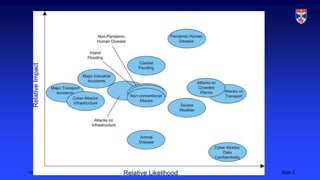
The document discusses infrastructure resilience and how to achieve it. Resilience is the ability to withstand disruptive events and continue providing essential services. Pandemics and cyberattacks are major risks. Infrastructure depends on power and communications, so failures in those have the largest impacts. Vulnerabilities include outdated software and lack of monitoring/coordination. Achieving resilience involves resistance to anticipated threats, reliable systems, redundant capacity, and response/recovery planning. Key points are that resilience allows infrastructure to continue operating during hazards and depends on contingency planning and resilient design principles.