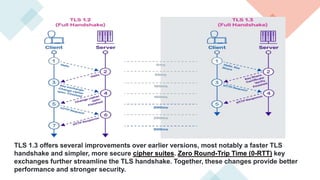
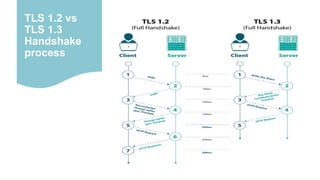
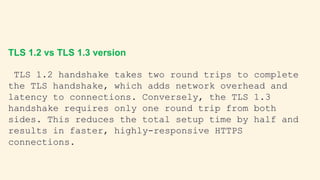
TLS 1.3 offers improvements over TLS 1.2 such as faster handshake times, simpler cipher suites, and stronger security. TLS 1.3 reduces the number of round trips needed for handshake from two to one, improving performance. It also removes support for vulnerable algorithms and features like renegotiation. While TLS 1.2 is still widely used, migration to TLS 1.3 is growing due to its benefits like reduced latency, improved website performance, and more secure connections. Businesses may need to support both versions during transition to secure communications with legacy systems.