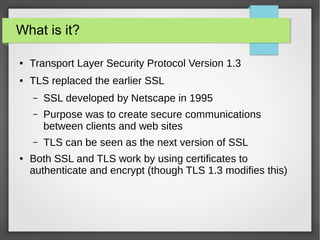
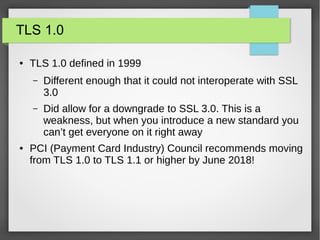
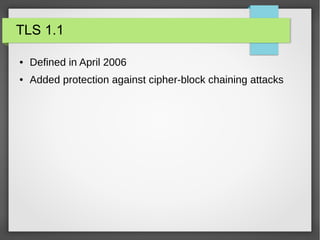
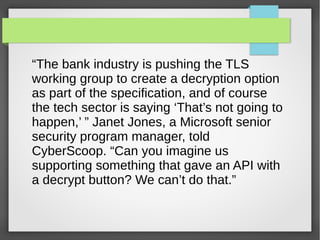
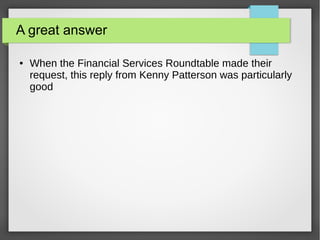
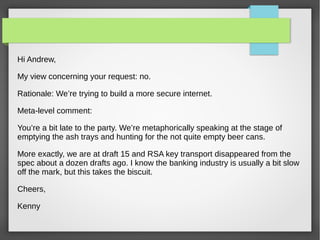
TLS 1.3 is the latest version of the Transport Layer Security protocol. It aims to improve security and performance over previous versions. Key changes include removing support for older encryption standards, simplifying the handshake process to reduce latency, improving protections against downgrade attacks, and using ephemeral Diffie-Hellman key exchange for forward secrecy instead of long-lived RSA keys. While improving security, TLS 1.3 also faces challenges around compatibility with older systems and allowing passive network monitoring.