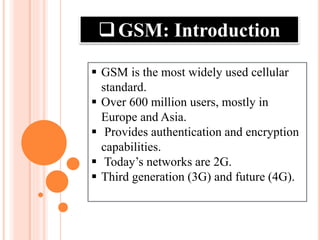
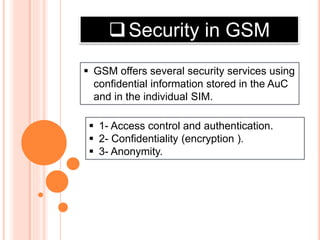
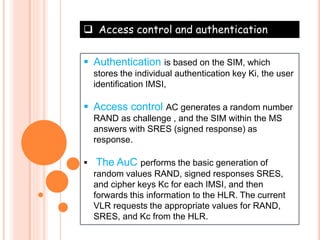
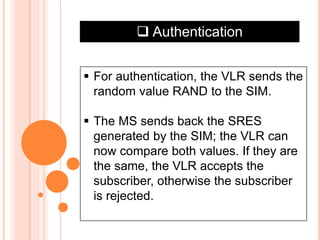
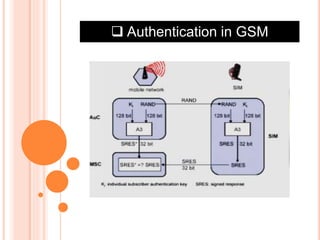
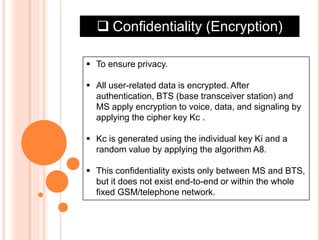
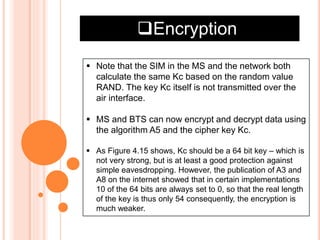
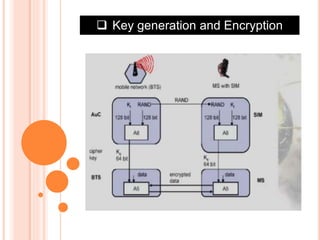
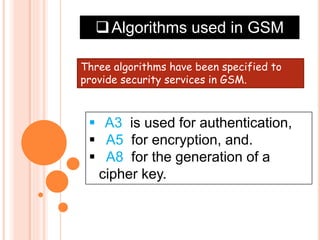
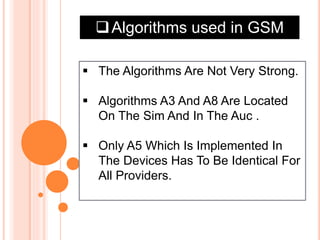
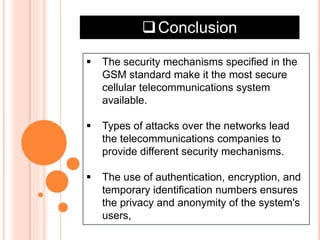
GSM is the most widely used cellular standard with over 600 million users, particularly in Europe and Asia, and provides essential security services such as authentication, encryption, and anonymity. Authentication relies on individual SIM cards storing unique keys, while confidentiality is managed through encryption after authentication, although this is not end-to-end secure. Despite certain vulnerabilities in the algorithms used, GSM remains the most secure cellular telecommunications system due to its implemented security mechanisms.