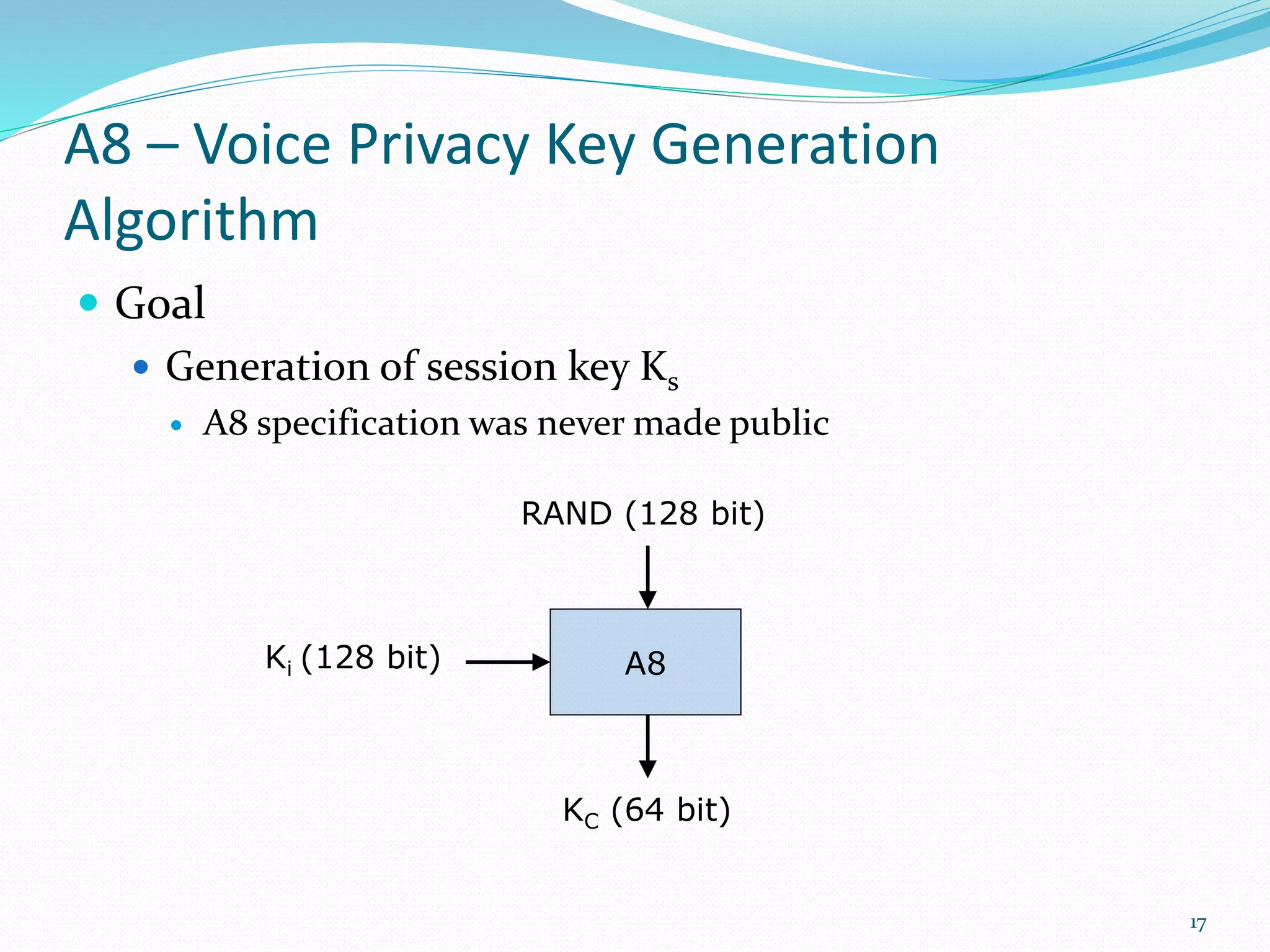
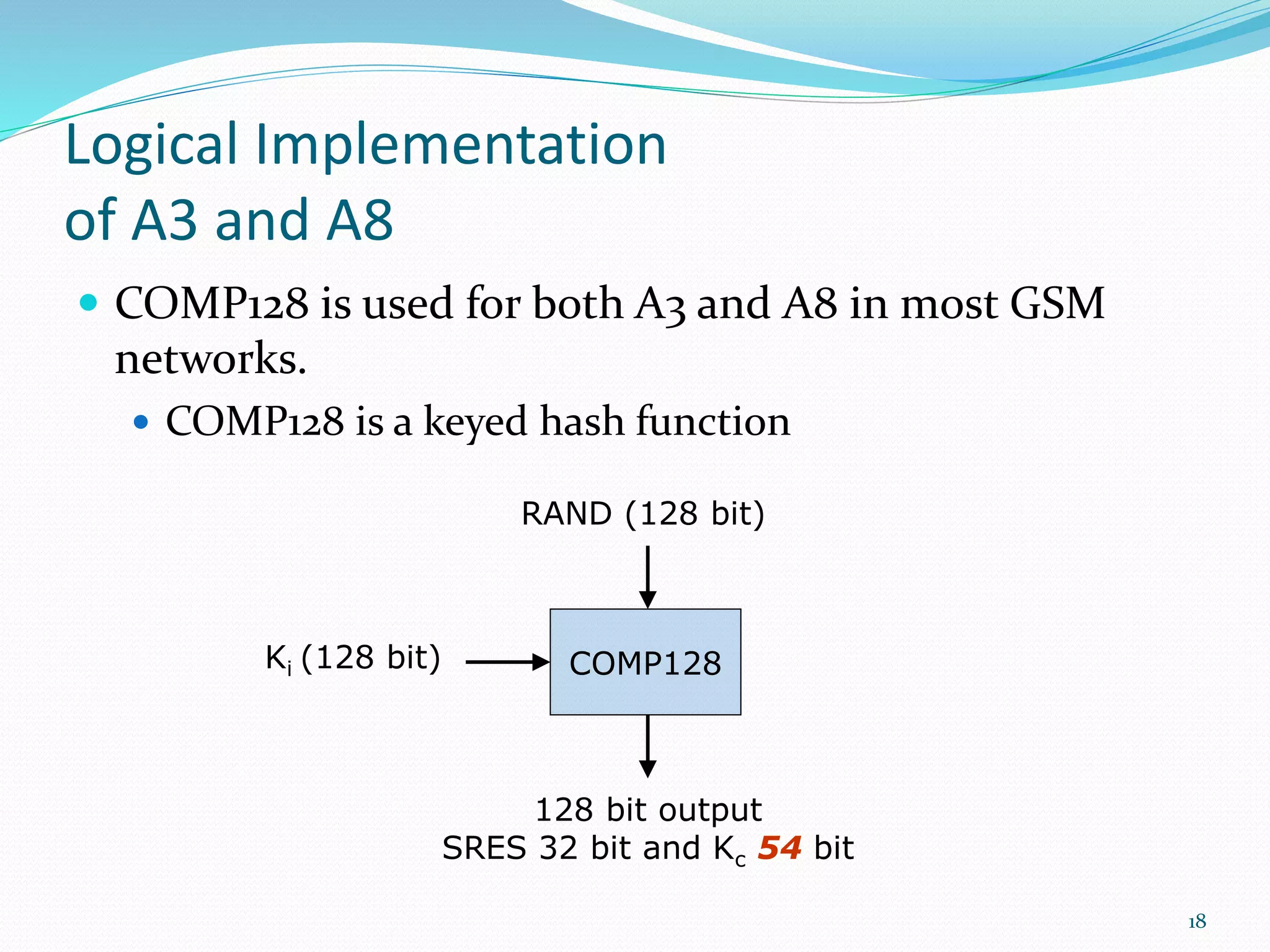
GSM uses authentication and encryption to provide security. Authentication involves generating a signed response (SRES) to a random challenge (RAND) using an authentication key (Ki) and algorithm (A3). Encryption uses a session key (Kc) generated from Ki and RAND by algorithm A8. The stream cipher A5 encrypts voice data using Kc and a frame number. GSM security protects conversations, signaling data, and prevents fraud through these methods of authentication, encryption, and temporary subscriber identities.