The document provides a disaster recovery plan for KDU Bank. It includes:
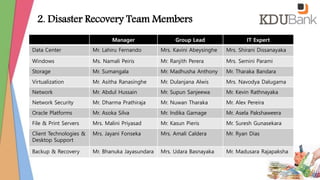
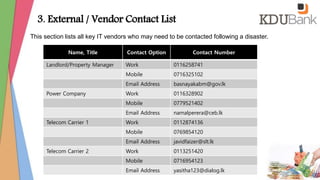
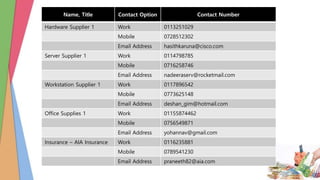
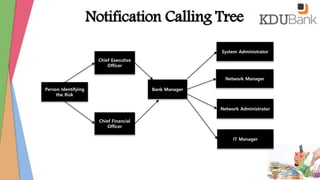
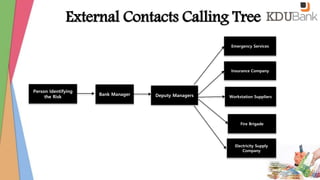
- Contact information for key IT personnel and external vendors.
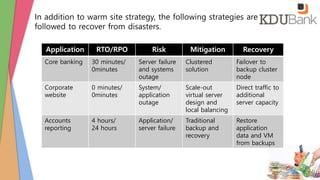
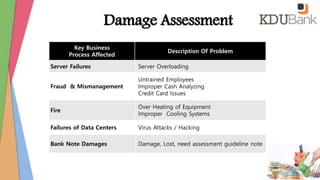
- Identification of critical systems and timelines for recovery within 4-24 hours including restoring backups and key services.
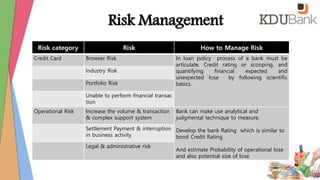
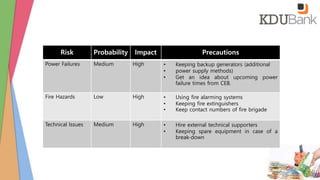
- Risks are assessed and contingencies are outlined for various disaster scenarios affecting operations.
- Backup strategies, software and physical safeguards are defined to enable recovery from disruption of computer and network services.