Embed presentation

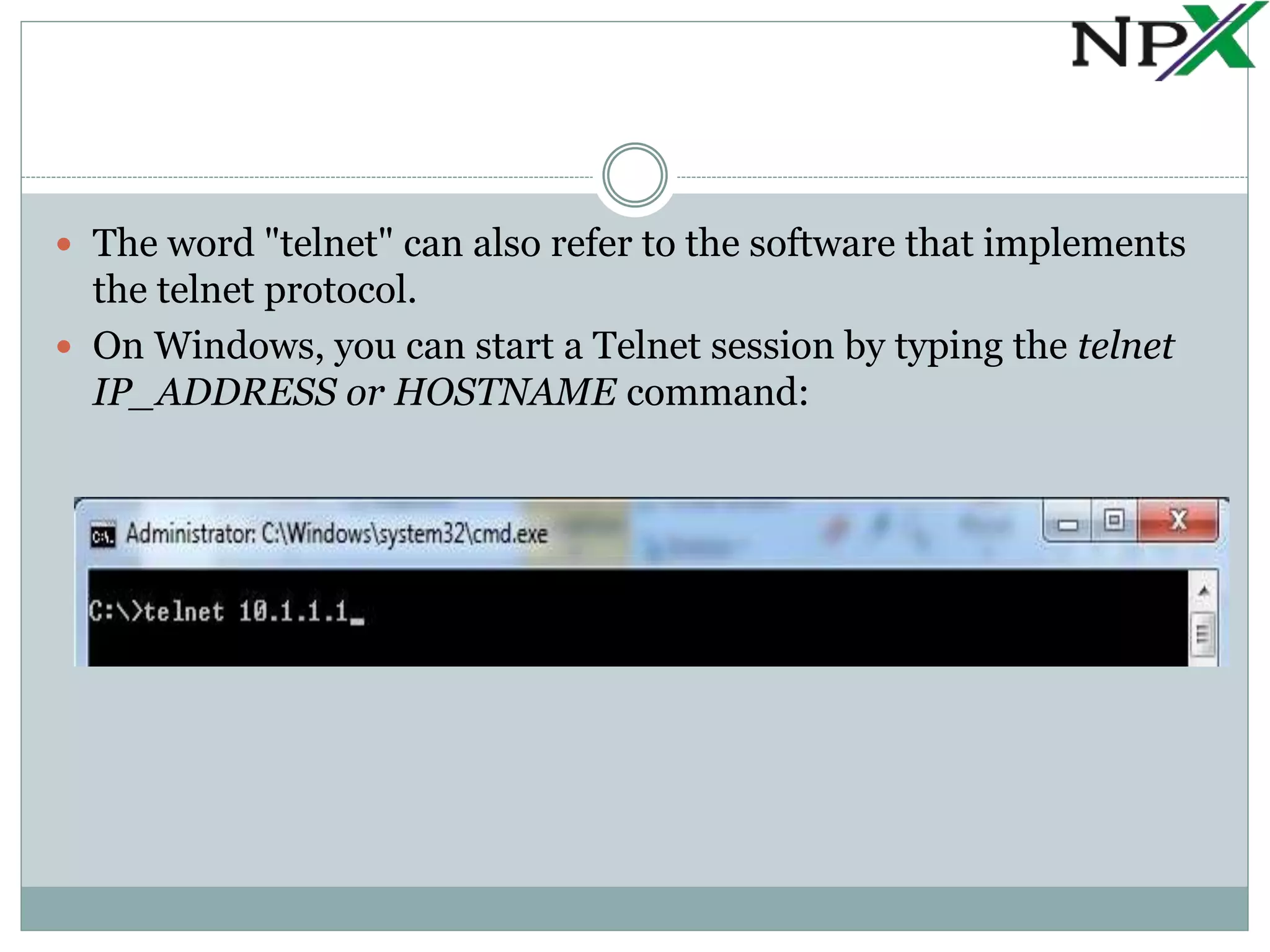

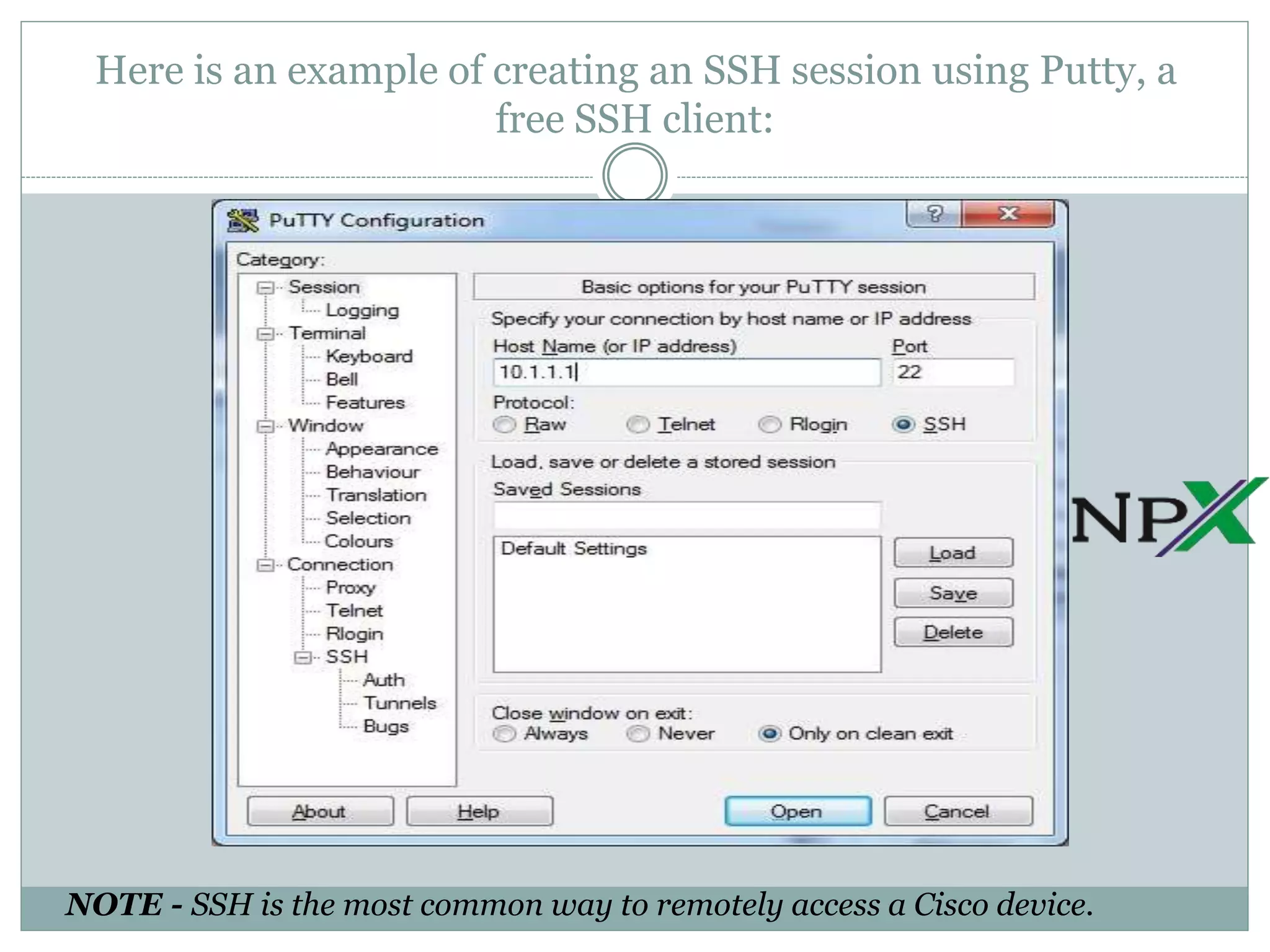

Telnet is a protocol that allows administrators to remotely access and manage devices, but it transmits usernames and passwords in clear text, posing a security risk. SSH is a more secure replacement for Telnet, as it encrypts all transmitted data using public key cryptography. Both protocols require a client and server, with Telnet using port 23 and SSH typically using port 22.




