
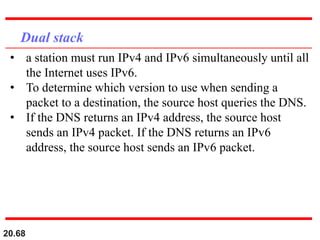
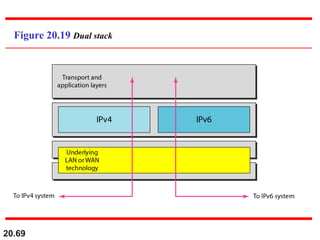
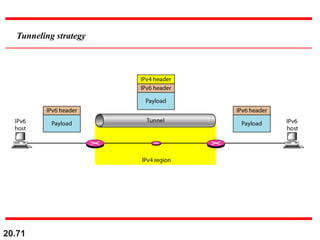
This document provides an overview of Internet Protocol version 4 (IPv4) and version 6 (IPv6). It discusses the need for a network layer in an internetwork, IPv4 addressing and packet format, fragmentation, and IPv6 advantages over IPv4 such as a larger address space and better header format. Key aspects of IPv4 include the header length field, total length field, identification field for fragmentation, flags, fragmentation offset, checksum, and protocol field. IPv6 improvements include a fixed header length, larger addresses, priority and flow label fields, and extension headers.