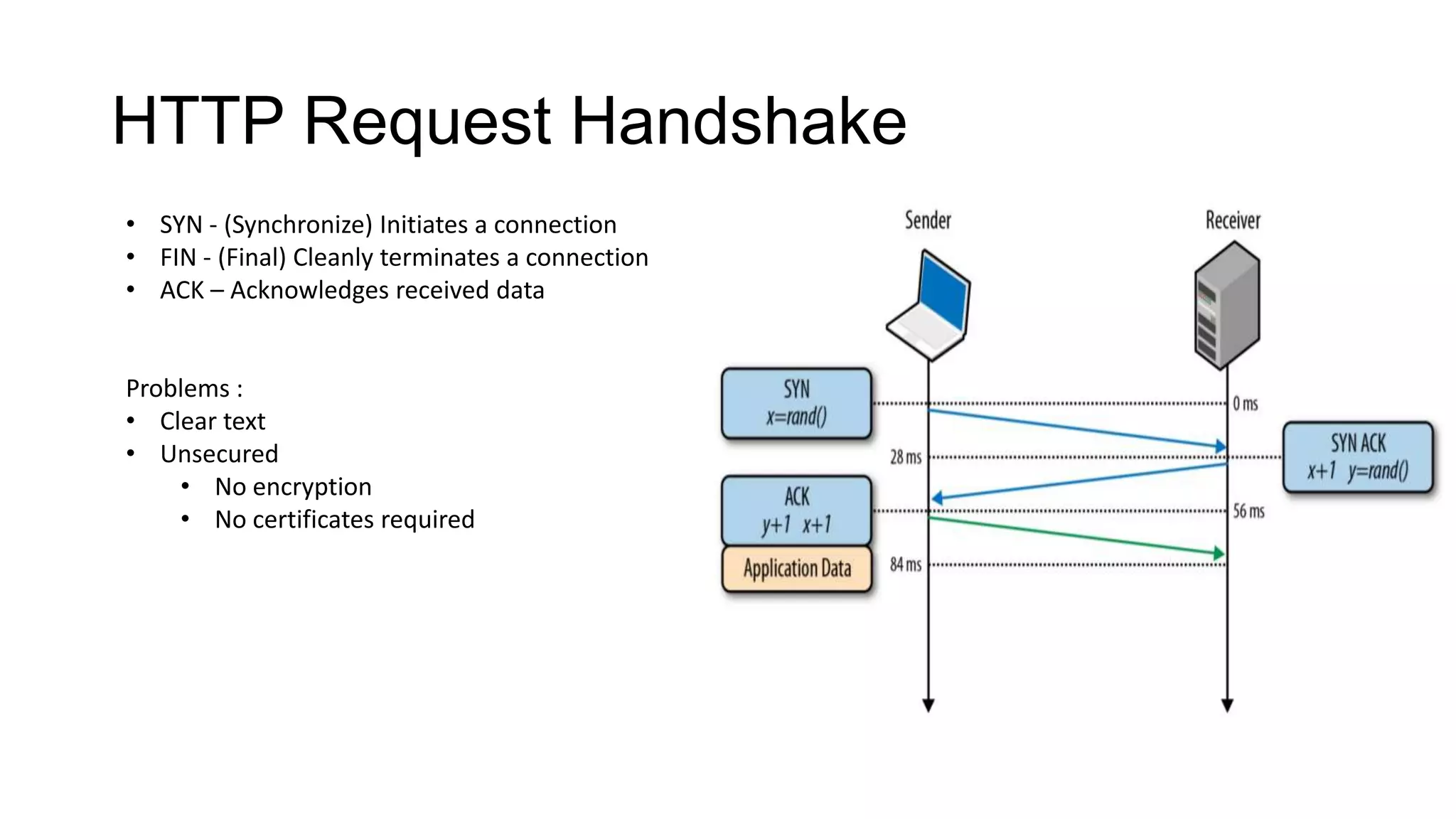
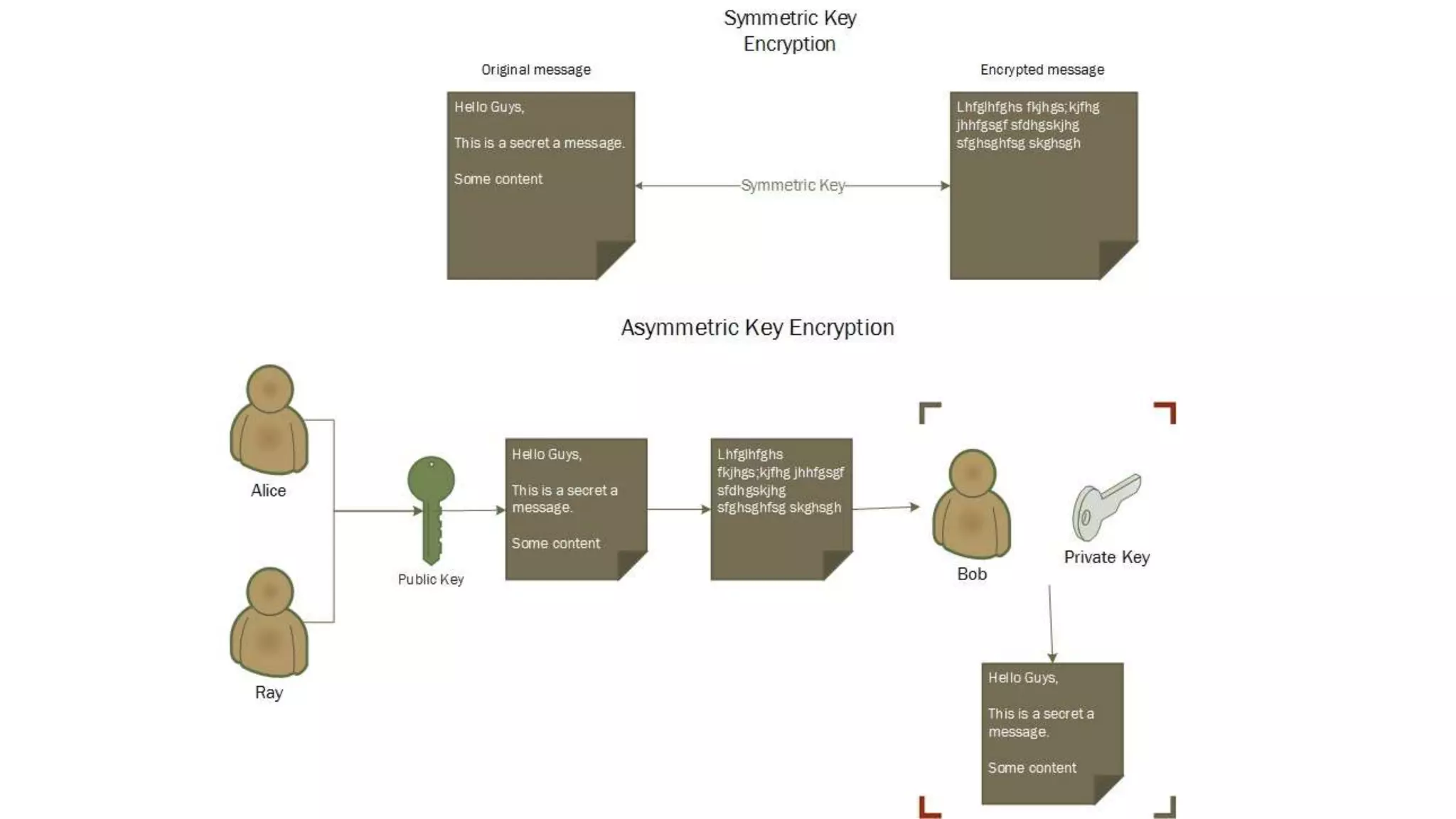
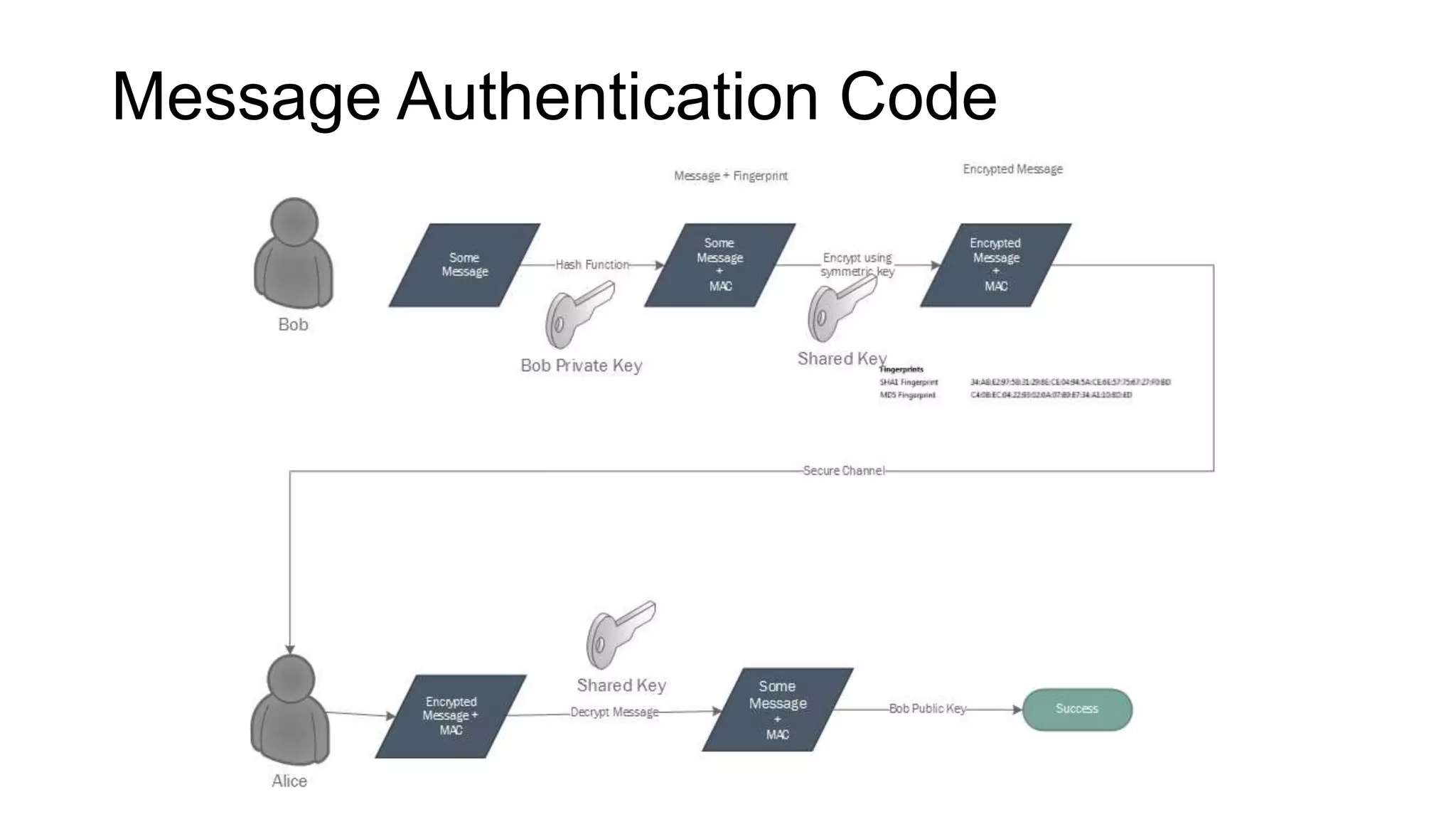
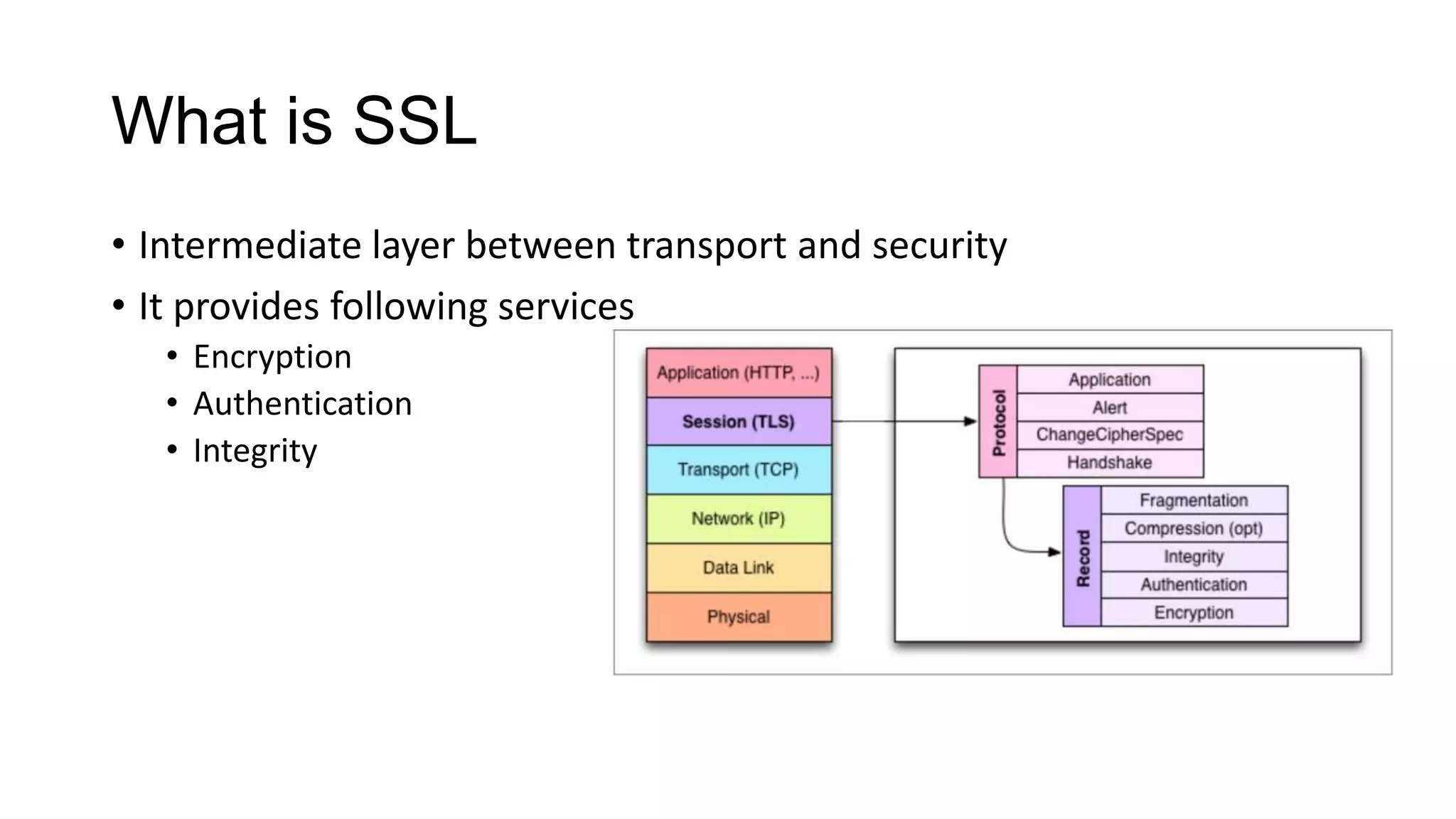
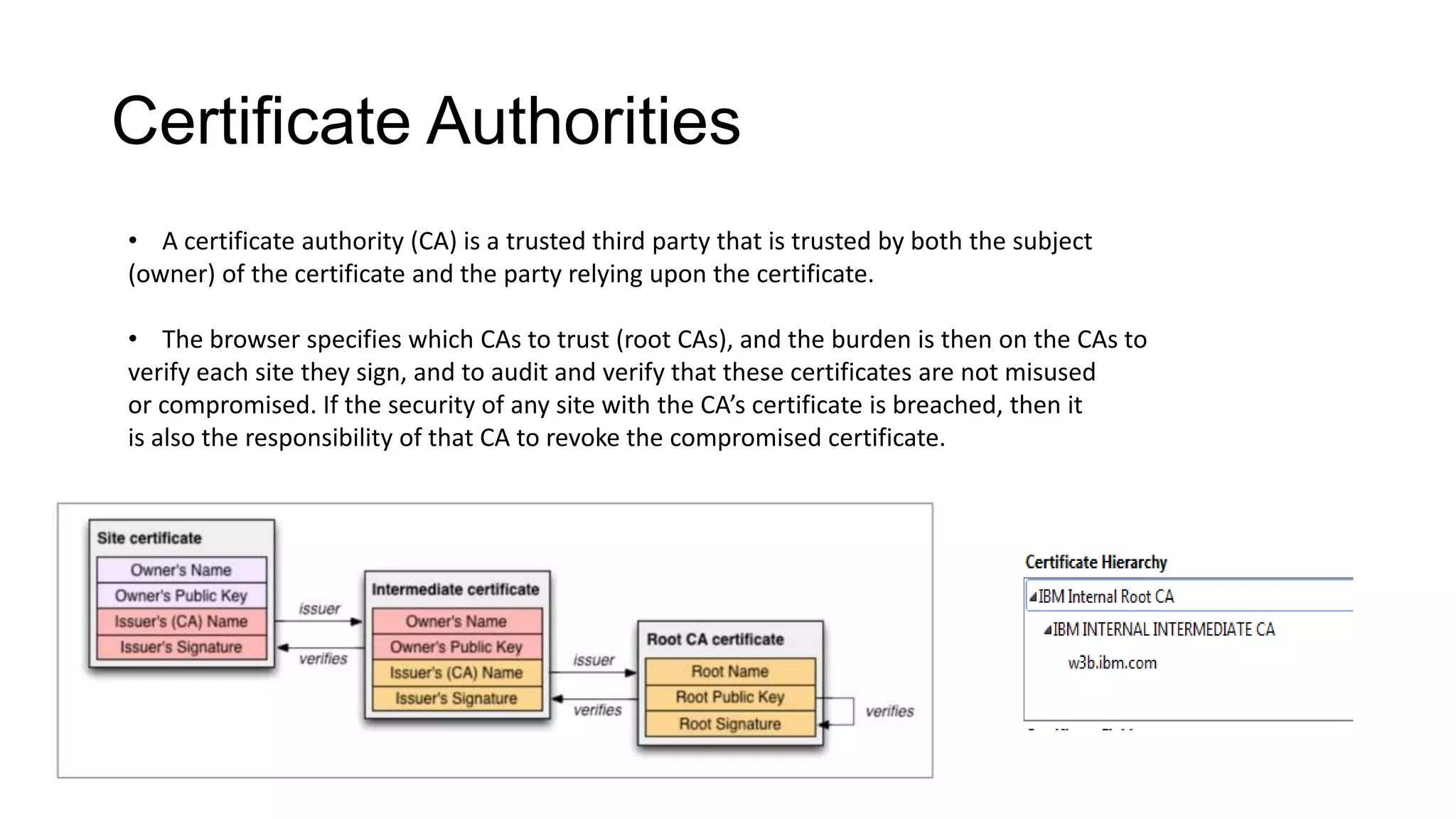
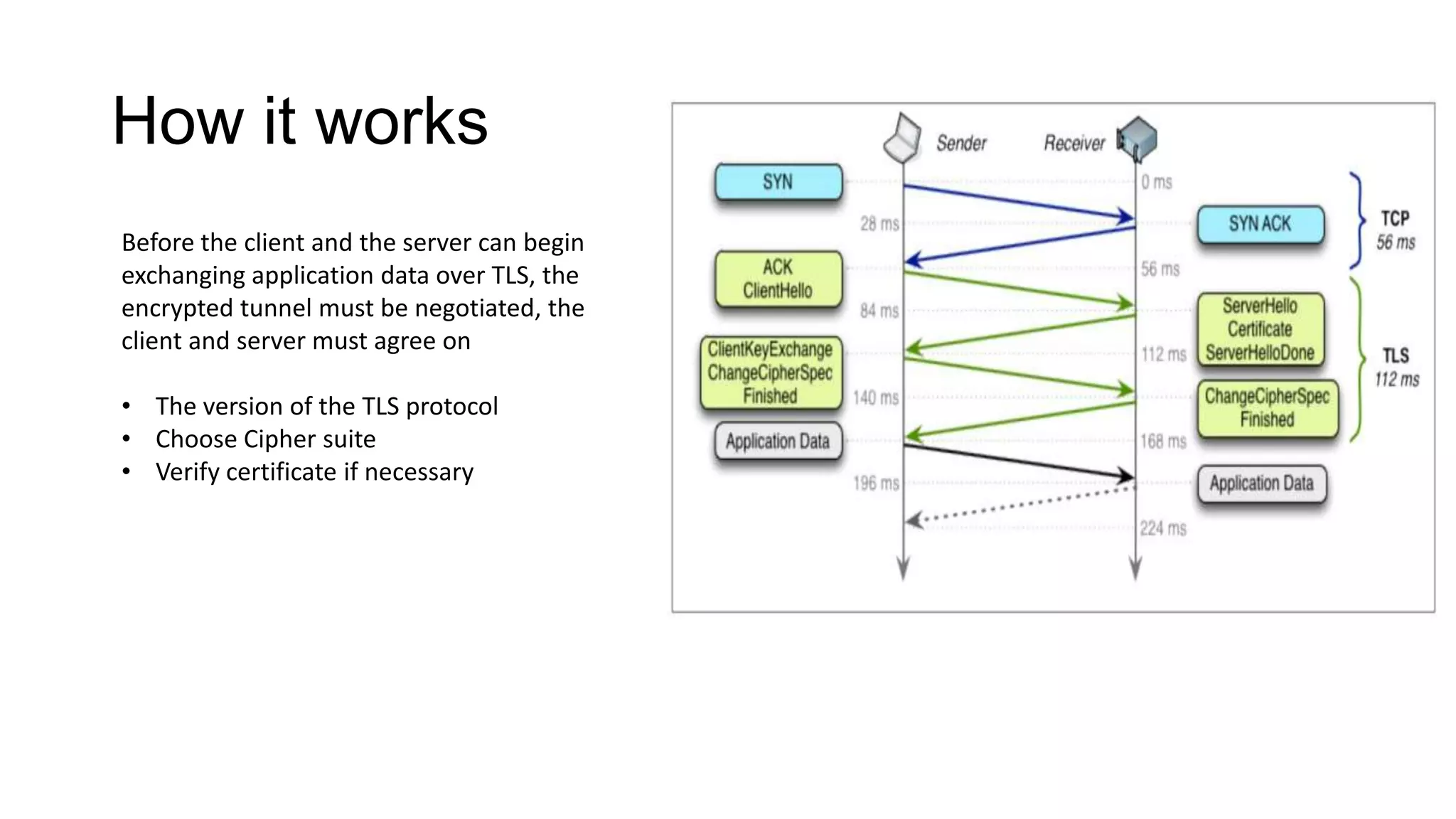
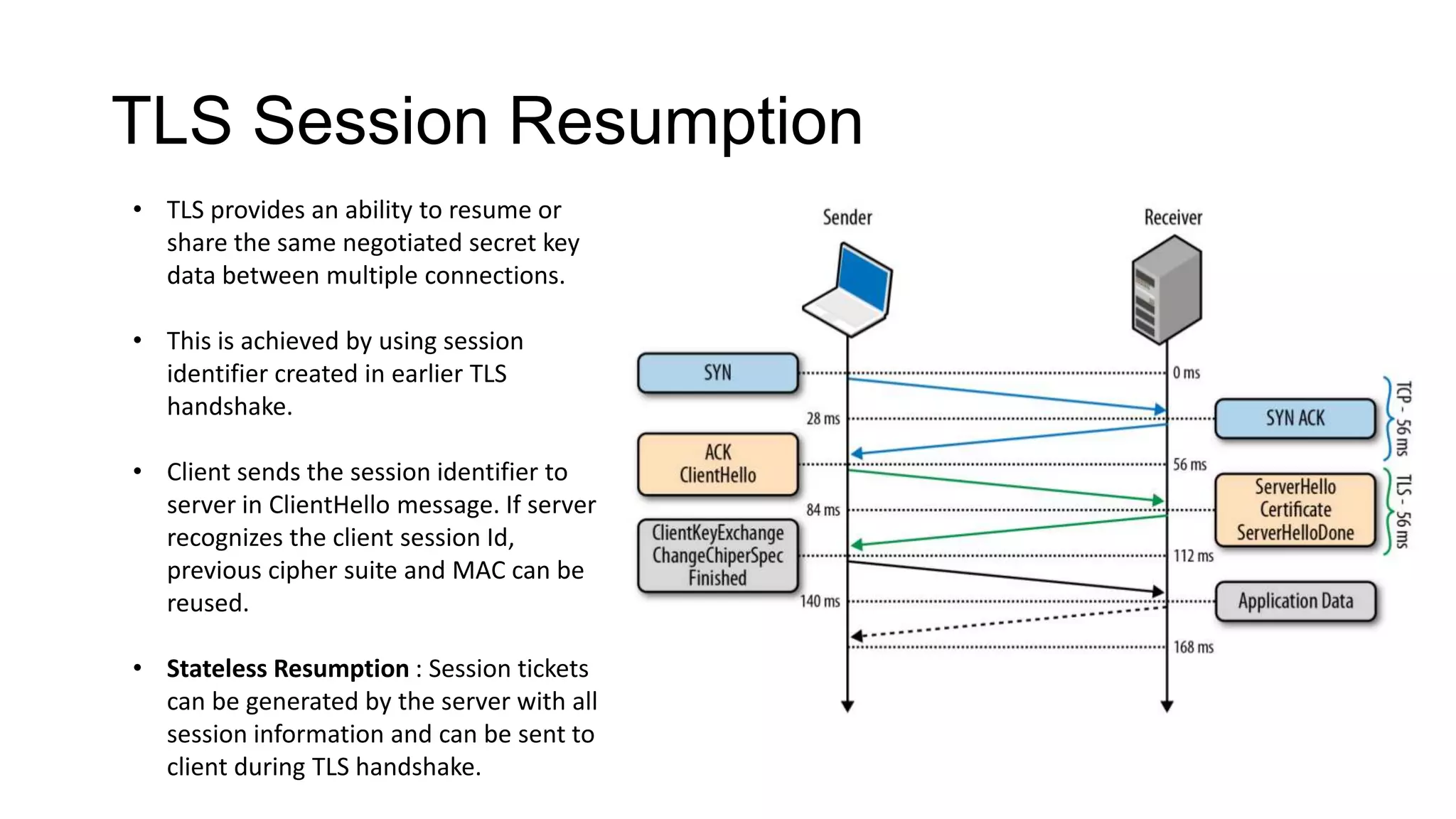
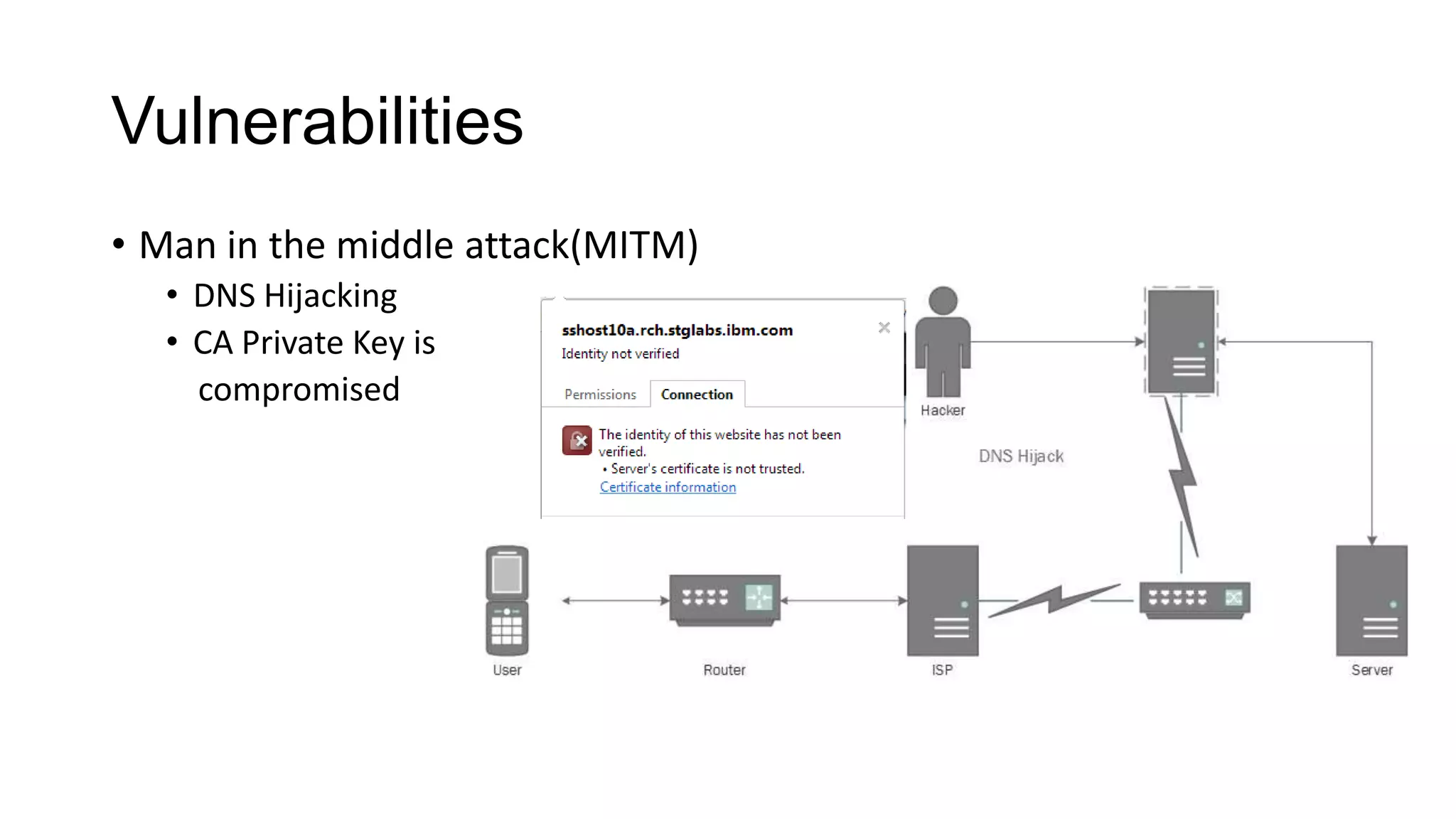
SSL/TLS is a protocol that provides encryption and authentication for web requests. It evolved from earlier SSL versions into the current TLS standard. During a TLS handshake, the client and server agree on encryption parameters and verify certificates from a certificate authority to establish a secure connection. TLS allows for session resumption to reuse encryption settings for subsequent connections via session identifiers or tickets. However, TLS is still vulnerable to man-in-the-middle and DNS hijacking attacks if certificate authorities are compromised.