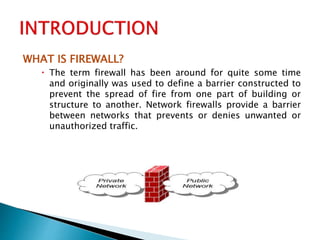
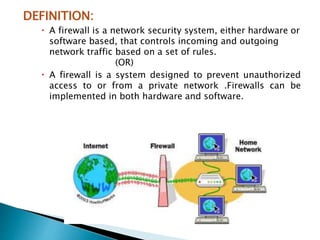
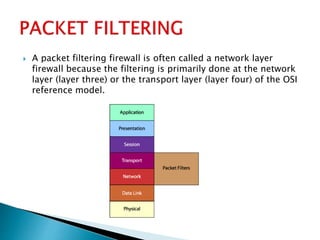
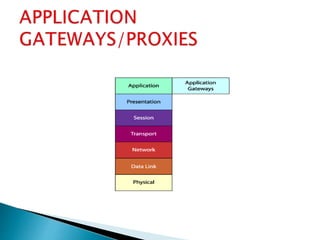
This document discusses firewalls and their types. It begins by explaining that firewalls protect networks by guarding entry points and are becoming more sophisticated. It then defines a firewall as a network security system that controls incoming and outgoing network traffic based on rules. The document outlines different generations of firewalls and describes four main types: packet filtering, stateful packet inspection, application gateways/proxies, and circuit-level gateways. It details the characteristics, strengths, and weaknesses of each type. Finally, it emphasizes that networks are still at risk of attacks and that firewalls have become ubiquitous, so choosing the right solution depends on needs, policies, resources.